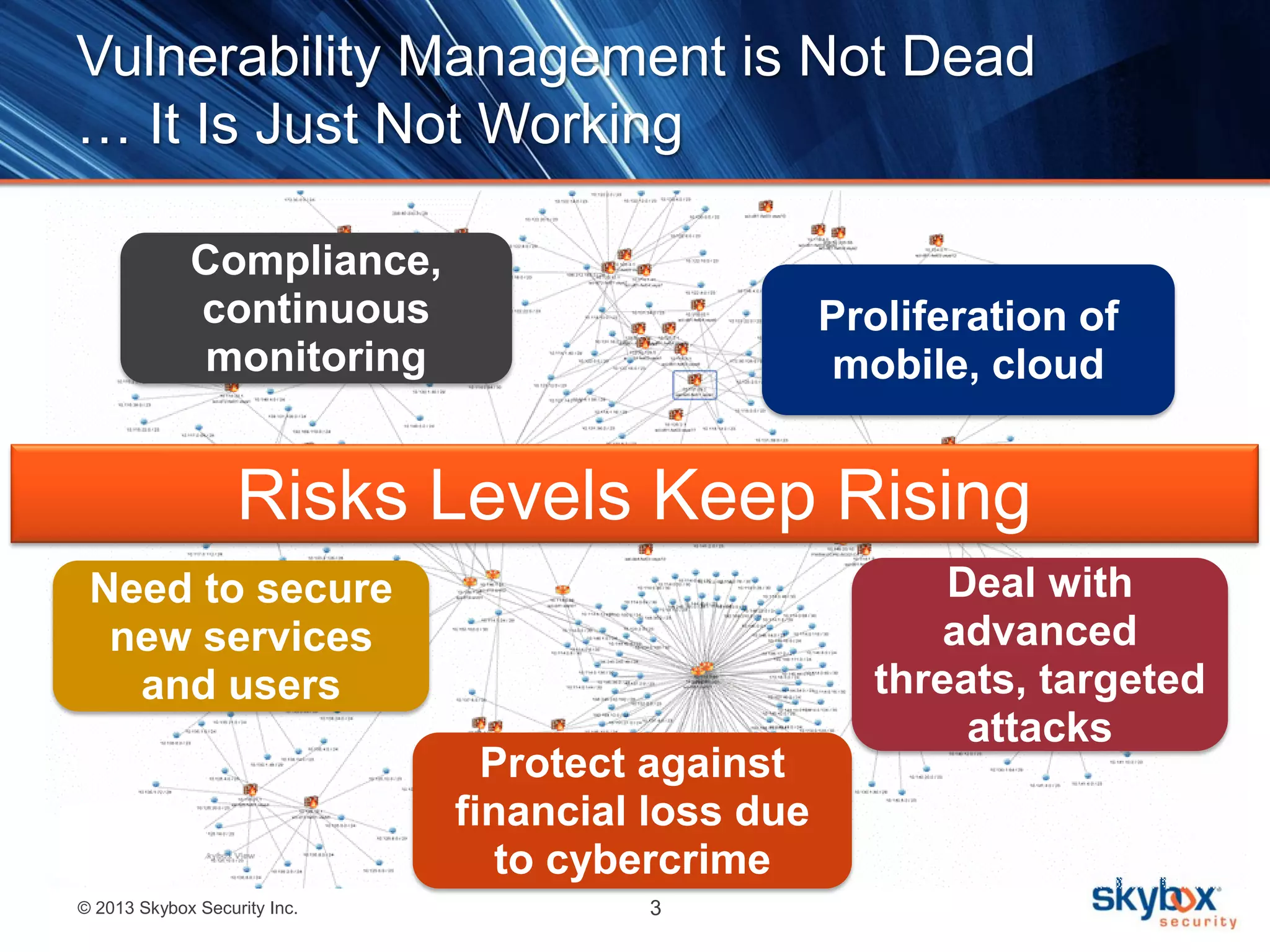
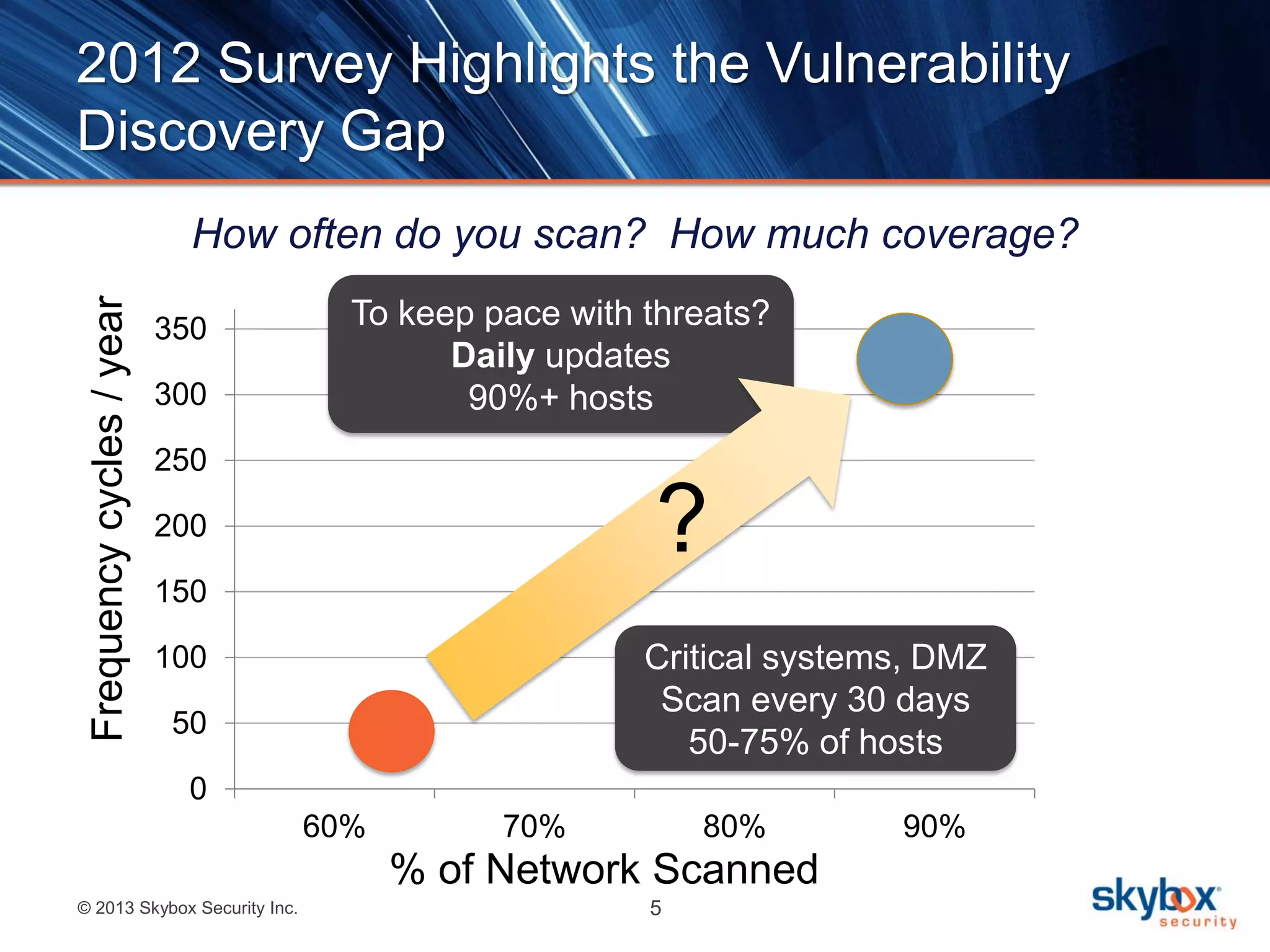
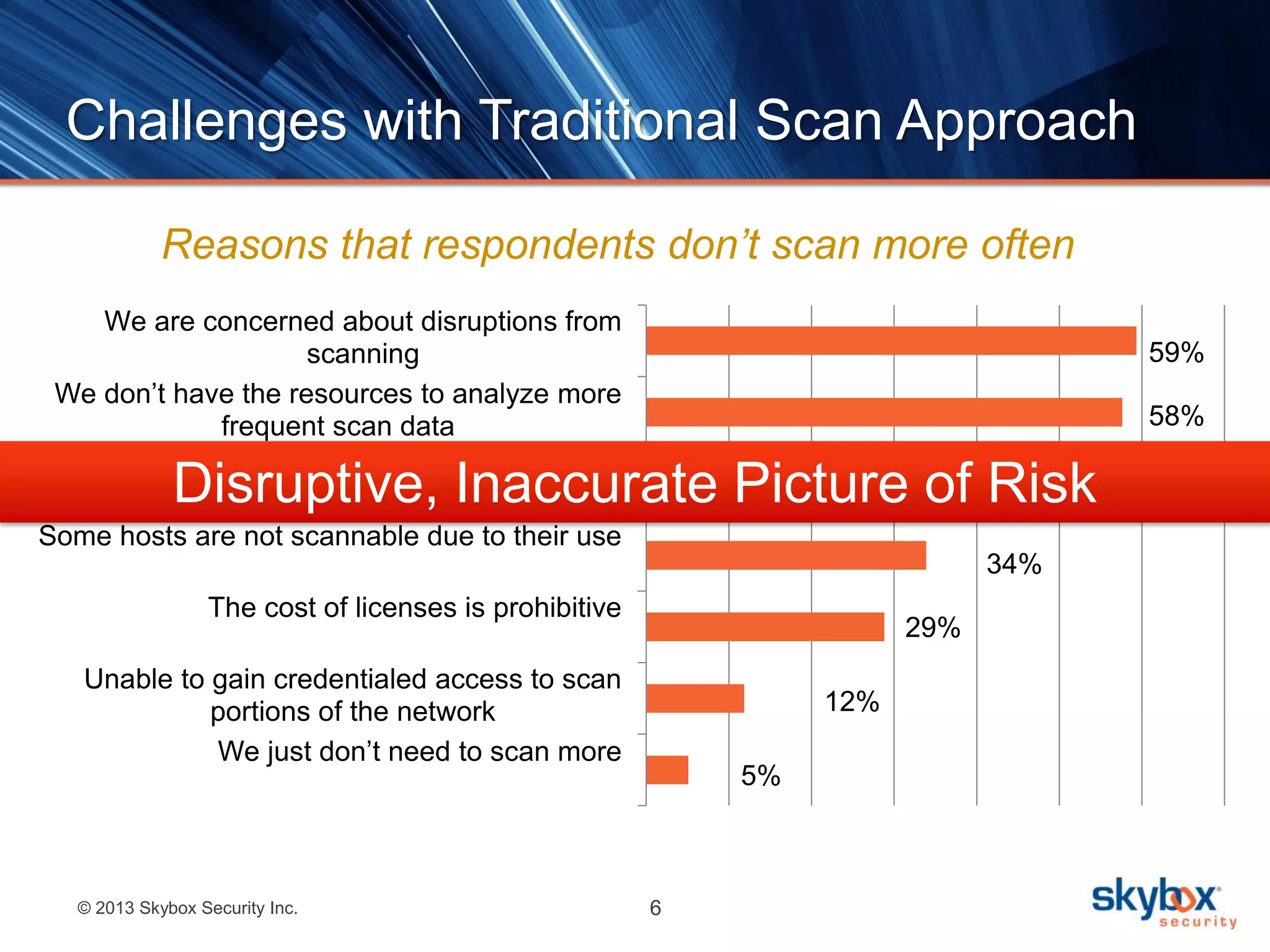
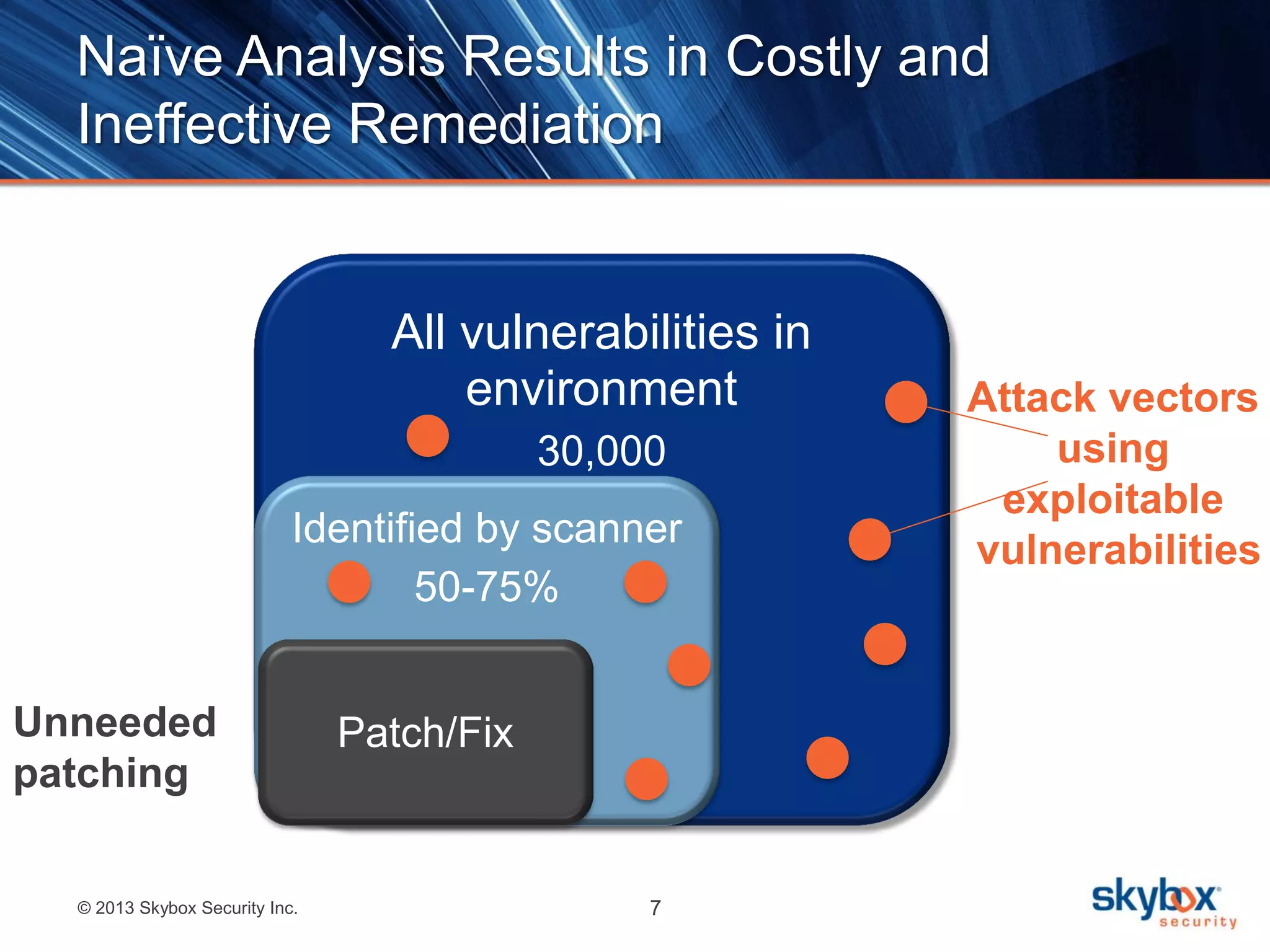
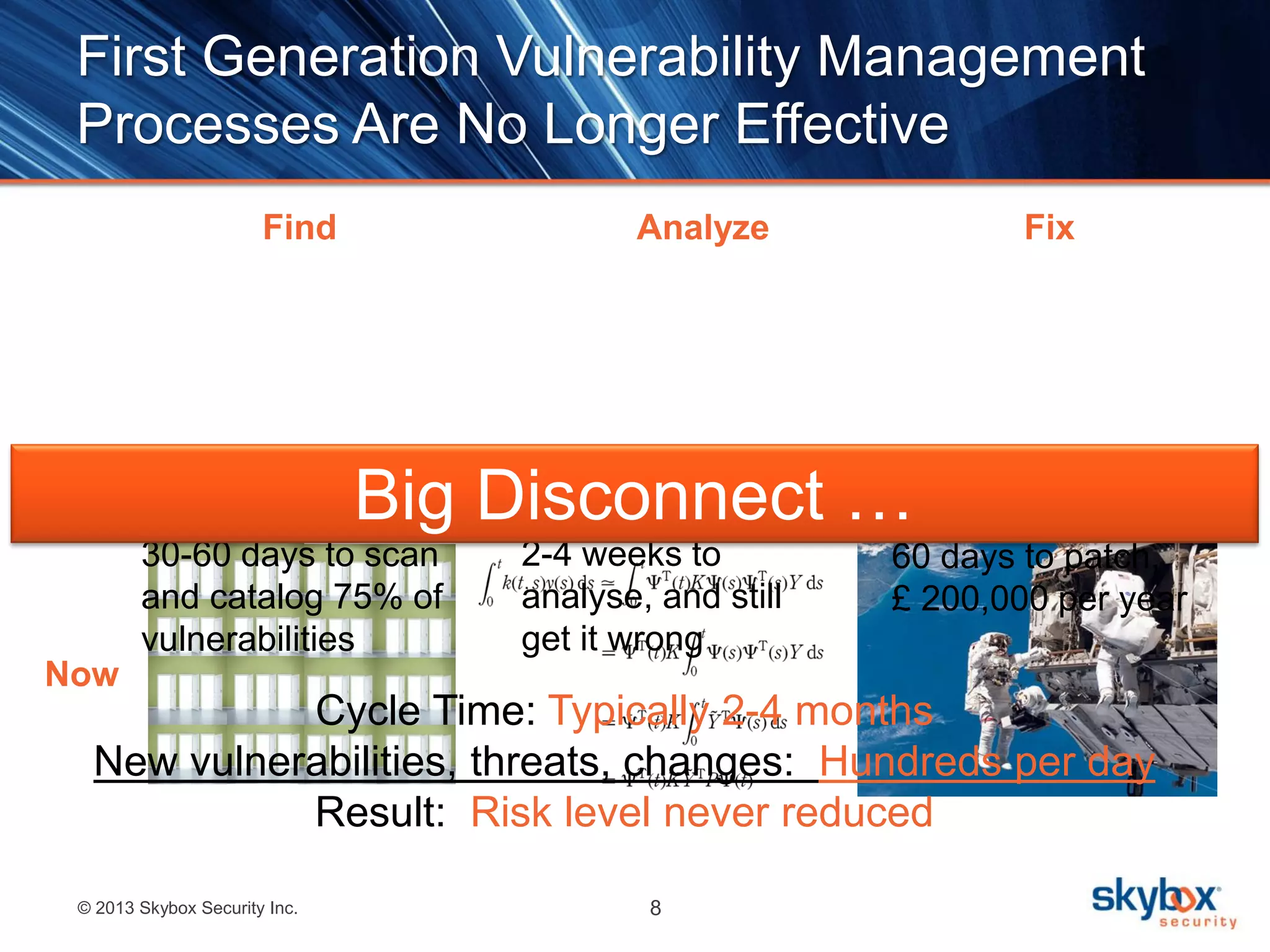
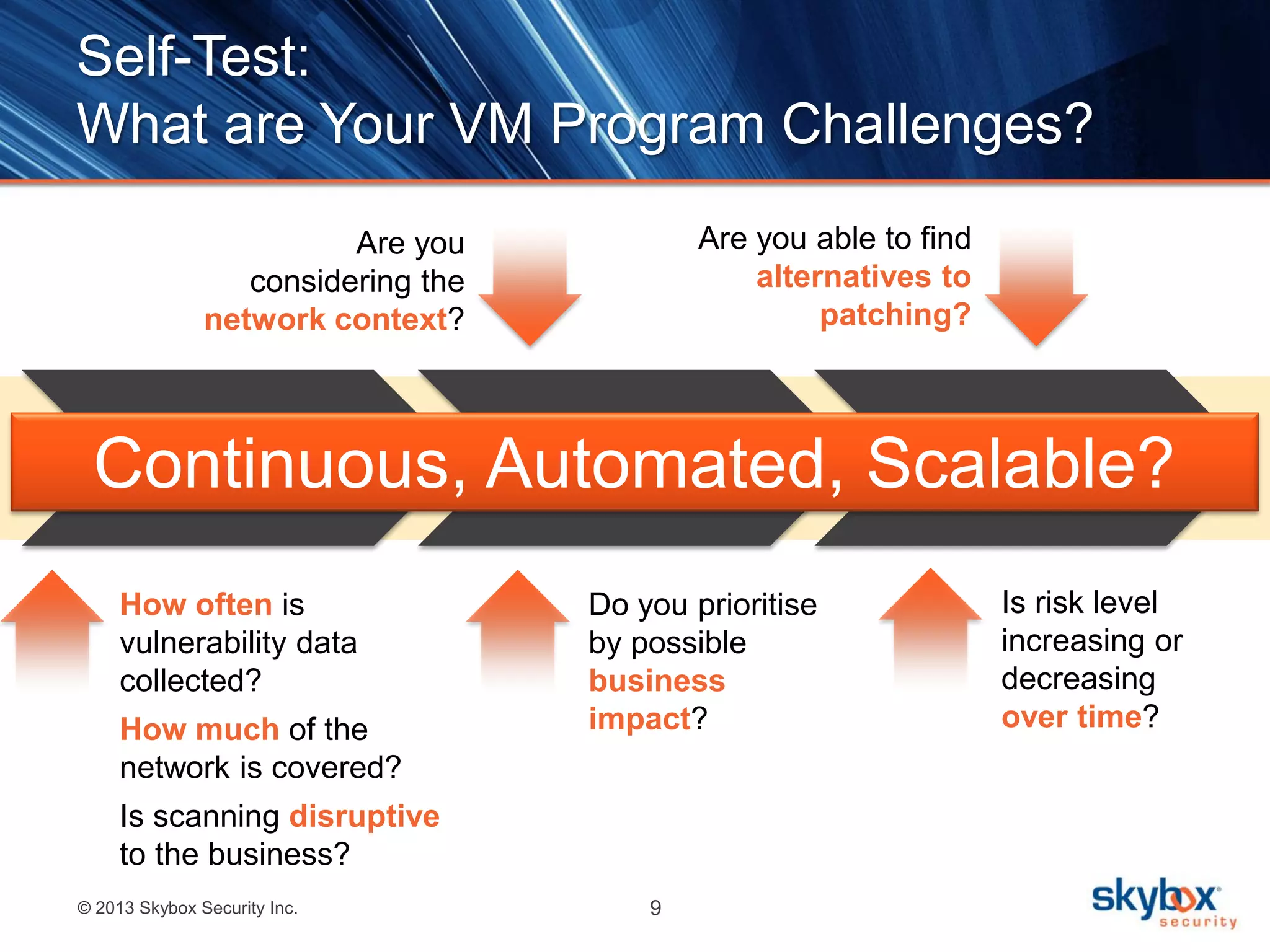
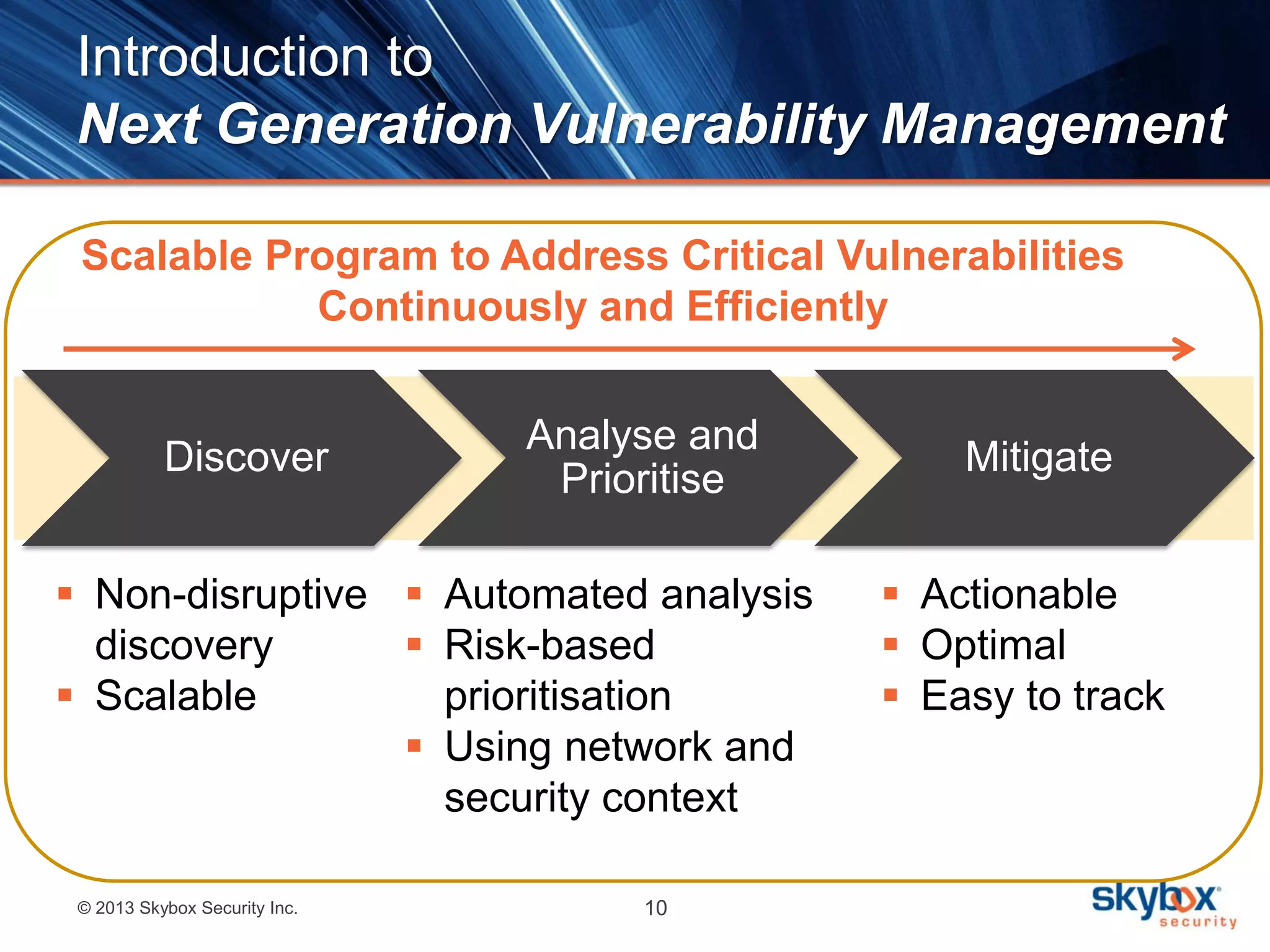
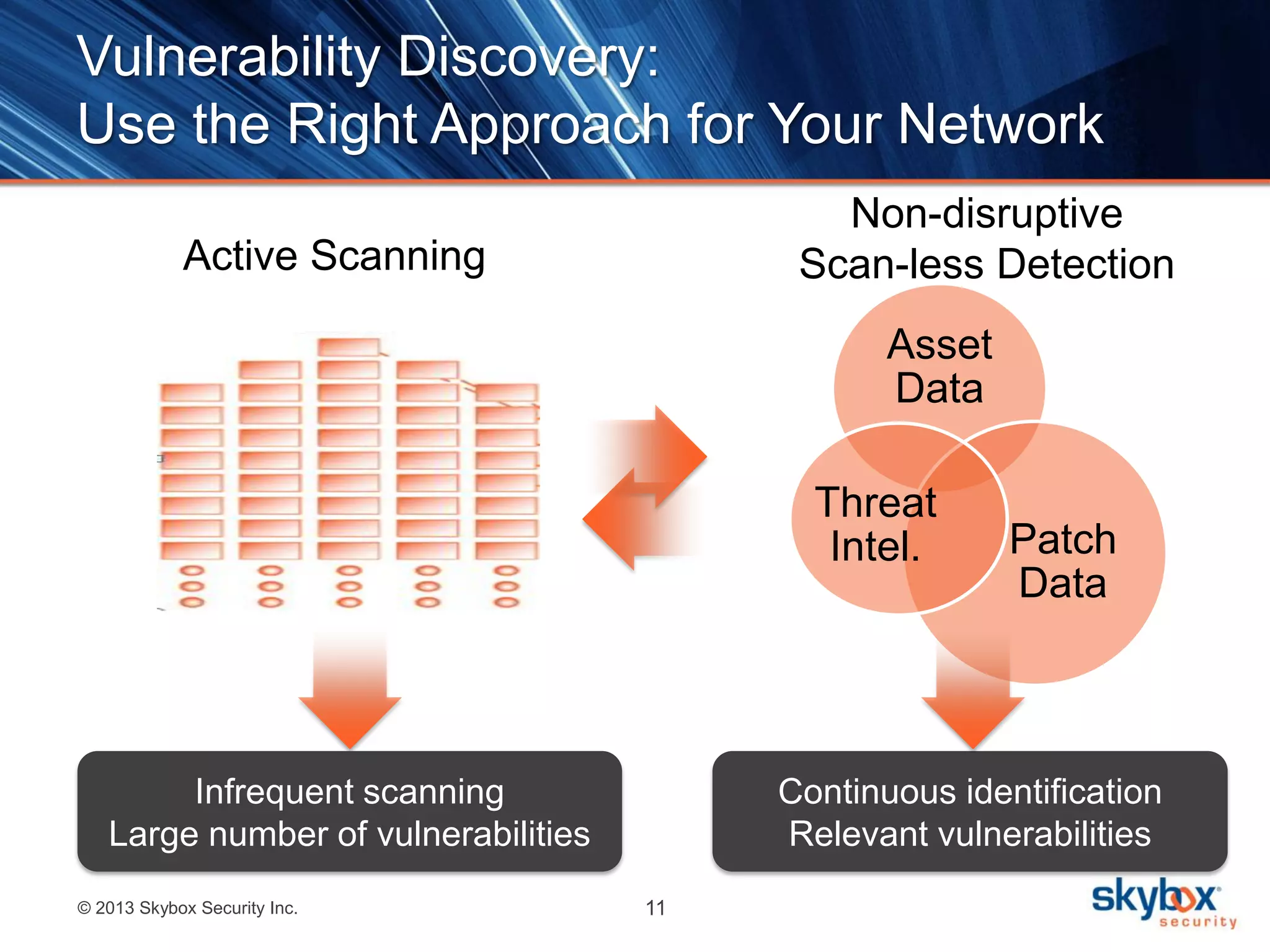
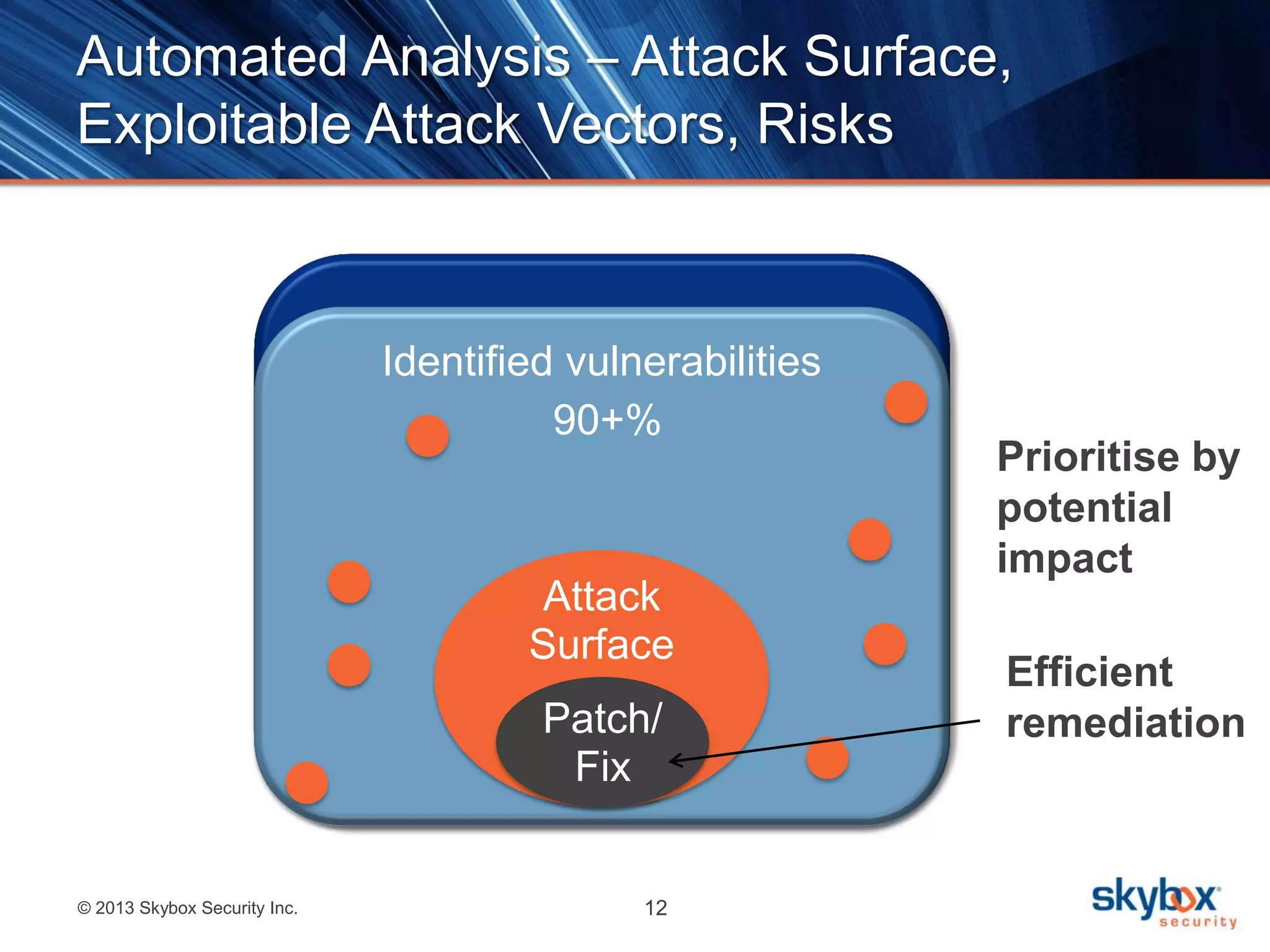
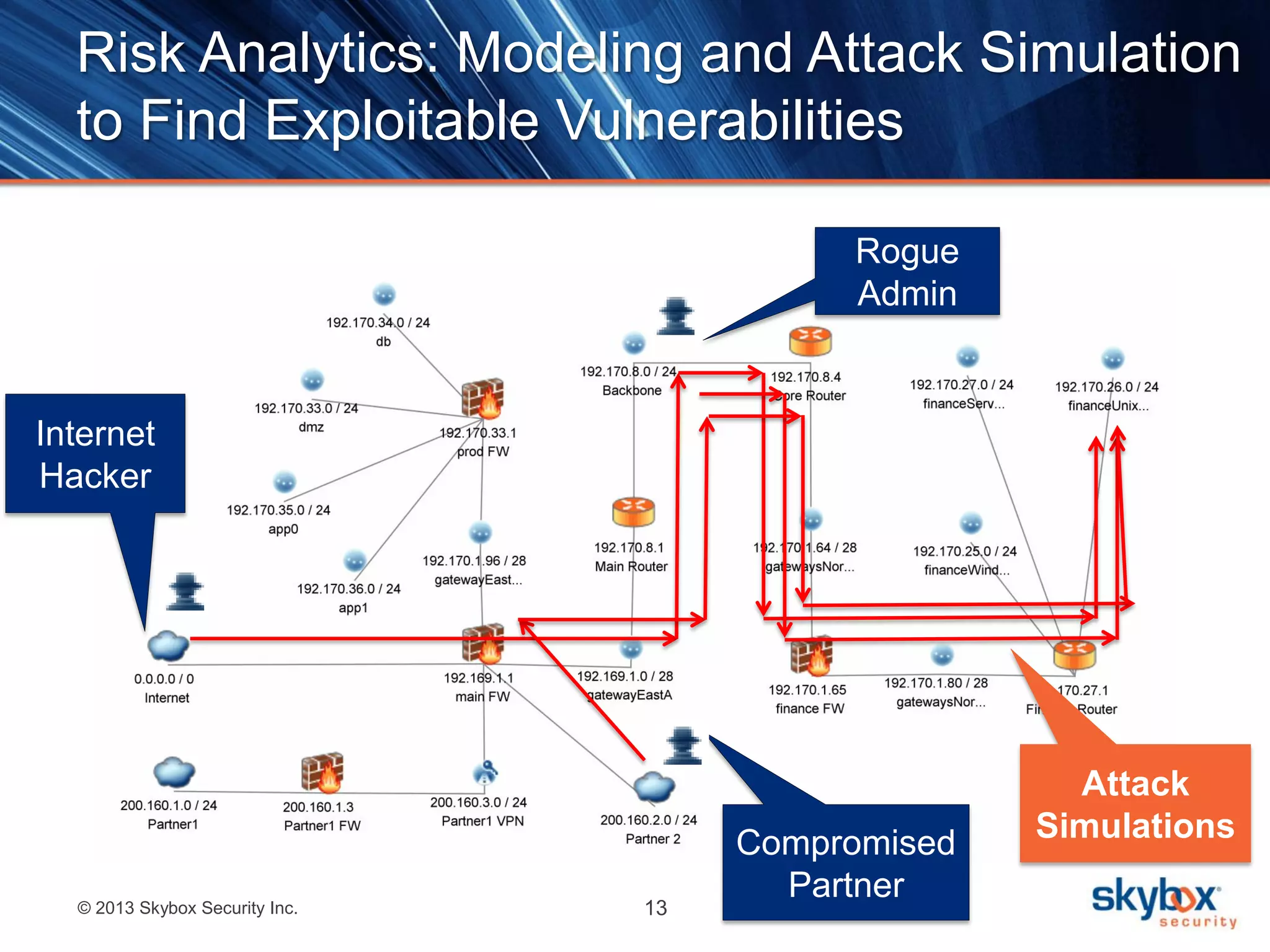
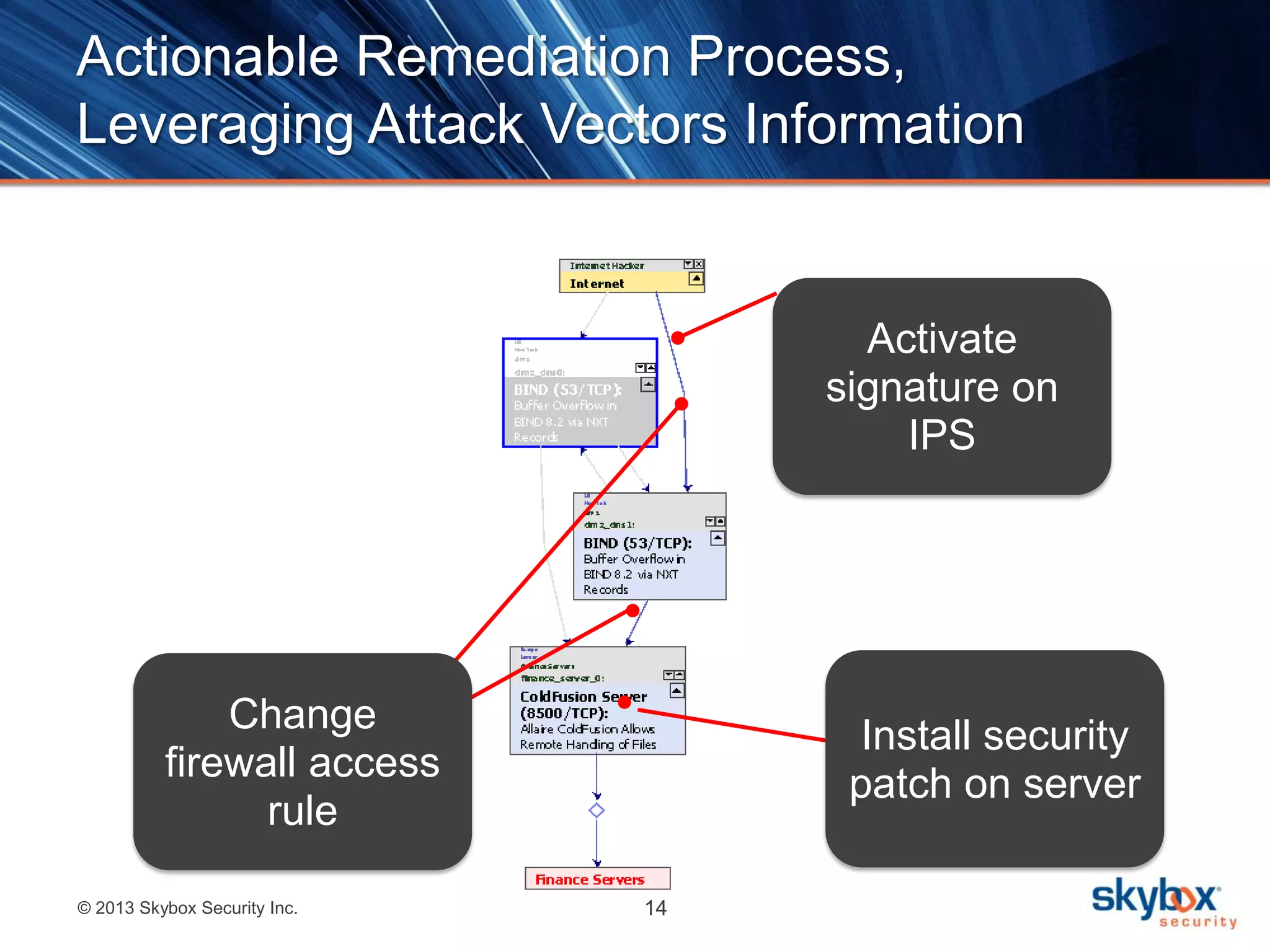
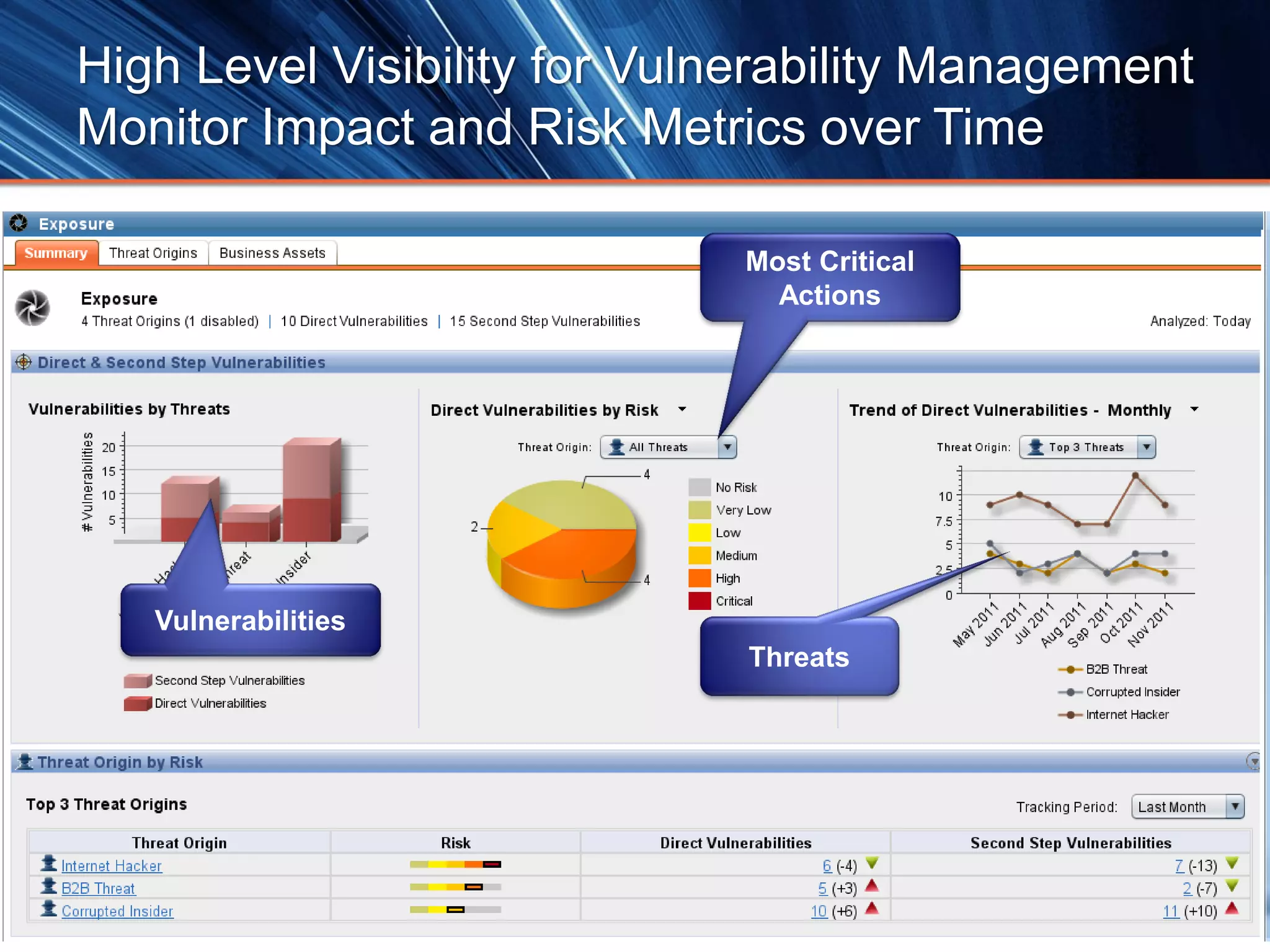
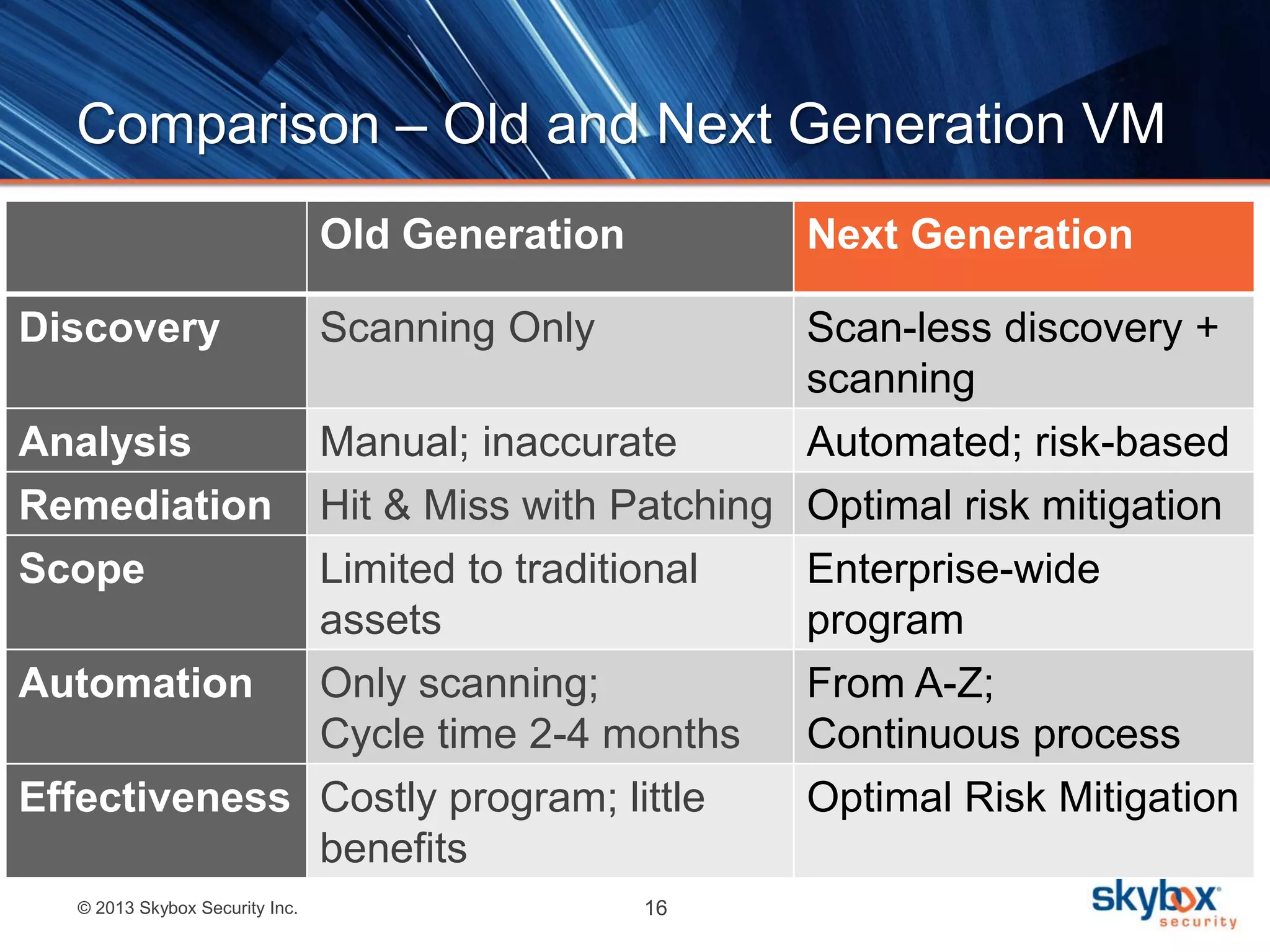
The document outlines best practices for next-generation vulnerability management, emphasizing the need for a shift from traditional methods due to rising risks and compliance demands. It highlights the importance of automated, non-disruptive discovery and risk-based prioritization in effectively addressing vulnerabilities. The key steps presented include understanding exploitable vulnerabilities, increasing assessment coverage and frequency, and leveraging risk analytics for informed decision-making.