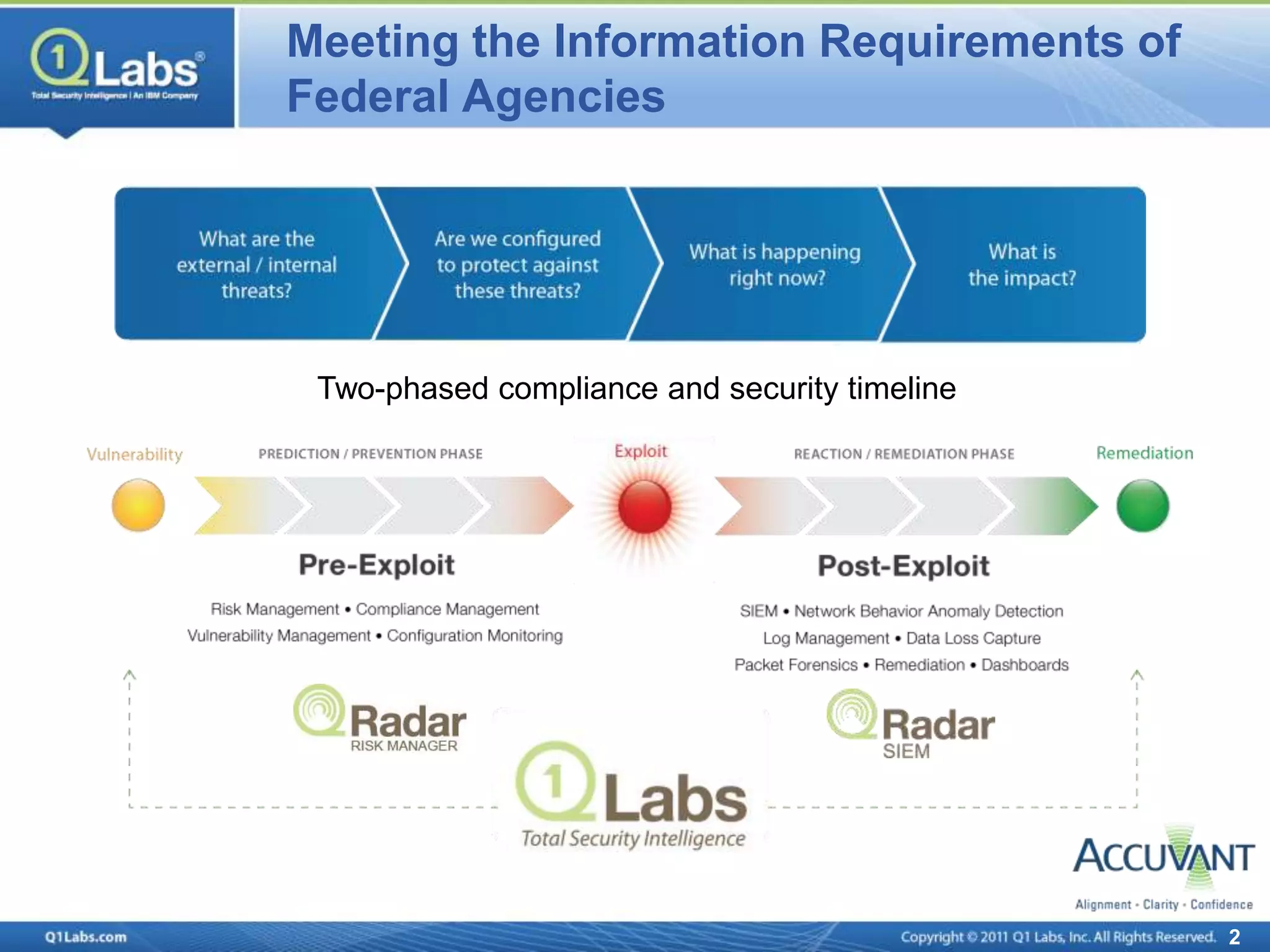
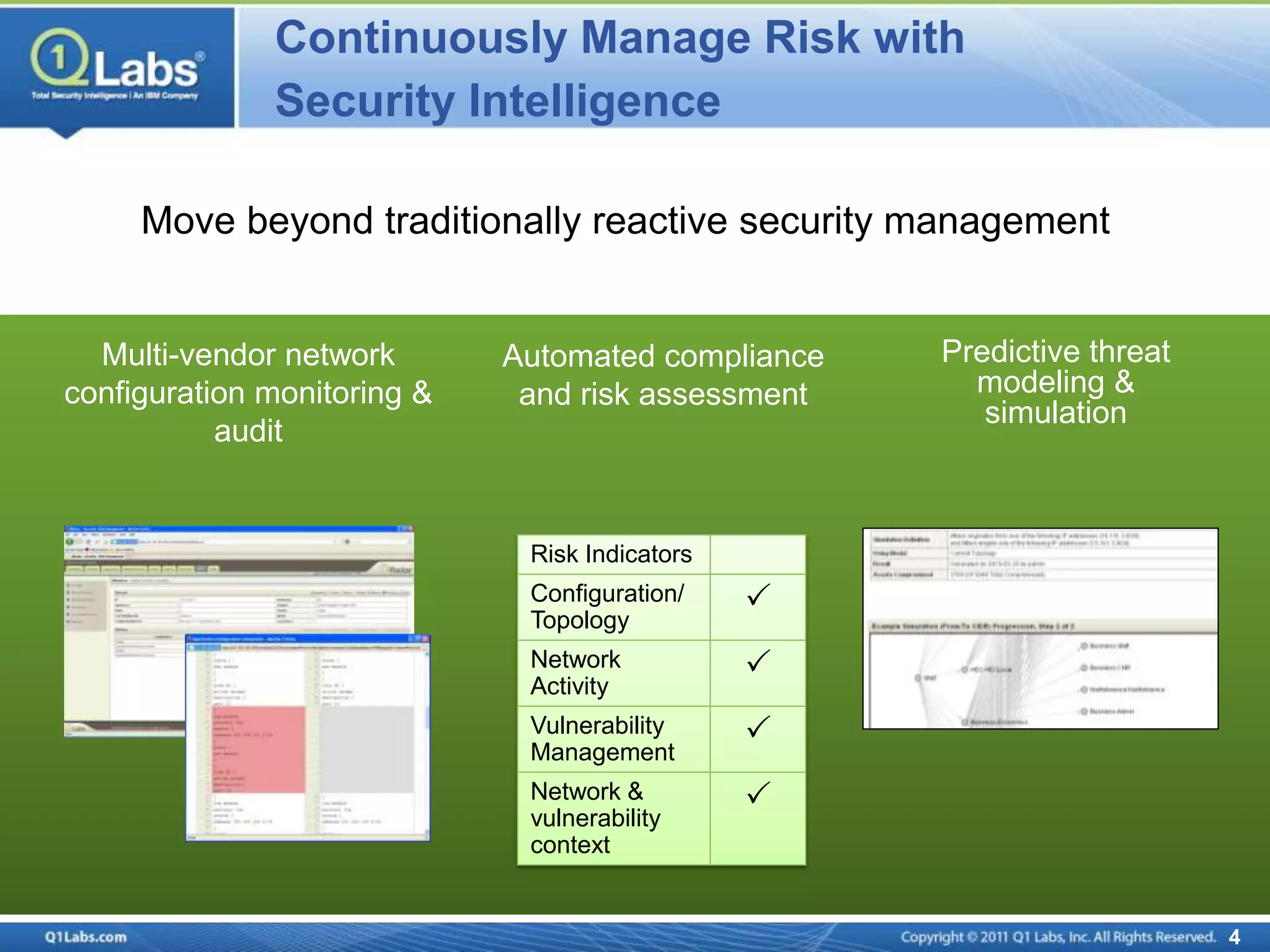
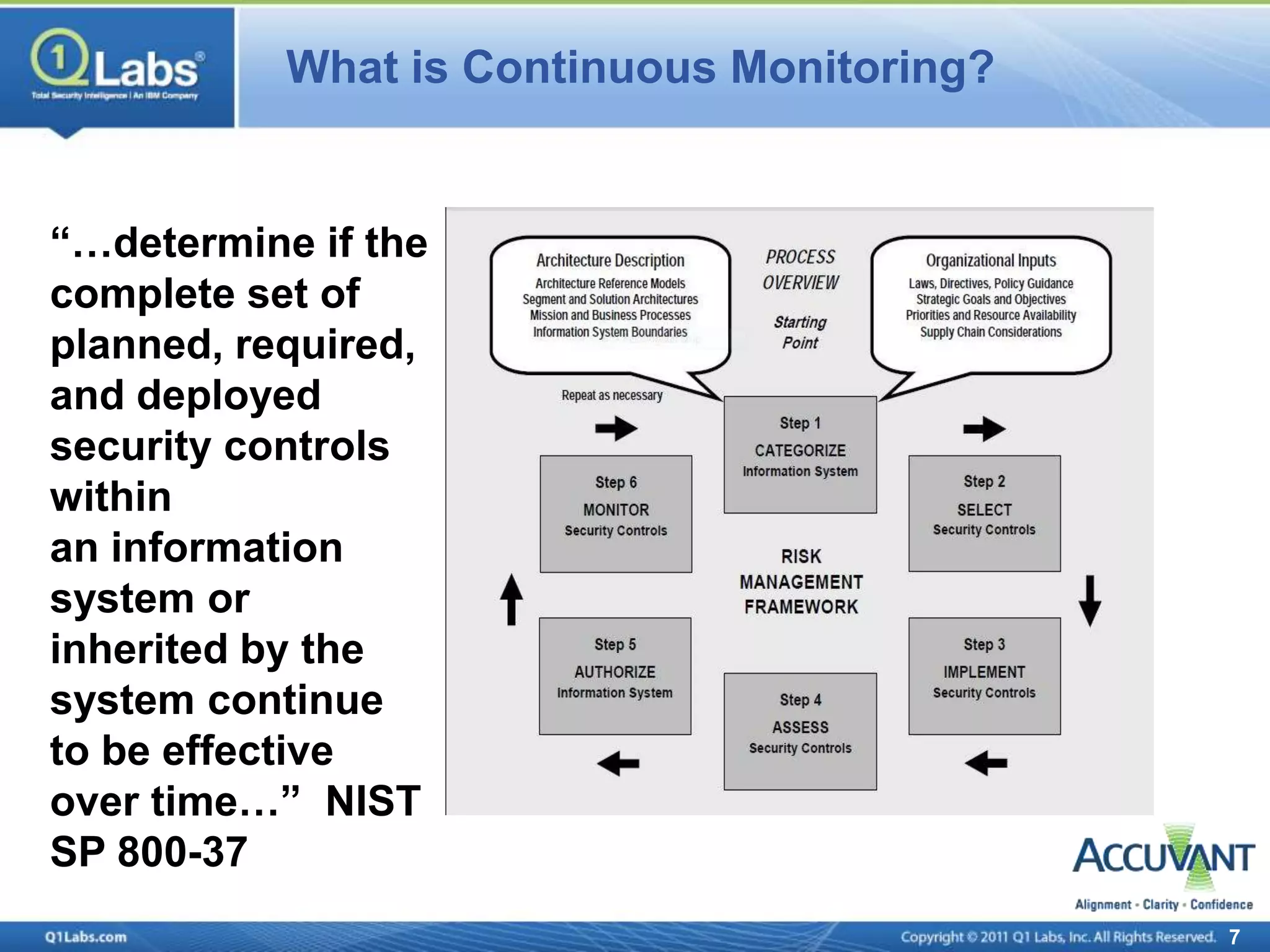
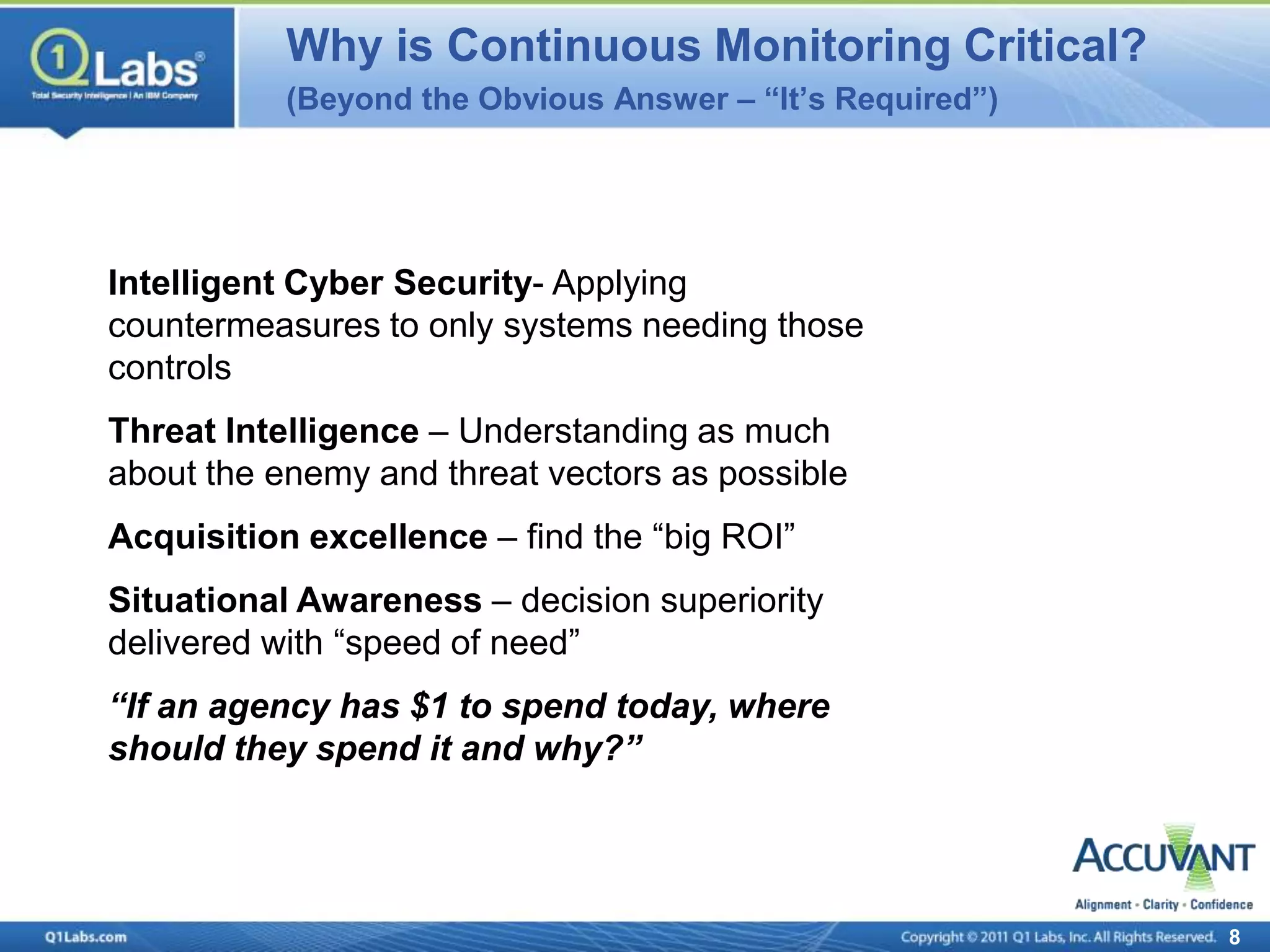
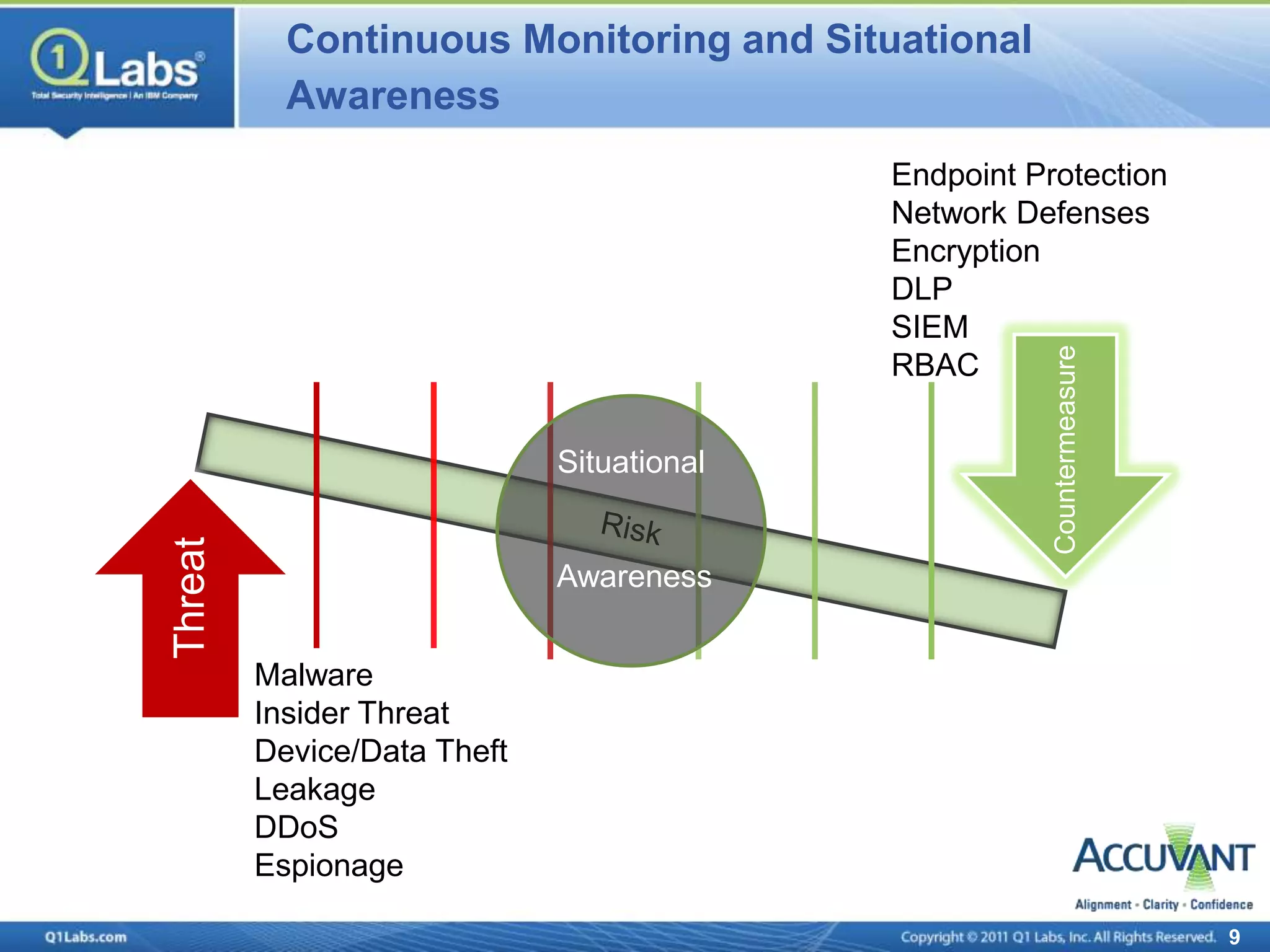
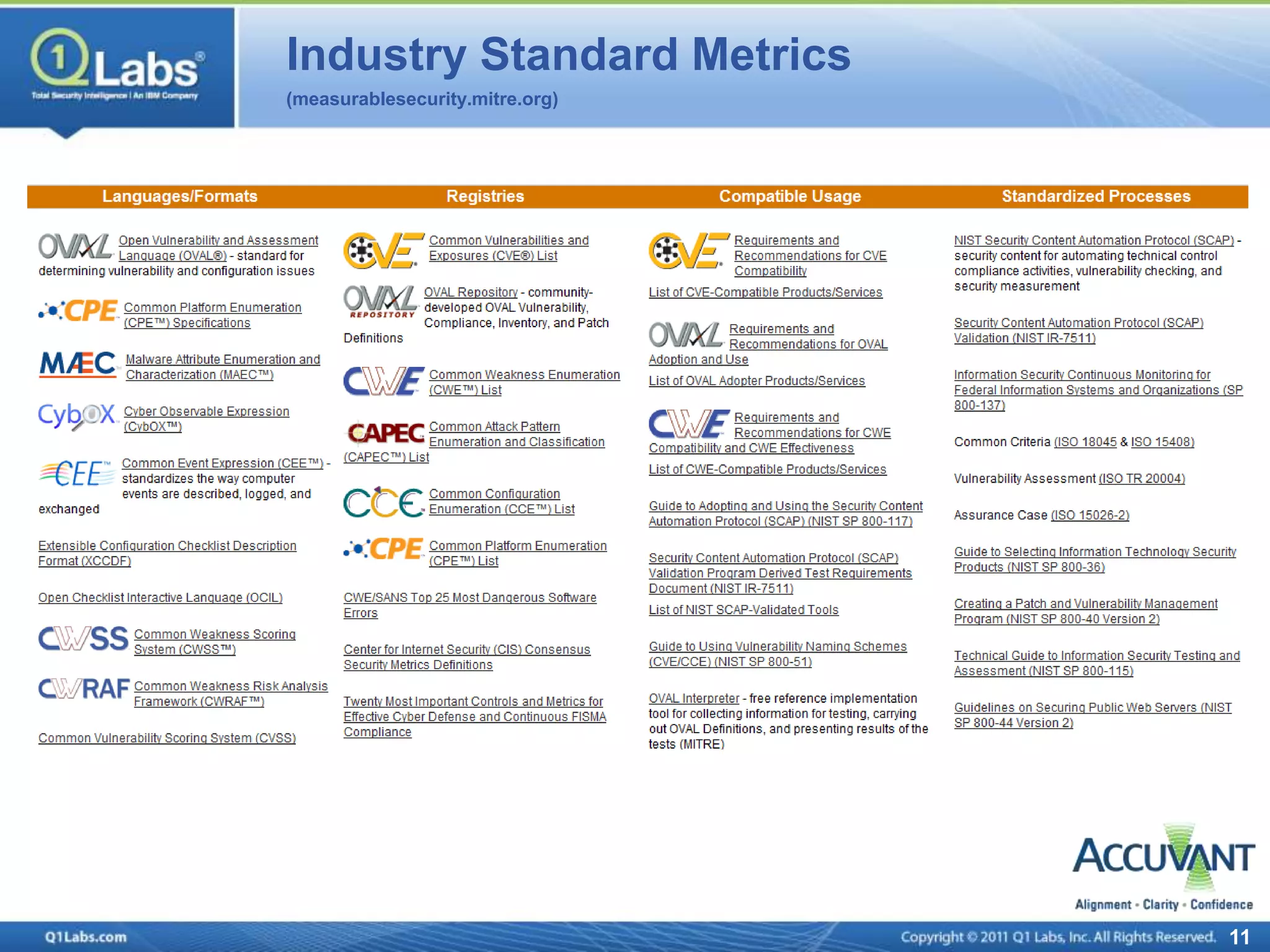
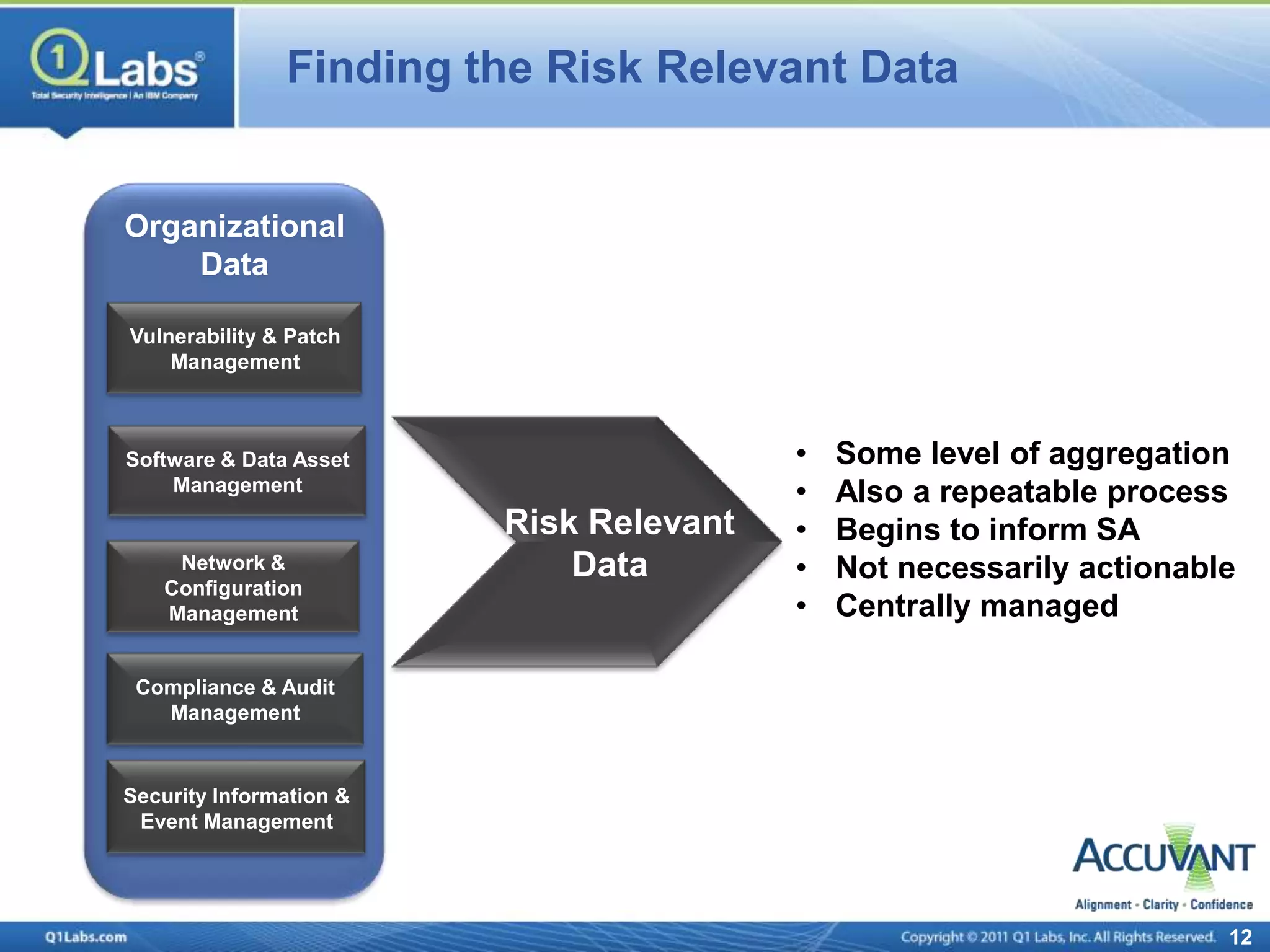
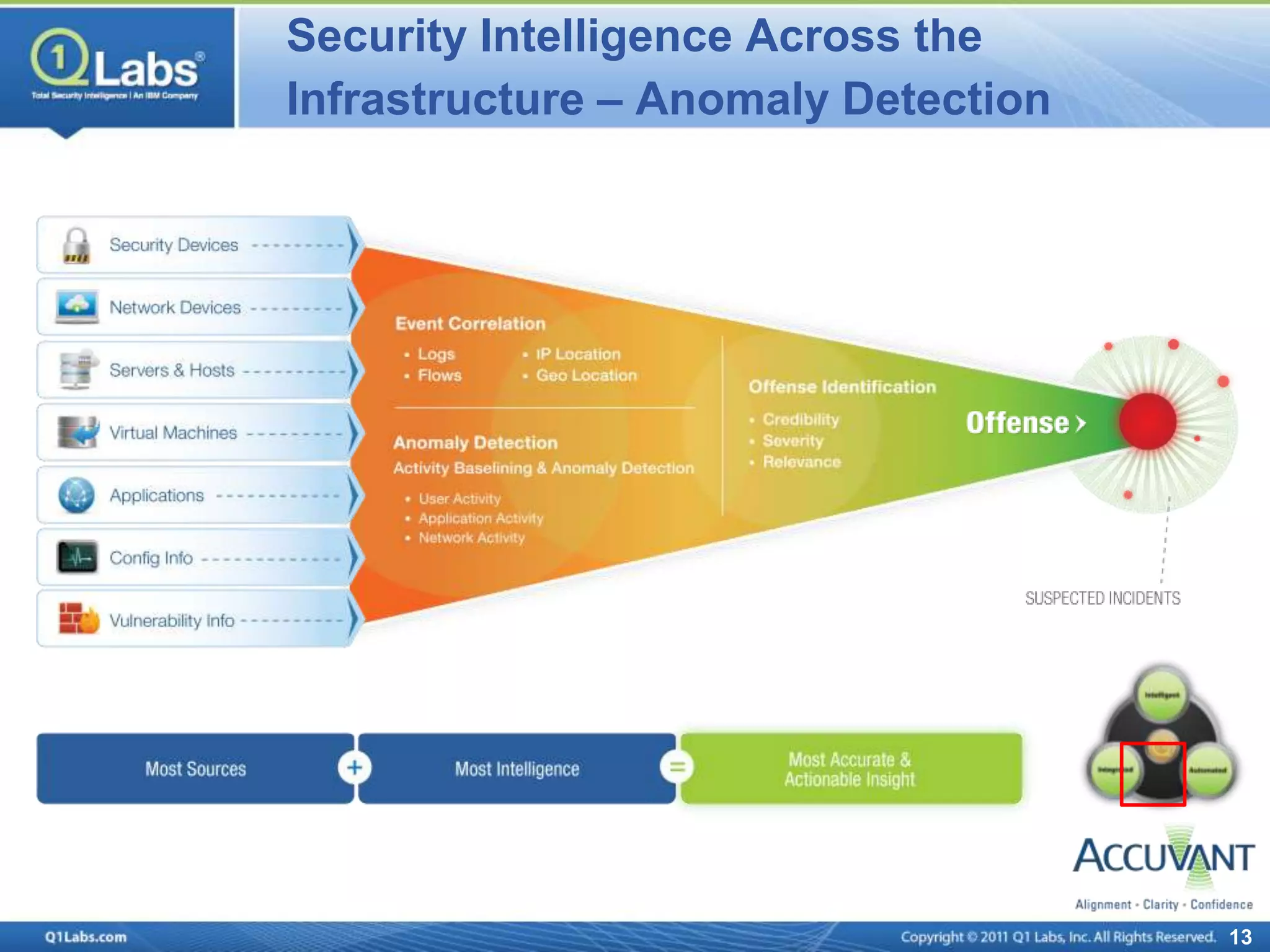
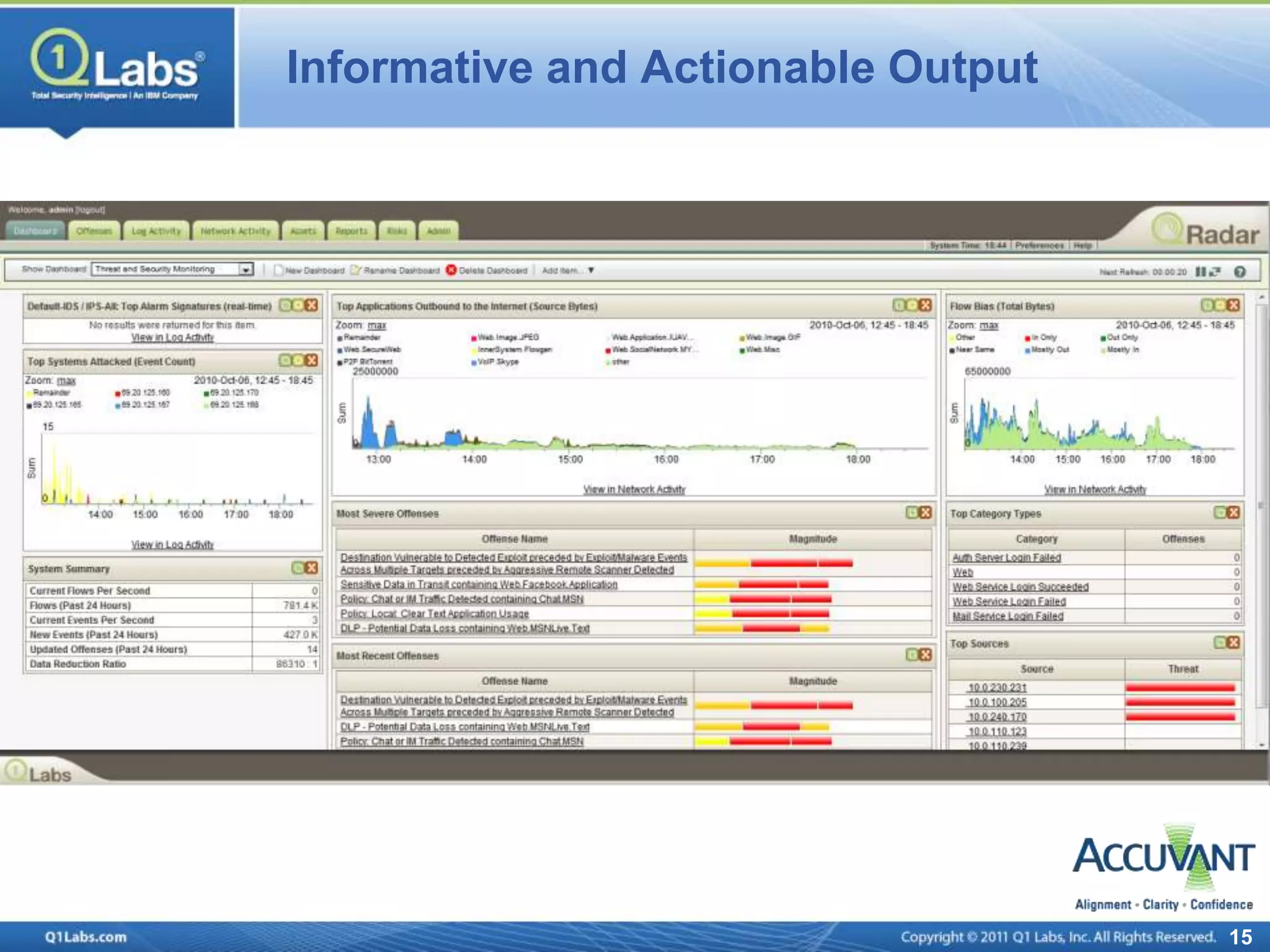
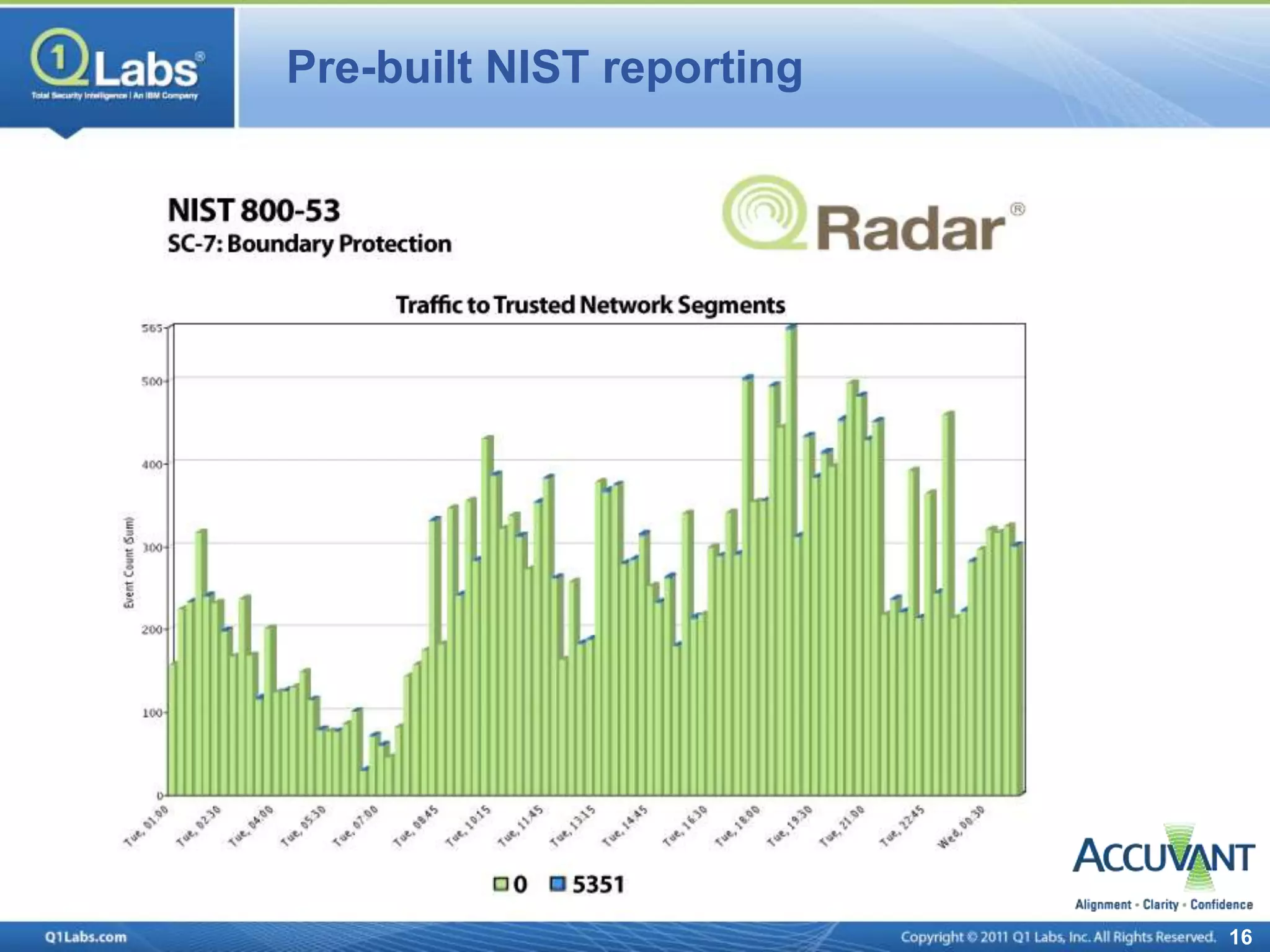
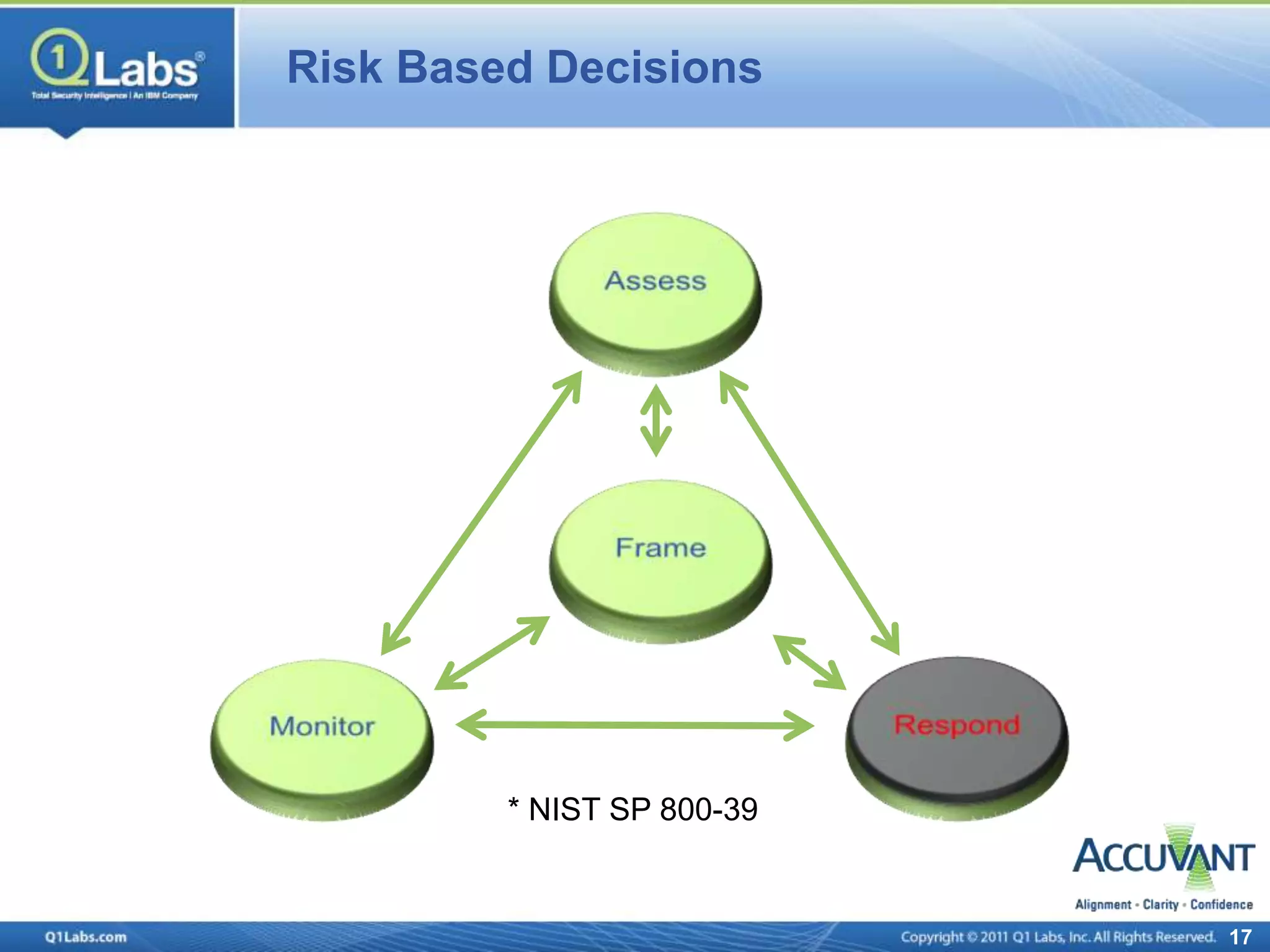
This document discusses continuous monitoring and real-time risk scoring. It describes how continuous monitoring can detect vulnerabilities and potential threats by monitoring network changes and comparing configurations to network activity. A two-phased compliance timeline is mentioned. Continuous monitoring provides a single console view of risk exposure needed to meet federal requirements. Metrics and risk-relevant data are discussed. The benefits of security intelligence across infrastructure for anomaly detection and actionable, informative outputs are presented.