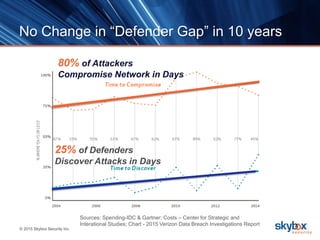
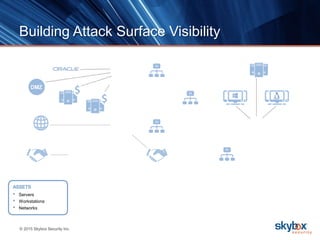
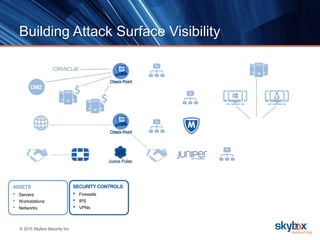
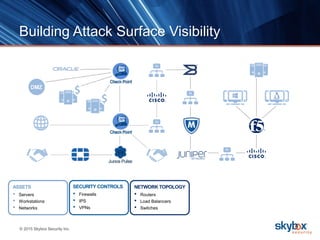
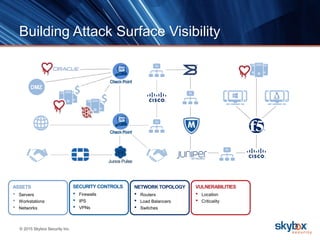
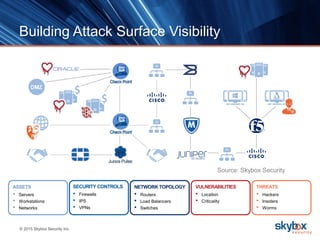
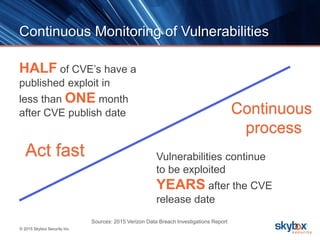
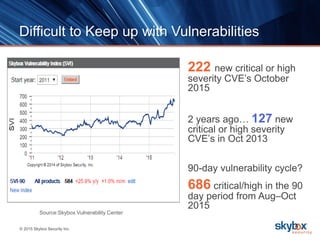
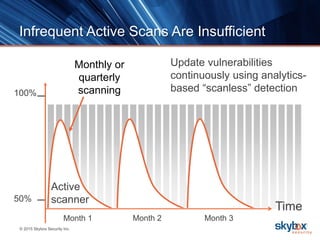
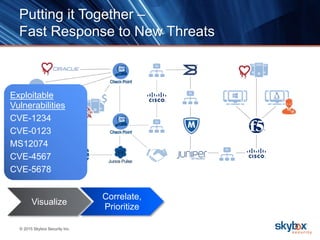
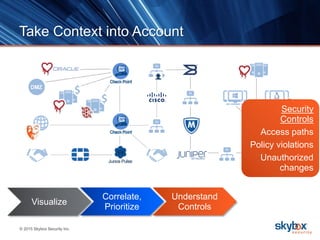
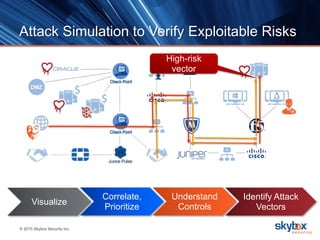
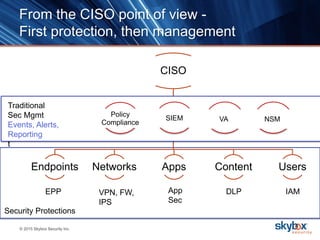
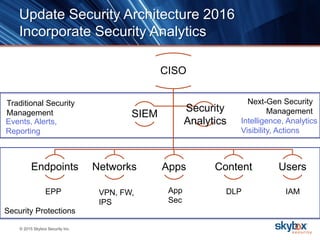
The document outlines key security trends for 2016, emphasizing the growing challenges faced by CISOs due to increased vulnerabilities from cloud and mobile technology, and the necessity for continuous monitoring and rapid response to threats. It discusses the high costs of cybercrime, the proliferation of security solutions, and the need for adaptive technologies amid complex networks. Recommendations include leveraging security analytics, improving visibility, and prioritizing threat monitoring to address the continuous compromise landscape.