This document provides instructions and information for using the Bro network security monitor and its associated tools. It discusses installing Bro from source and describes Bro's architecture and event-based model. It also explains how to use Bro tools like BroControl and inspect Bro logs. The document outlines how to write Bro scripts and filter network traffic. It demonstrates reading pcap files with Bro and communicating with Bro using the Broccoli library.



![Install Bro
Here using install-from-source way and steps to build and install Bro tools are described in below link. It also
lists required and optional dependencies for building/compiling Bro source.
https://www.bro.org/sphinx/install/install.html
All operations are done under the Linux distribution Ubuntu 14.04 LTS 64-bit.
1) Download a copy of Bro source archive from the official site shown as below and extract the archive.
https://www.bro.org/download/index.html
Or using GIT to retrieve Bro source:
git clone --recursive git://git.bro.org/bro
The version used in this document is v2.3.2 (bro-2.3.2.tar.gz)
2) Change directory to Bro source root folder (here using "/home/william/bro-2.3.2" for example), configure
building environment and make(compile). There may be auxiliary tools and libraries available in the aux/
sub-directory. Some of them will be automatically built and installed along with Bro.
cd /home/william/bro-2.3.2
./configure --prefix=/home/william/bro
[Note: Cause to that the execution of Bro tools needs root privileges mode, so I configure it to install tools
into a folder named "bro" in my home directory. If you do not use a folder for installation, it will create
folders needed for Bro under your home directory. The default installation path is /usr/local/bro]](https://image.slidesharecdn.com/usagenotesofthebro2-150331114344-conversion-gate01/85/Usage-Notes-of-The-Bro-2-2-2-3-6-320.jpg)
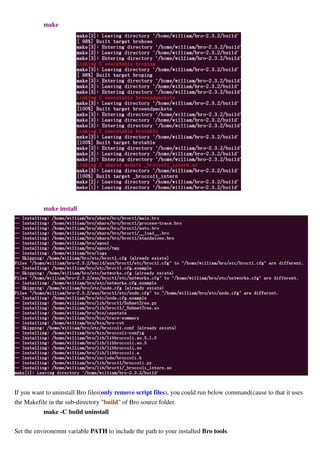

![# In Bro-Install-Path/etc/broctl.cfg, change the MailTo variable for email address to a desired recipient and
the LogRotationInterval variable to a desired log archival frequency/period value.
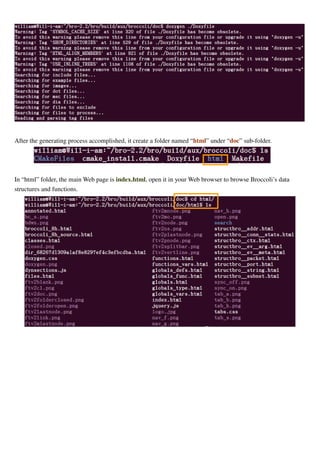
1) Start the BroControl shell, type the command:
$ broctrl
2) When you run BroControl shell for the first time, please perform an initial installation of the BroControl
configuration:
[BroControl] > install
3) Then start up a Bro instance:
[BroControl] > start
Note:
<I> If you encounter a error whose message is similar to below, it means you need root privileges
"error: cannot acquire lock: [Errno 13] Permission denied: '/usr/local/bro/spool/lock"
<II> If it shows message, "bro terminated immediately after starting", it means there have errors and](https://image.slidesharecdn.com/usagenotesofthebro2-150331114344-conversion-gate01/85/Usage-Notes-of-The-Bro-2-2-2-3-10-320.jpg)
![you could view the detail through the command "diag."
[BroControl] > diag
, or you could inspect the error log file “Bro-Install-Path/logs/current/stderr.log.”
<II> The user starting BroControl needs permission to capture network traffic. If you are not root, you
may need to grant further privileges to the account you’re using. Follow the question and answer of
the Bro's FAQ Web page, https://www.bro.org/documentation/faq.html :
When bro executable runs normally, you could use ps command to observe it.
To stop this Bro instance you would do:
Q: How can I capture packets as an unprivileged user?
A: Fully implemented since Linux kernel 2.6.24, capabilities are a way of parceling super user privileges into
distinct units.
Attach capabilities required to capture packets to the bro executable file like this:
sudo setcap cap_net_raw,cap_net_admin=eip /path/to/bro
where "bro" is a Bro executable tool.
Example:
sudo setcap cap_net_raw,cap_net_admin=eip /home/william/bro/bin/bro
Now any unprivileged user should have the capability to capture packets using Bro provided that they have the
traditional file permissions to read/execute the bro binary.](https://image.slidesharecdn.com/usagenotesofthebro2-150331114344-conversion-gate01/85/Usage-Notes-of-The-Bro-2-2-2-3-11-320.jpg)
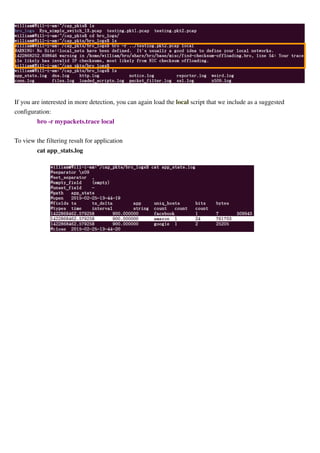
![[BroControl] > stop
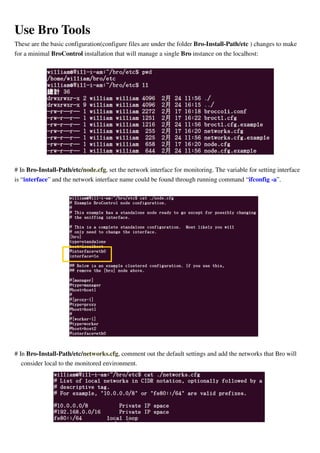
Inspect Log Files
By default, logs are written out in human-readable (ASCII) format and data is organized into columns
(tab-delimited).
Logs that are part of the current rotation interval are accumulated in "Bro-Install-Path/logs/current/" (if Bro is
not running, the directory will be empty).
By default, BroControl regularly takes all the logs from "Bro-Install-Path/current/" and archives them to a
directory named by date, e.g. Bro-Install-Path/logs/2011-10-06. For example:
The frequency at which this is done can be configured via the LogRotationInterval option in
Bro-Install-Path/etc/broctl.cfg.
Some logs are worth explicit mention:
conn.log Contains an entry for every connection seen on the wire, with basic properties
such as time and duration, originator and responder IP addresses, services and
ports, payload size, and much more. This log provides a comprehensive record
of the network’s activity.
notice.log Identifies specific activity that Bro recognizes as potentially interesting, odd, or
bad. In Bro-speak, such activity is called a “notice”.
Script Files
Bro includes an event-driven scripting language that provides the primary means for an organization to extend](https://image.slidesharecdn.com/usagenotesofthebro2-150331114344-conversion-gate01/85/Usage-Notes-of-The-Bro-2-2-2-3-12-320.jpg)


![Communicate With Bro System By Programming
Q: What is Broccoli?
A: BRO Client COmmunications LIbrary.
It allows you to write applications that speak the communication protocol of the Bro intrusion detection system
for exchanging Bro events with external programs. Broccoli is free software under terms of the BSD license as
given in the COPYING file distributed with its source code.
From my experiment result of using Bro v2.3 Broccoli and the below link, I changed to use the version of
Broccoli of Bro v2.2.
http://bro.bro-ids.narkive.com/XaJeX1aM/broccoli-not-processing-events
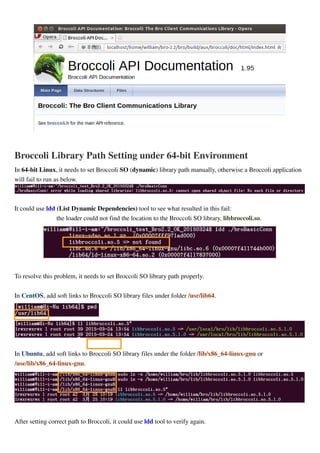
Default Listen Port Number for Broccoli
The default port number for listening Broccoli connecting request is 47760 and it could be confirmed through
running netstat tool:
netstat -ant
If you want to change the port number, it could change the port number value in the Python file “options.py”
under Bro installation path.
After changing the port number, run “broctl” to invoke Bro controller, execute “install” after prompt
“[BroControl] >” to re-generate configuration file and then execute “restart” to restart Bro daemon.
Using netstat tool to verify if the port number is what you set.
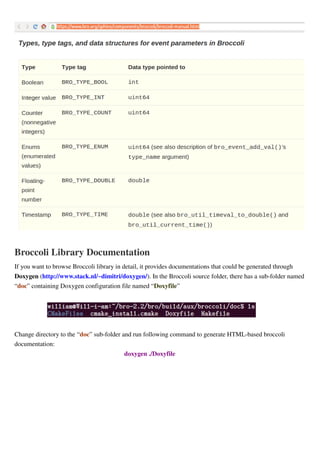
Data Type Mapping between Bro Script and Broccoli Program
When you want to test an event provided by Bro scripts(.bro file) in program, it needs to convert data type of
parameters in event handler of Bro script. Bro official site provides this mapping shown as below:](https://image.slidesharecdn.com/usagenotesofthebro2-150331114344-conversion-gate01/85/Usage-Notes-of-The-Bro-2-2-2-3-17-320.jpg)