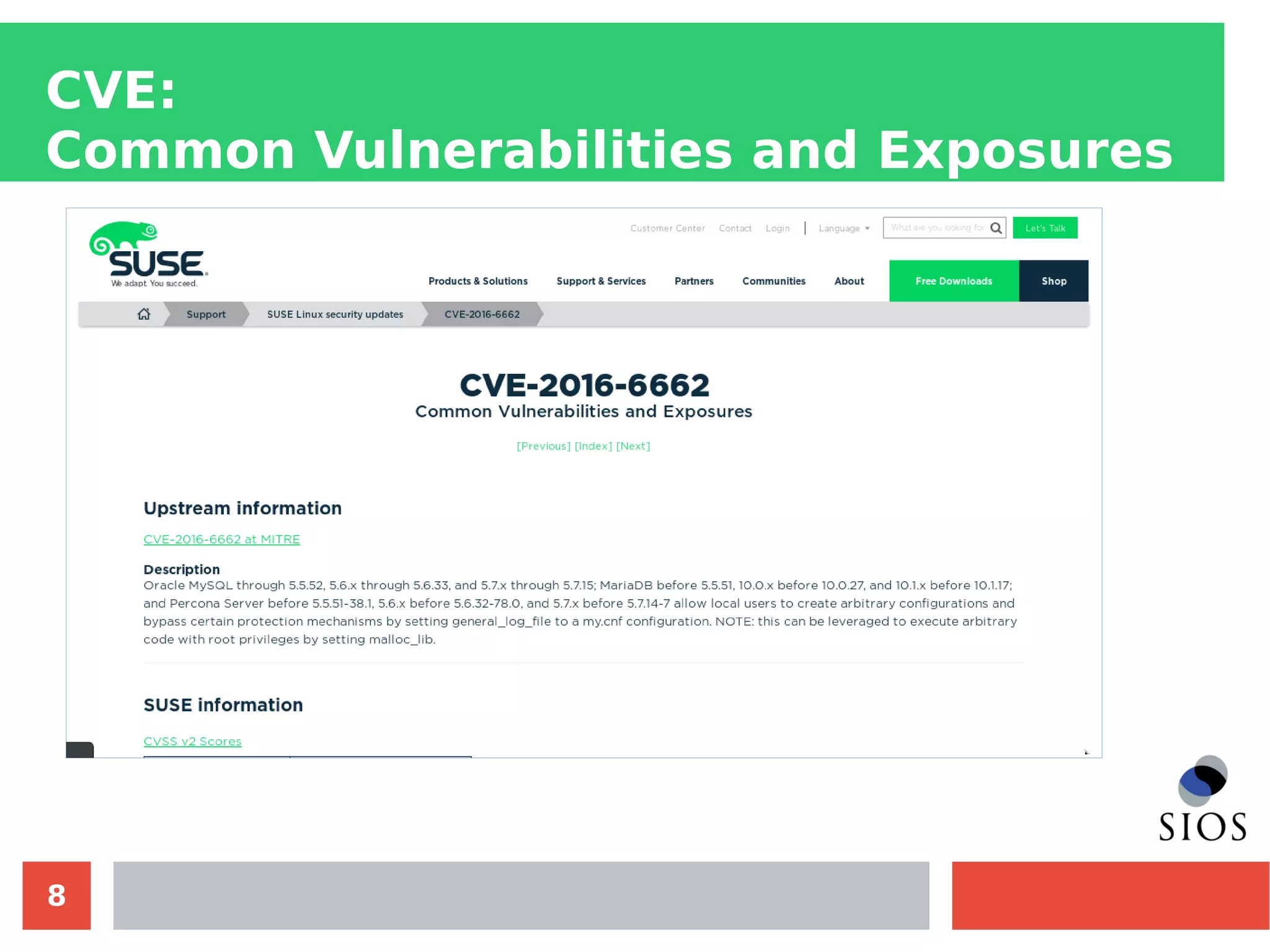
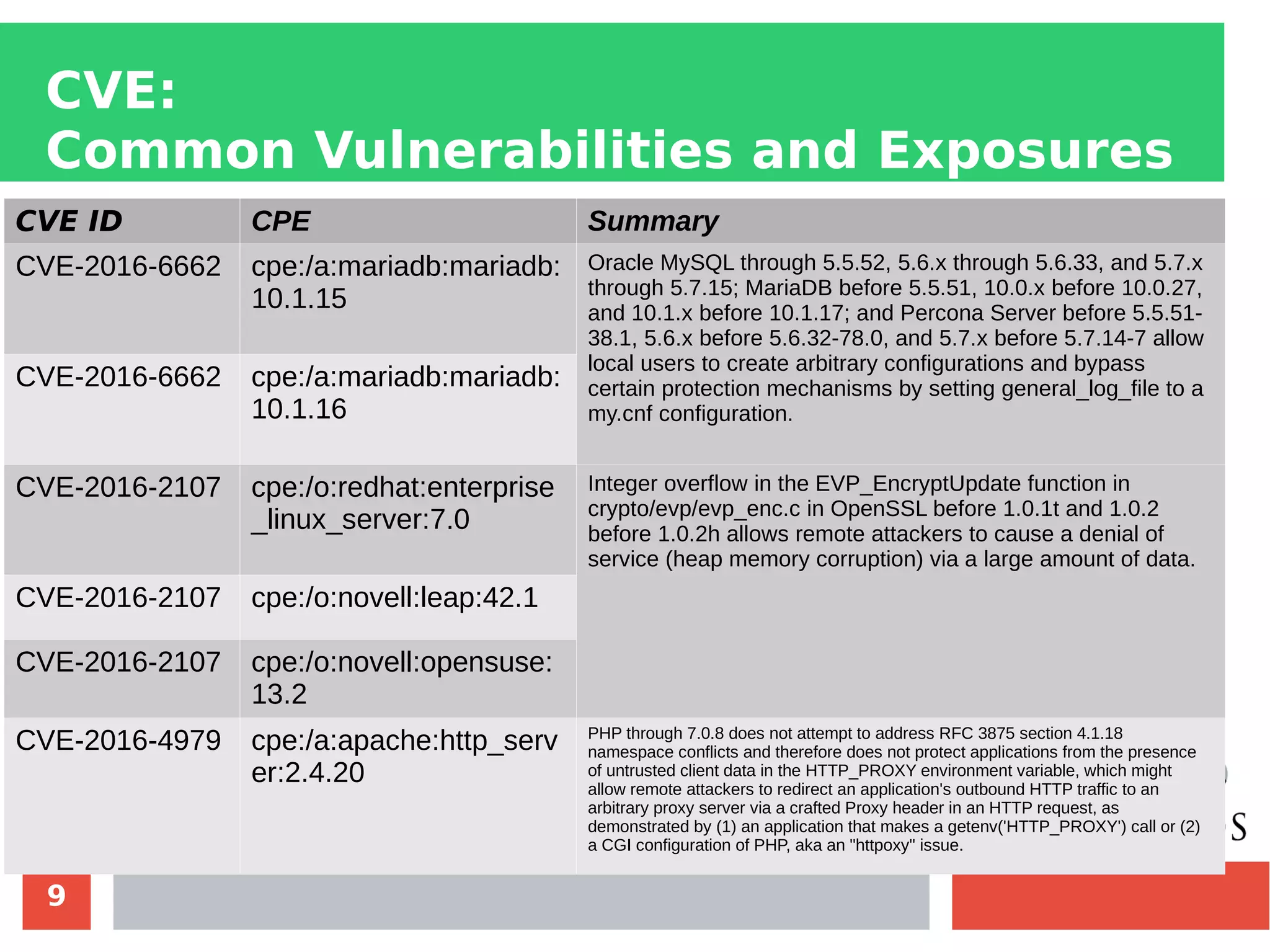
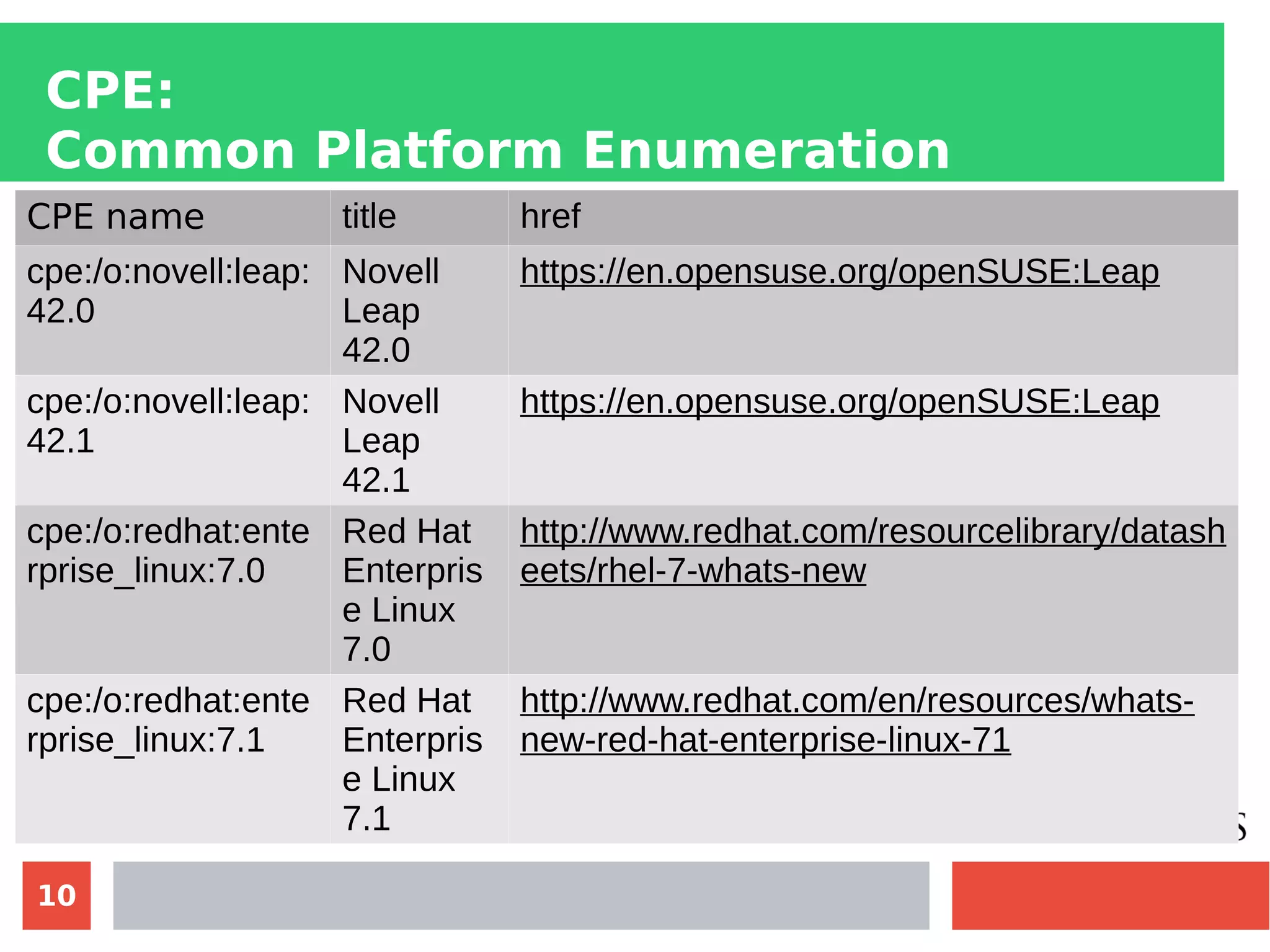
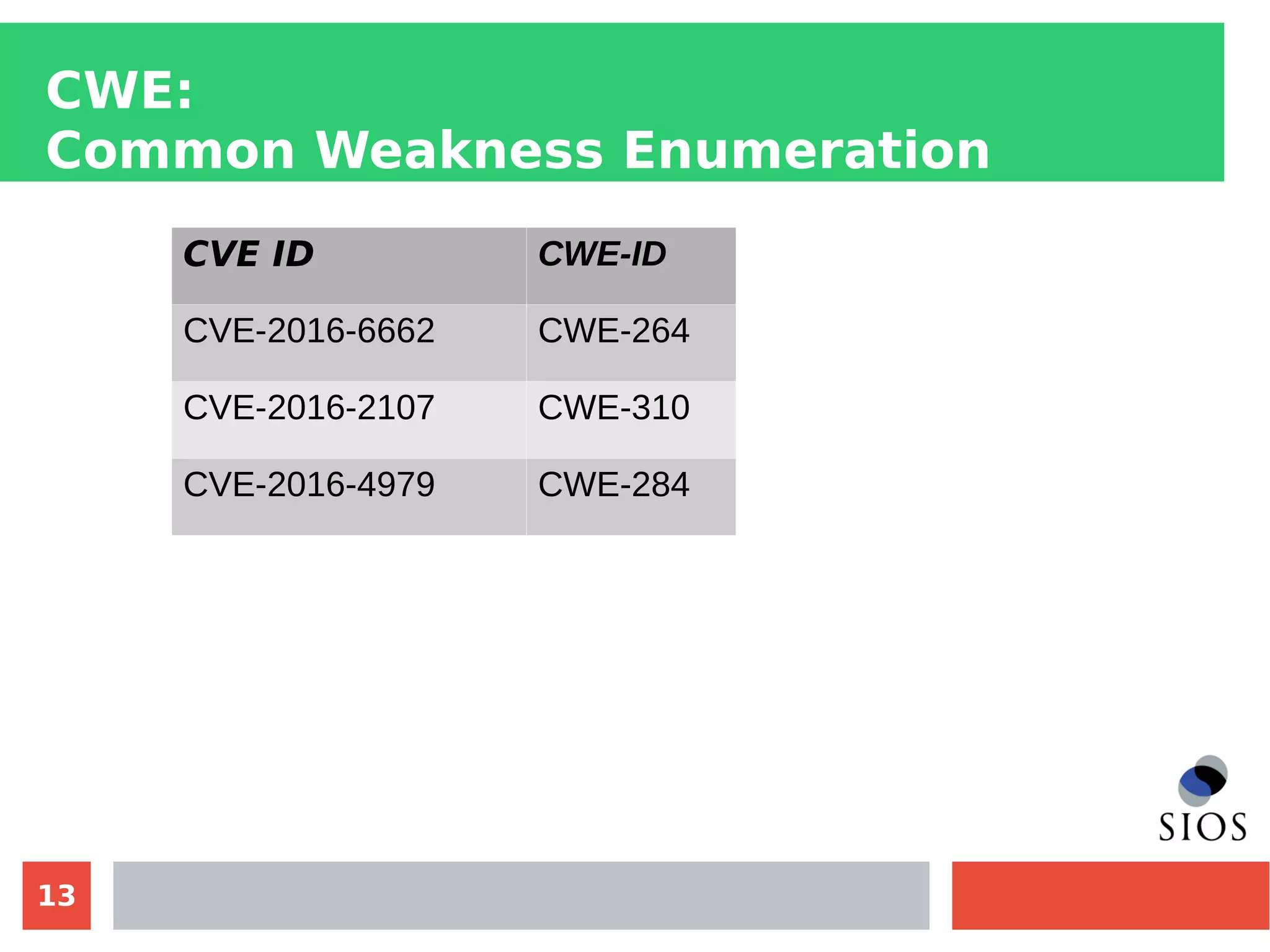
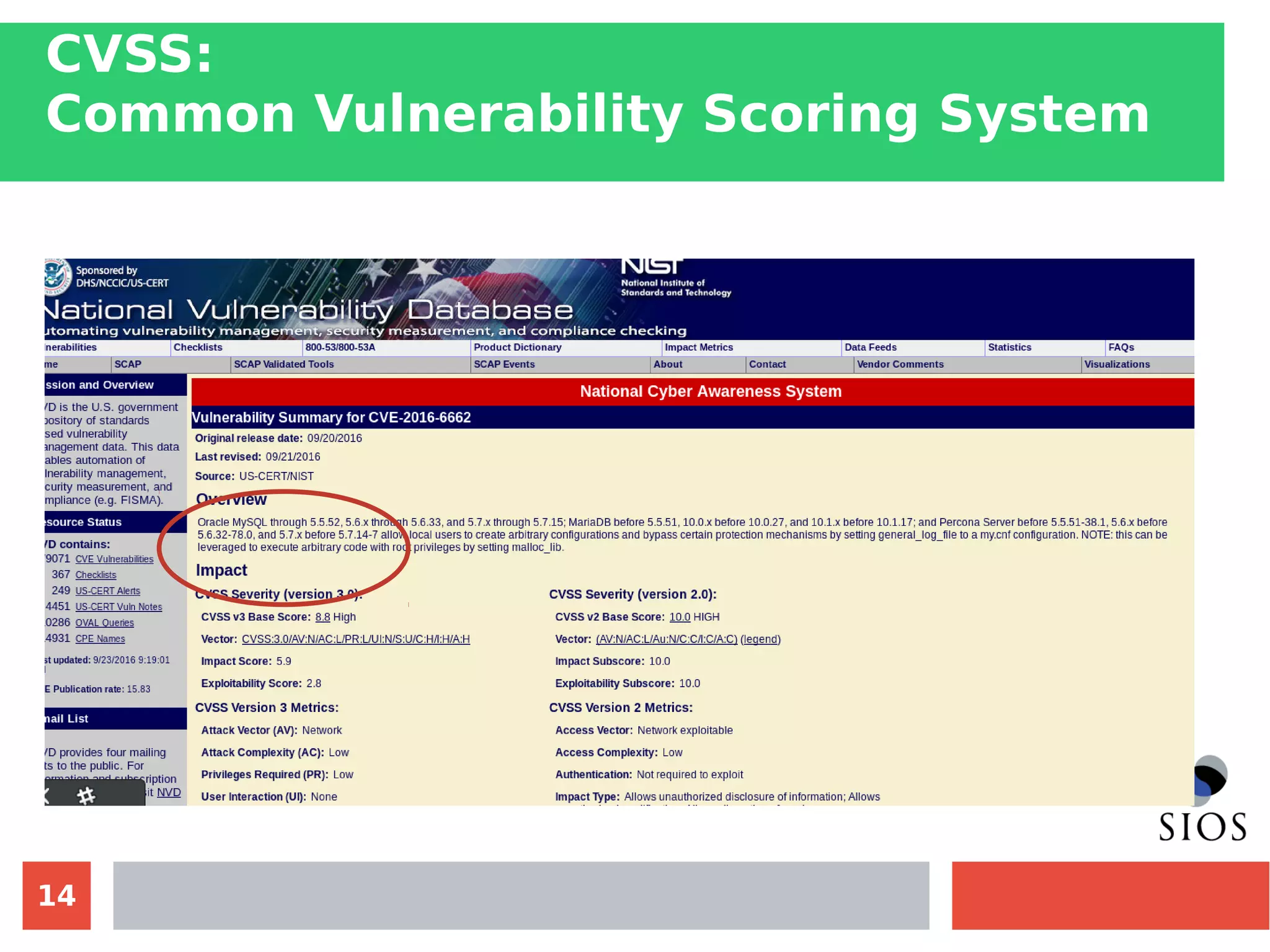
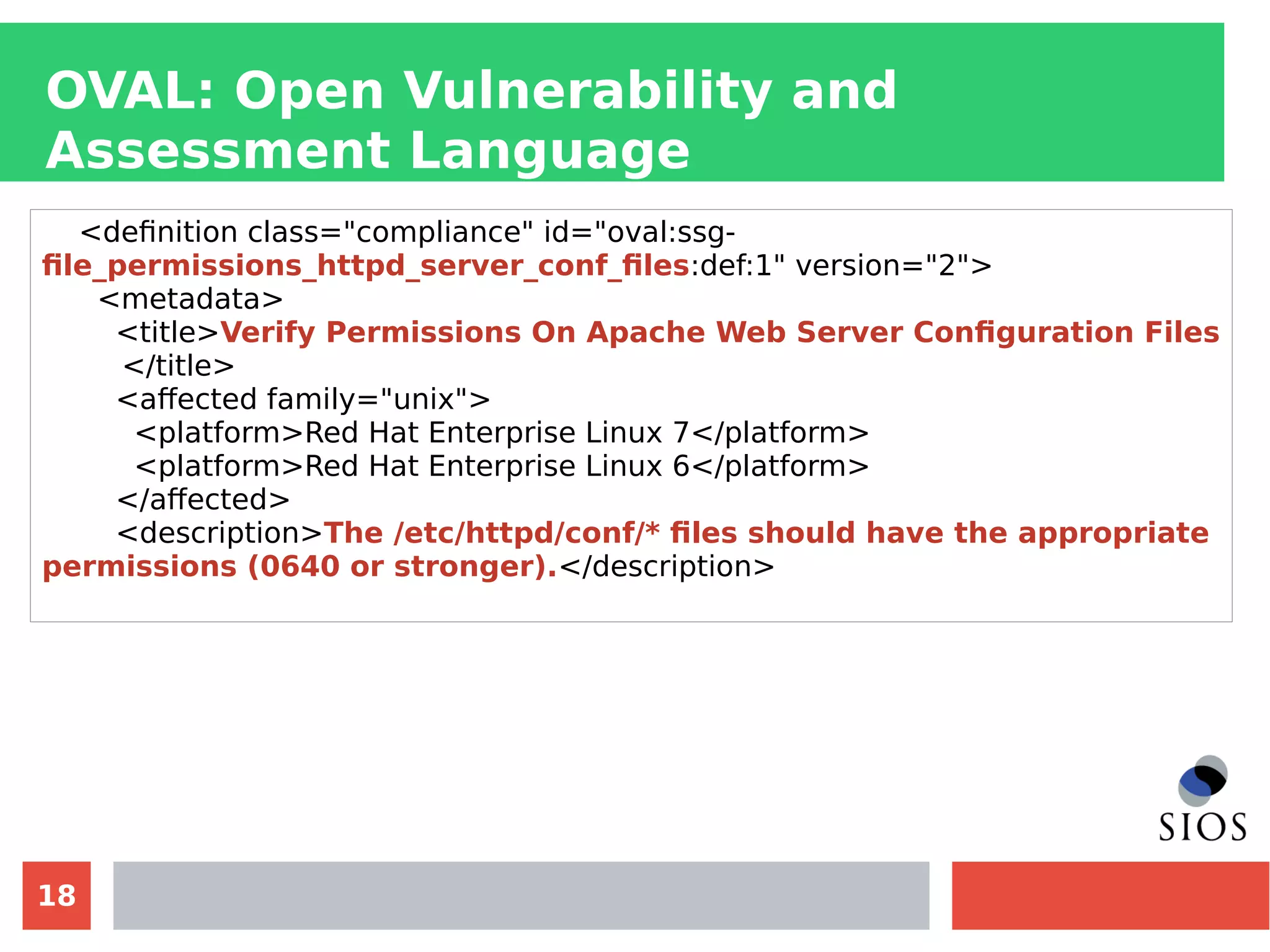
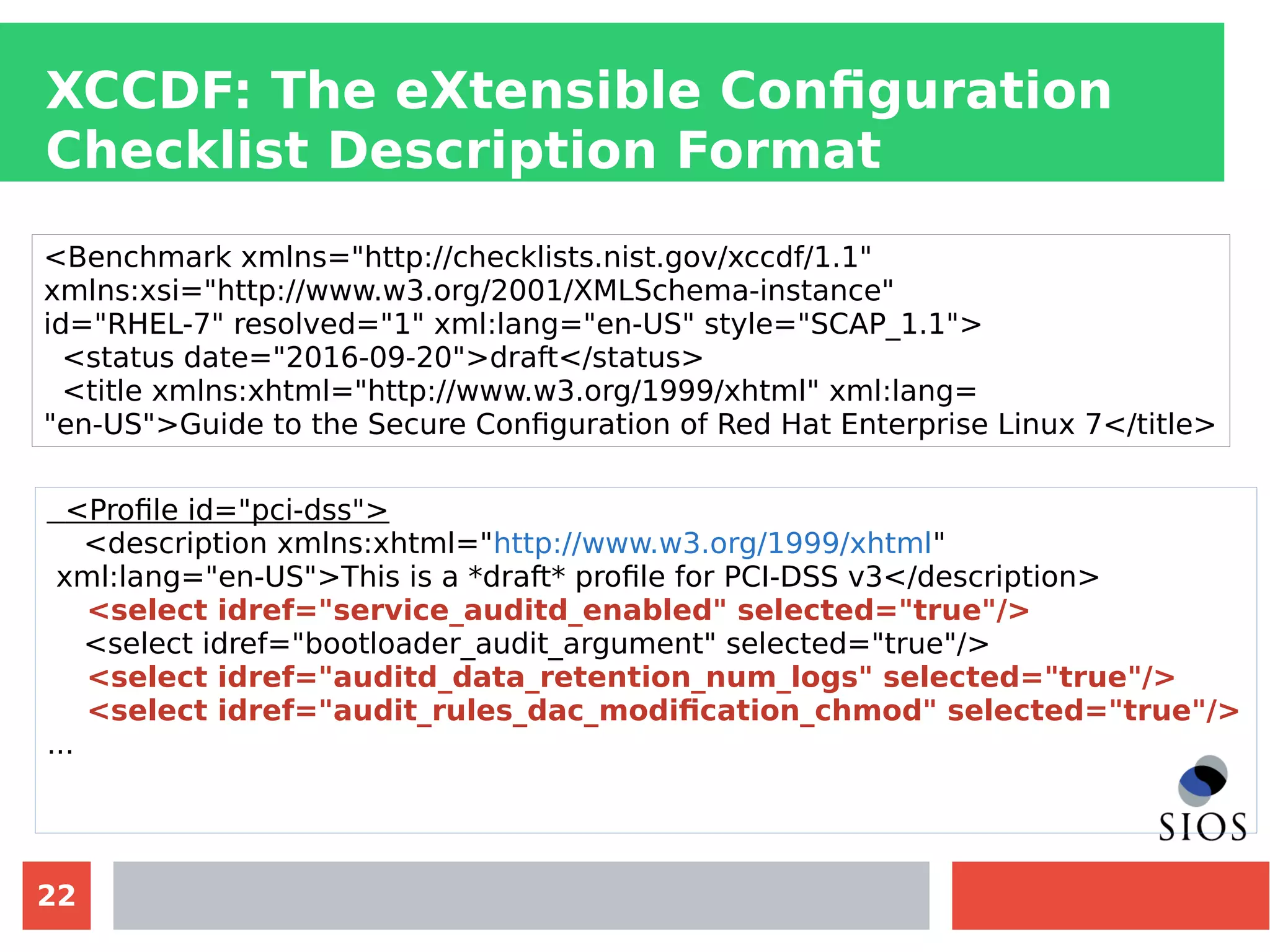
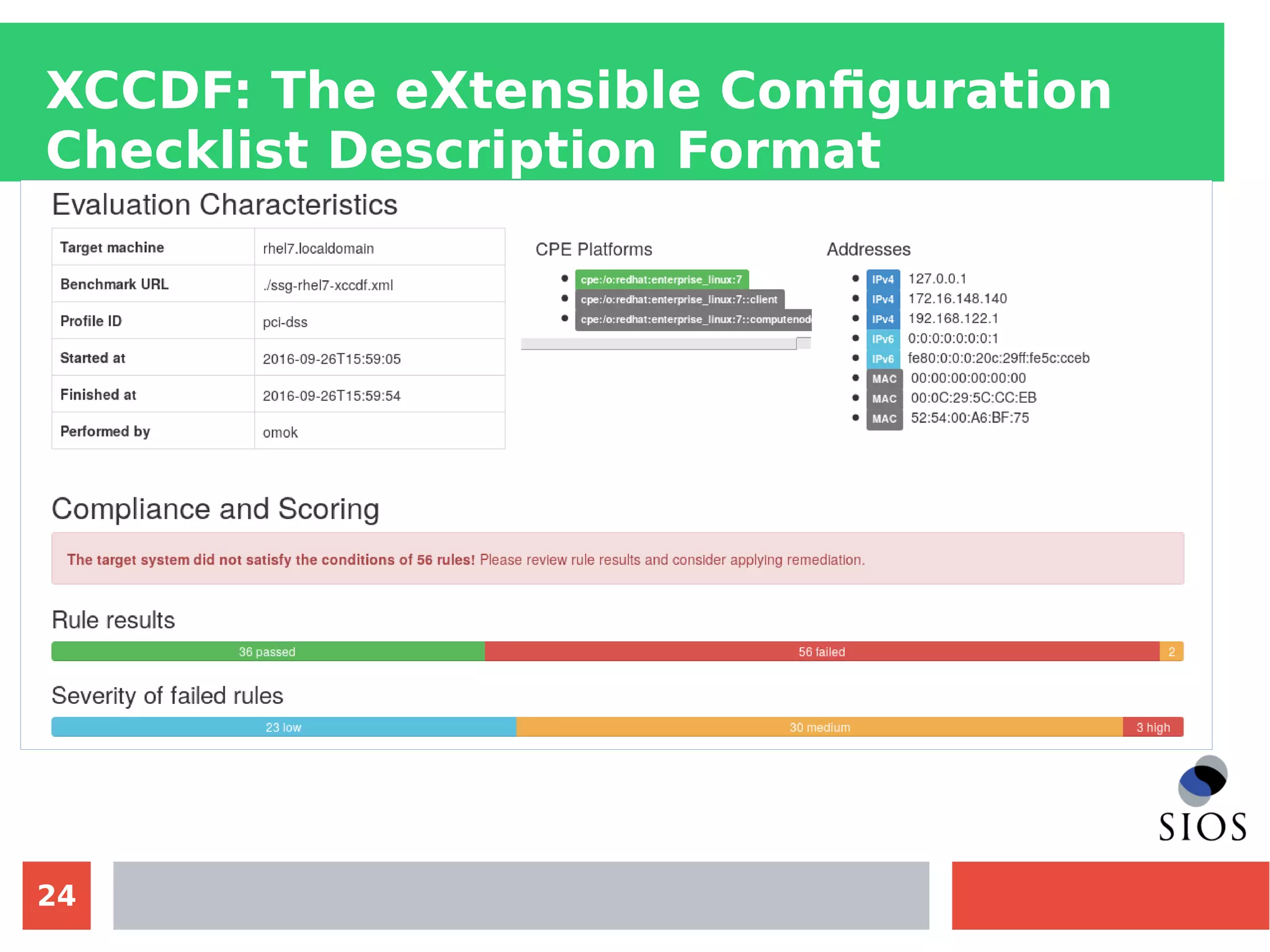
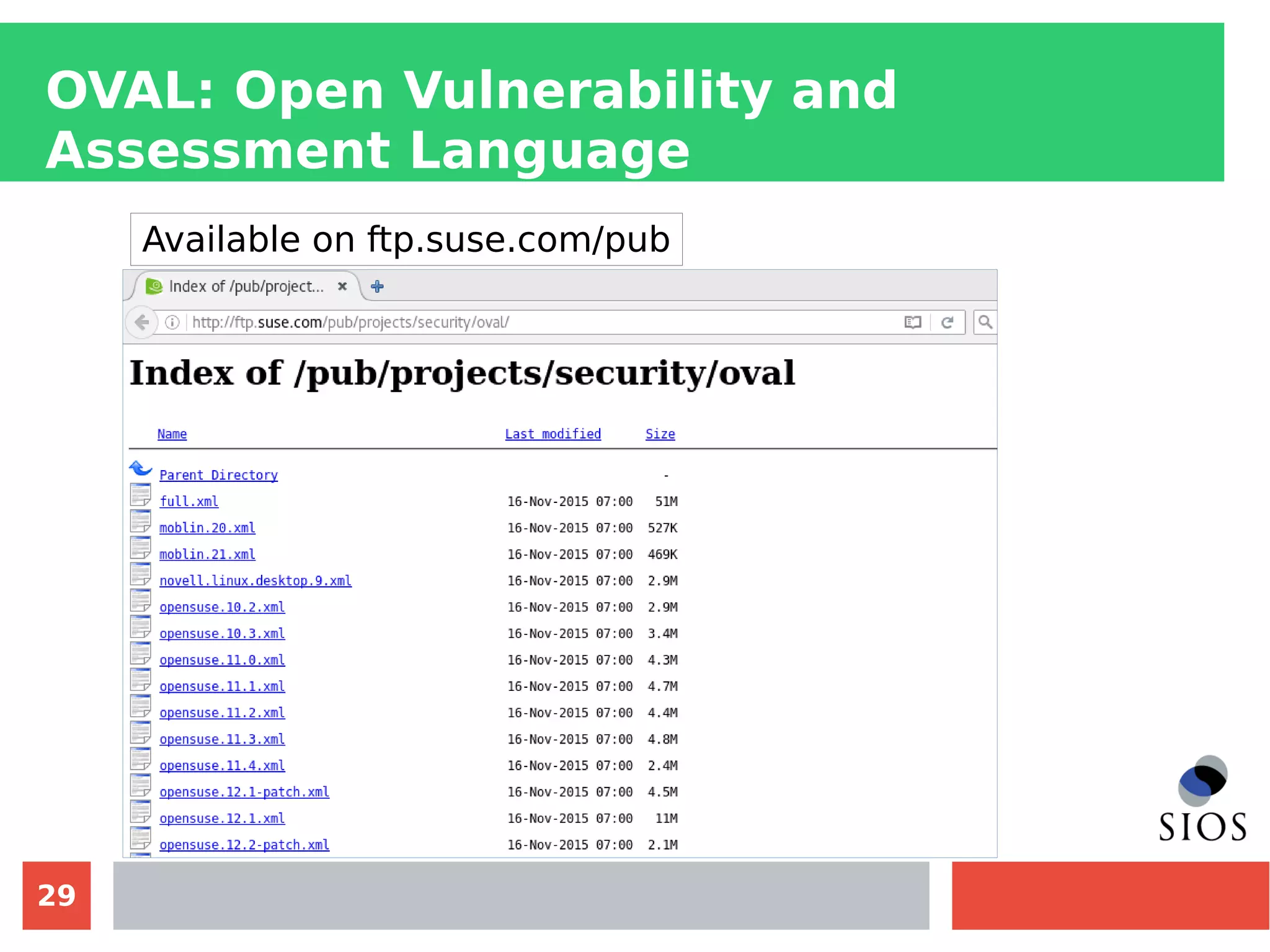
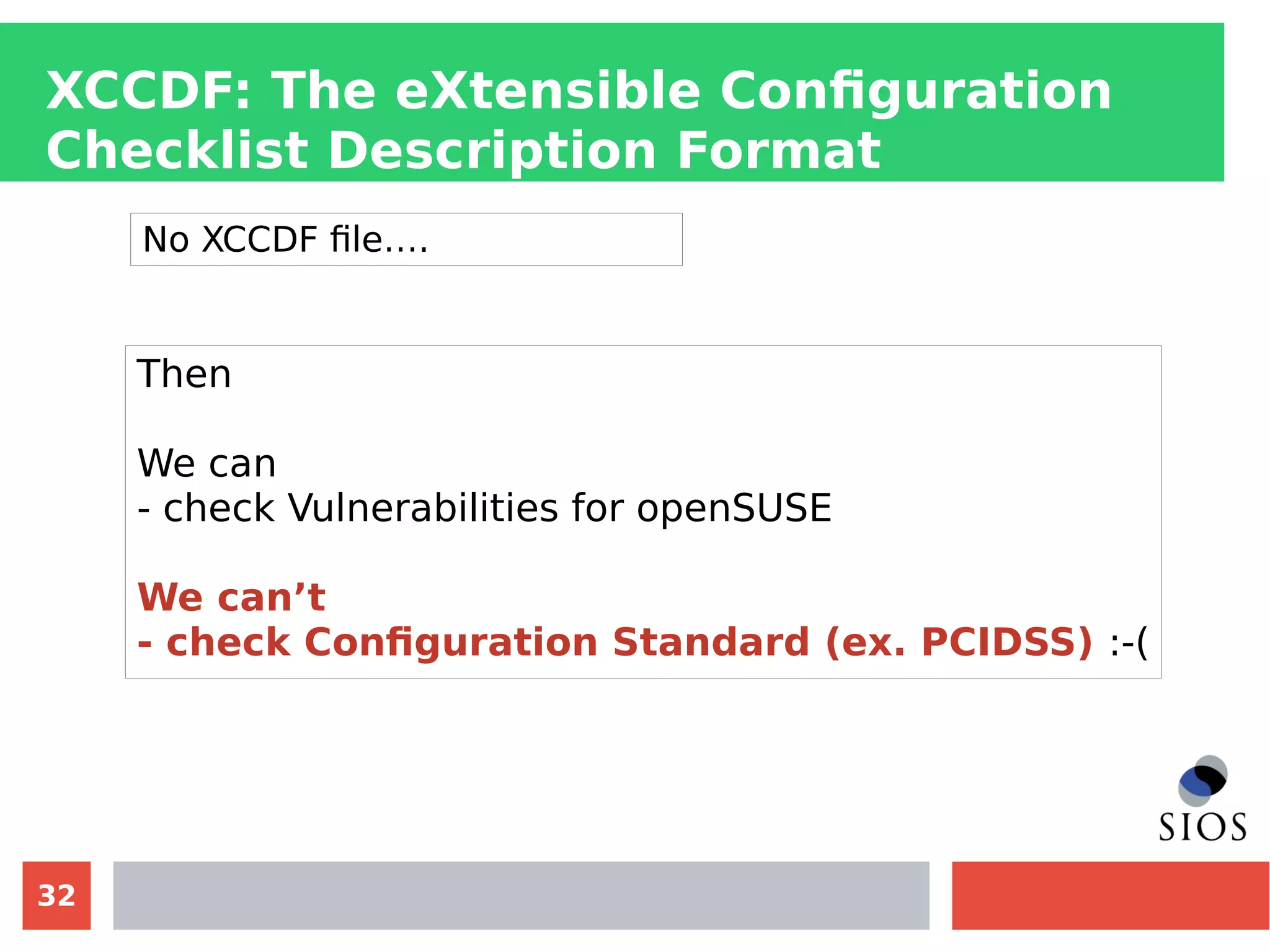
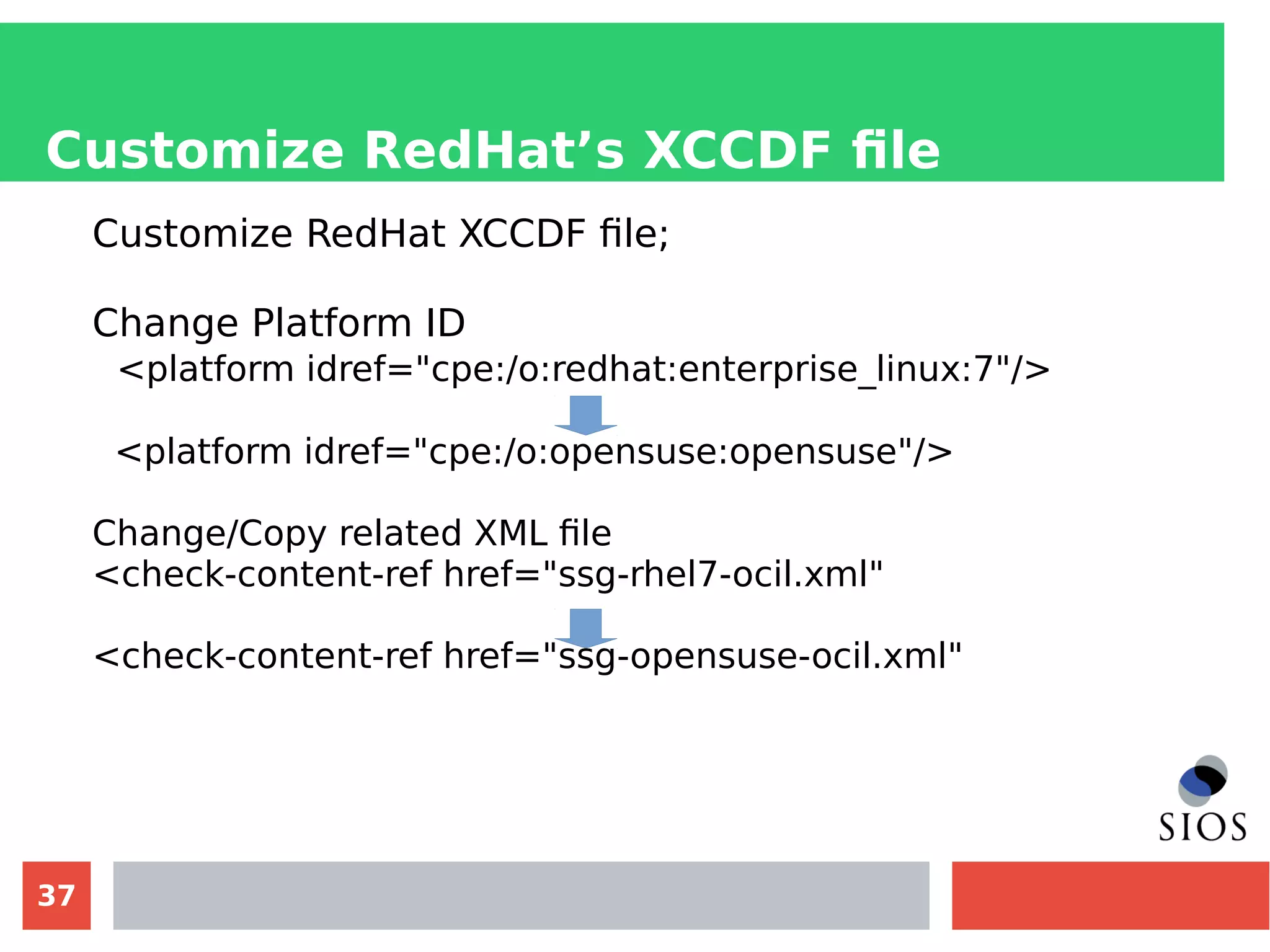
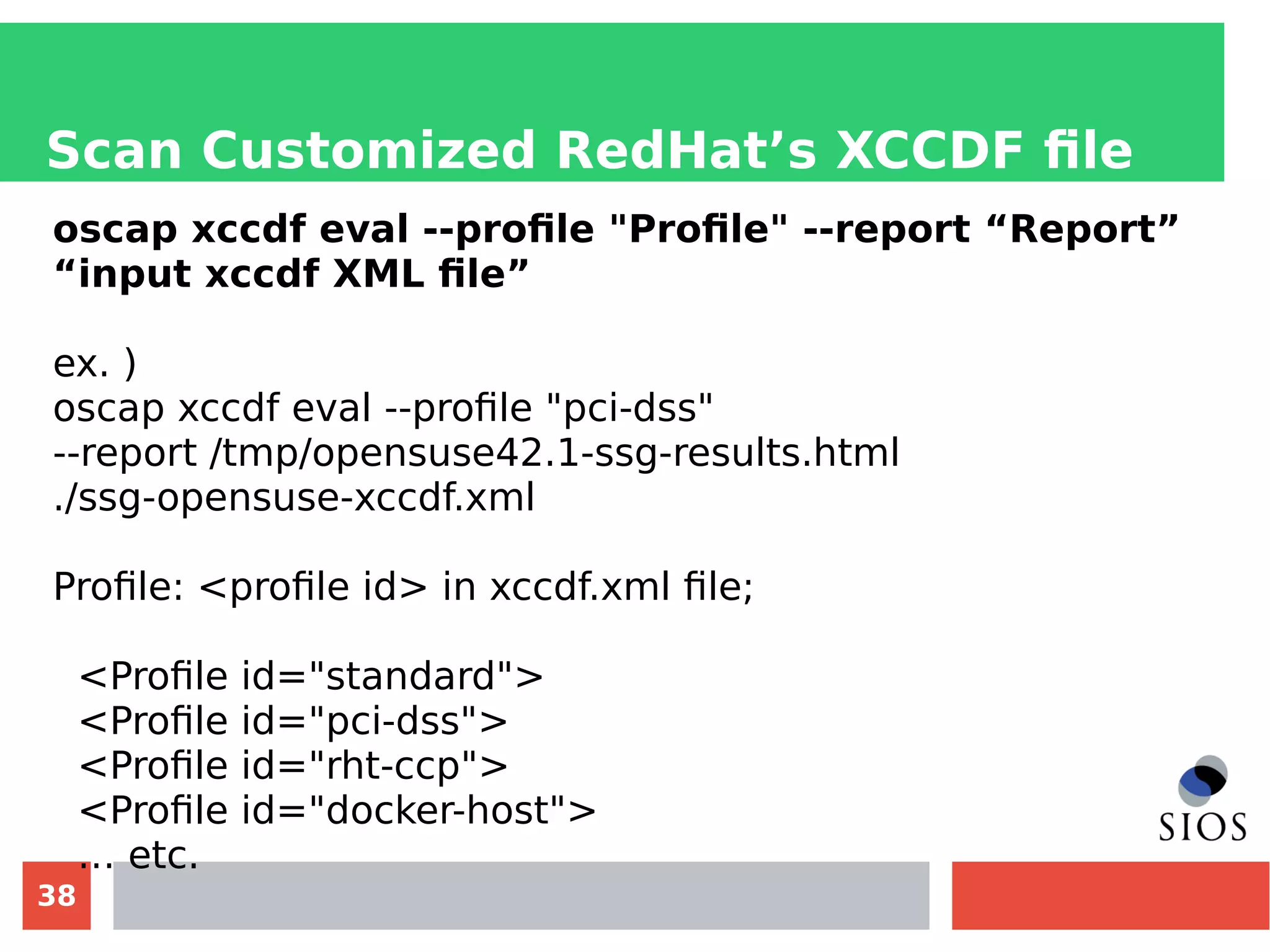
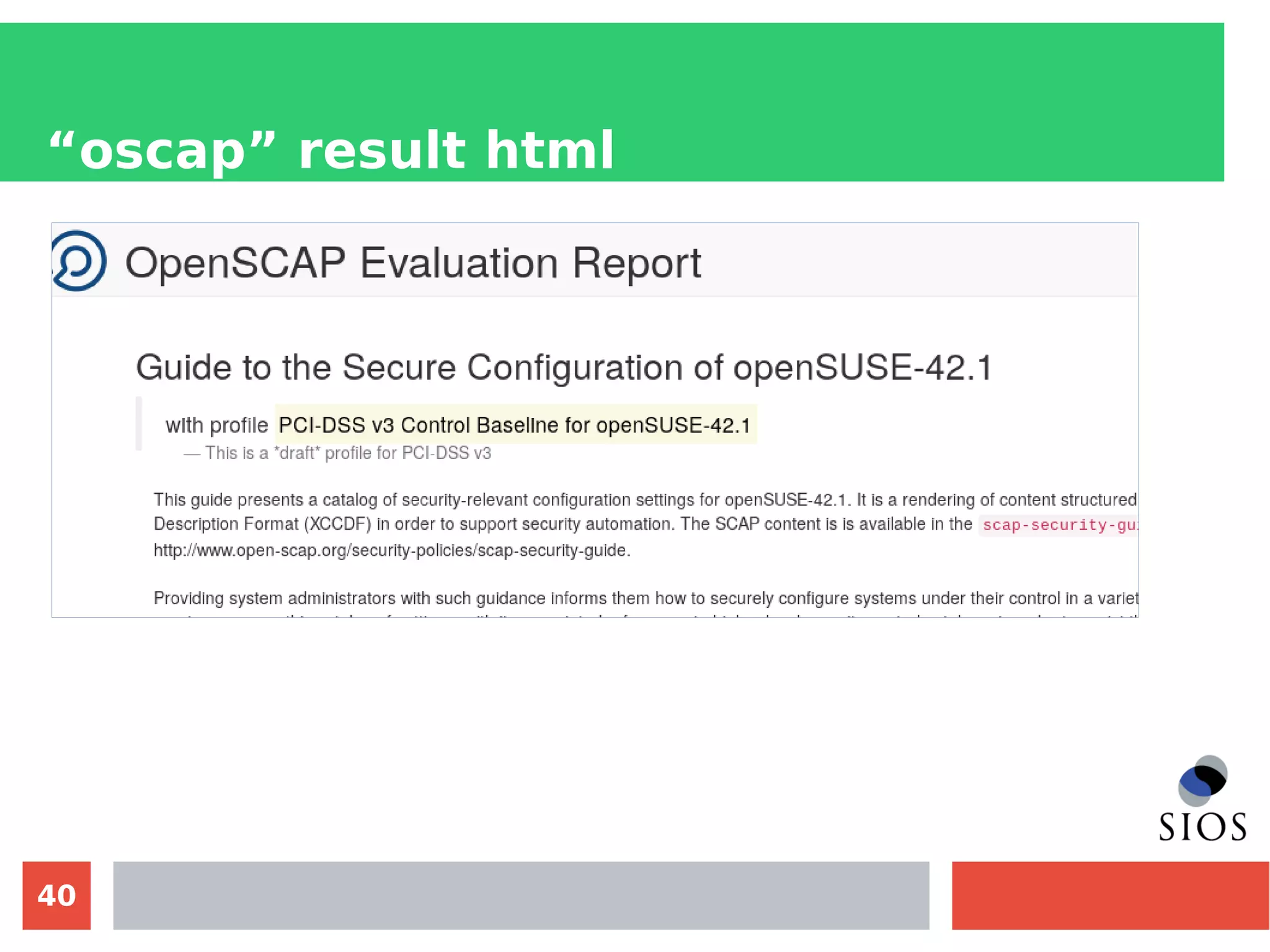
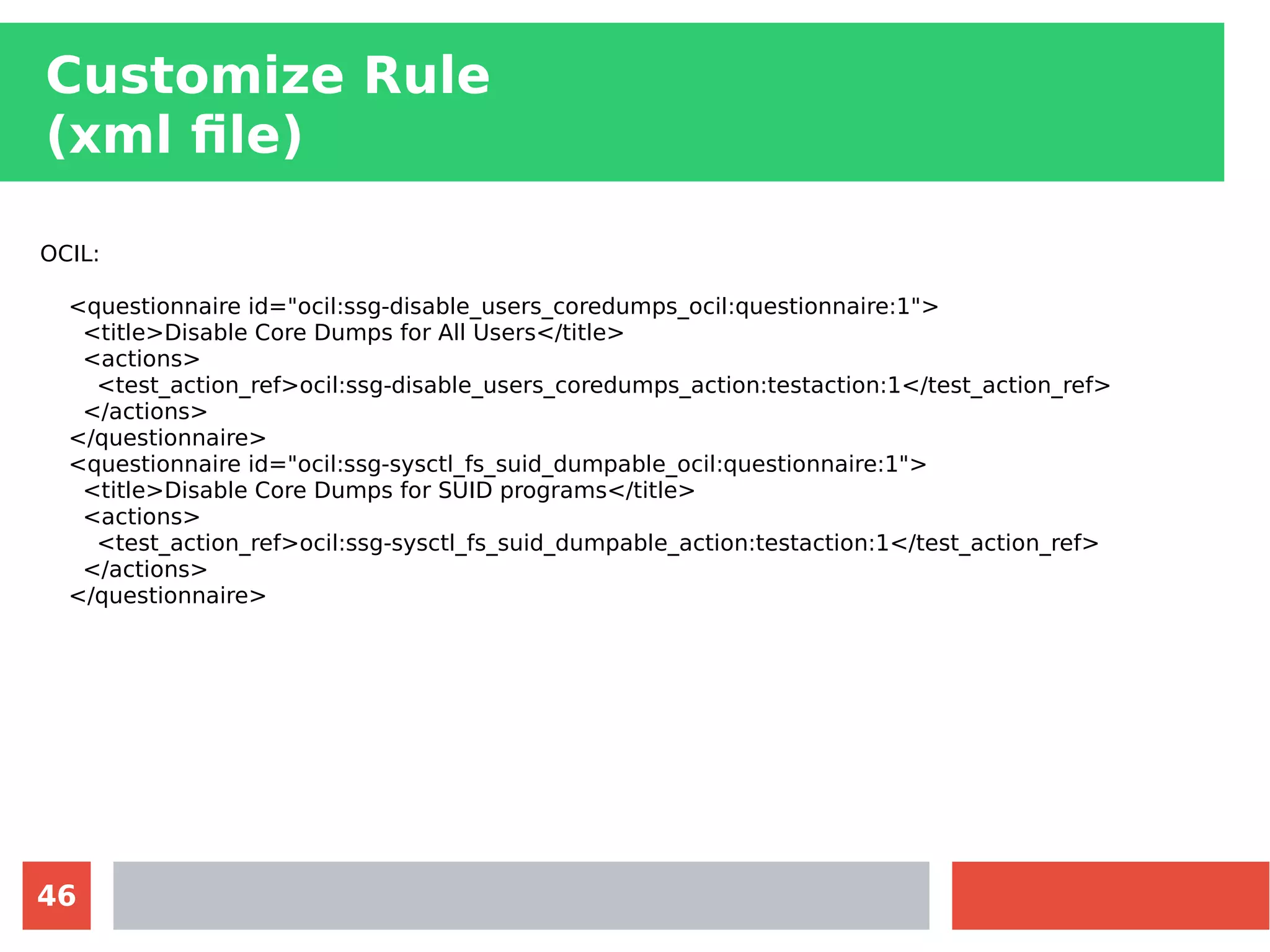
This document discusses customizing Security Content Automation Protocol (SCAP) content for openSUSE. It begins with an introduction to SCAP and its components like OVAL, XCCDF, and OCIL. It notes that while OVAL definitions exist for openSUSE, an XCCDF benchmark is needed to enable compliance testing. The document considers customizing an existing SLES or RHEL XCCDF file by changing platform identifiers and related files. It demonstrates using the oscap tool to evaluate a customized RHEL XCCDF benchmark against an openSUSE system and generating results. Further work is needed to fully adapt the customized XCCDF content to the openSUSE standard and profile for compliance benchmarks.