Embed presentation
Downloaded 13 times











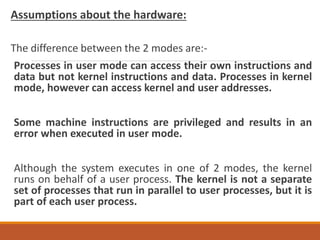
Unix is a multitasking, multiuser operating system developed in 1969 at Bell Labs. It allows multiple users to use a computer simultaneously and users can run multiple programs at once. There are several Unix variants like Solaris, AIX, and Linux. Unix was originally written for the PDP-7 computer in C programming language, making it portable. It uses a hierarchical file system and treats all resources as files with permissions. Processes run programs and the shell interprets commands to run programs or interact with the kernel for system calls. Everything in Unix is either a file or a process.
















