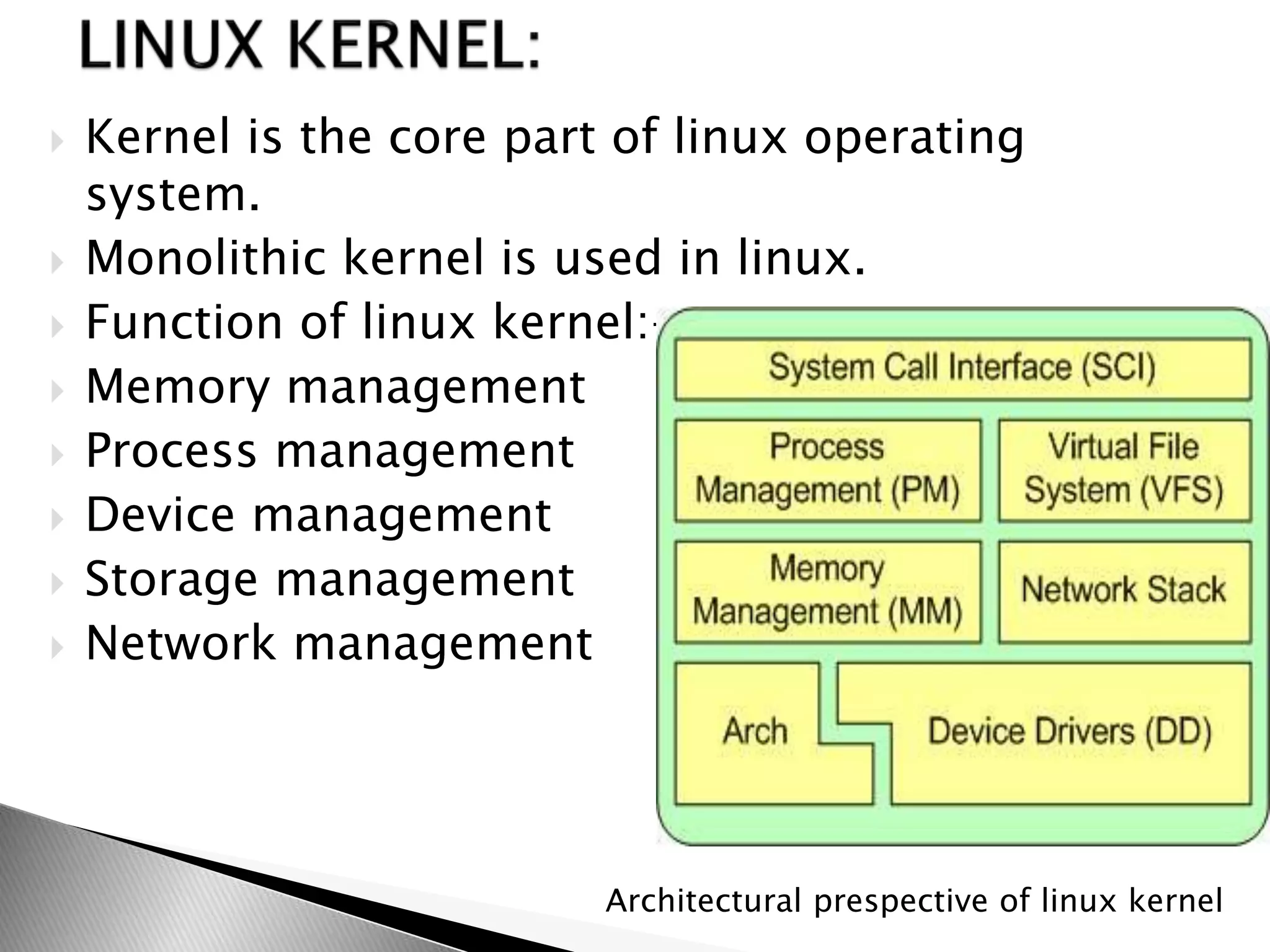
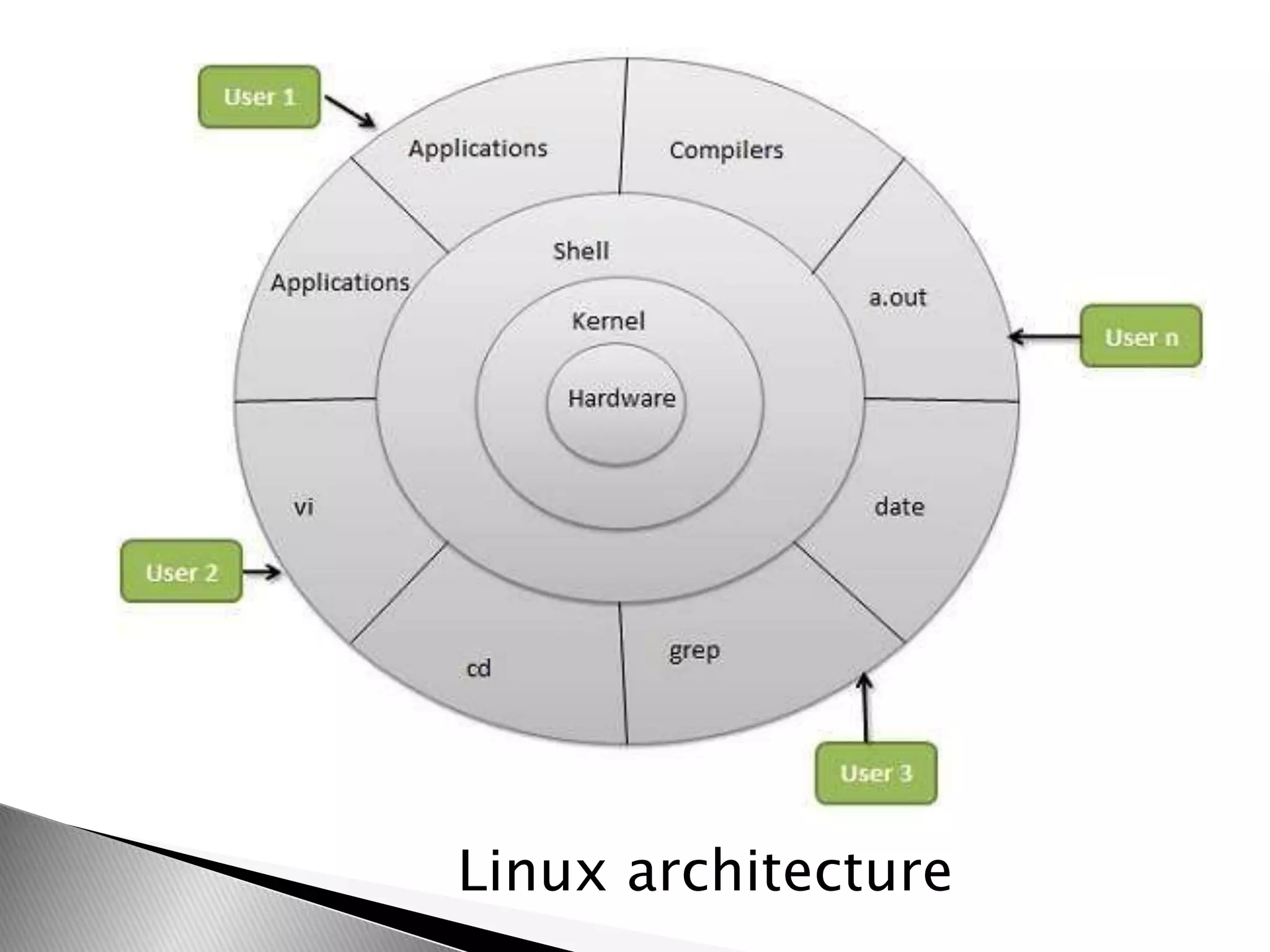
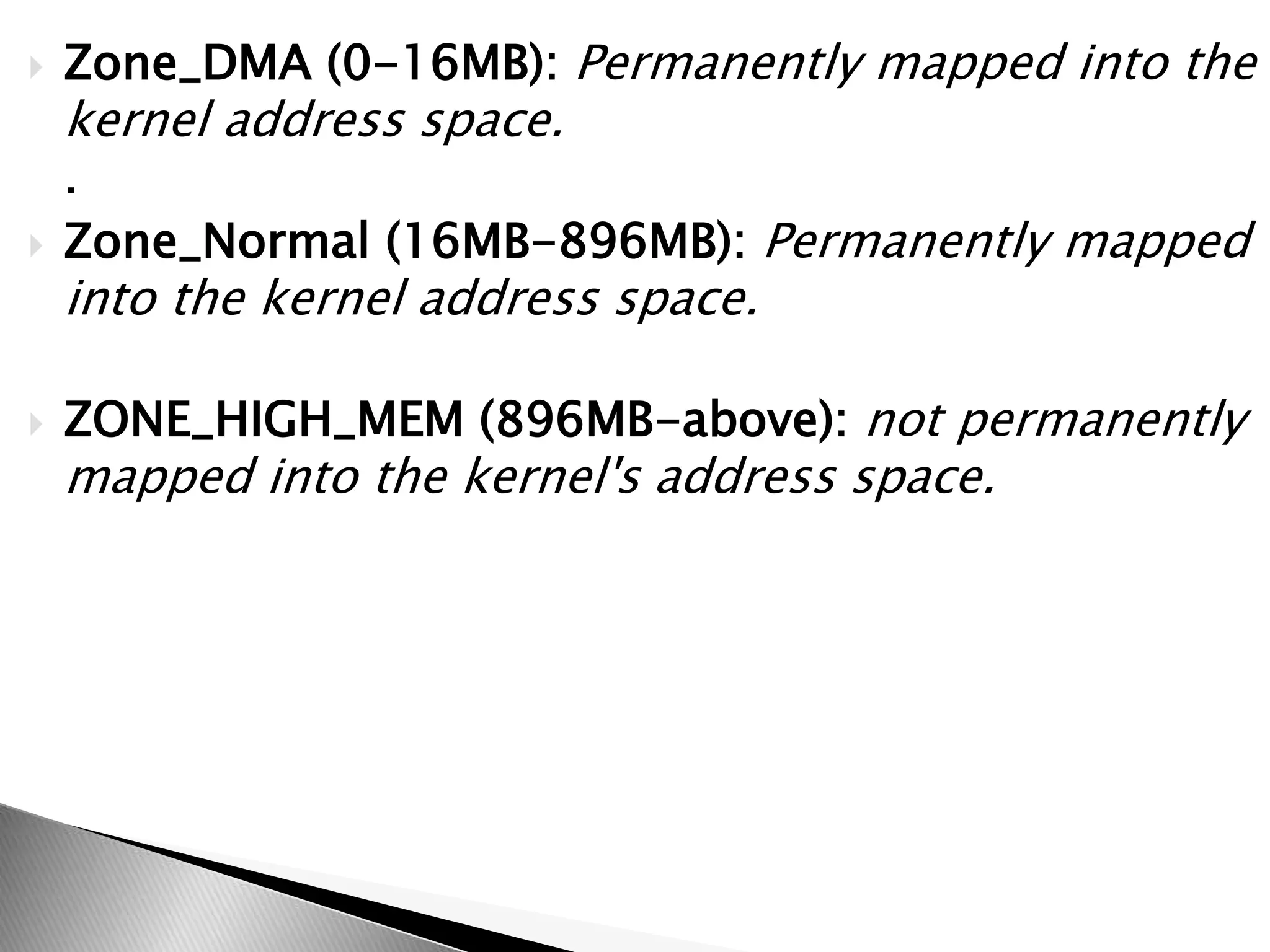
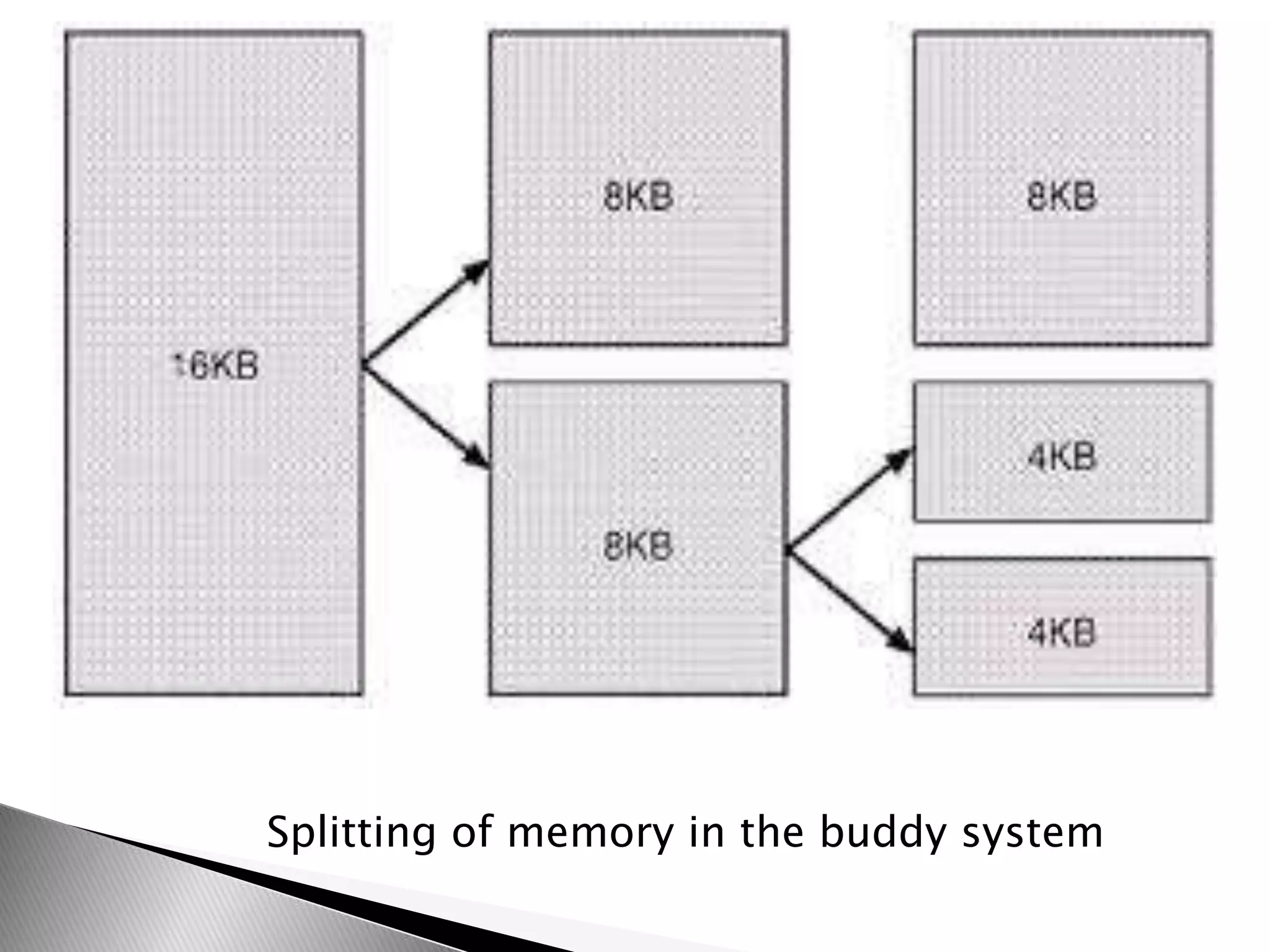
The document discusses various topics related to open source software and the Linux operating system. It begins by defining open source software and listing some examples of open source programs. It then discusses the history and development of Linux, from its origins in 1991 to its current usage. The rest of the document covers Linux distributions, features, kernel functions, process management, input/output handling, memory management, and advantages of the Linux operating system.