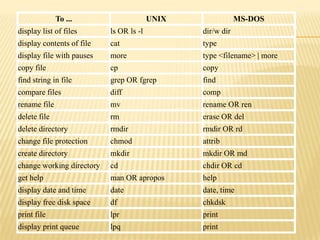
This document provides an overview of the UNIX operating system, including its history, features, basic structure, and commands. UNIX was created in 1969 at AT&T's Bell Labs and has undergone several revisions. It is a multi-user, multi-tasking operating system that runs on various hardware platforms. The kernel allocates resources and the shell acts as the interface between the user and kernel. Common UNIX commands allow users to navigate the file system, view and edit files, and manage the operating system.





















![ cp (copy)
cp file1 file2 is the command which makes a copy of file1 in the current
working directory and calls it file2.
% cp [options] <source> <destination>
% cp file1 file2
% cp file1 [file2] … /directory
mv (move)
mv file1 file2 moves file1 to file2. To move a file from one place to another,
use the mv command. This has the effect of moving rather than copying the file, so
we end up with only one file rather than two.
% mv <source> <destination>
– The <source> gets removed
% mv file1 dir/
% mv file1 file2](https://image.slidesharecdn.com/unixfinal-140311113442-phpapp01/85/Unix-Operating-System-23-320.jpg)


![ tail
This command shows the bottom N lines of one or more
text files.
tail -# file [file ...]
more
Shows the contents of one or more text files
interactively. Have a lot of viewing options and search
capability.
more file [file ...]](https://image.slidesharecdn.com/unixfinal-140311113442-phpapp01/85/Unix-Operating-System-26-320.jpg)
![ grep
shows lines in one or more text files that match a
given regular expression.
grep regular-expression file [file ...]](https://image.slidesharecdn.com/unixfinal-140311113442-phpapp01/85/Unix-Operating-System-27-320.jpg)
