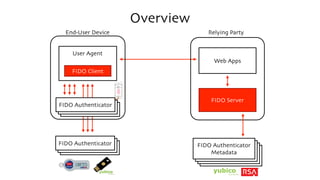
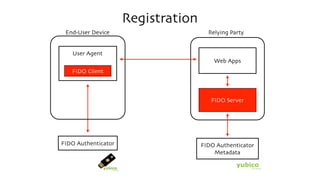
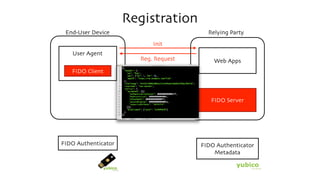
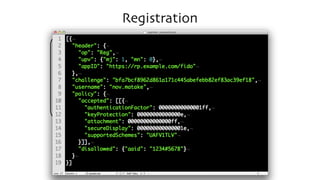
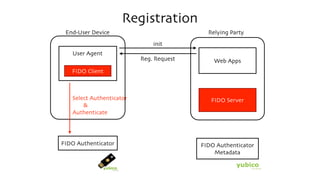
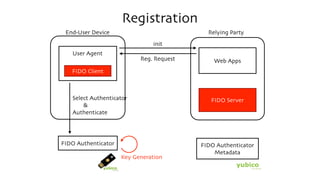
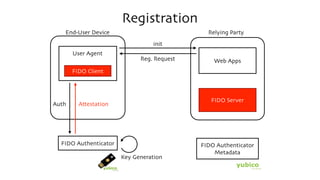
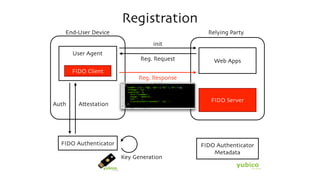
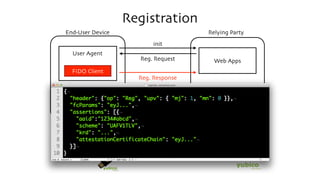
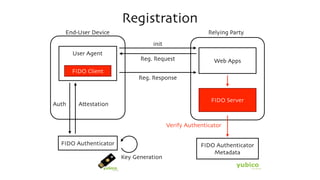
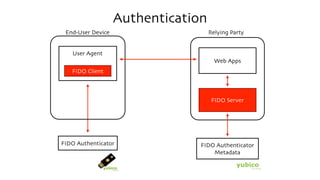
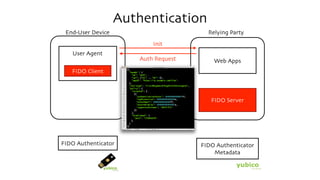
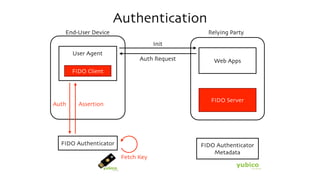
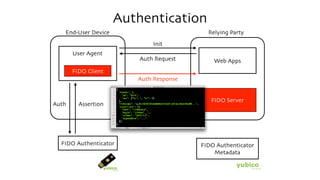
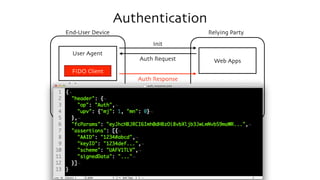
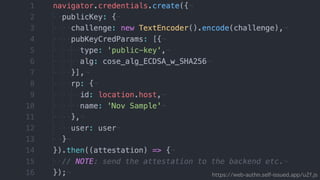
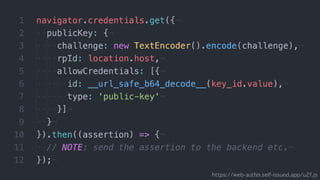
The document discusses the W3C Web Authentication standard (also known as FIDO 2.0) for passwordless strong authentication on the web. It provides an overview of the key components and actors in the standard like FIDO authenticators, user agents, relying parties. It then summarizes the basic flows of registration and authentication in 2 phases. During registration, a key pair is generated on the authenticator and the public key is registered with the FIDO server. During authentication, the authenticator performs local authentication using the registered key and sends an assertion to the server for remote authentication.



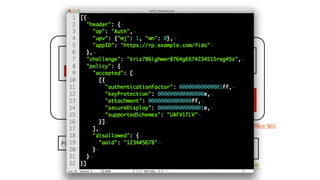



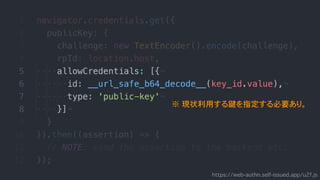
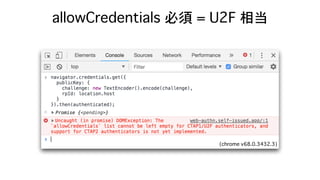




![authData contains..
Name Length (in bytes) Description
rpIdHash 32 SHA-256 hash of the RP ID associated with the credential.
flags 1
Flags (bit 0 is the least significant bit):
• Bit 0: User Present (UP) result.
• Bit 1: Reserved for future use (RFU1).
• Bit 2: User Verified (UV) result.
• Bits 3-5: Reserved for future use (RFU2).
• Bit 6: Attested credential data included (AT).
• Bit 7: Extension data included (ED).
signCount 4 Signature counter, 32-bit unsigned big-endian integer.
attestedCredentialData variable (if present)
attested credential data (if present). See §6.3.1 Attested credential
data for details. Its length depends on the length of the credential ID
and credential public key being attested.
extensions variable (if present)
Extension-defined authenticator data. This is a CBOR [RFC7049]
map with extension identifiers as keys, and authenticator extension
outputs as values. See §9 WebAuthn Extensions for details.](https://image.slidesharecdn.com/web-authn-180609055641/85/W3C-Web-Authentication-idcon-vol-24-34-320.jpg)
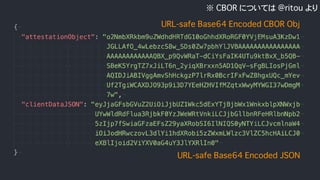
![attestedCredentialData contains..
Name Length (in bytes) Description
aaguid 16 The AAGUID of the authenticator.
credentialIdLength 2 Byte length L of Credential ID, 16-bit unsigned big-endian integer.
credentialId L Credential ID
credentialPublicKey variable
The credential public key encoded in COSE_Key format, as defined
in Section 7 of [RFC8152], using the CTAP2 canonical CBOR
encoding form. The COSE_Key-encoded credential public key MUST
contain the optional "alg" parameter and MUST NOT contain any
other optional parameters. The "alg" parameter MUST contain a
COSEAlgorithmIdentifier value. The encoded credential public
key MUST also contain any additional required parameters stipulated
by the relevant key type specification, i.e., required for the key type
"kty" and algorithm "alg" (see Section 8 of [RFC8152]).](https://image.slidesharecdn.com/web-authn-180609055641/85/W3C-Web-Authentication-idcon-vol-24-35-320.jpg)
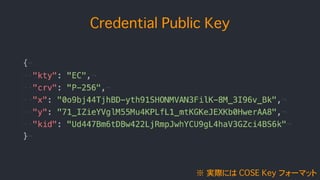
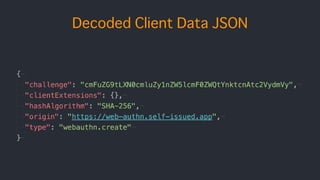
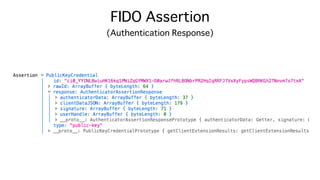
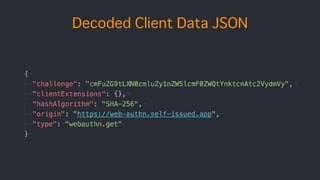
![authData contains..
Name Length (in bytes) Description
rpIdHash 32 SHA-256 hash of the RP ID associated with the credential.
flags 1
Flags (bit 0 is the least significant bit):
• Bit 0: User Present (UP) result.
• Bit 1: Reserved for future use (RFU1).
• Bit 2: User Verified (UV) result.
• Bits 3-5: Reserved for future use (RFU2).
• Bit 6: Attested credential data included (AT).
• Bit 7: Extension data included (ED).
signCount 4 Signature counter, 32-bit unsigned big-endian integer.
attestedCredentialData variable (if present)
attested credential data (if present). See §6.3.1 Attested credential
data for details. Its length depends on the length of the credential ID
and credential public key being attested.
extensions variable (if present)
Extension-defined authenticator data. This is a CBOR [RFC7049]
map with extension identifiers as keys, and authenticator extension
outputs as values. See §9 WebAuthn Extensions for details.](https://image.slidesharecdn.com/web-authn-180609055641/85/W3C-Web-Authentication-idcon-vol-24-40-320.jpg)