This document discusses different types of data structures and queues. It provides examples of queues and their applications. The key points are:
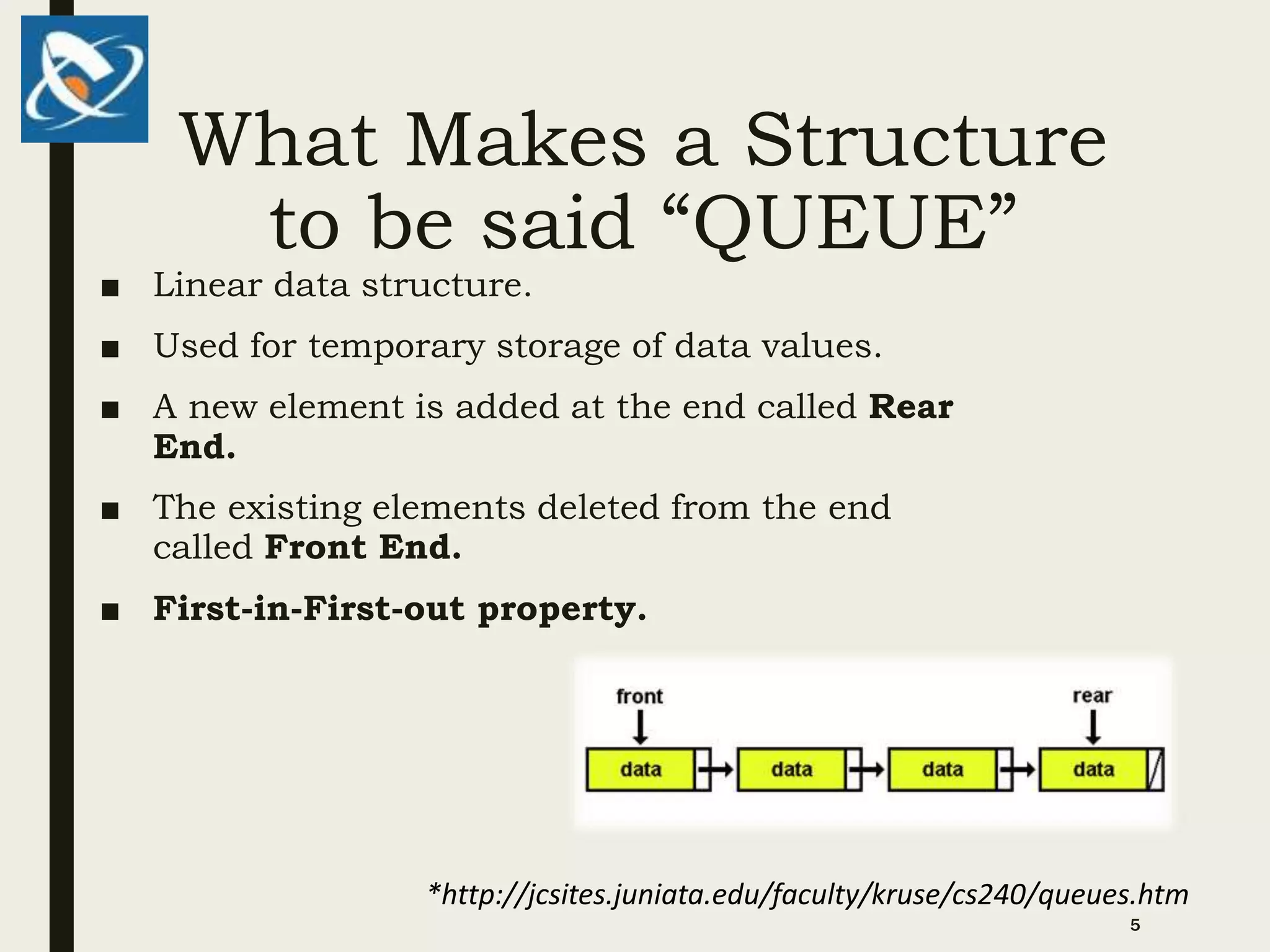
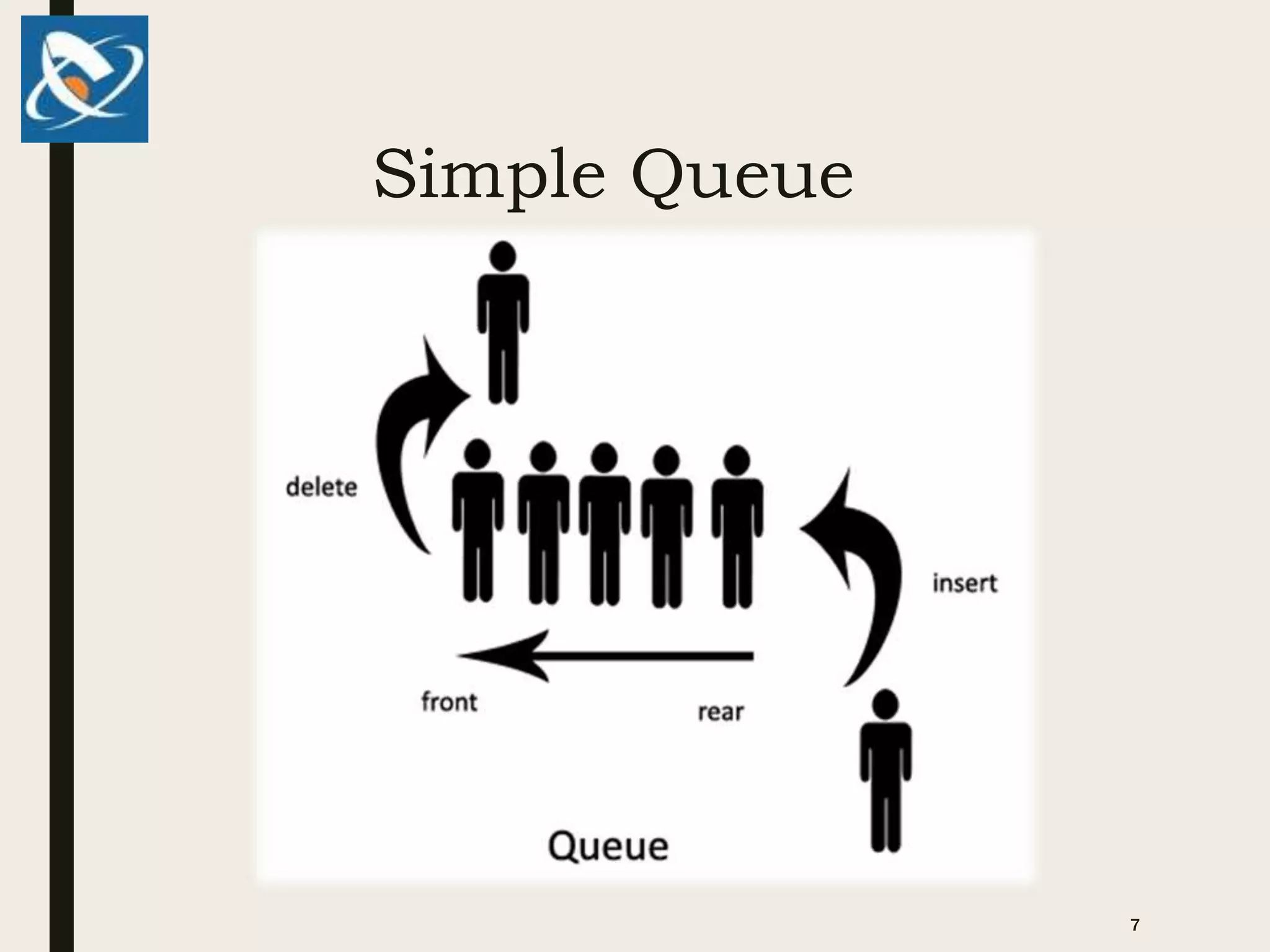
1. Queues are linear data structures that follow a first-in, first-out (FIFO) approach. New elements are added to the rear and existing elements are deleted from the front.
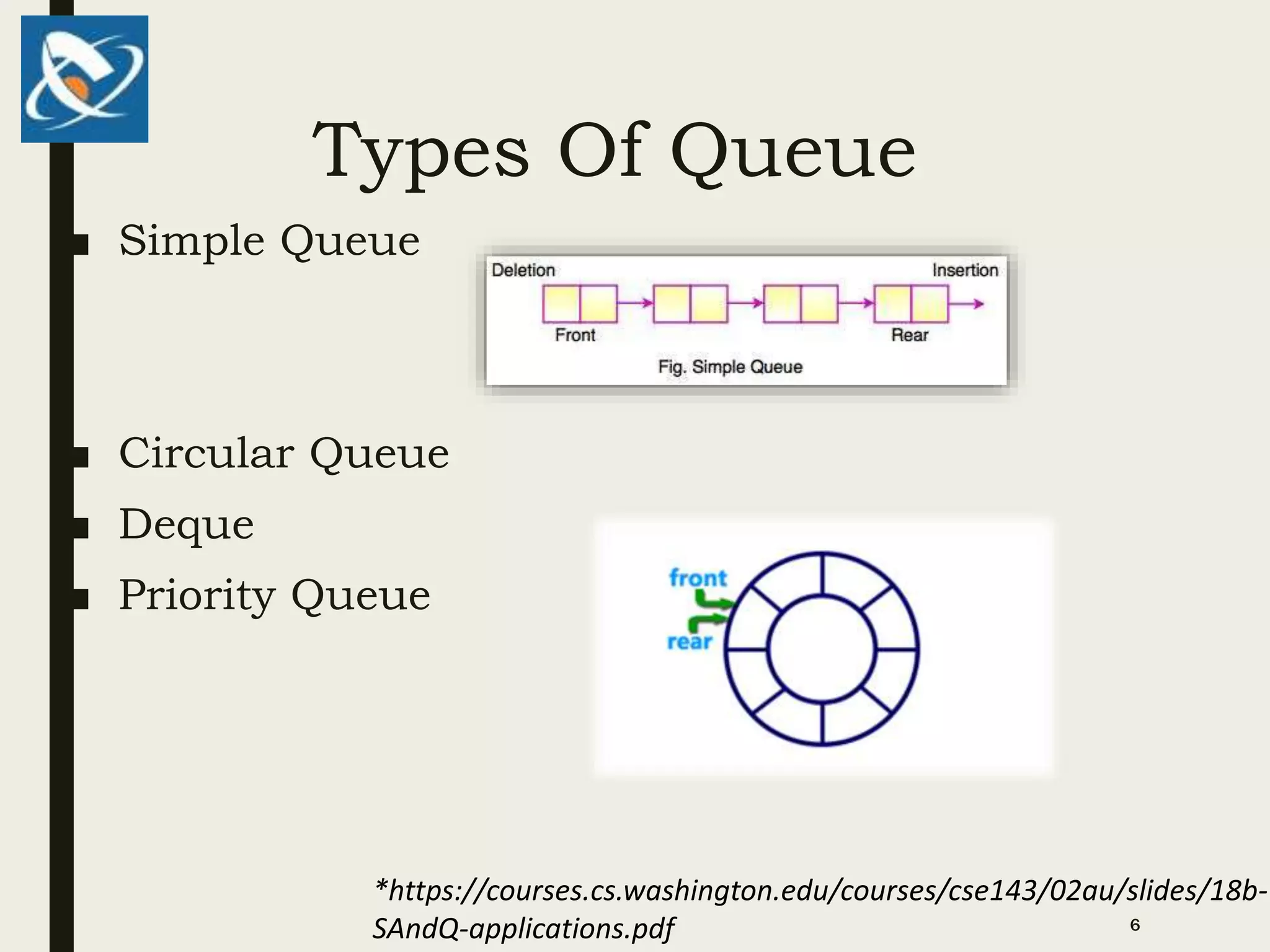
2. Common queue types include simple queues, circular queues, deques, and priority queues. Circular queues use a circular buffer that addresses empty spaces. Deques allow insertion and removal from both ends.
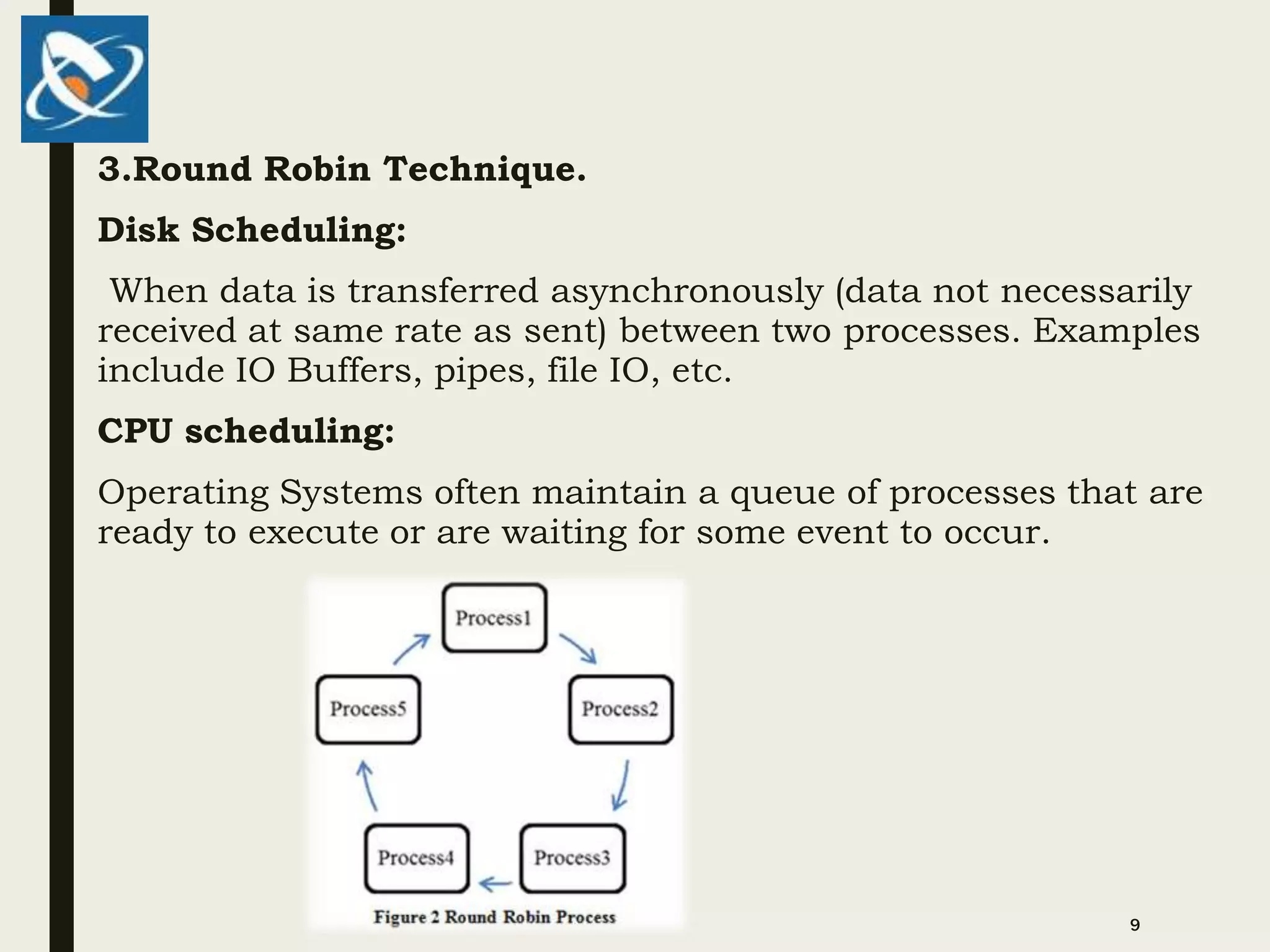
3. Queues have various applications including CPU scheduling, traffic light systems, baggage claim systems, undo-redo functions, and bandwidth management of network traffic. Priority queues