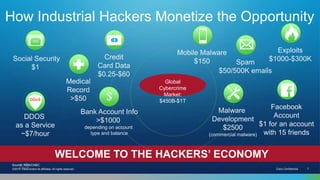
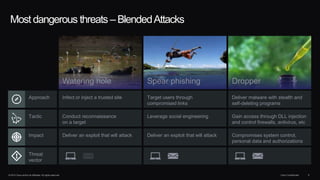
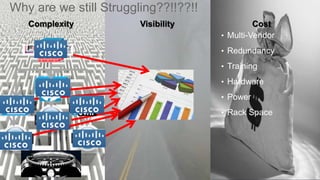
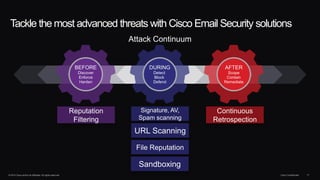
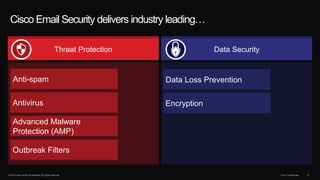
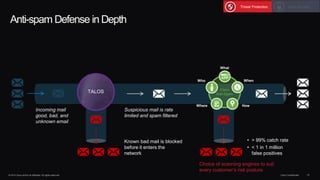
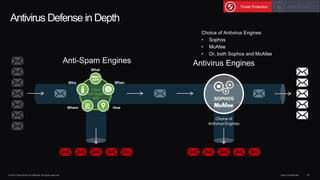
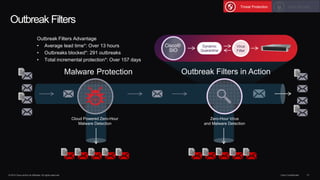
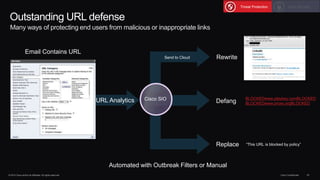
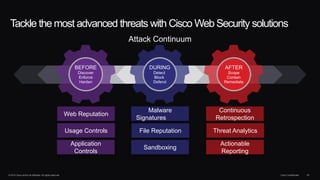
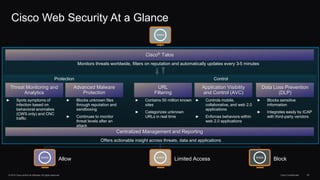
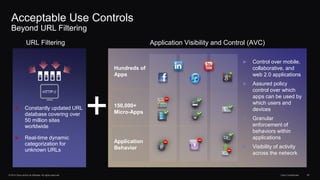
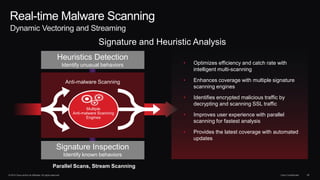
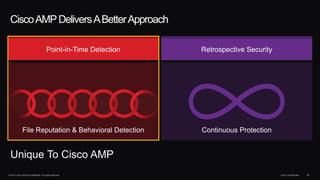
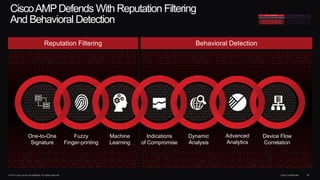
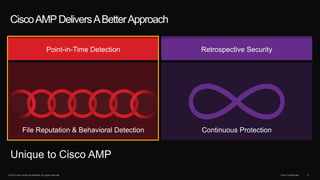
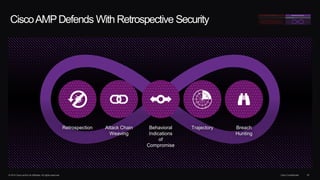
The document outlines housekeeping notes from Cisco Connect Halifax 2015 and discusses advanced threat security measures against industrialized hacking. It details the hacker economy, threats like blended attacks, and various Cisco security solutions including email and web security that address advanced cyber threats. Cisco emphasizes the importance of integrated threat defense and continuous protection for enhanced security resilience.