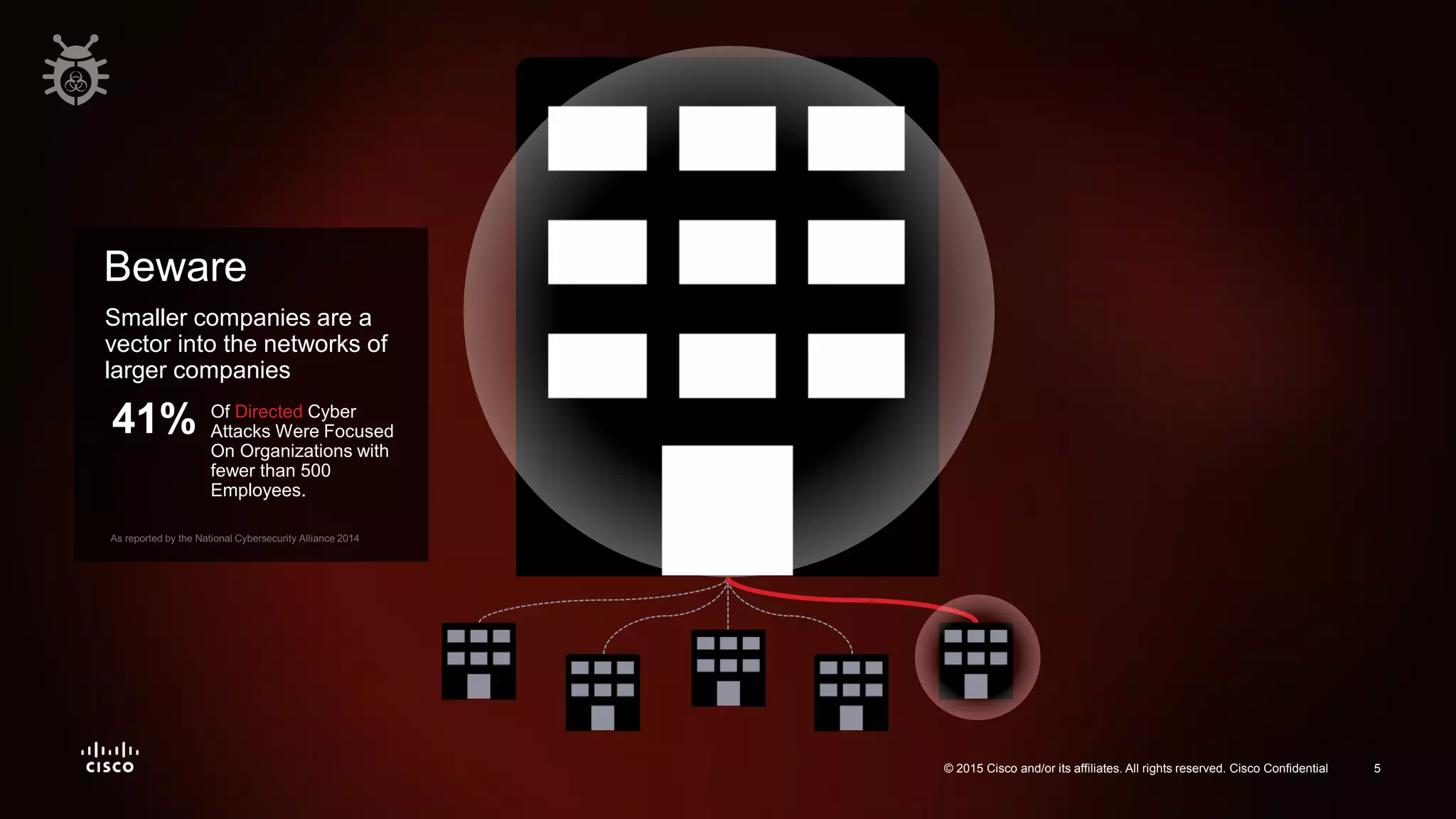
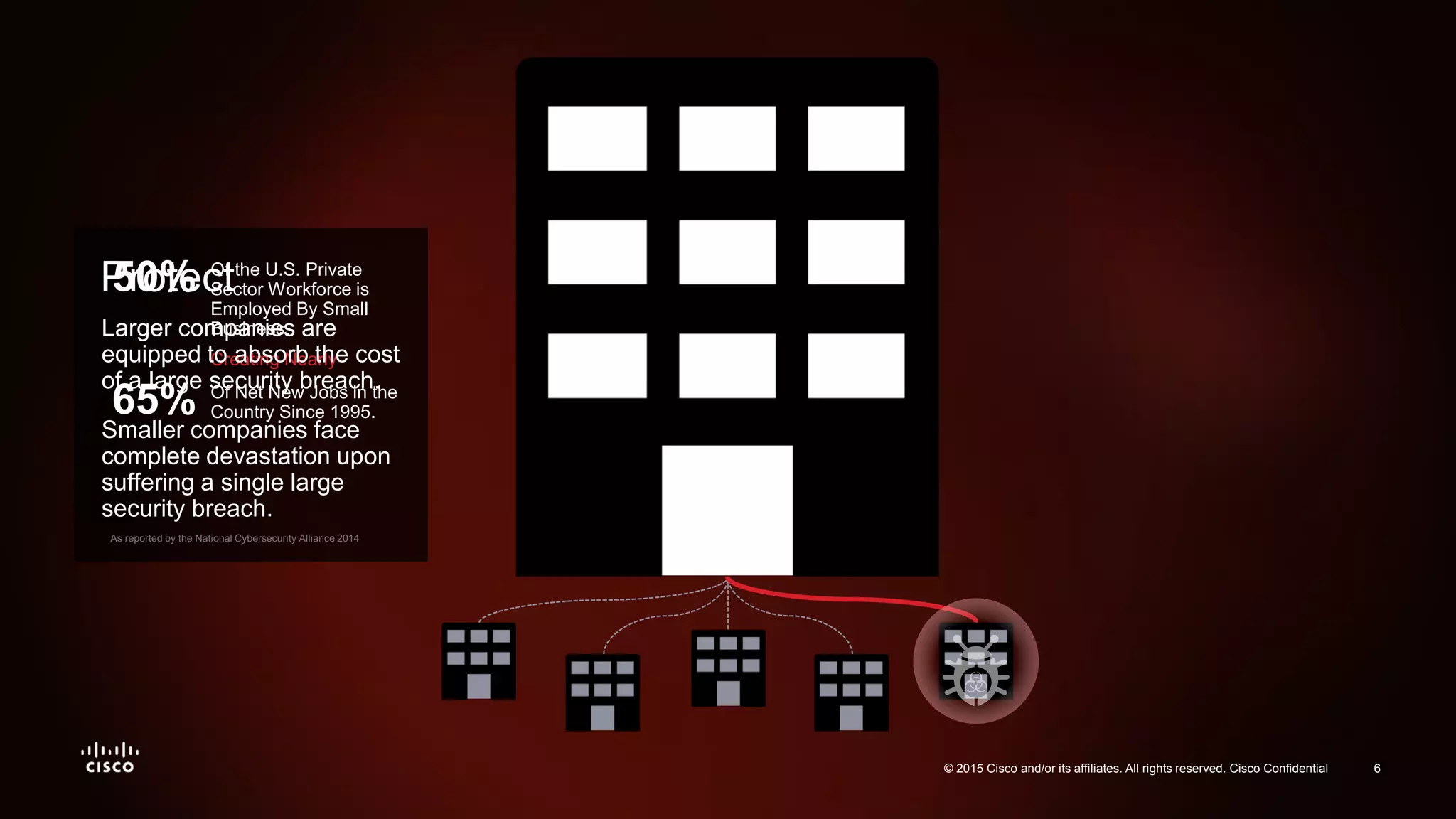
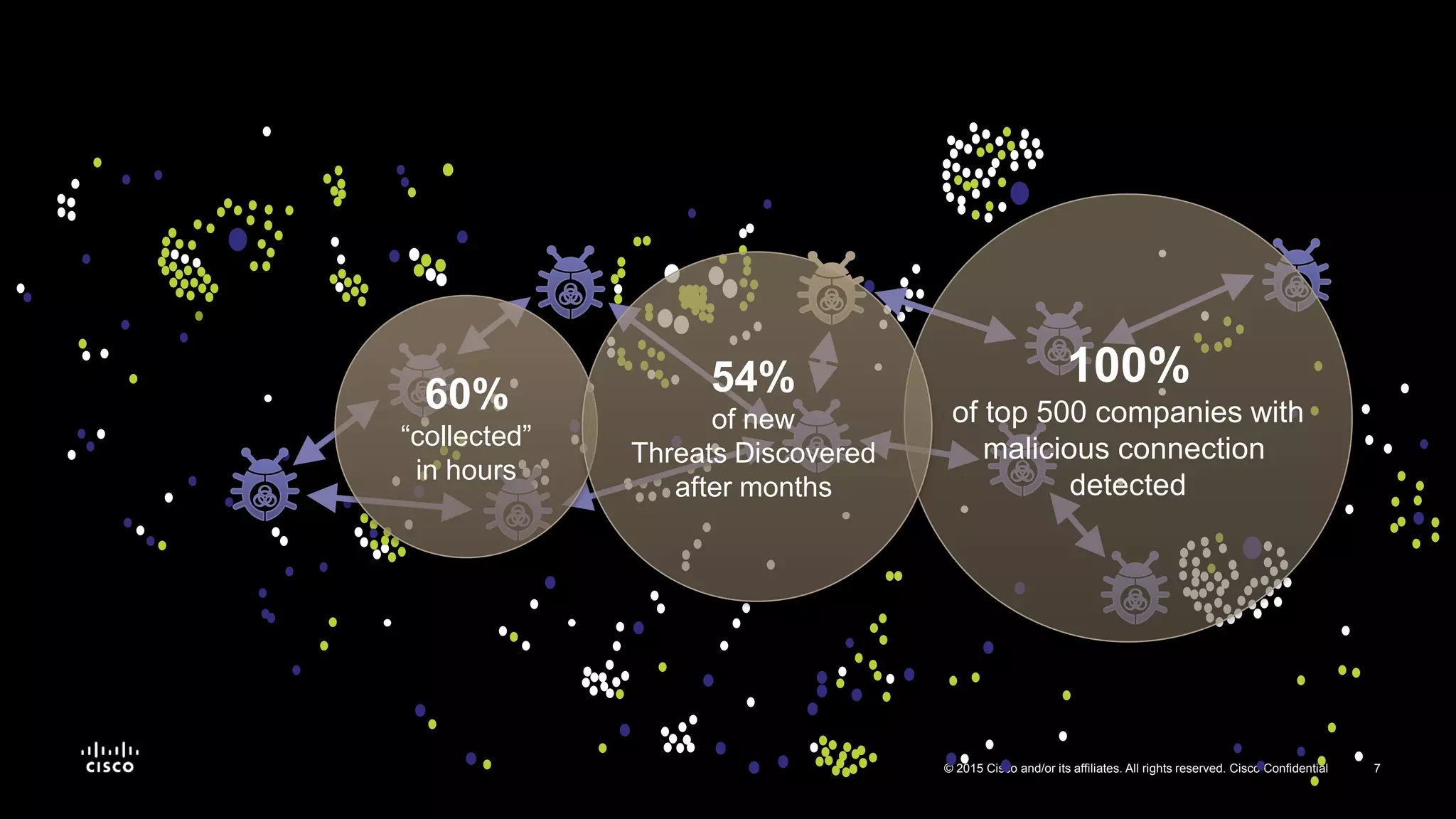
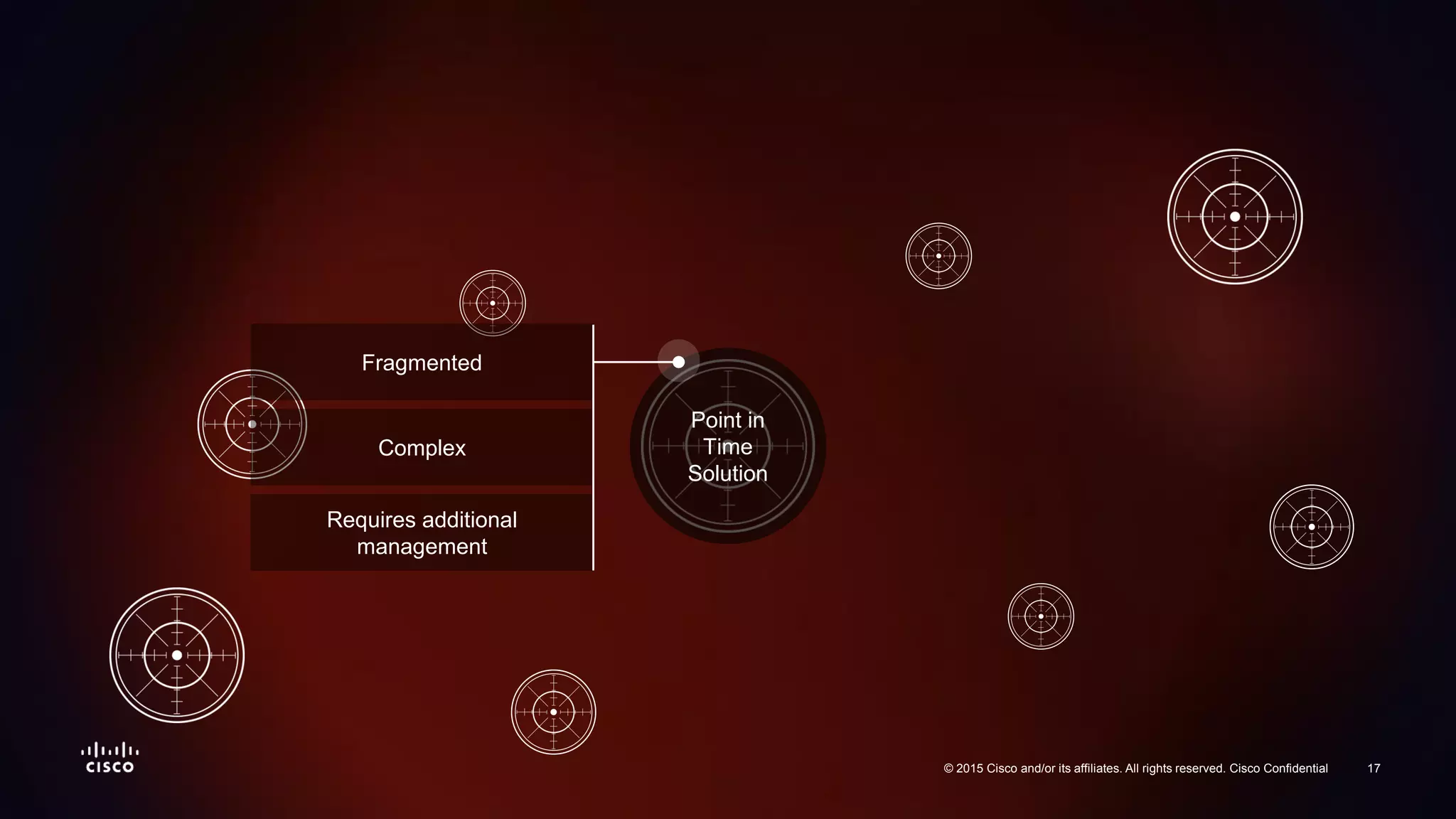
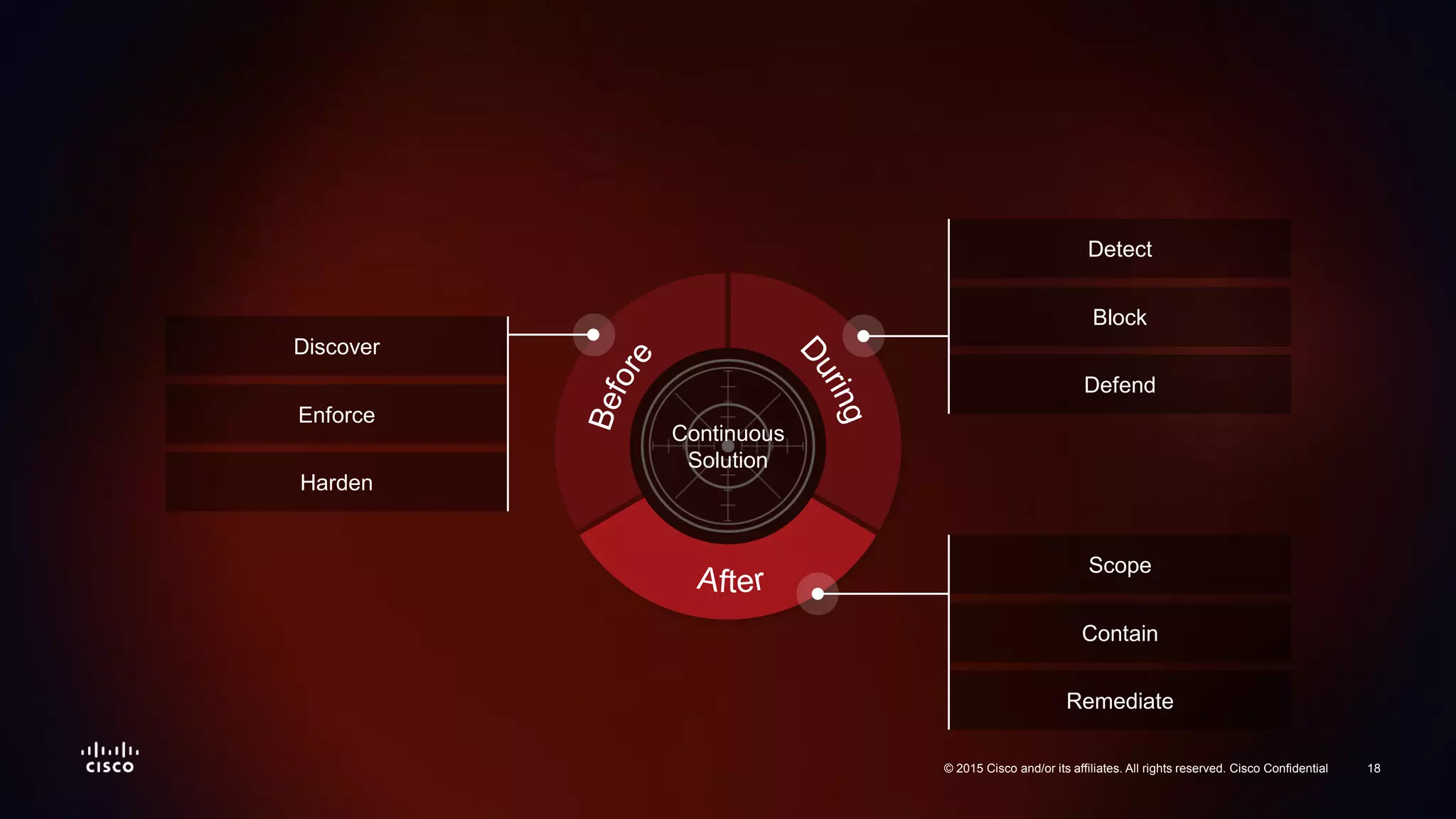
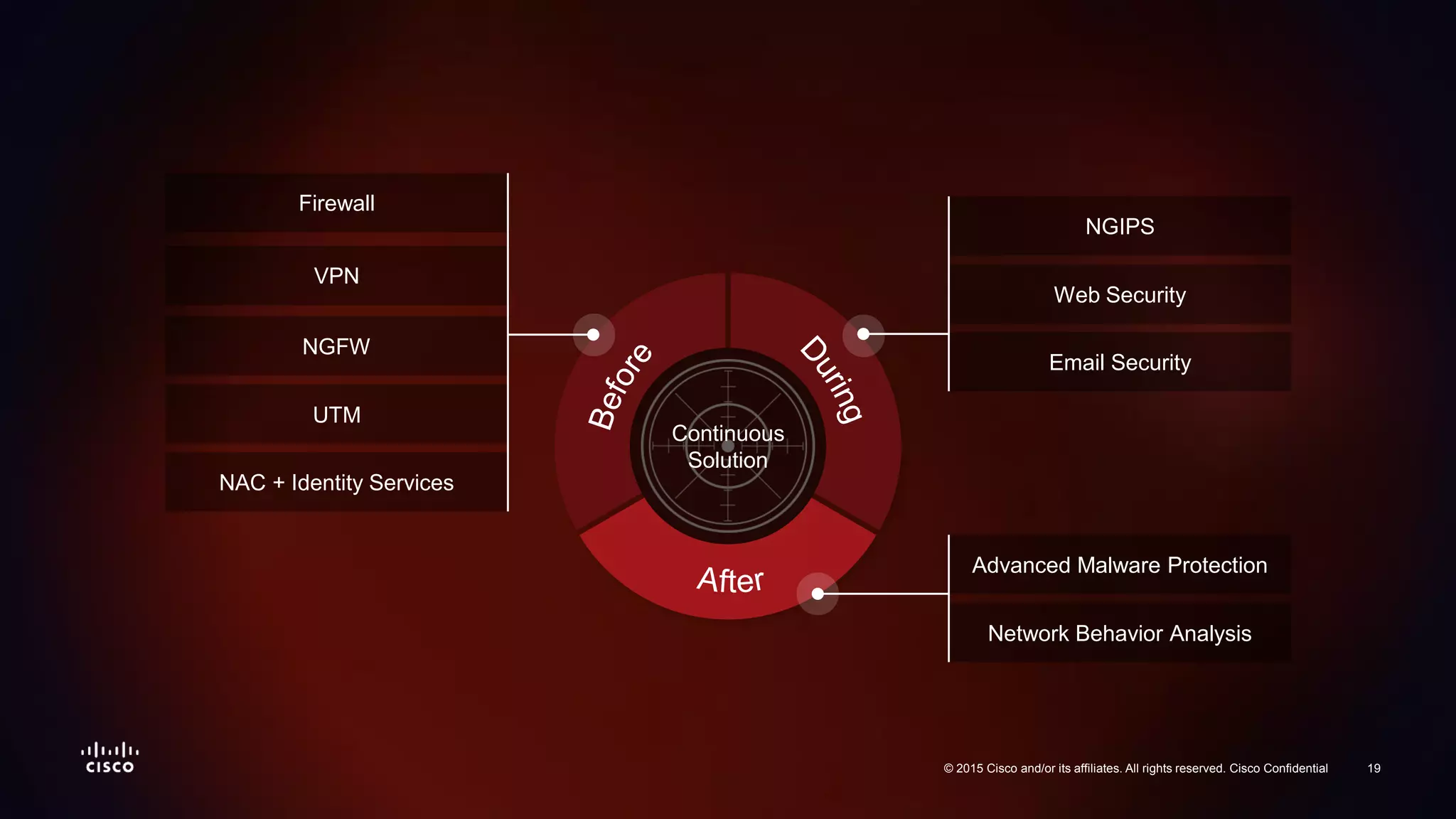
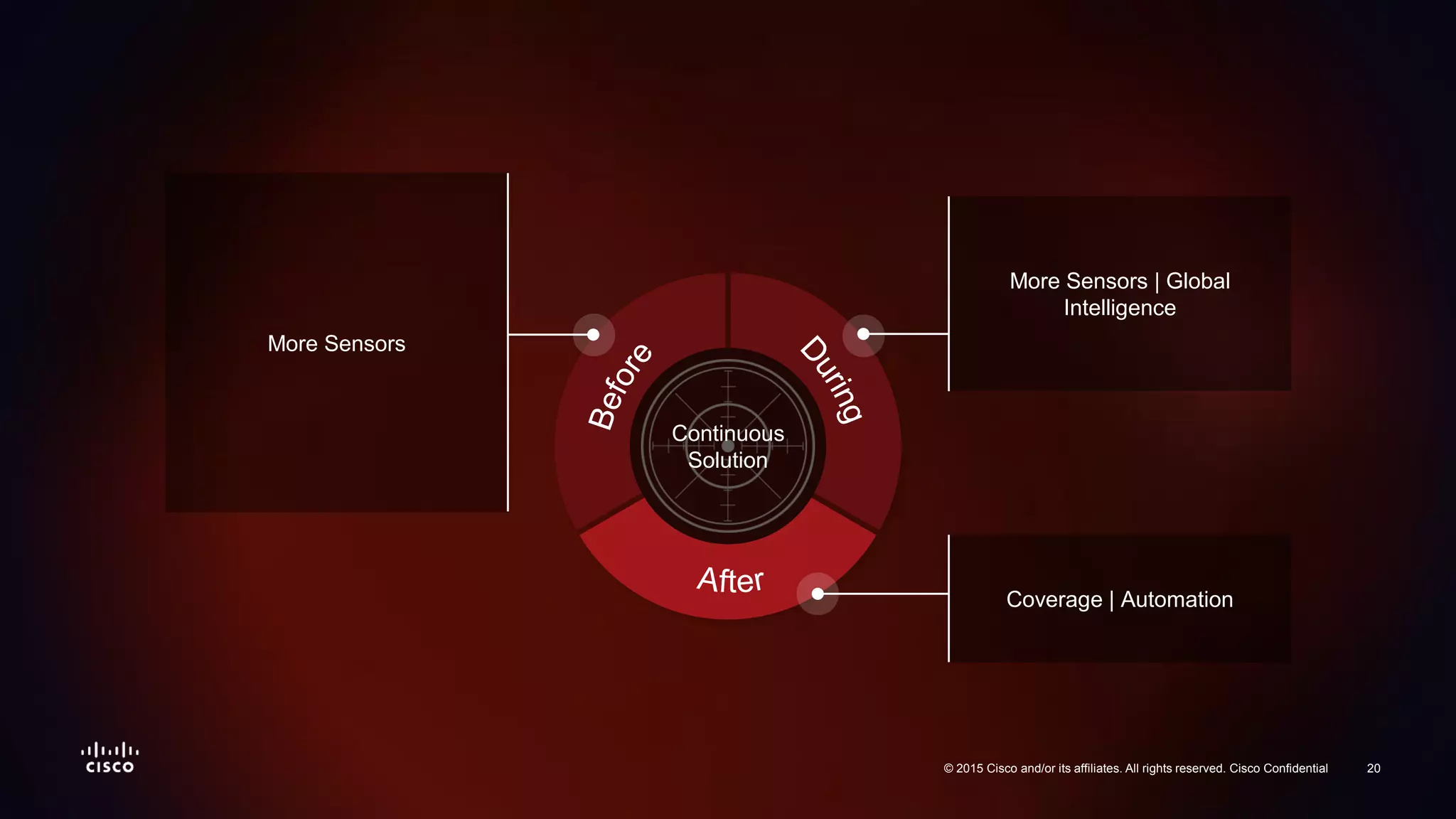
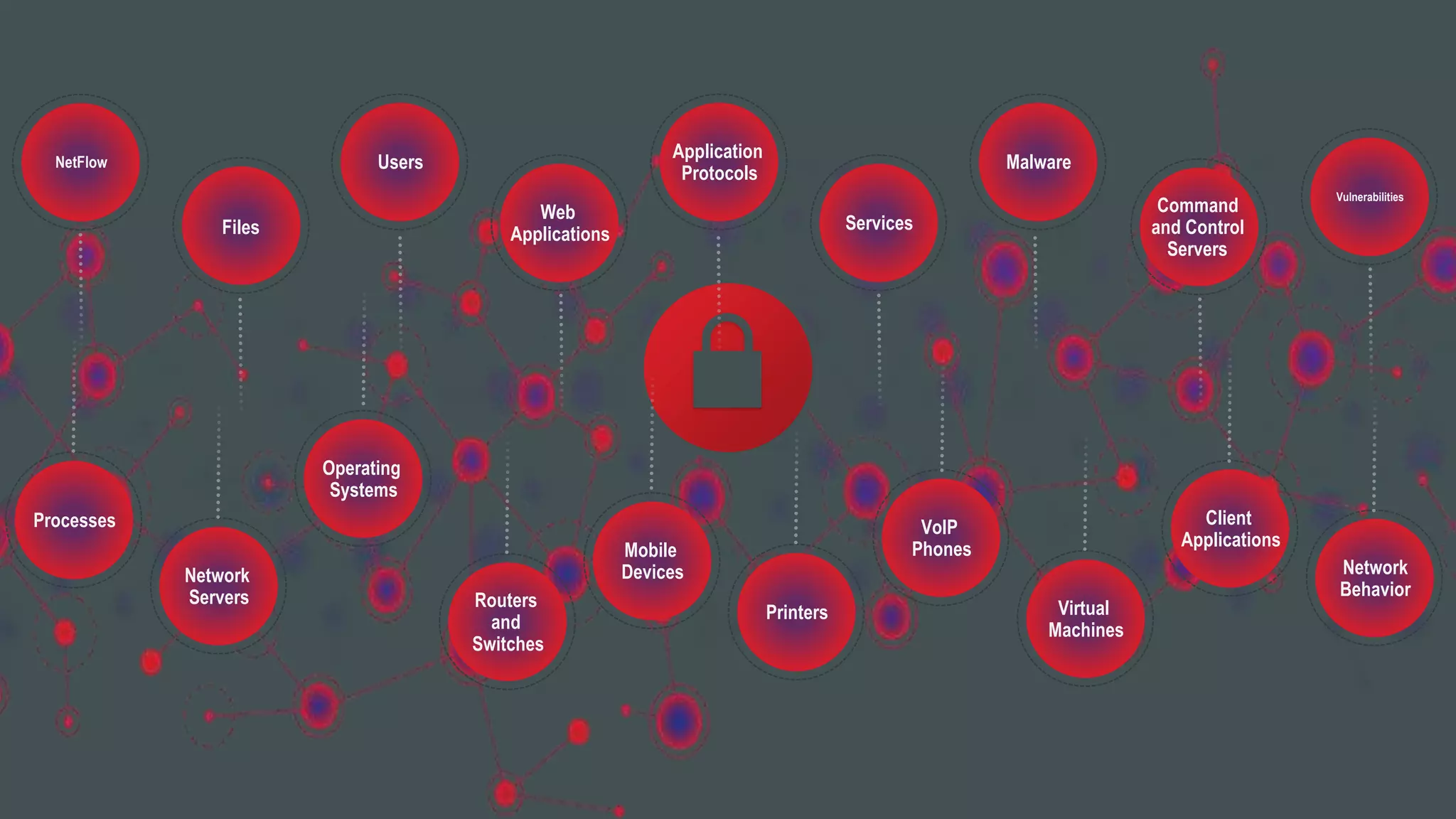
The document discusses the increasing vulnerability of organizations to cyber threats, particularly highlighting the risks faced by smaller companies which are often easier targets for attacks. It emphasizes the need for a comprehensive security strategy that goes beyond point-in-time solutions to continuous defense mechanisms involving advanced malware protection and network behavior analysis. The findings suggest that better information and awareness can lead to improved decision-making in cybersecurity.