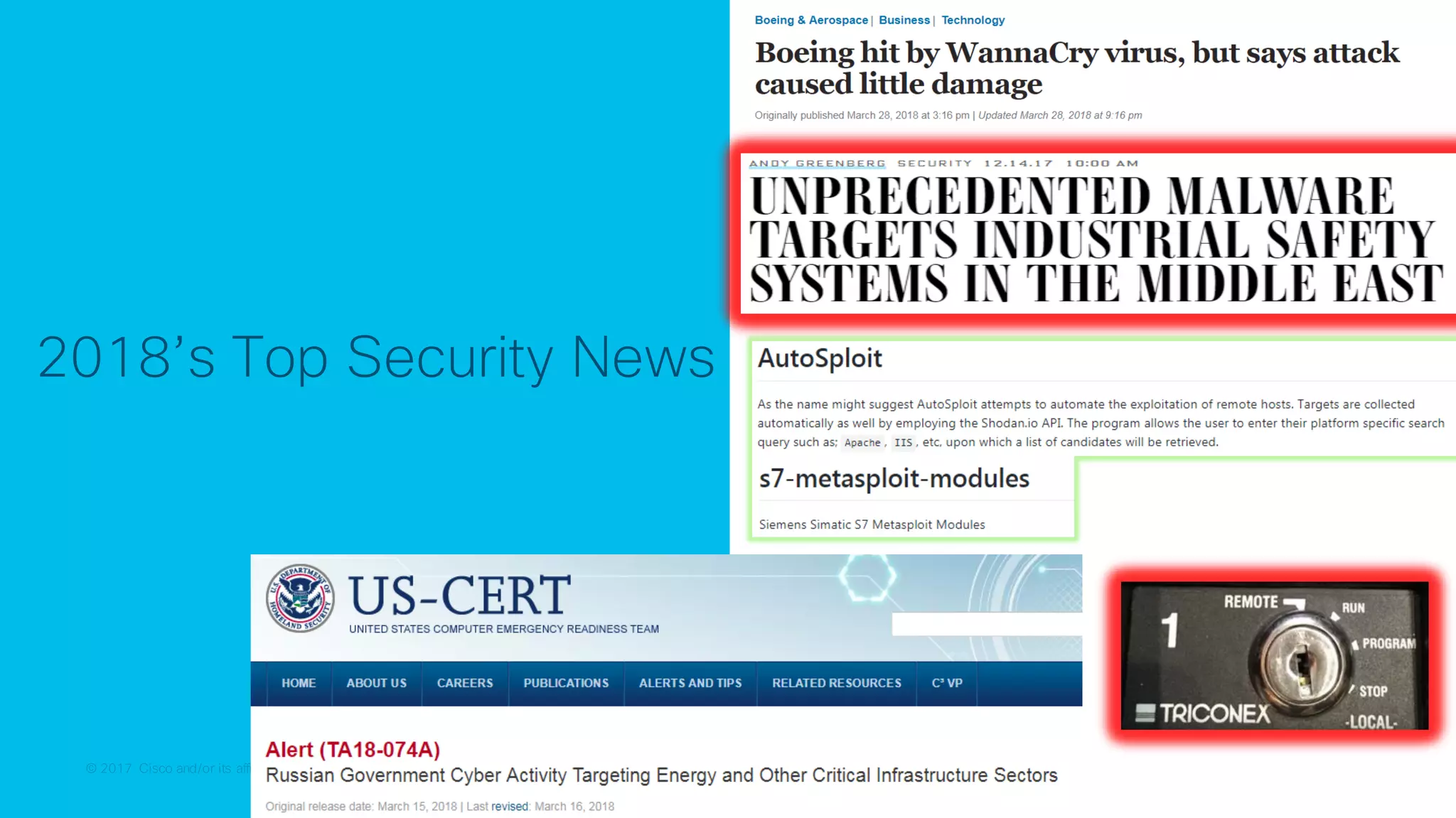
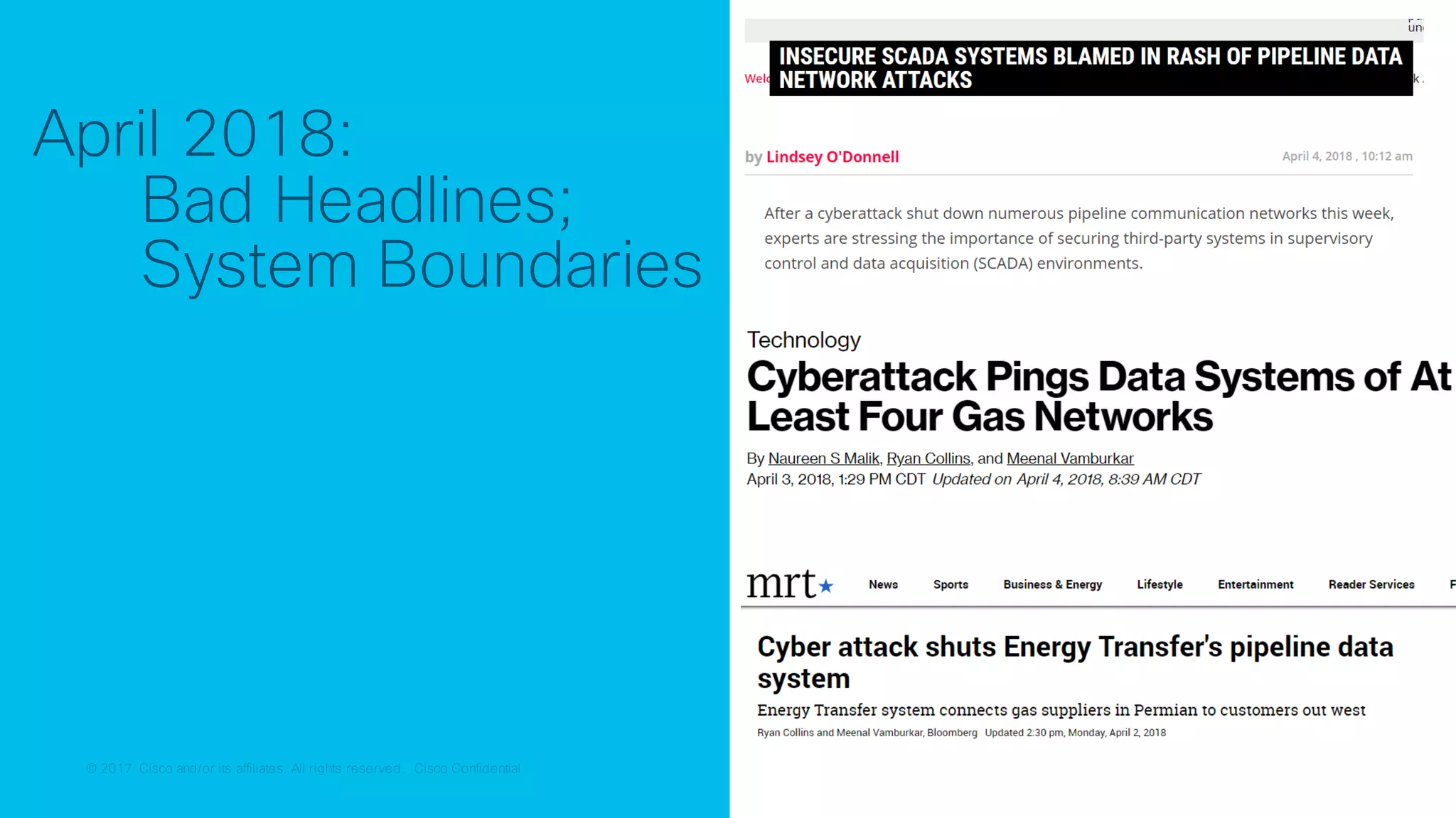
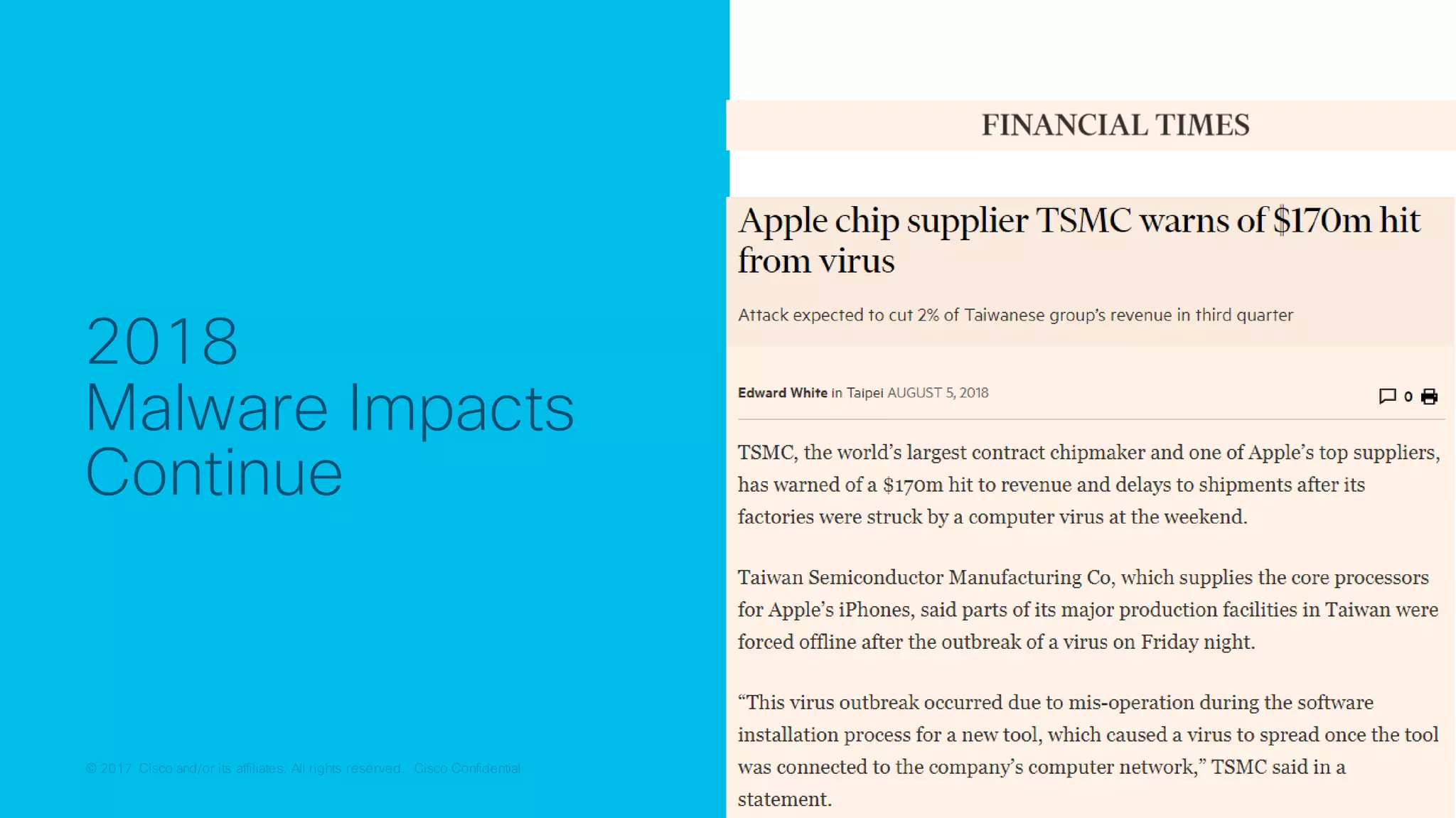
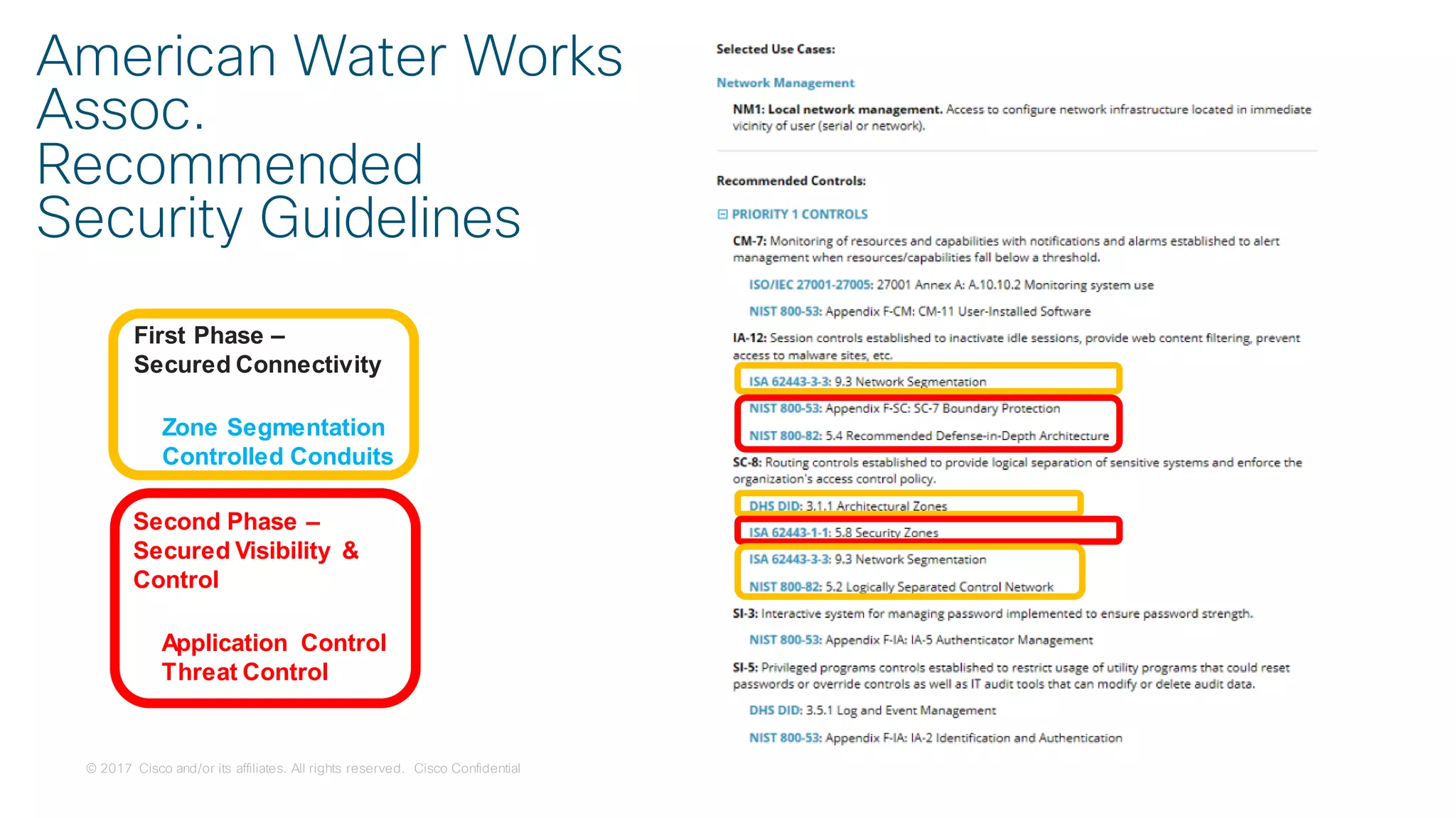
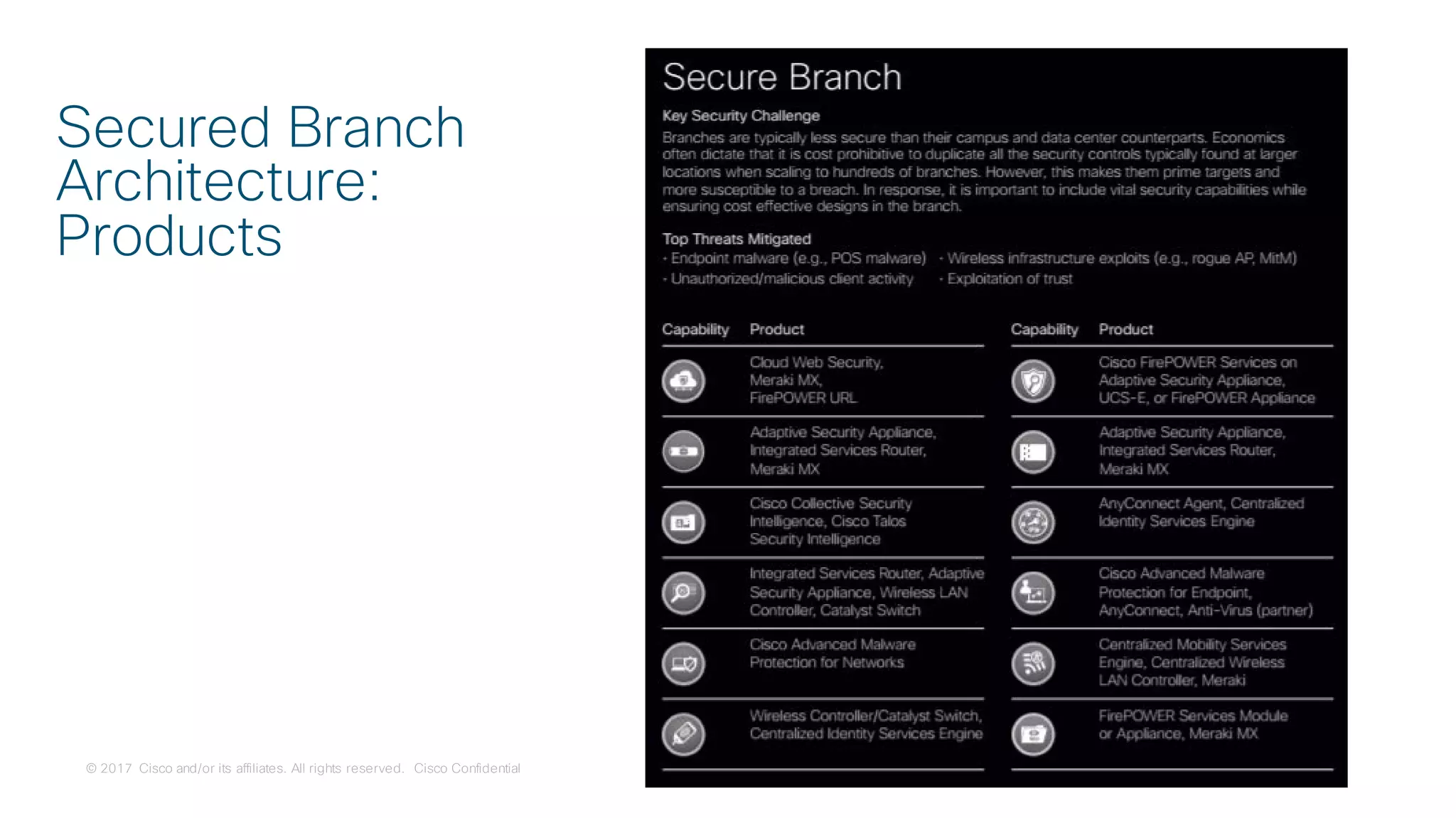
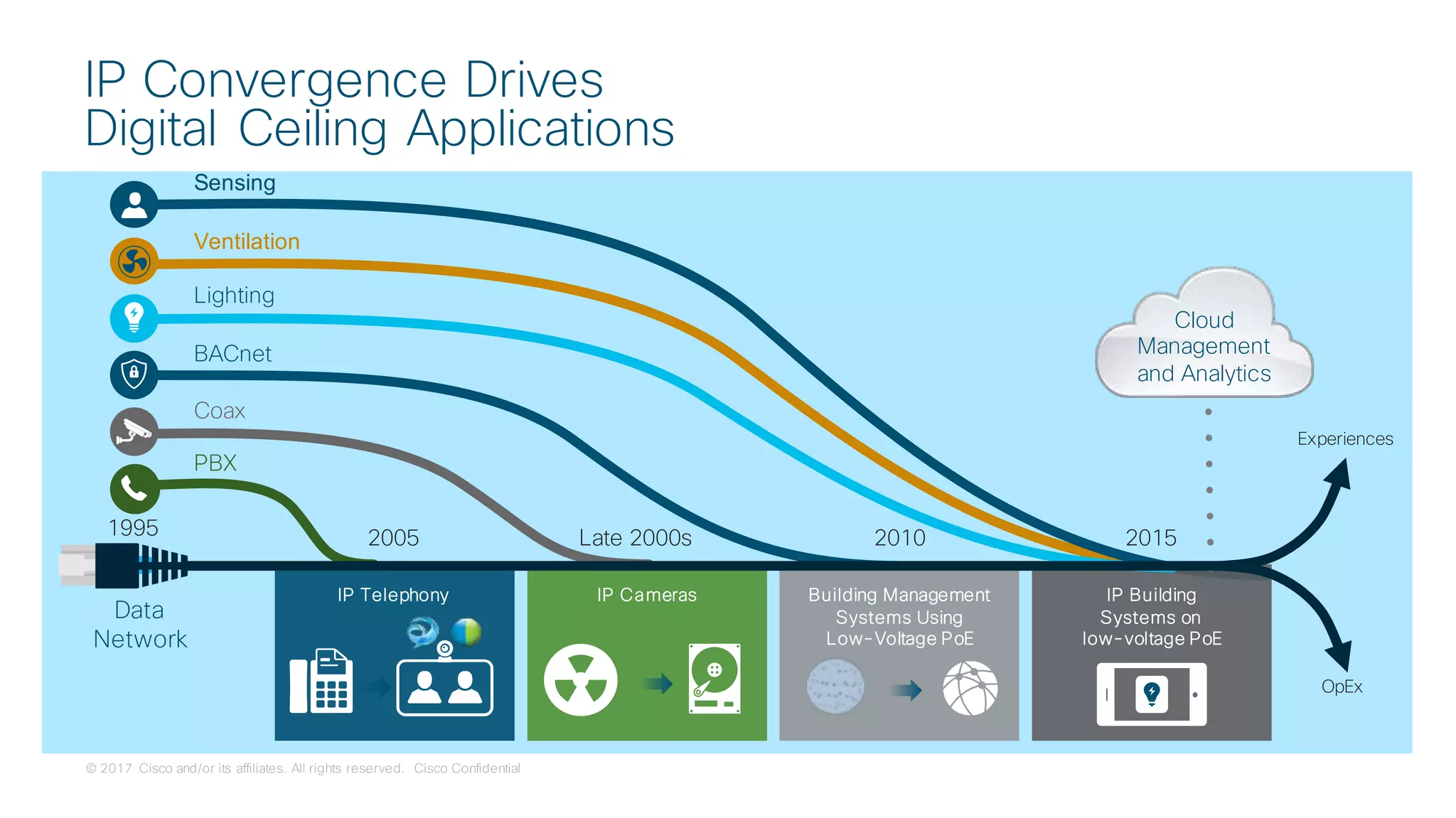
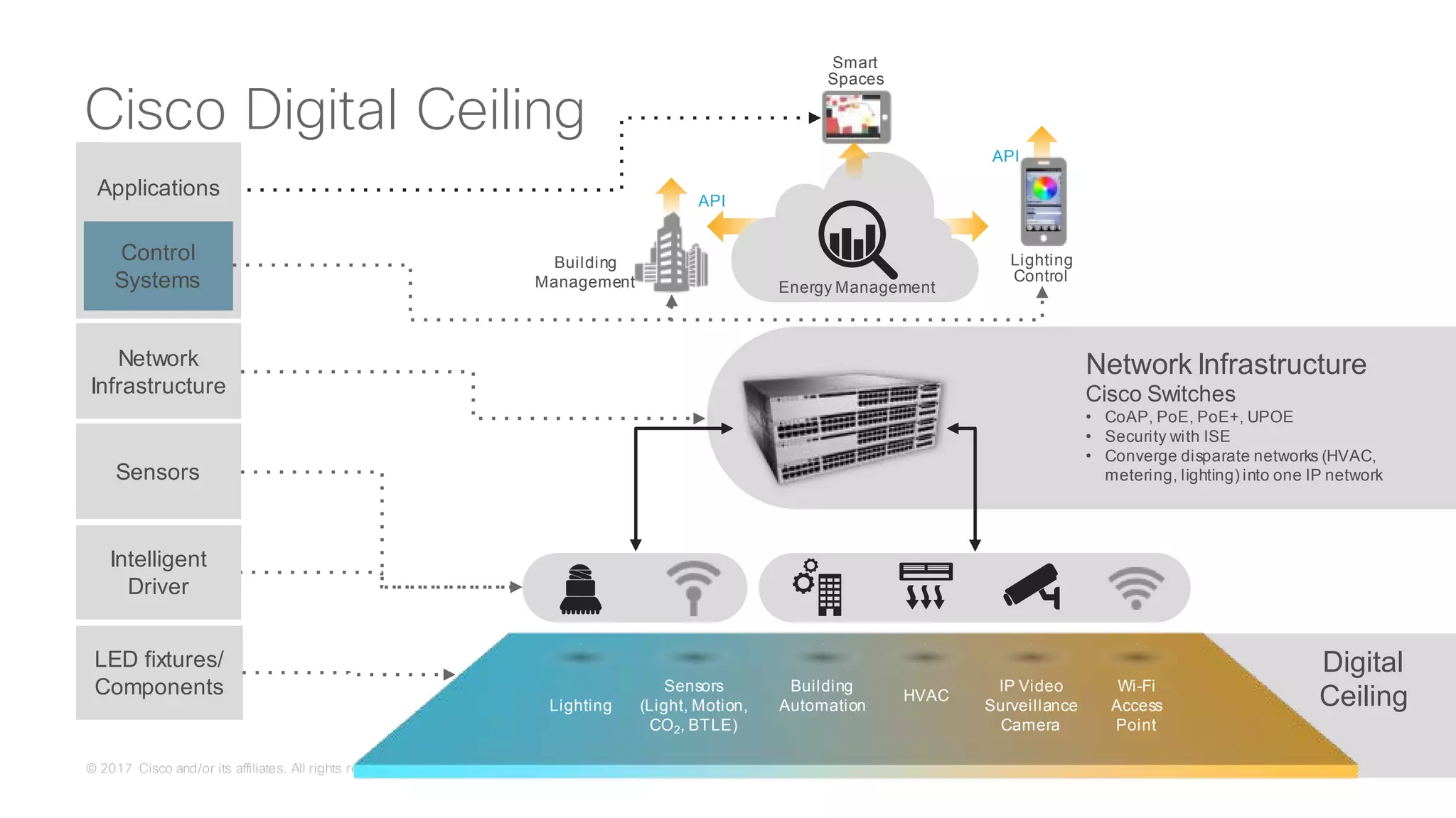
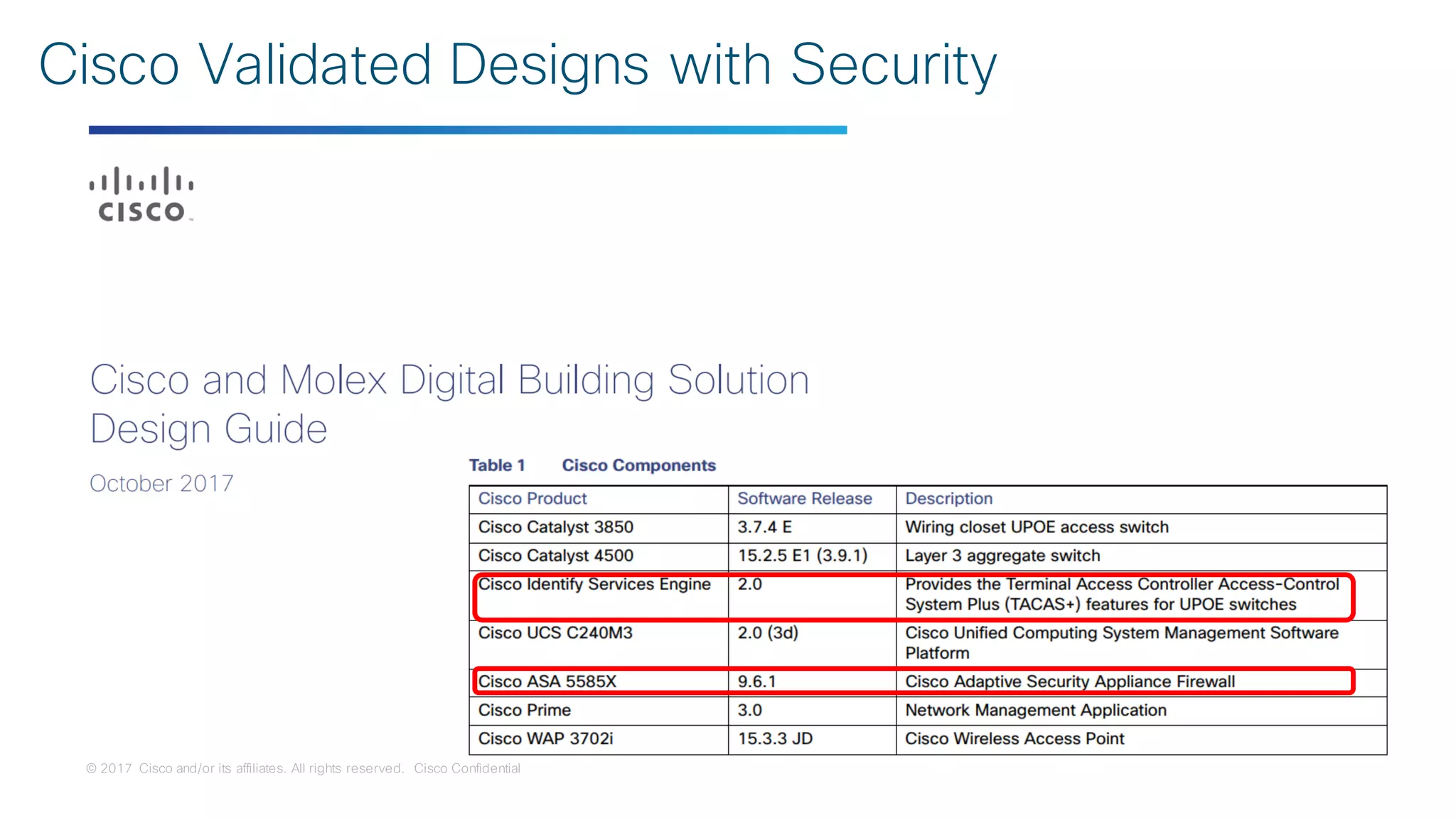
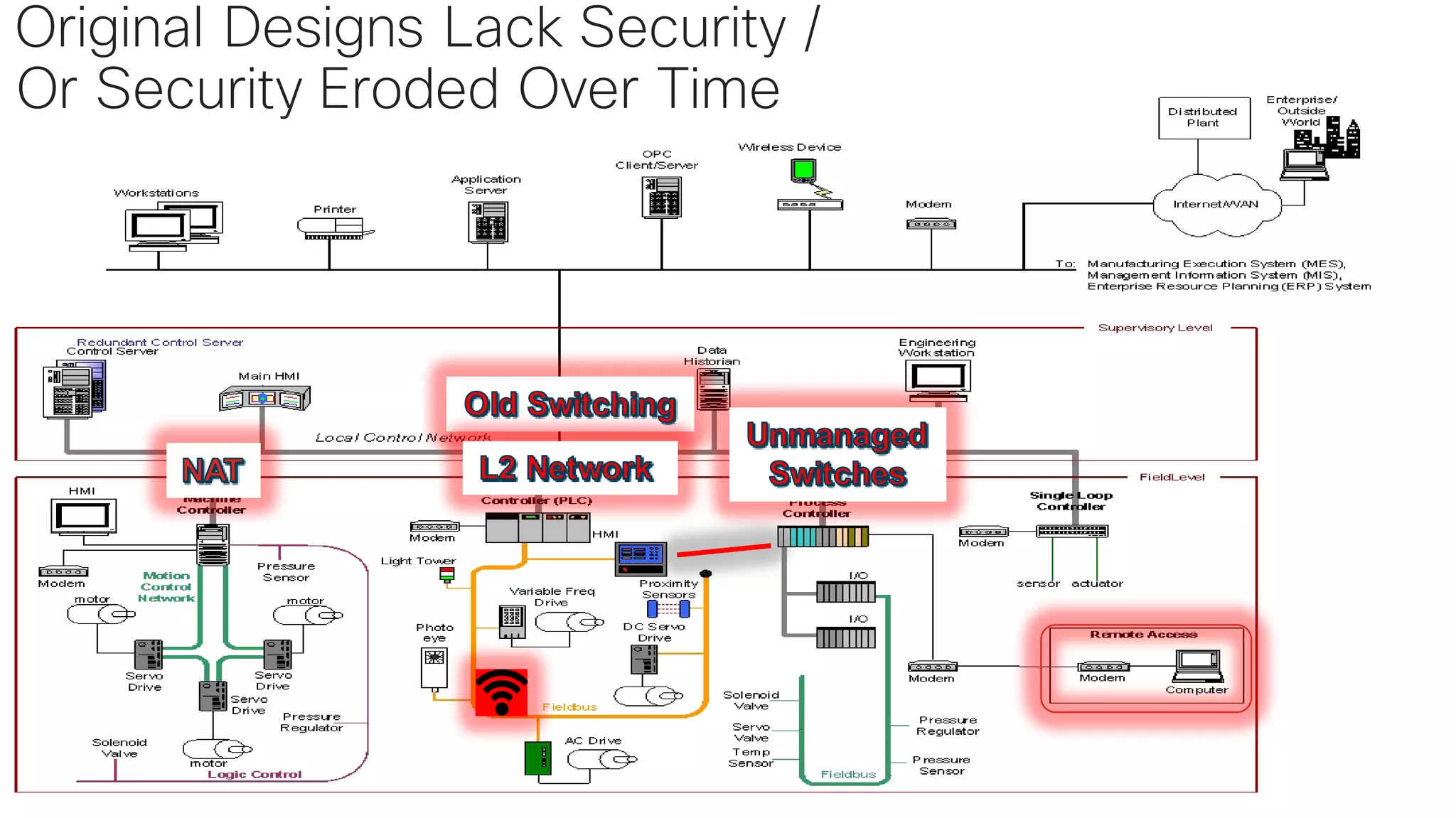
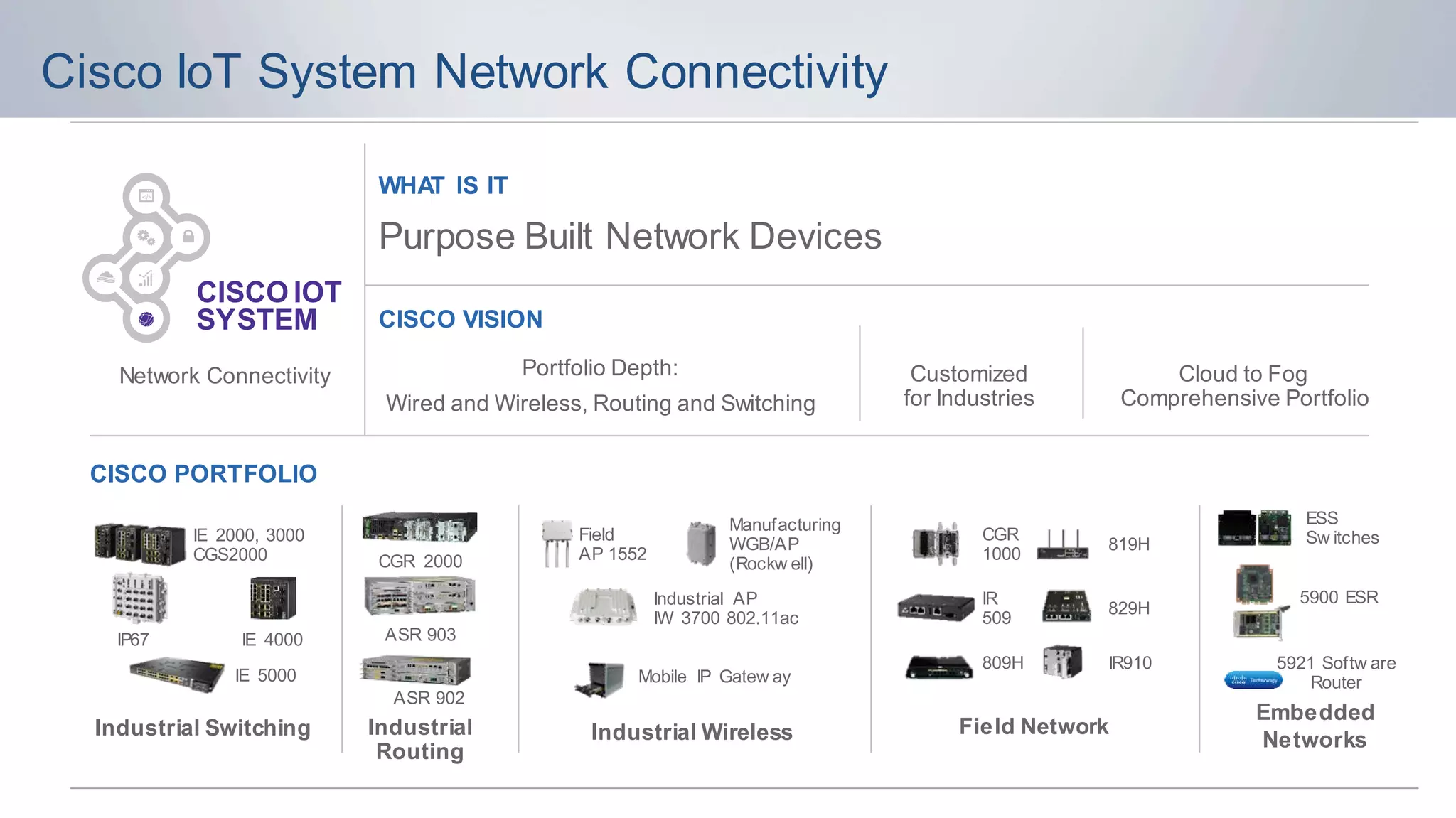
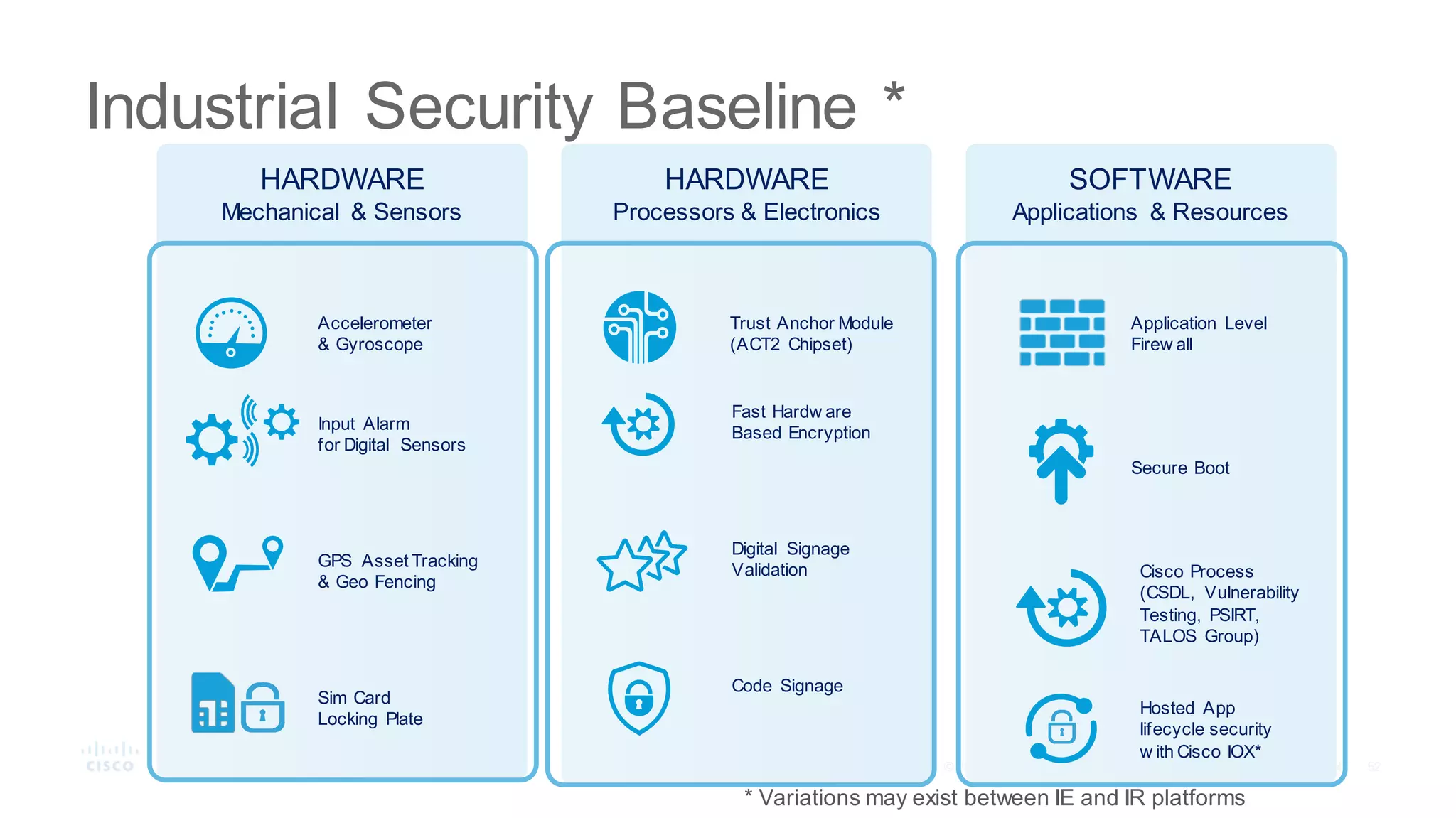
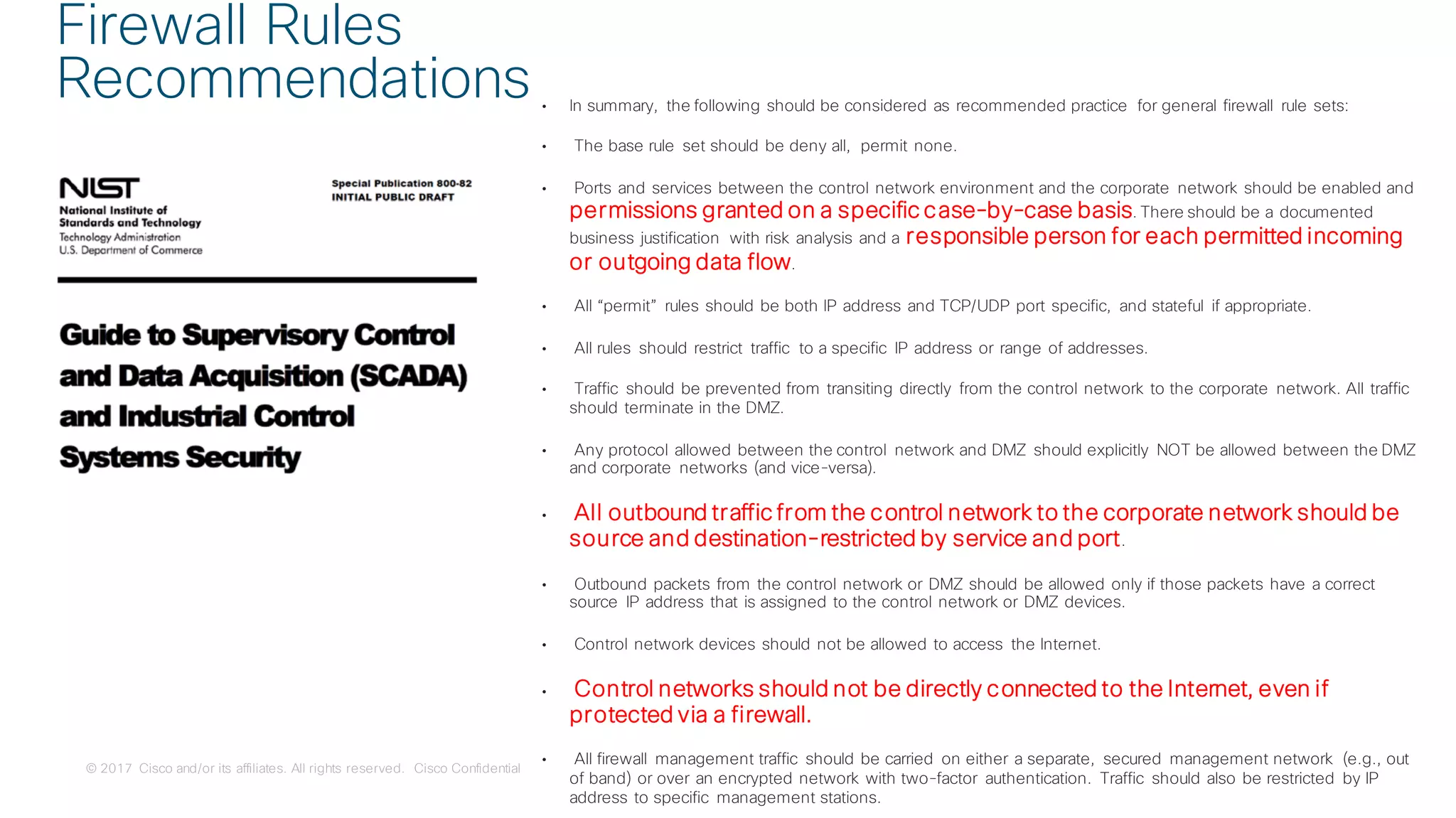
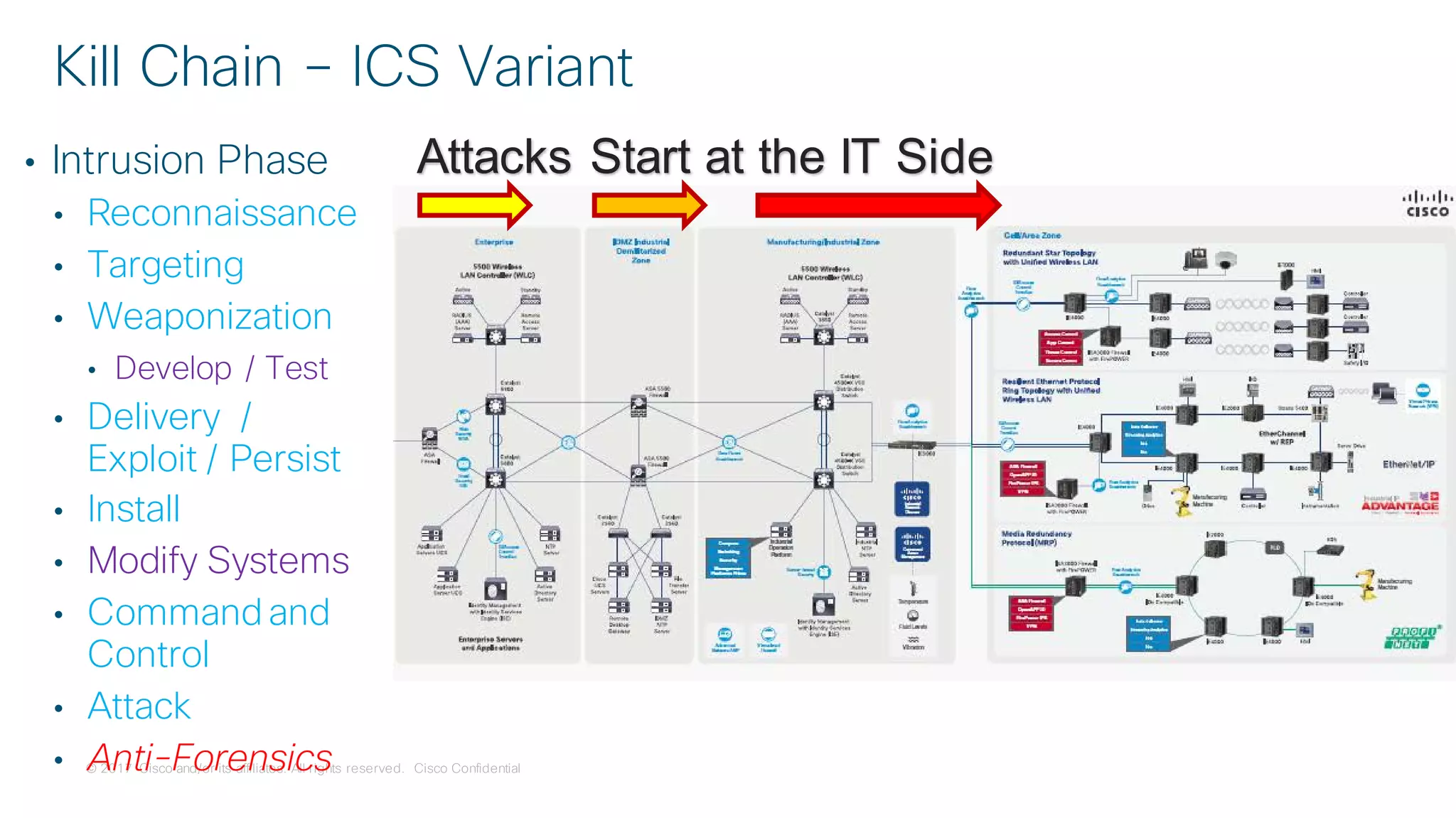
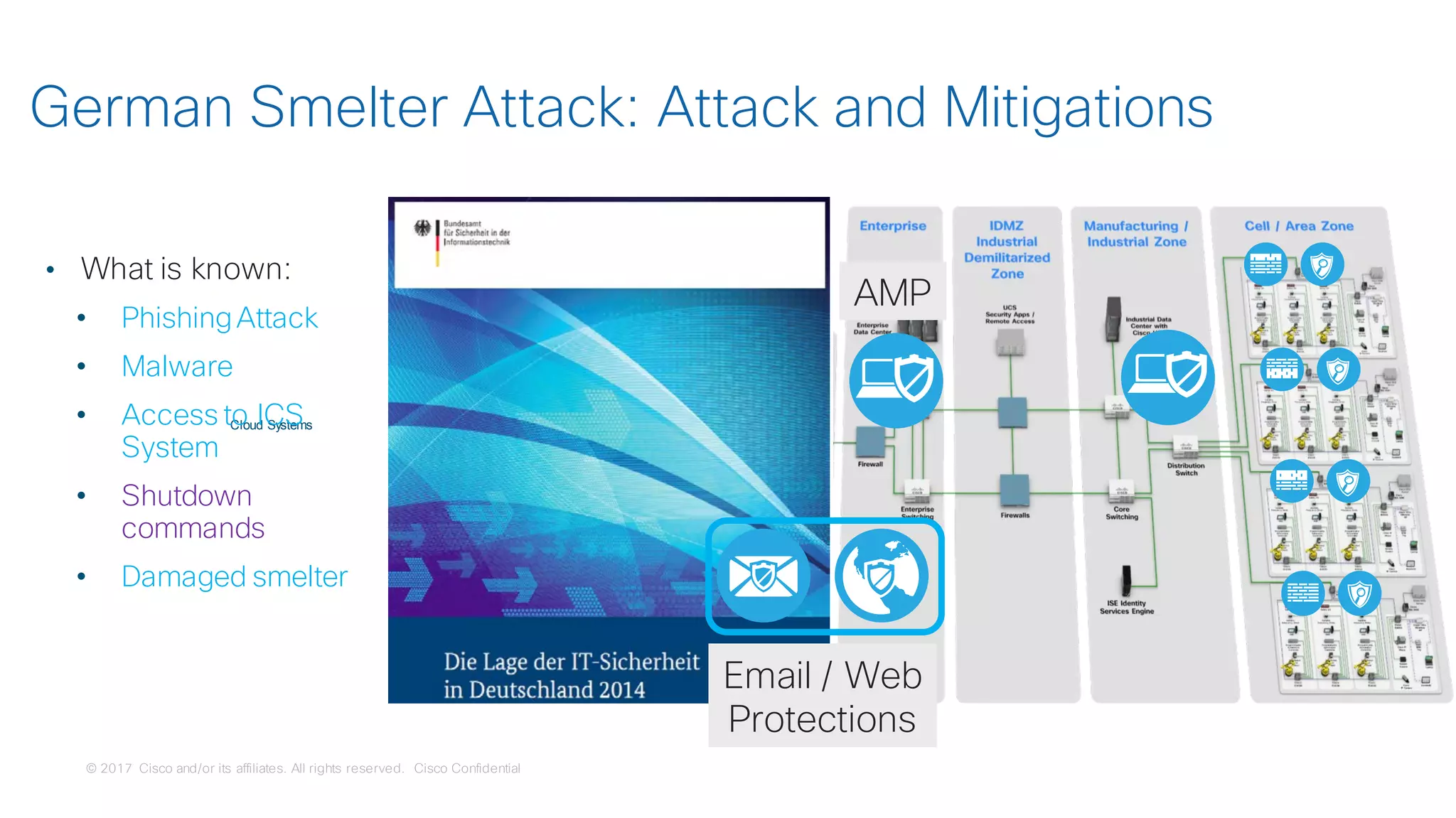
The document discusses strategies for securing the Internet of Things (IoT) and industrial systems, emphasizing a phased approach to security architecture. It outlines the importance of threat control and visibility within network environments while detailing various use cases, including secure connectivity and threat prevention. Recommendations for firewall rules and network segmentation are also provided to enhance operational security in connected environments.


![© 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
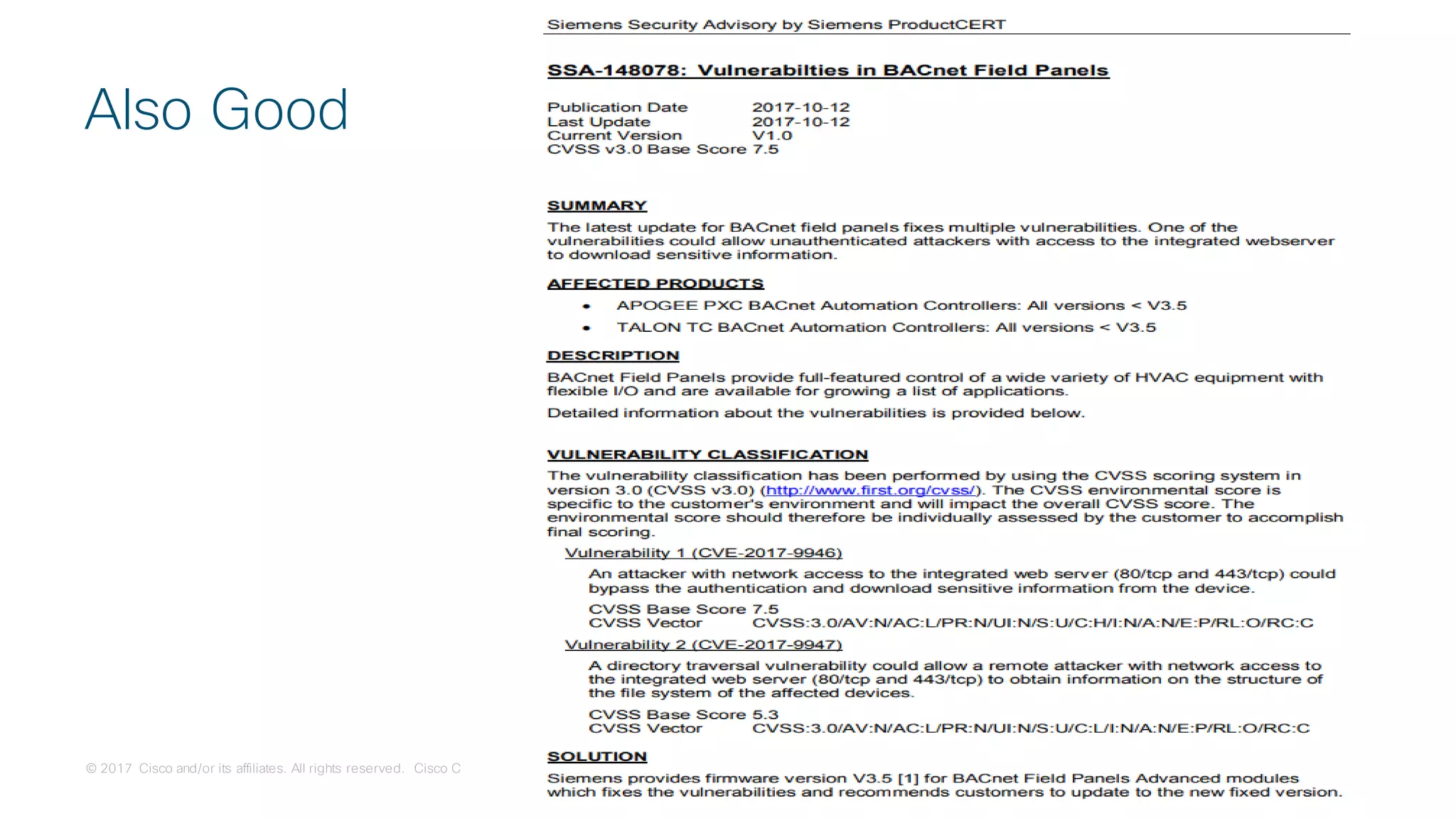
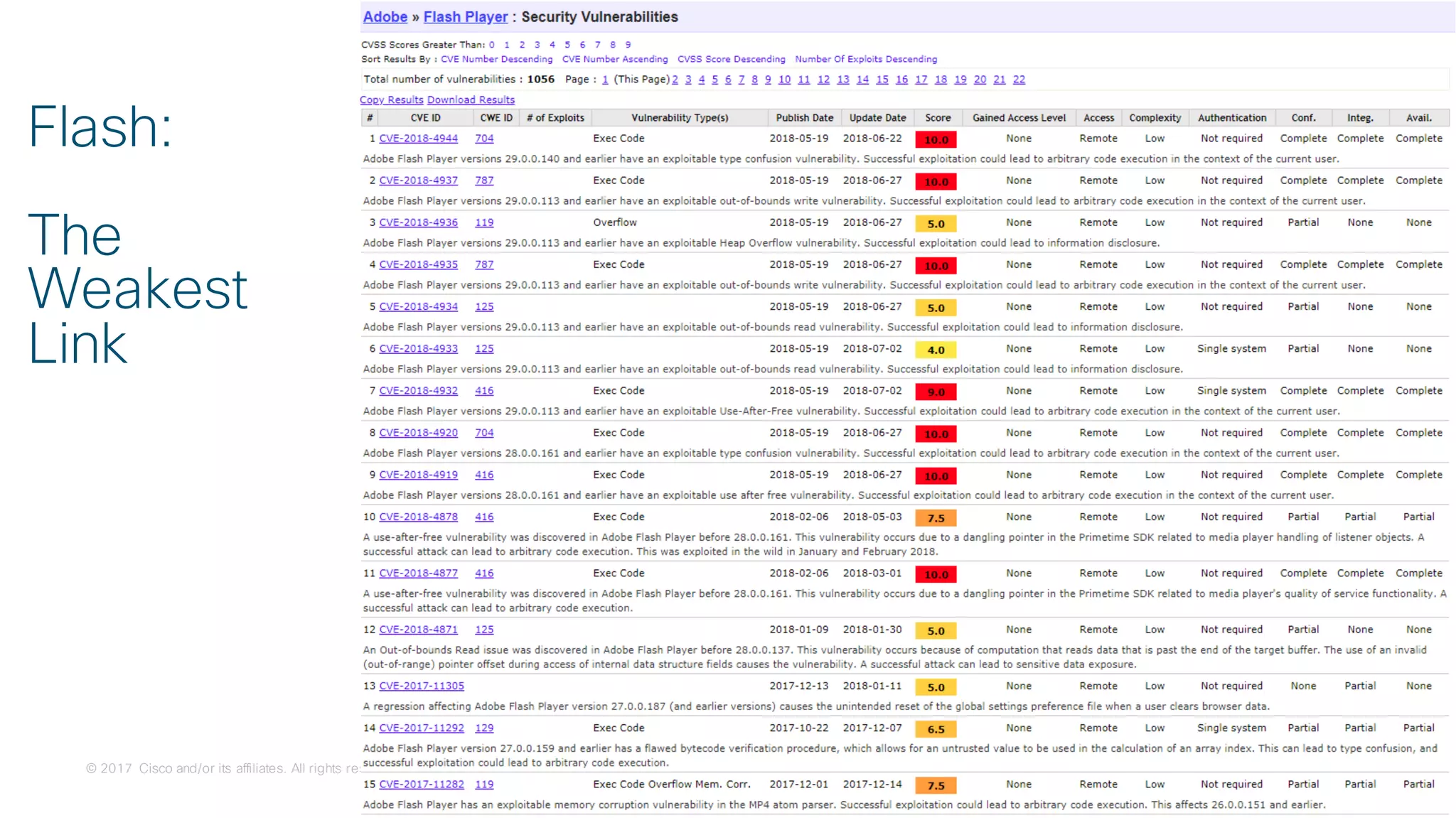
Quantifying Threats by Technology Stack
Vulnerabilities by Top 50 Vendors:
IT – 99.53%
IT Stack Vulns – 44%
[Web – 35%]OT – 0.47%](https://image.slidesharecdn.com/ciscoconnecttoronto2018-iot-unlockthepowerofdata-securingtheinternetofthings-fromthreatvectorstothea-181023171826/75/Cisco-Connect-Toronto-2018-IOT-unlock-the-power-of-data-securing-the-internet-of-things-from-threat-vectors-to-the-architectures-16-2048.jpg)




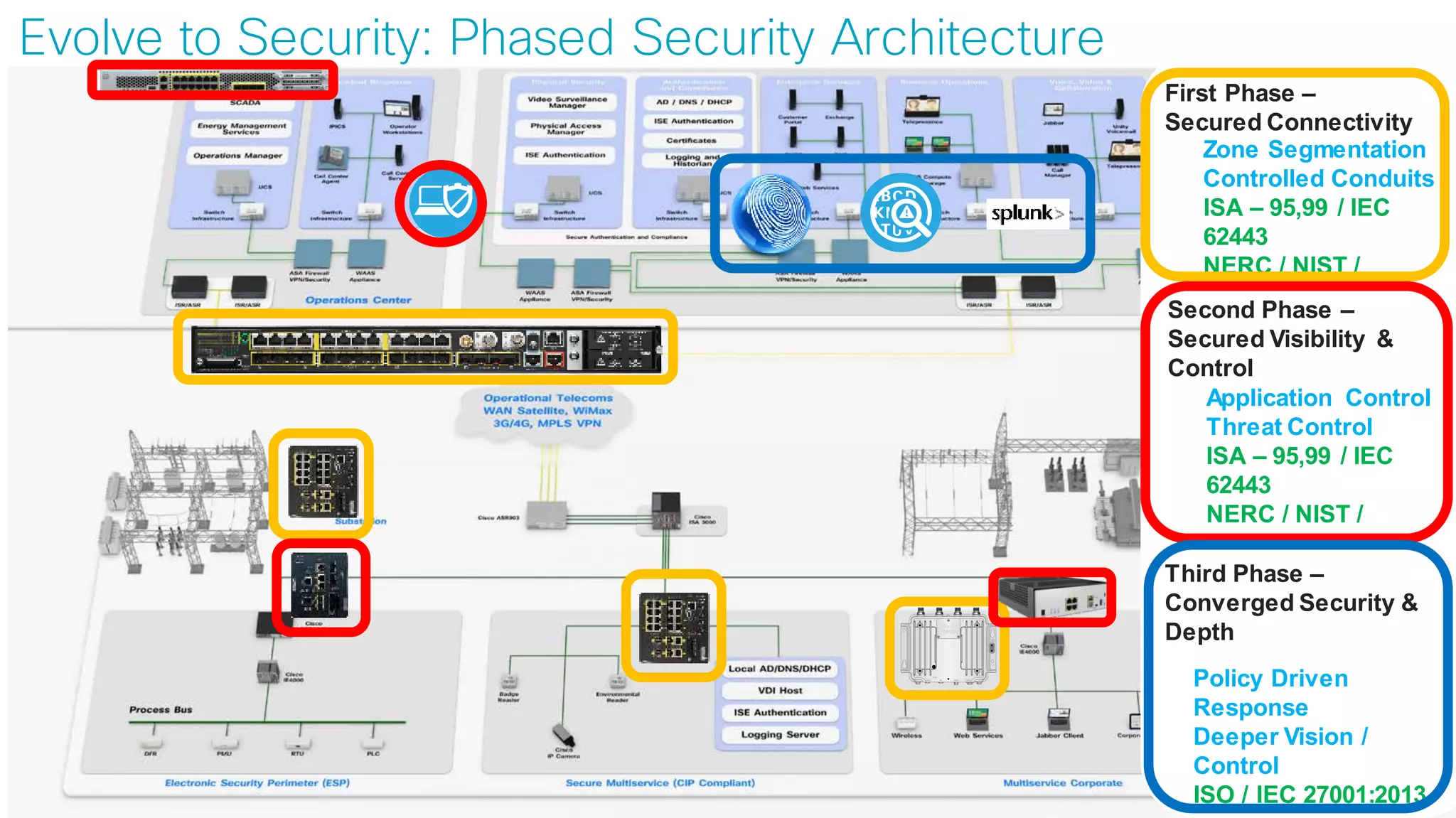

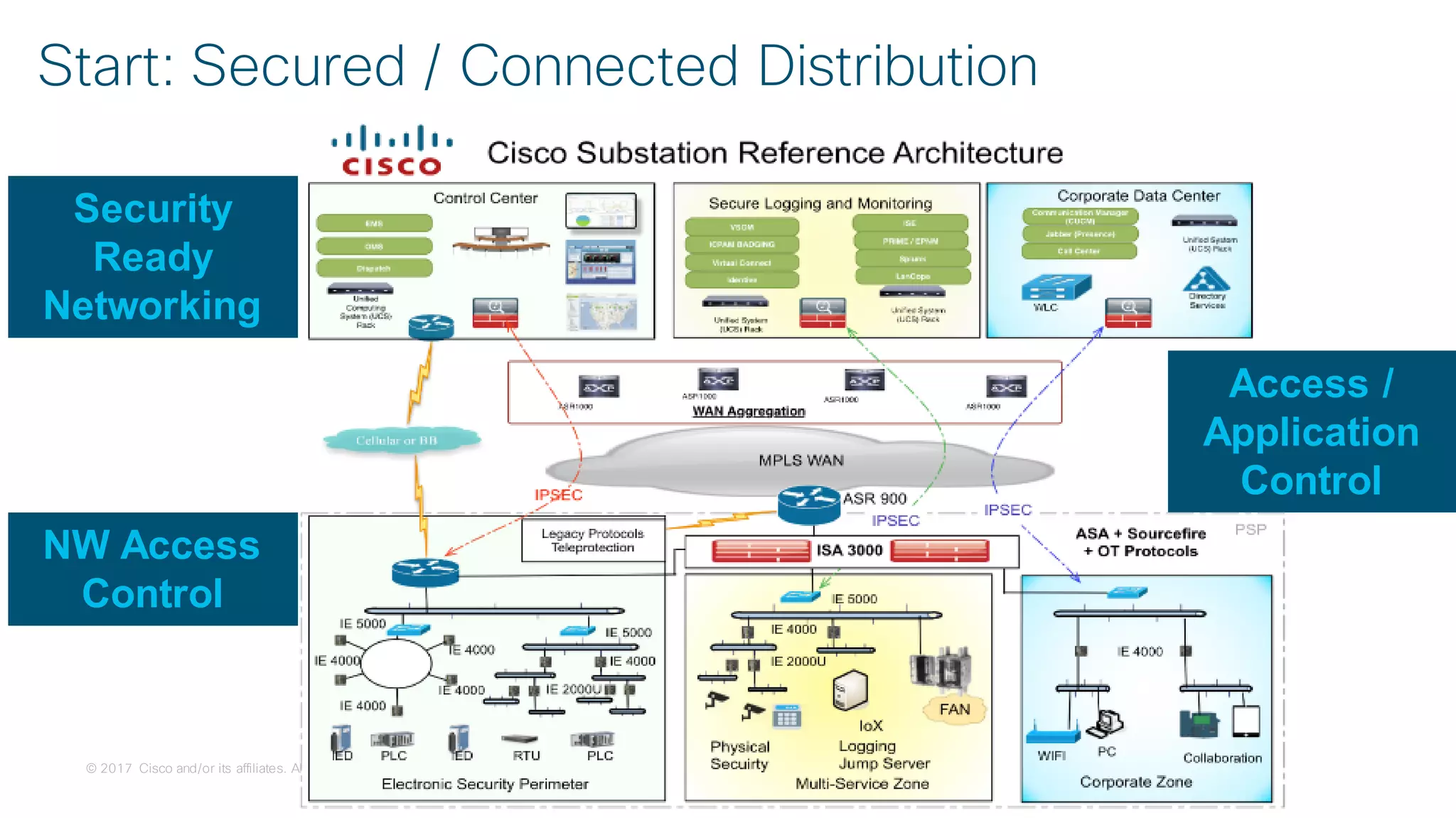
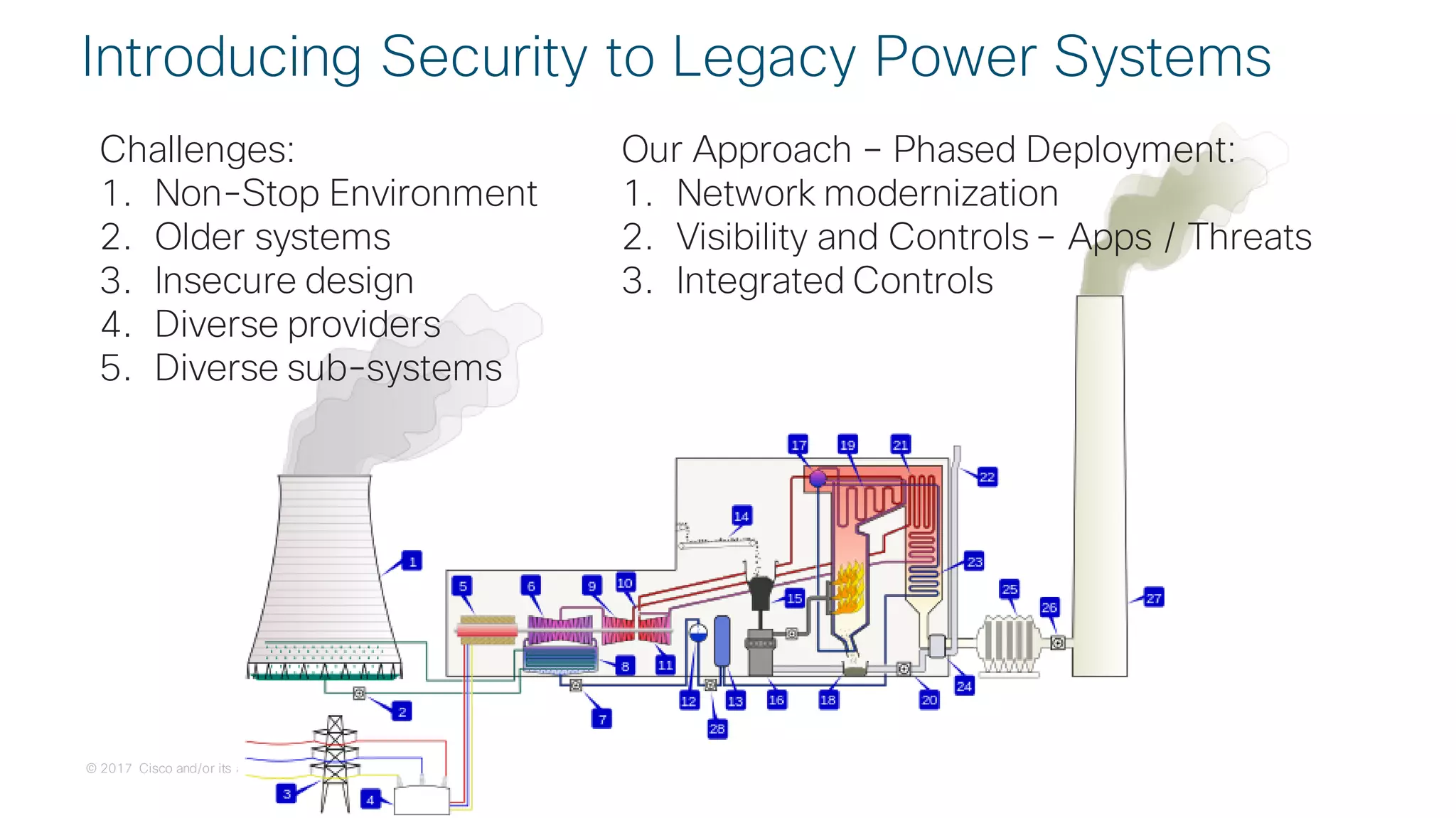
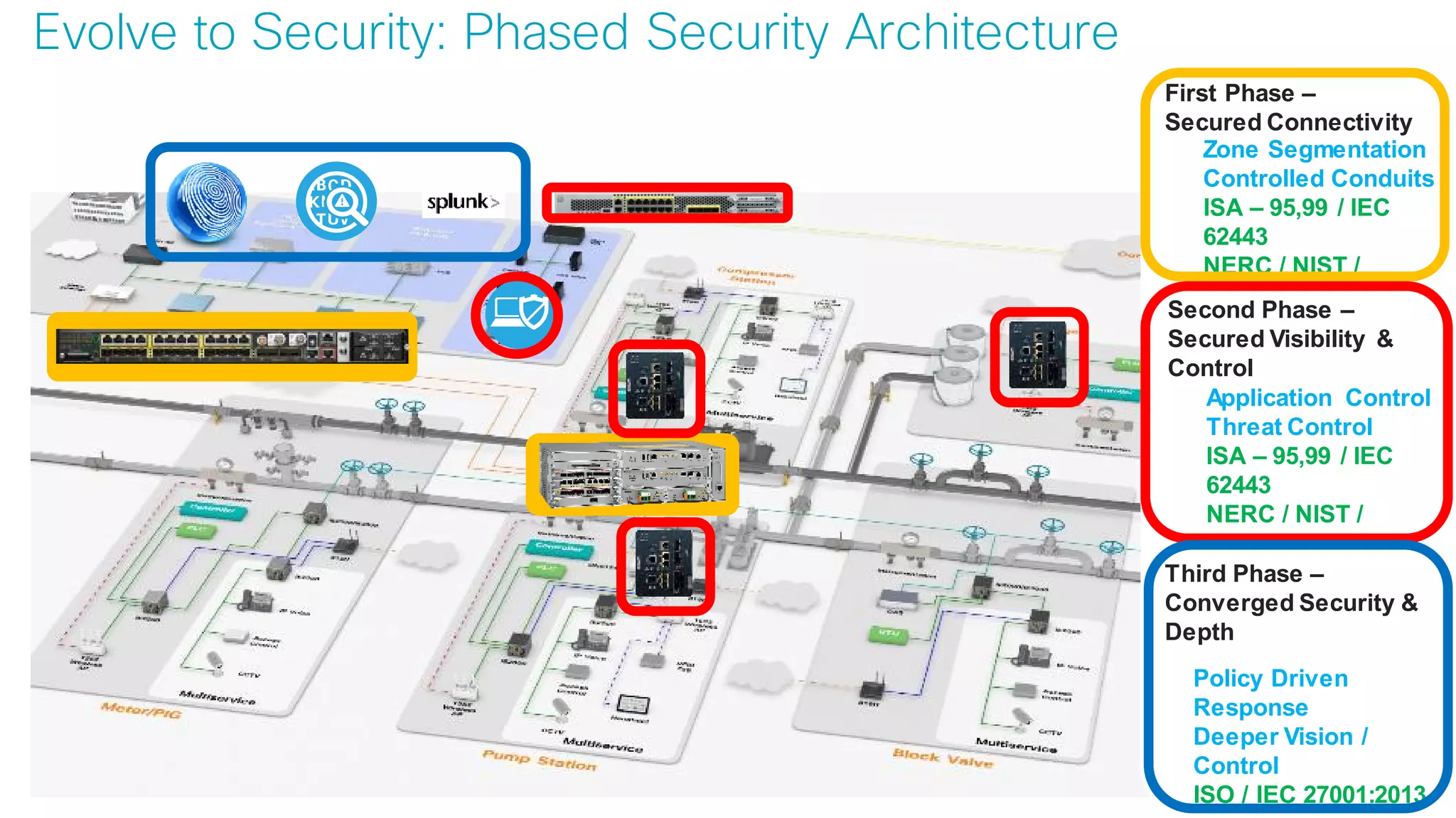

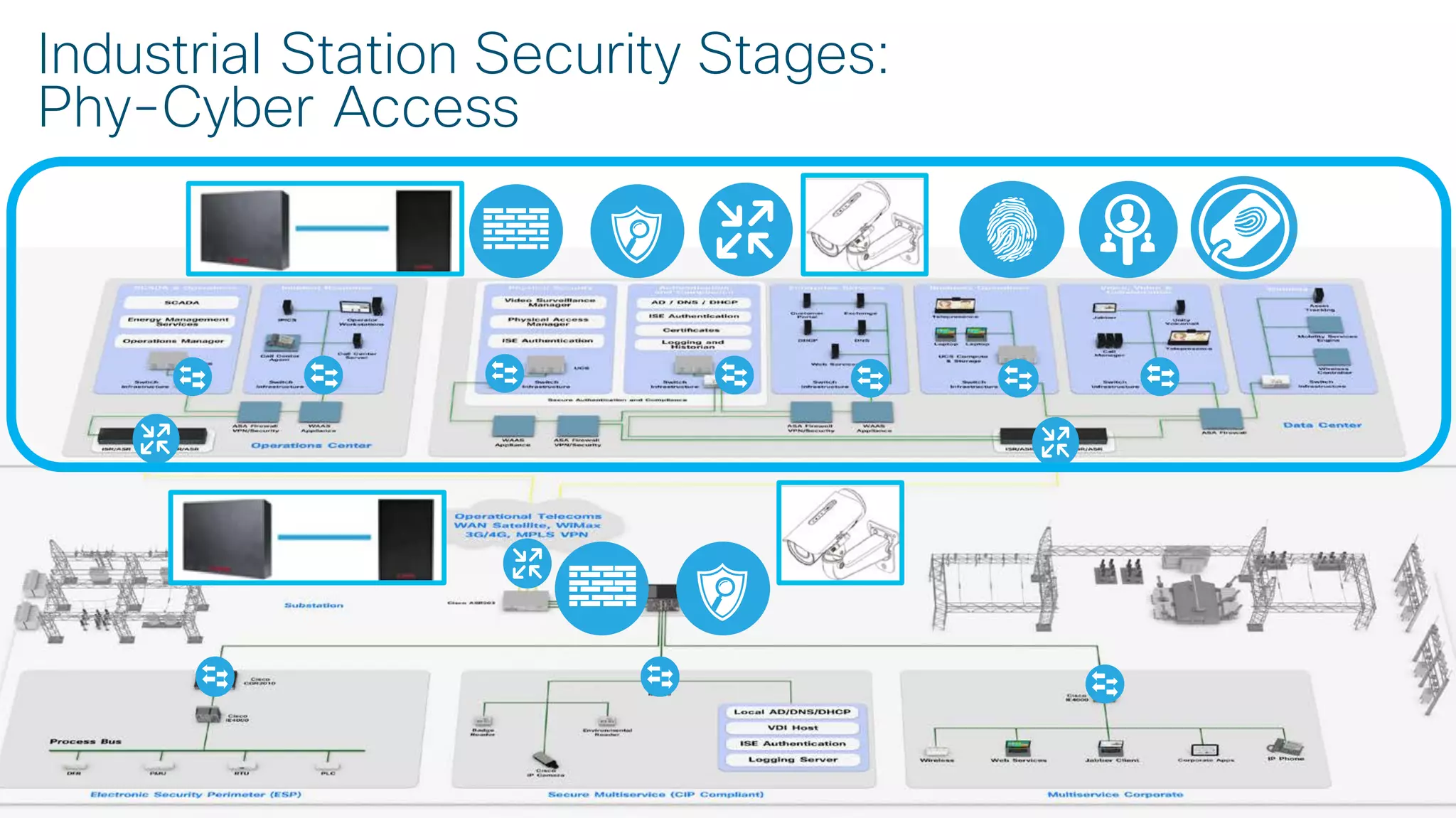
![© 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
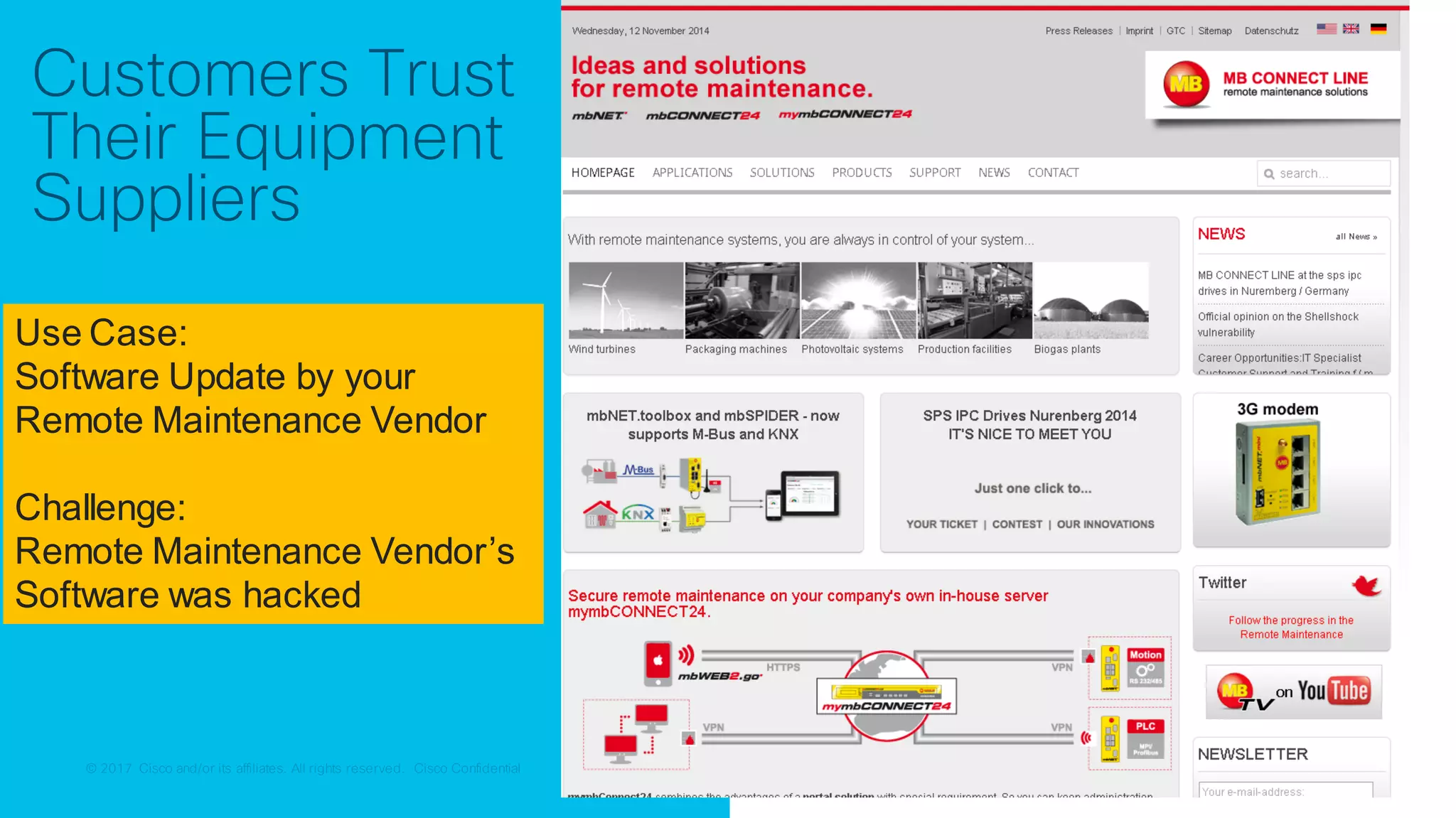
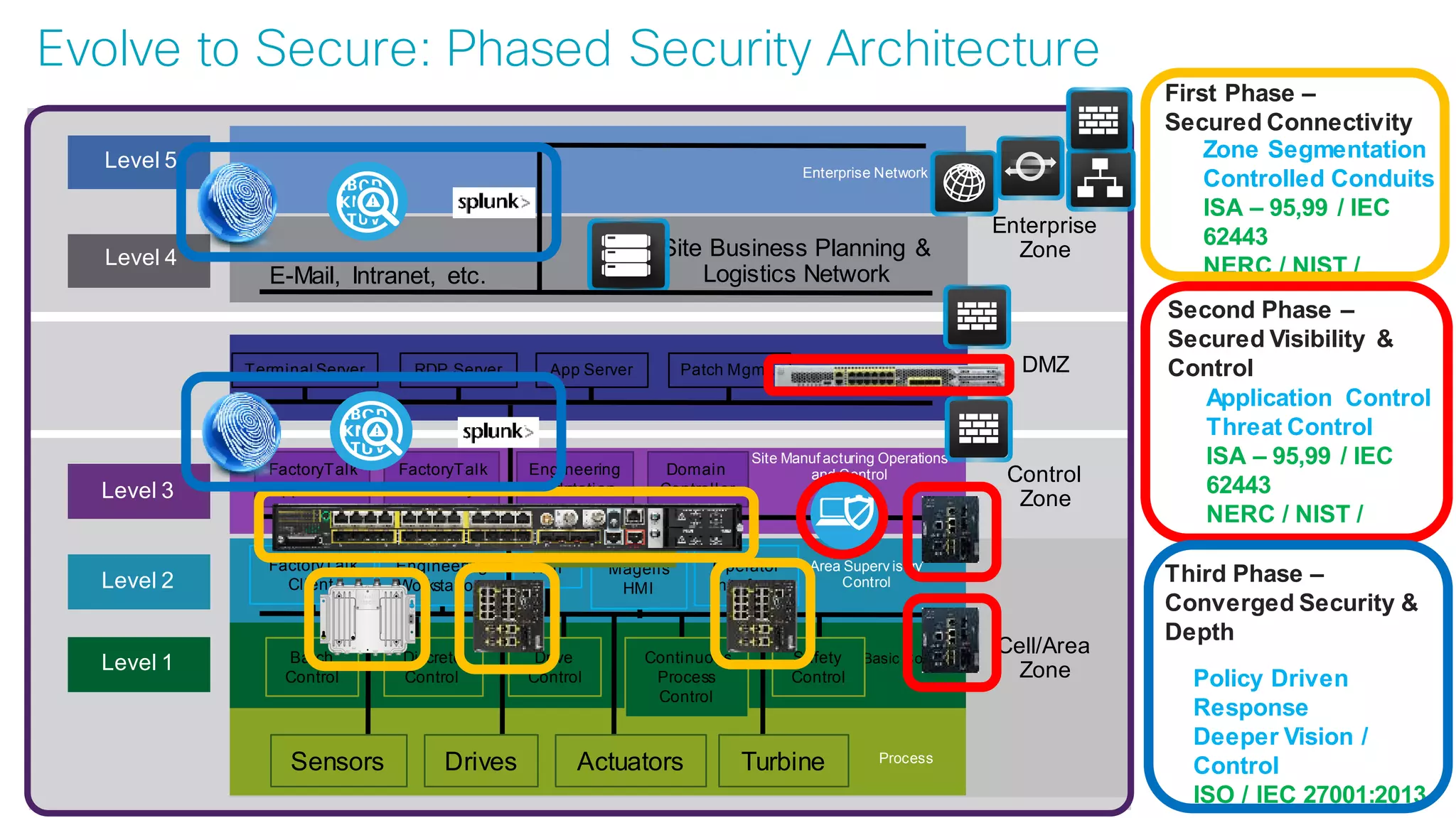
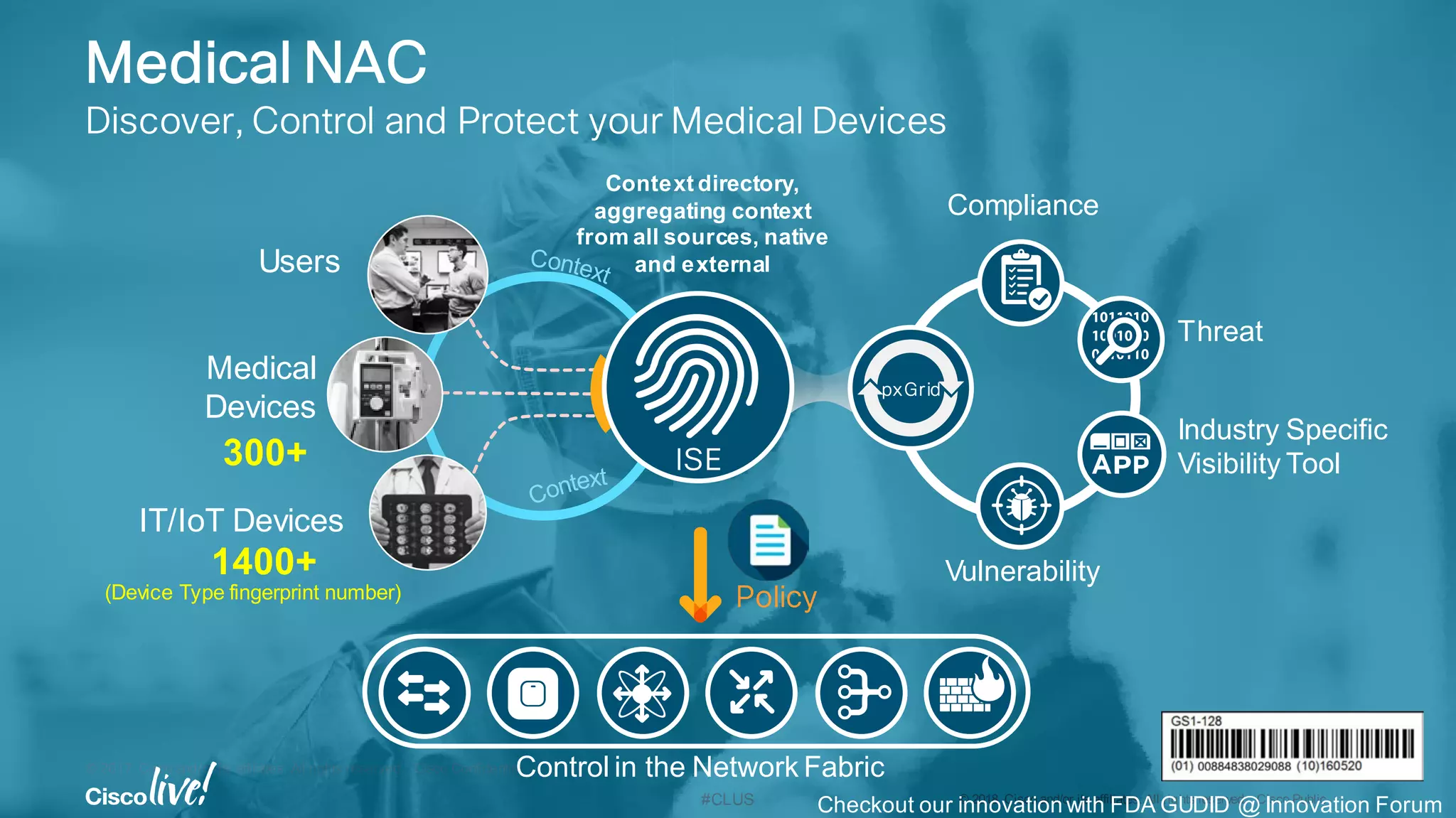
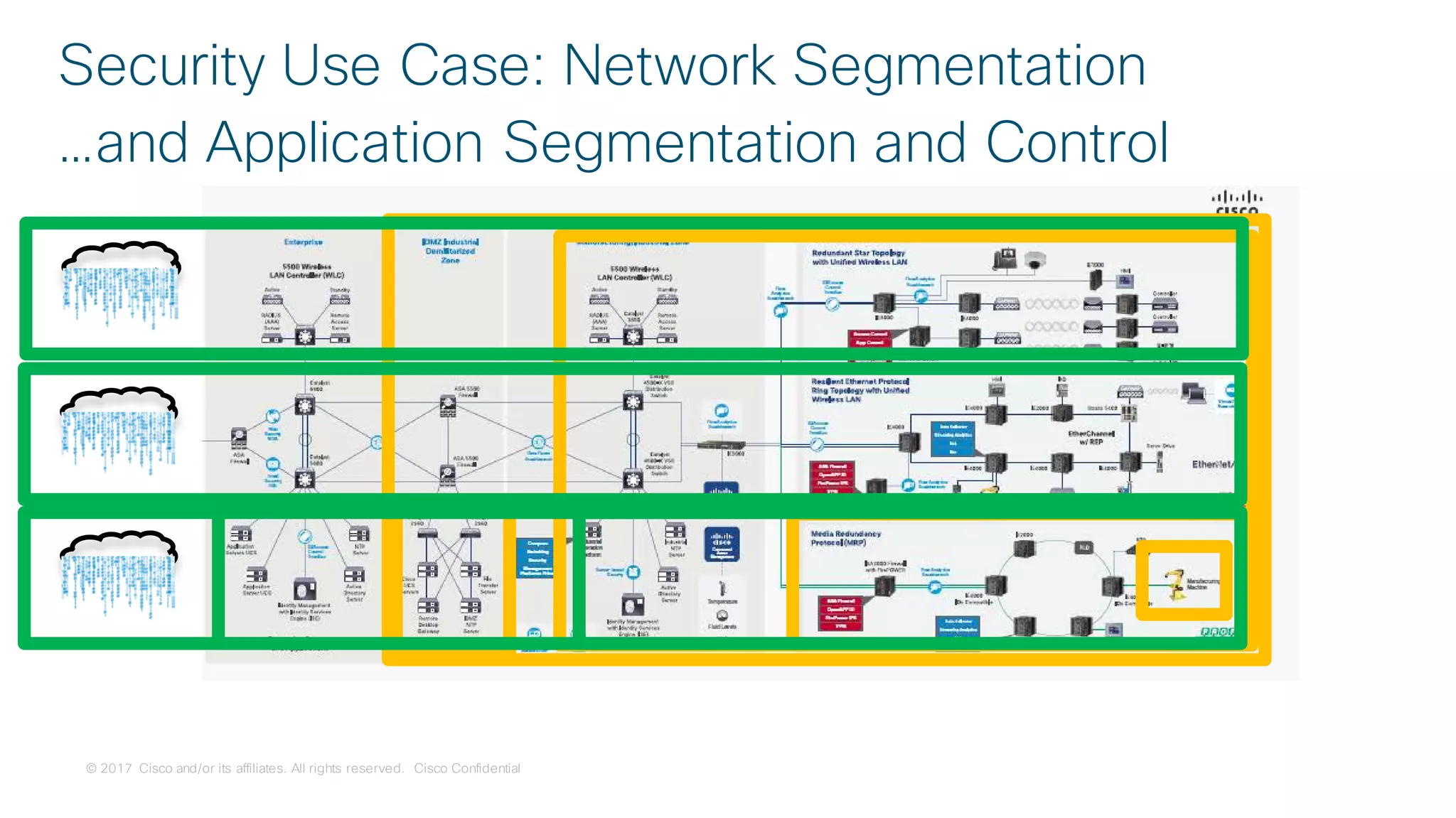
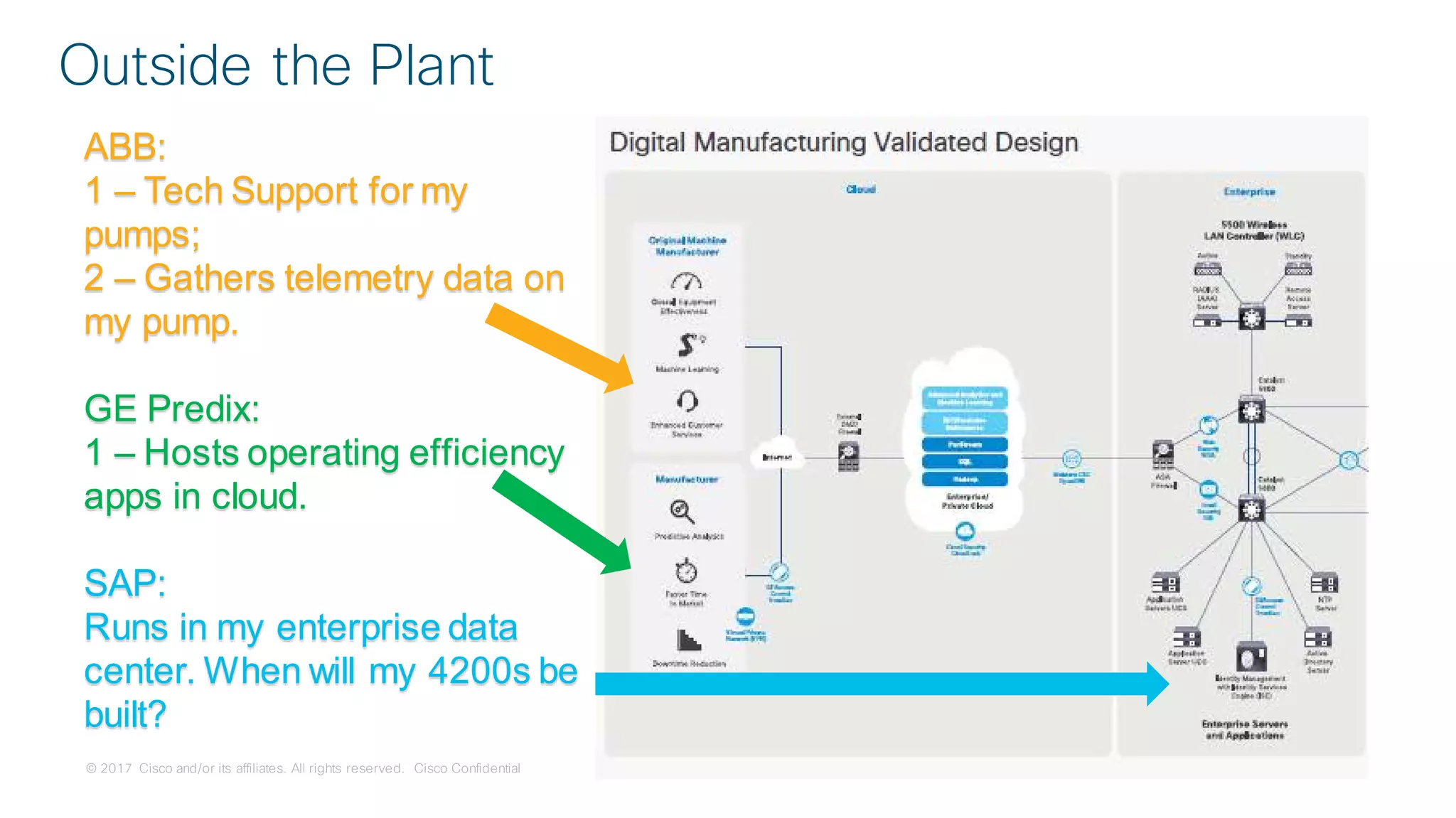
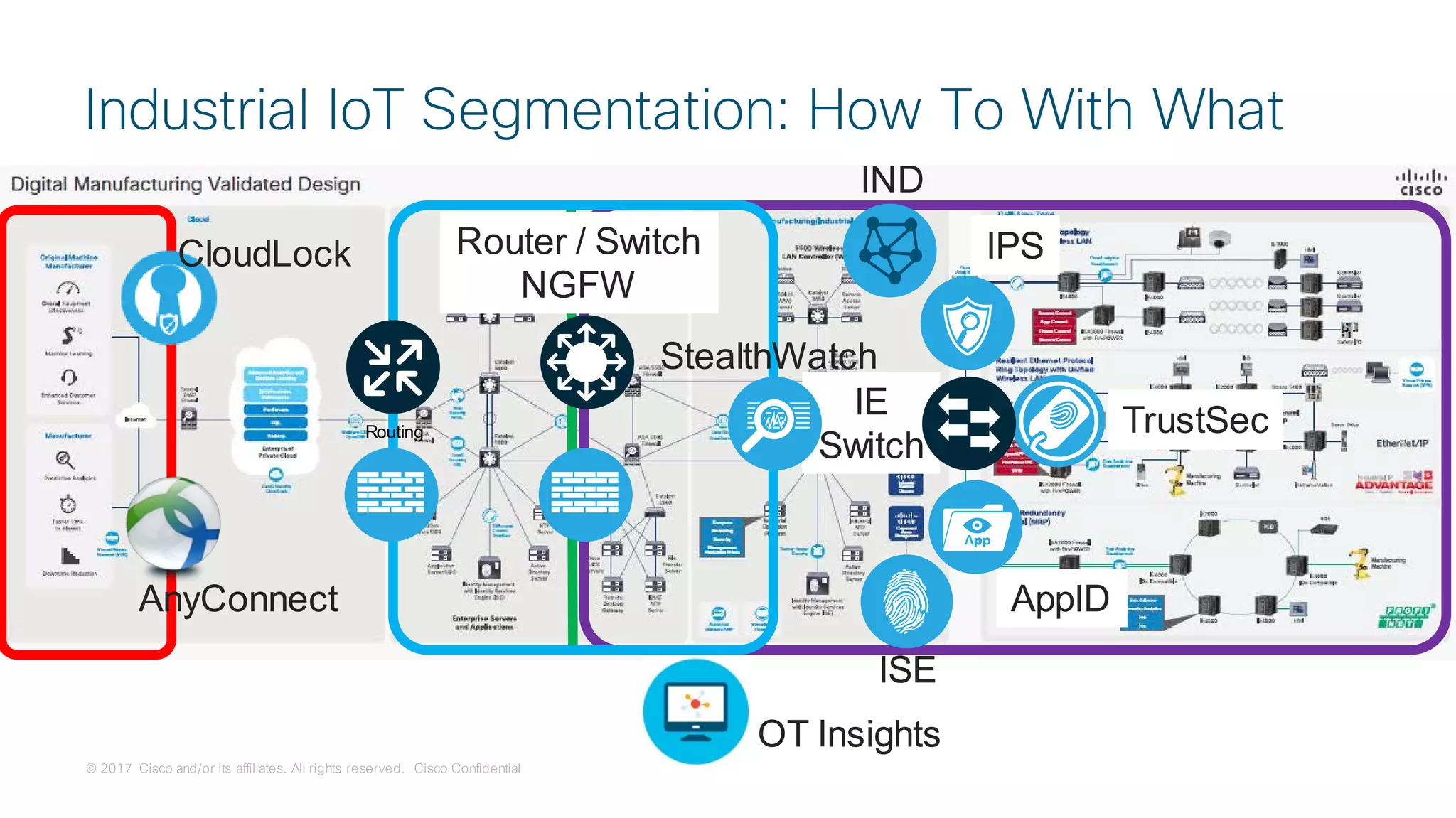
Use Case:
Secure Connectivity
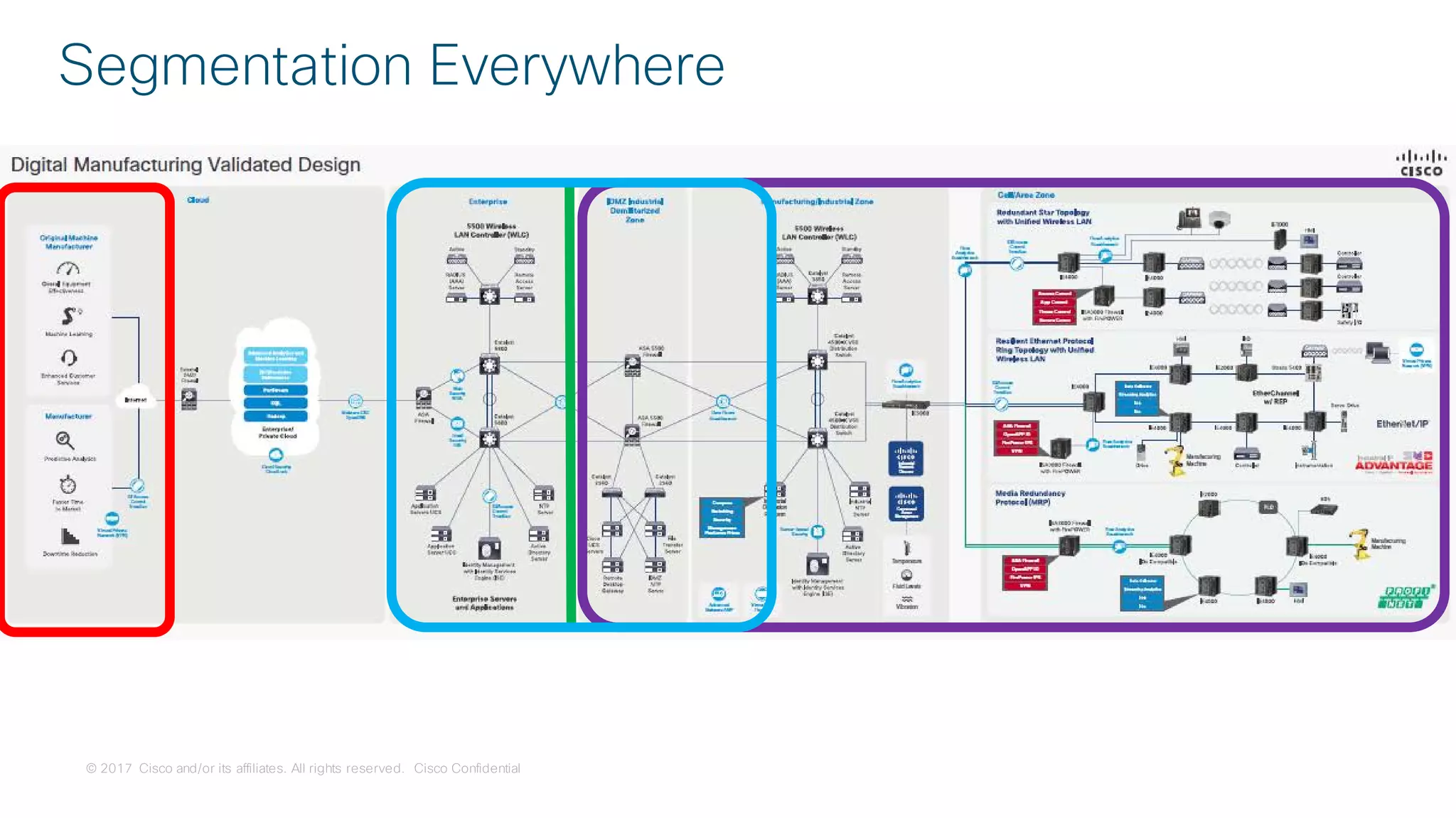
[Segmentation]](https://image.slidesharecdn.com/ciscoconnecttoronto2018-iot-unlockthepowerofdata-securingtheinternetofthings-fromthreatvectorstothea-181023171826/75/Cisco-Connect-Toronto-2018-IOT-unlock-the-power-of-data-securing-the-internet-of-things-from-threat-vectors-to-the-architectures-45-2048.jpg)





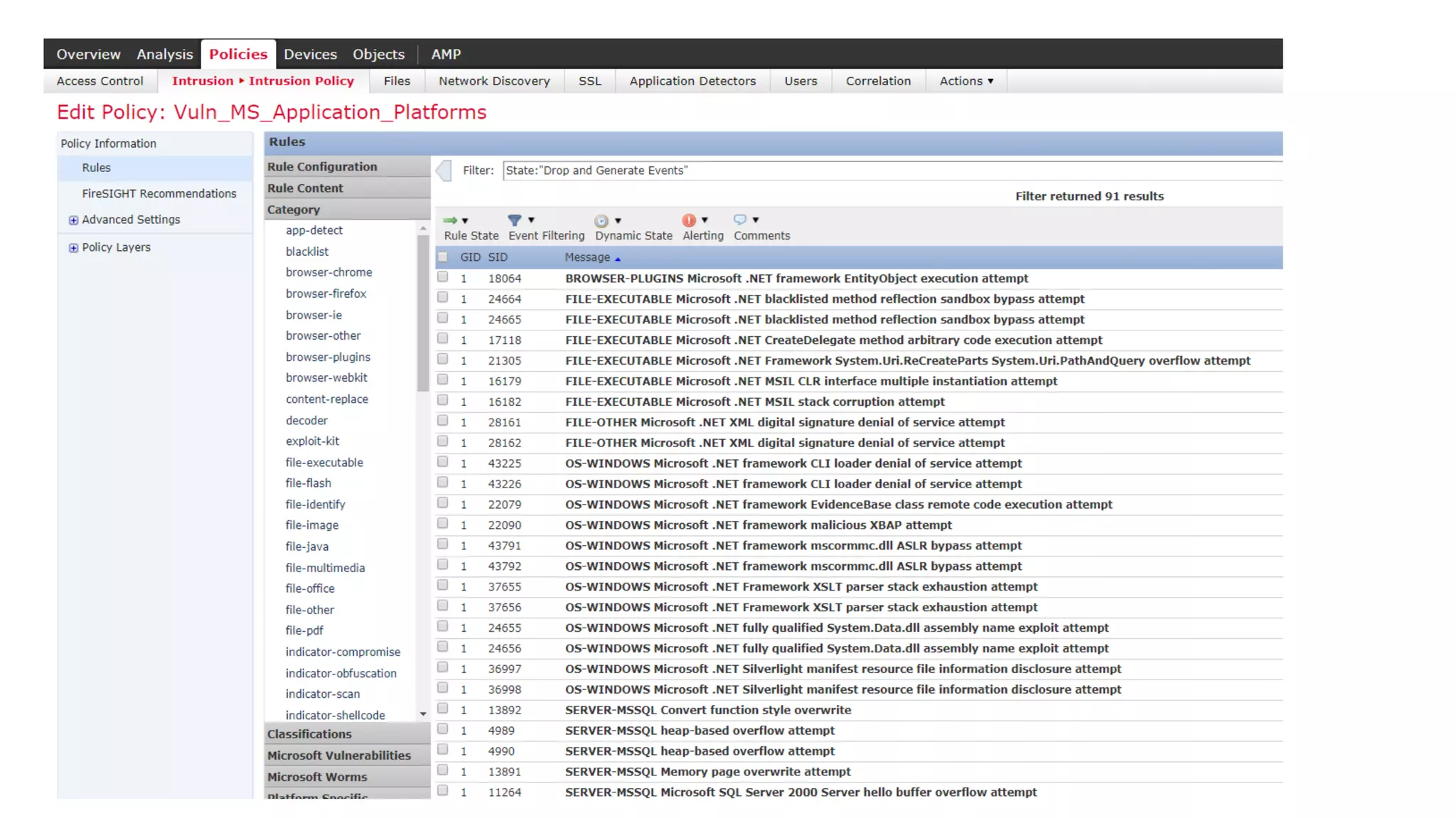
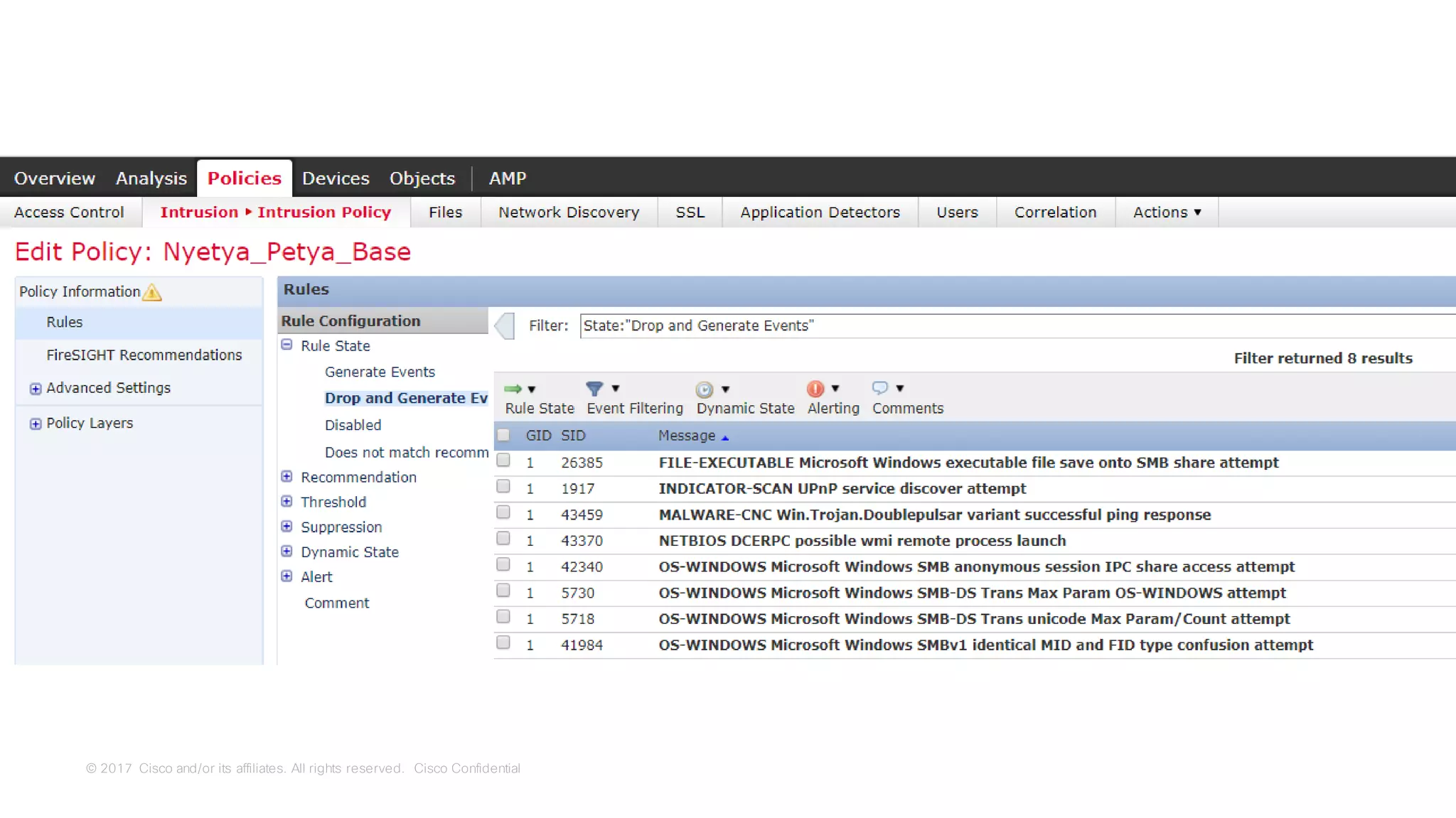
![© 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
Use Case:
Application Visibility and
Control
[Safety / Security]](https://image.slidesharecdn.com/ciscoconnecttoronto2018-iot-unlockthepowerofdata-securingtheinternetofthings-fromthreatvectorstothea-181023171826/75/Cisco-Connect-Toronto-2018-IOT-unlock-the-power-of-data-securing-the-internet-of-things-from-threat-vectors-to-the-architectures-71-2048.jpg)
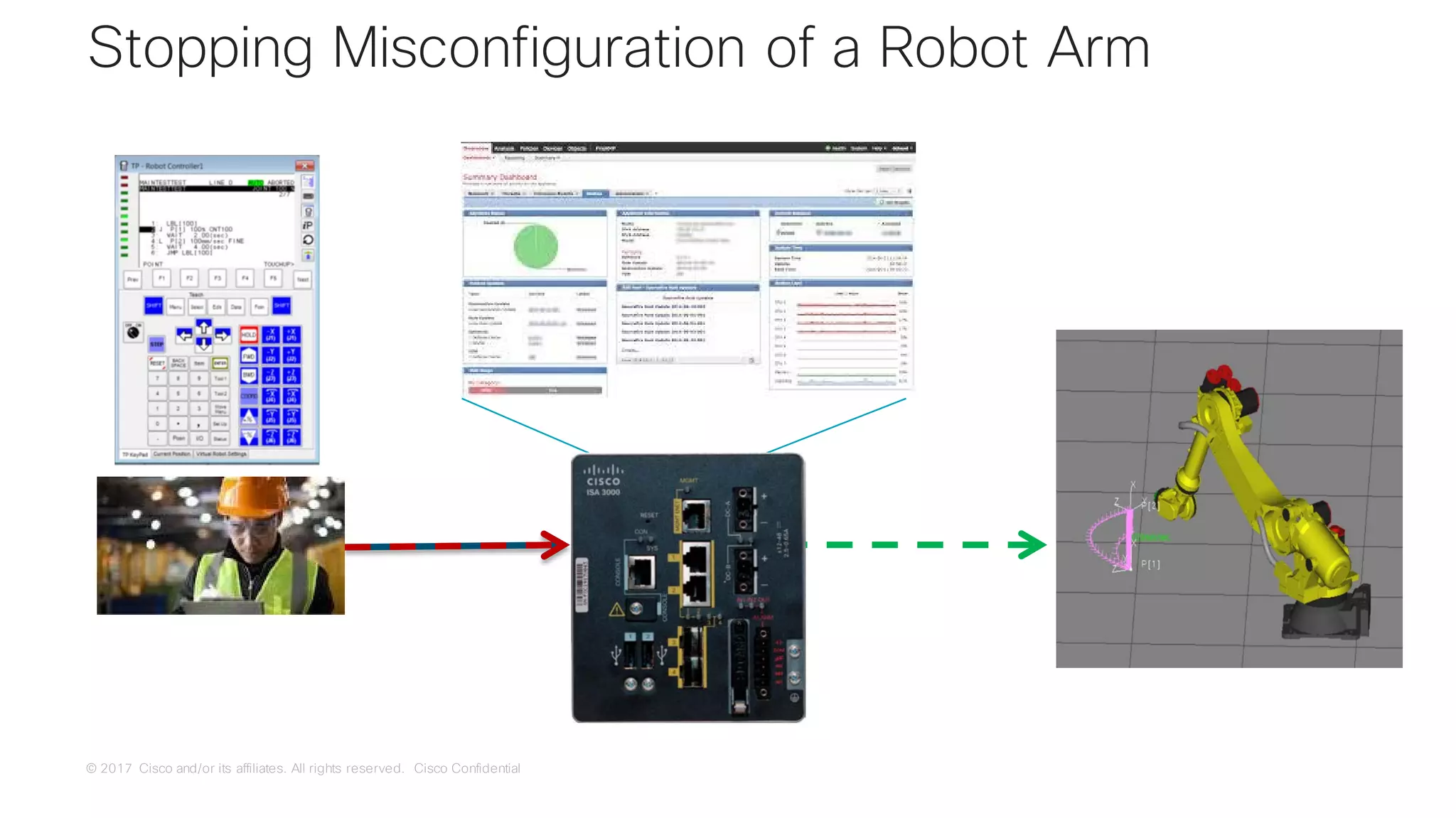
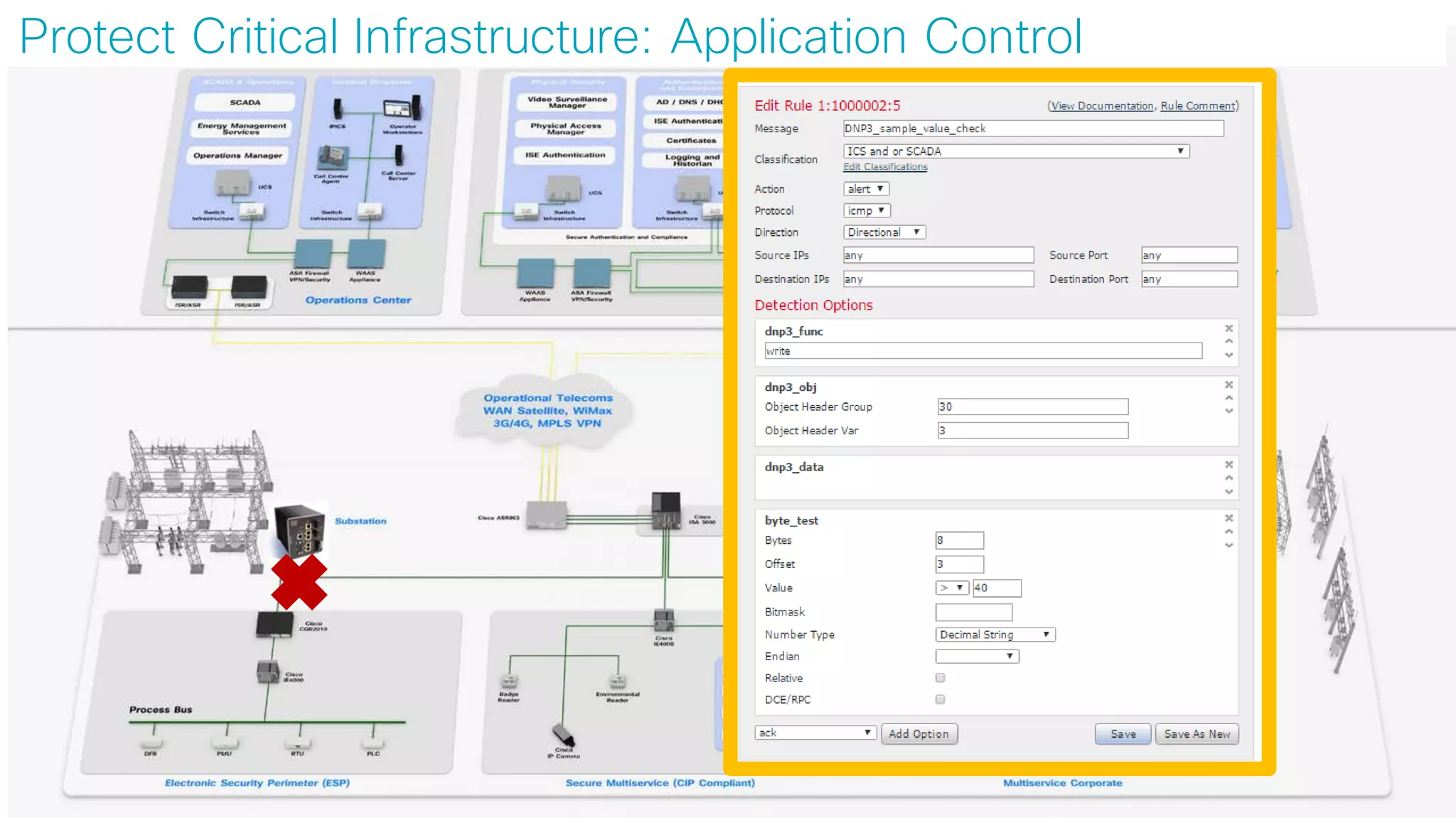

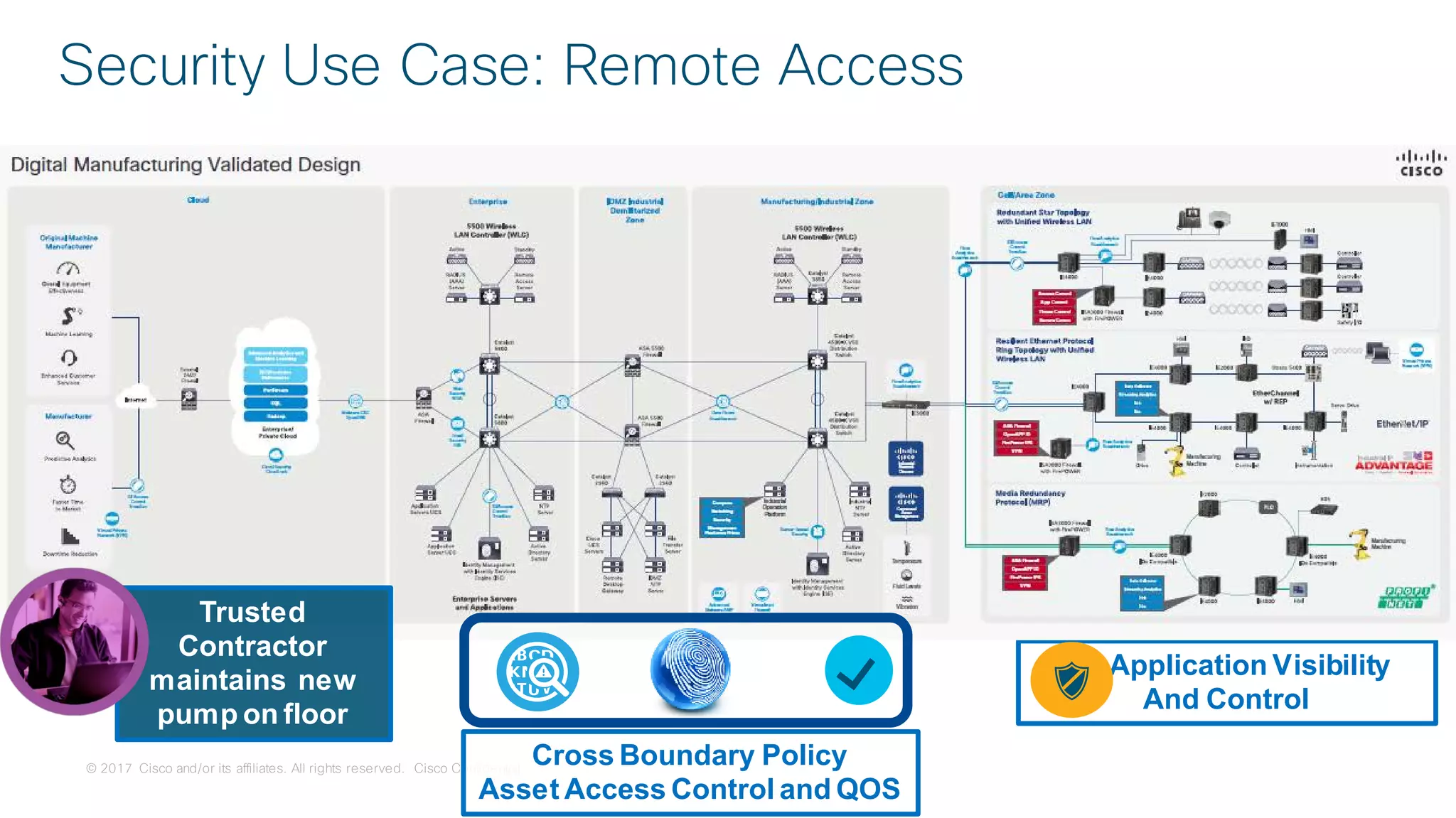
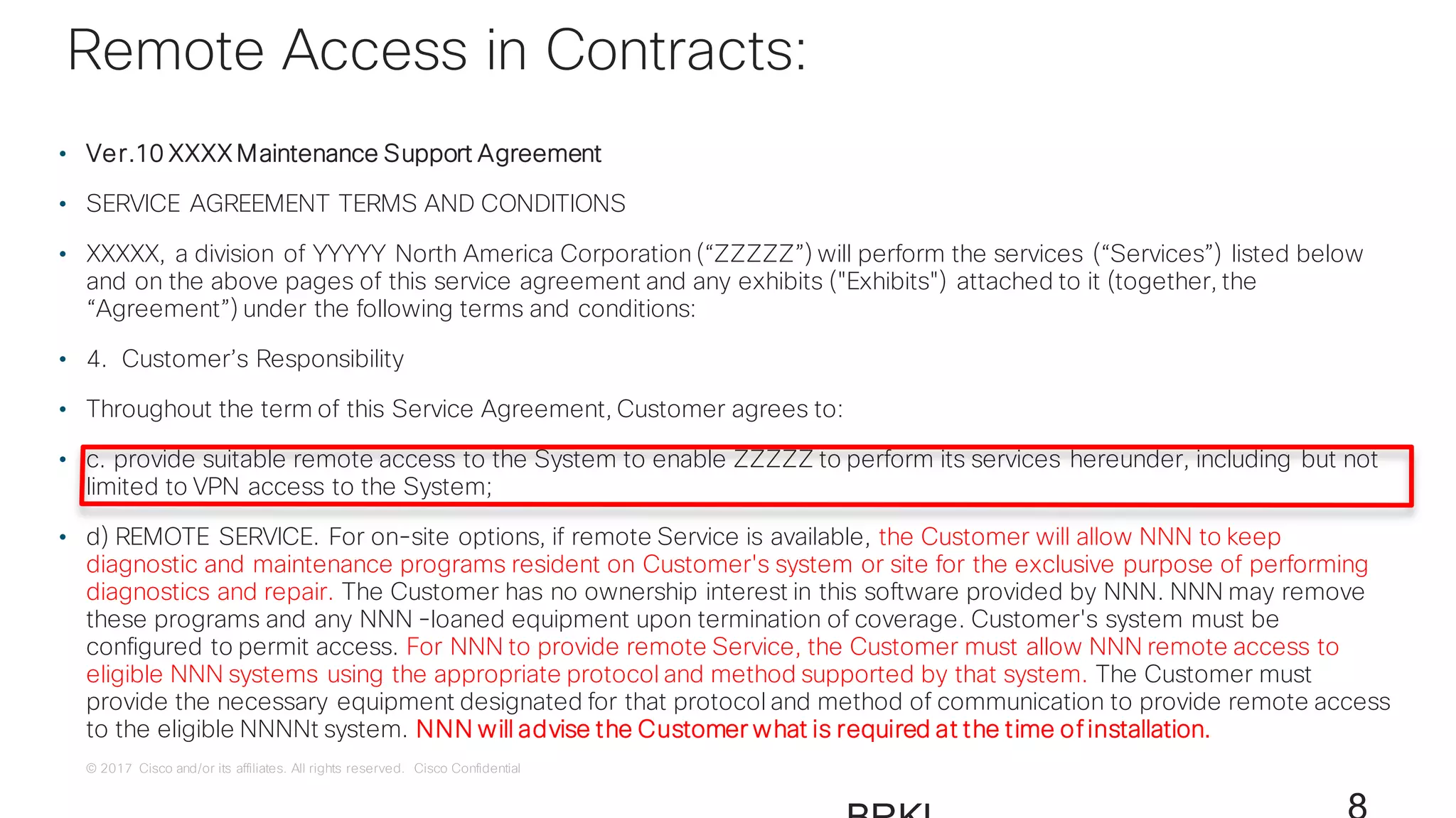
![© 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential
Use Case:
Remote Access
[A Brief Mention]](https://image.slidesharecdn.com/ciscoconnecttoronto2018-iot-unlockthepowerofdata-securingtheinternetofthings-fromthreatvectorstothea-181023171826/75/Cisco-Connect-Toronto-2018-IOT-unlock-the-power-of-data-securing-the-internet-of-things-from-threat-vectors-to-the-architectures-80-2048.jpg)