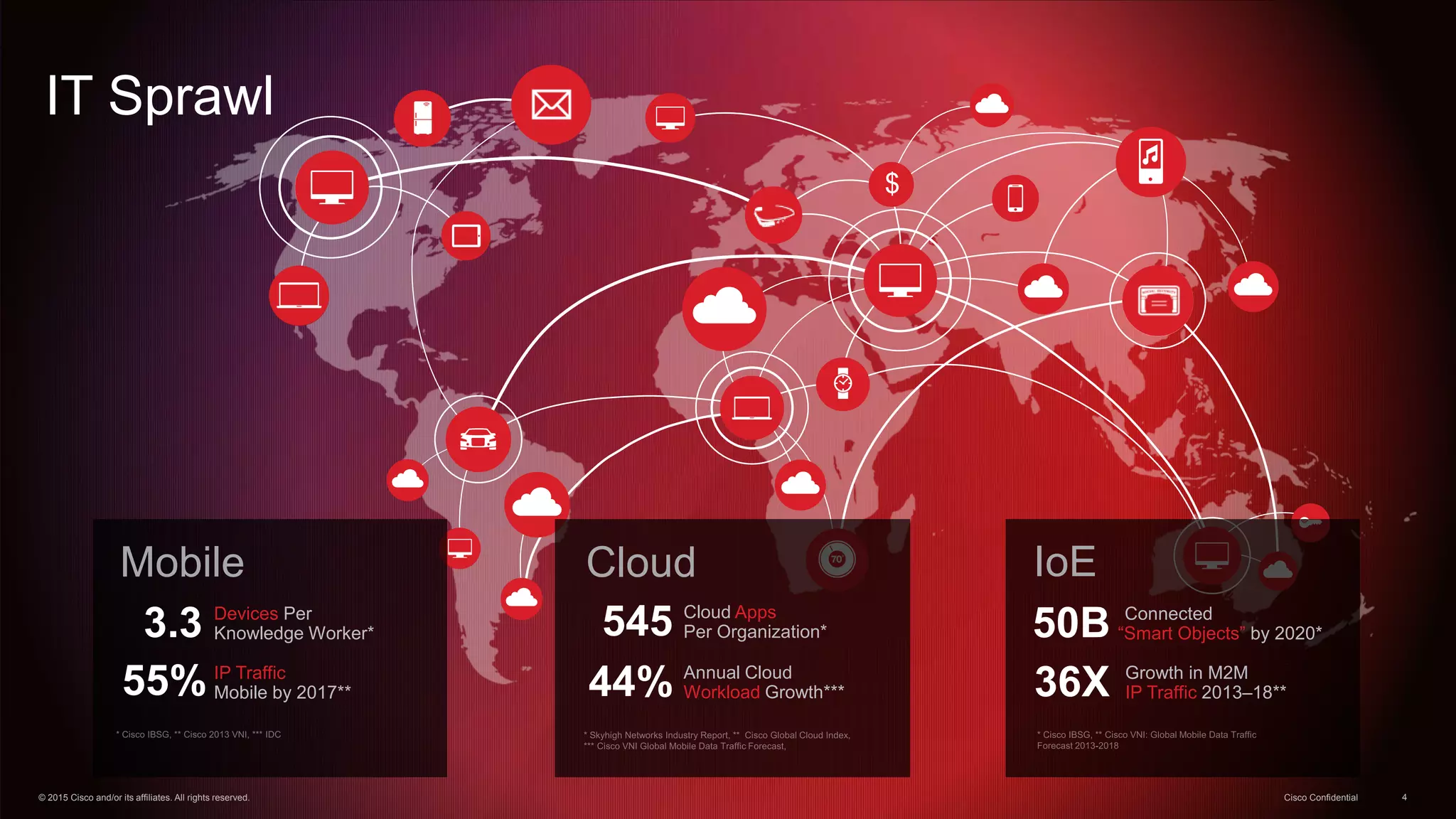
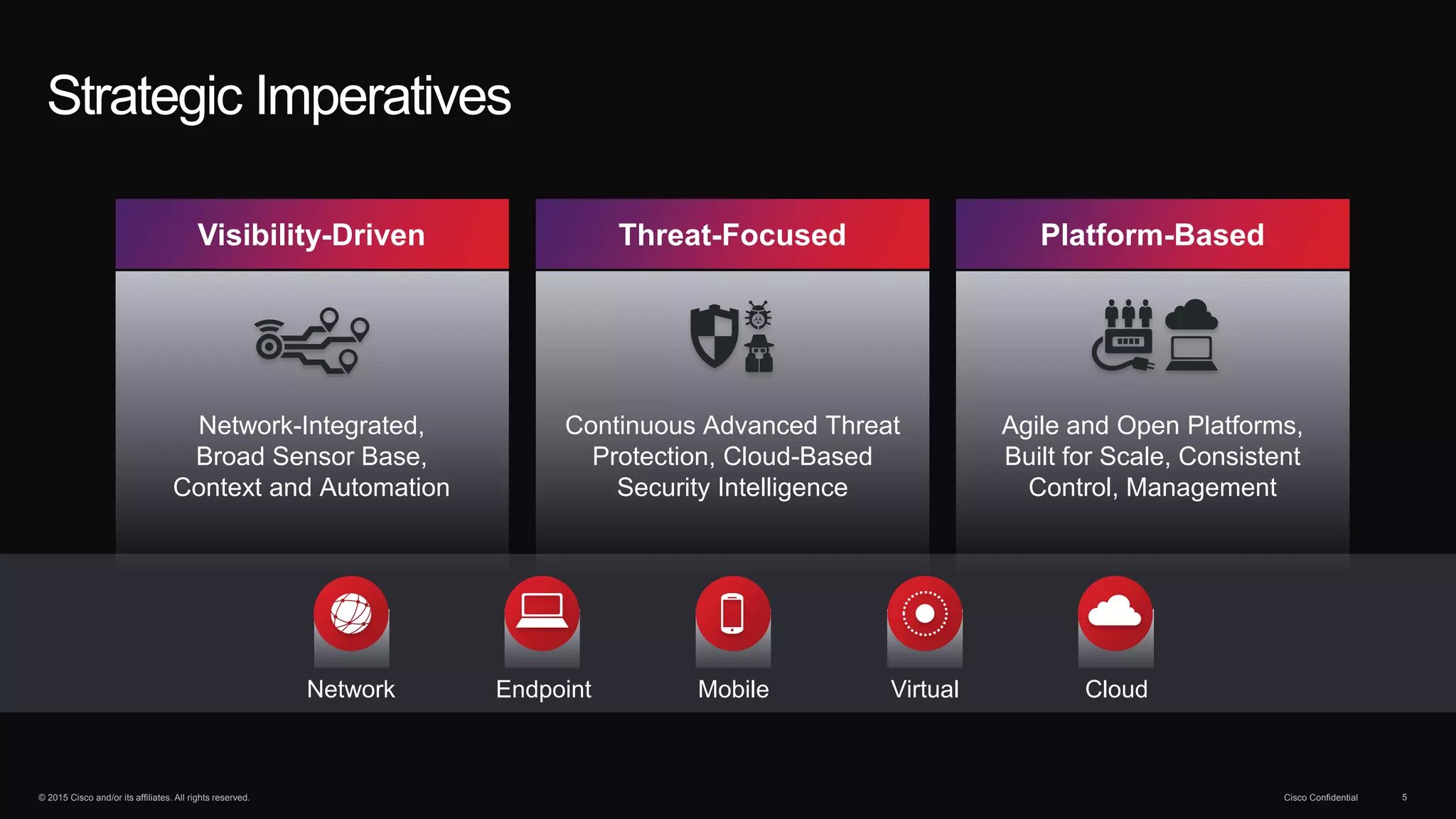
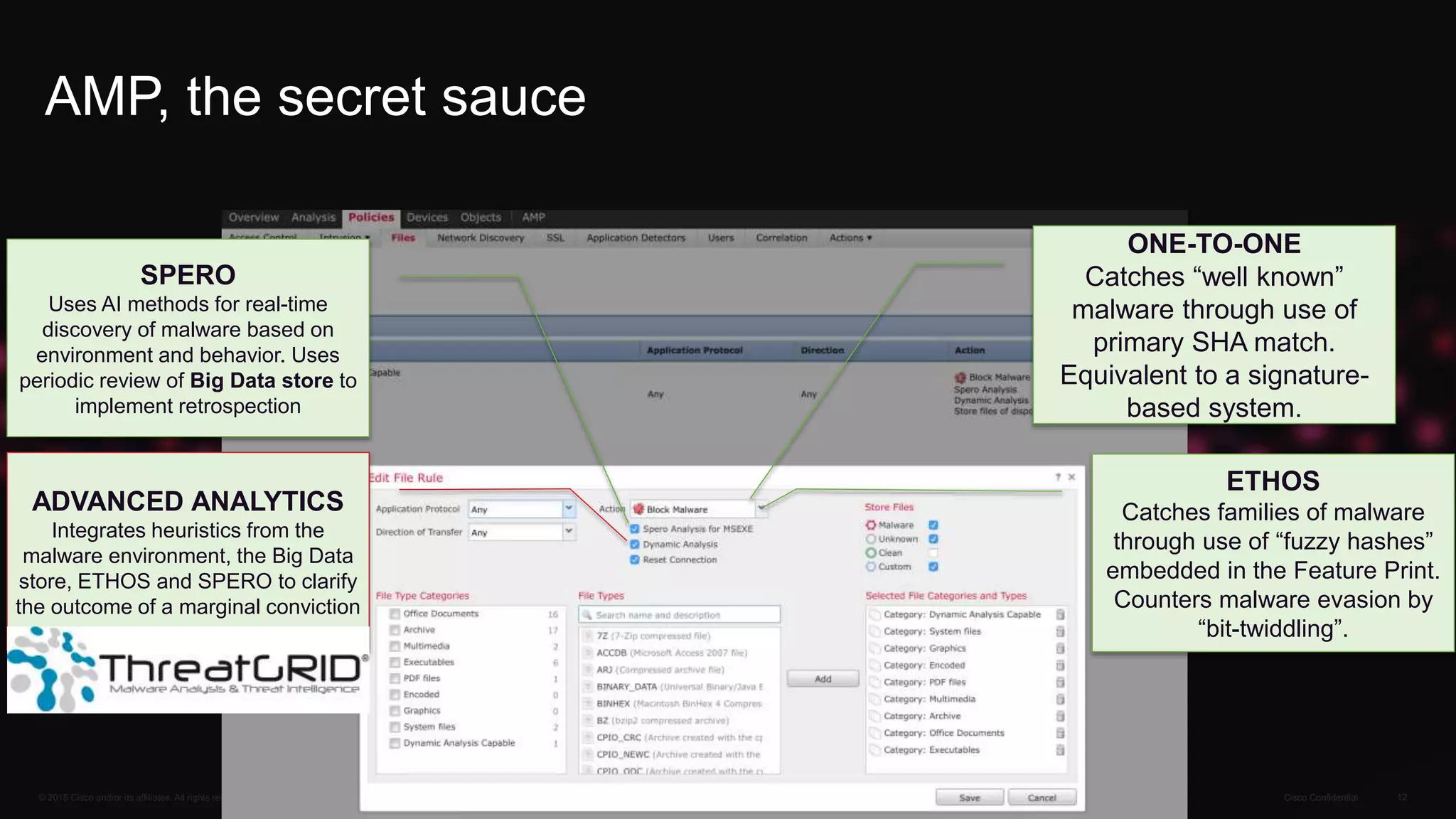
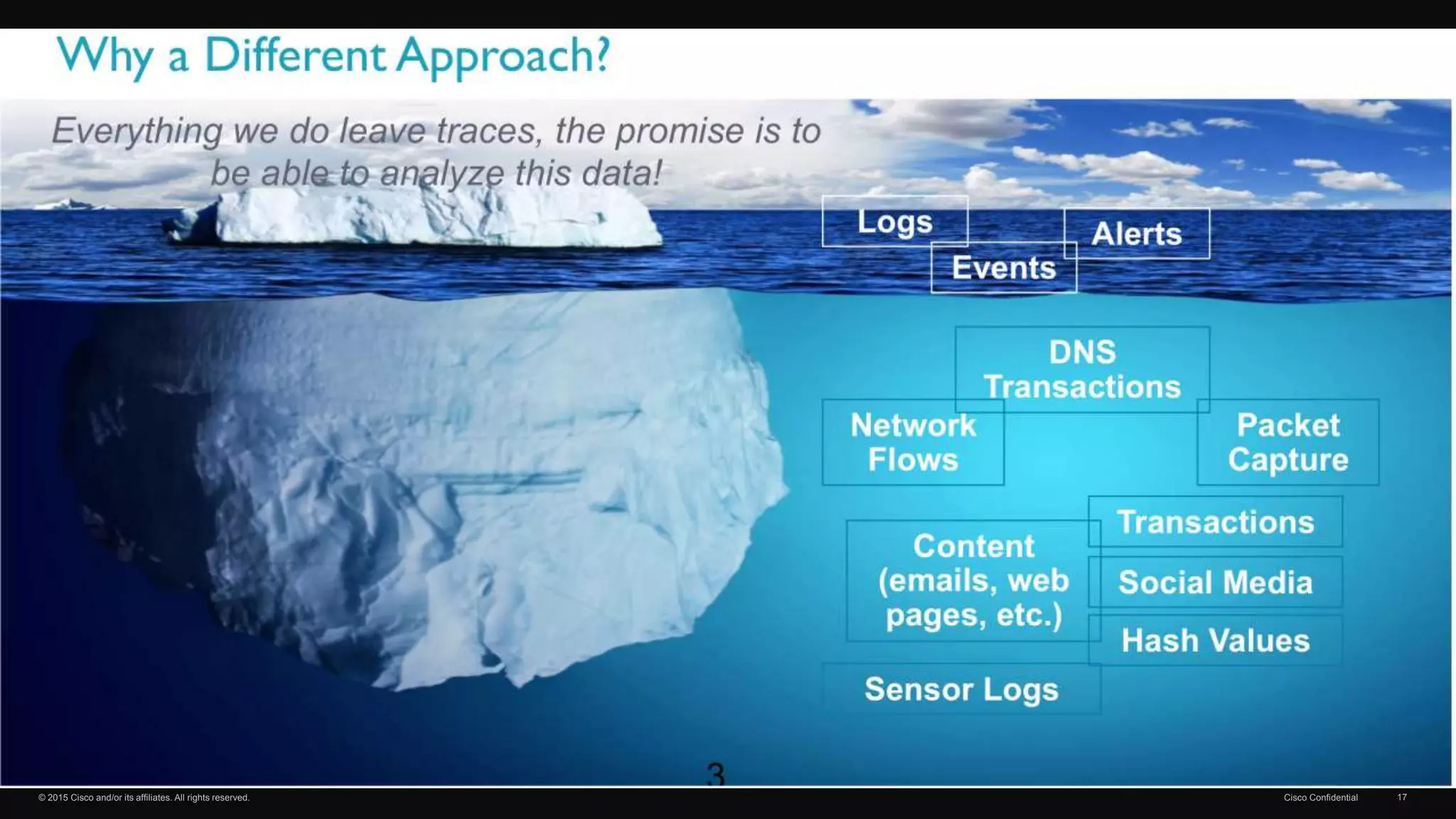
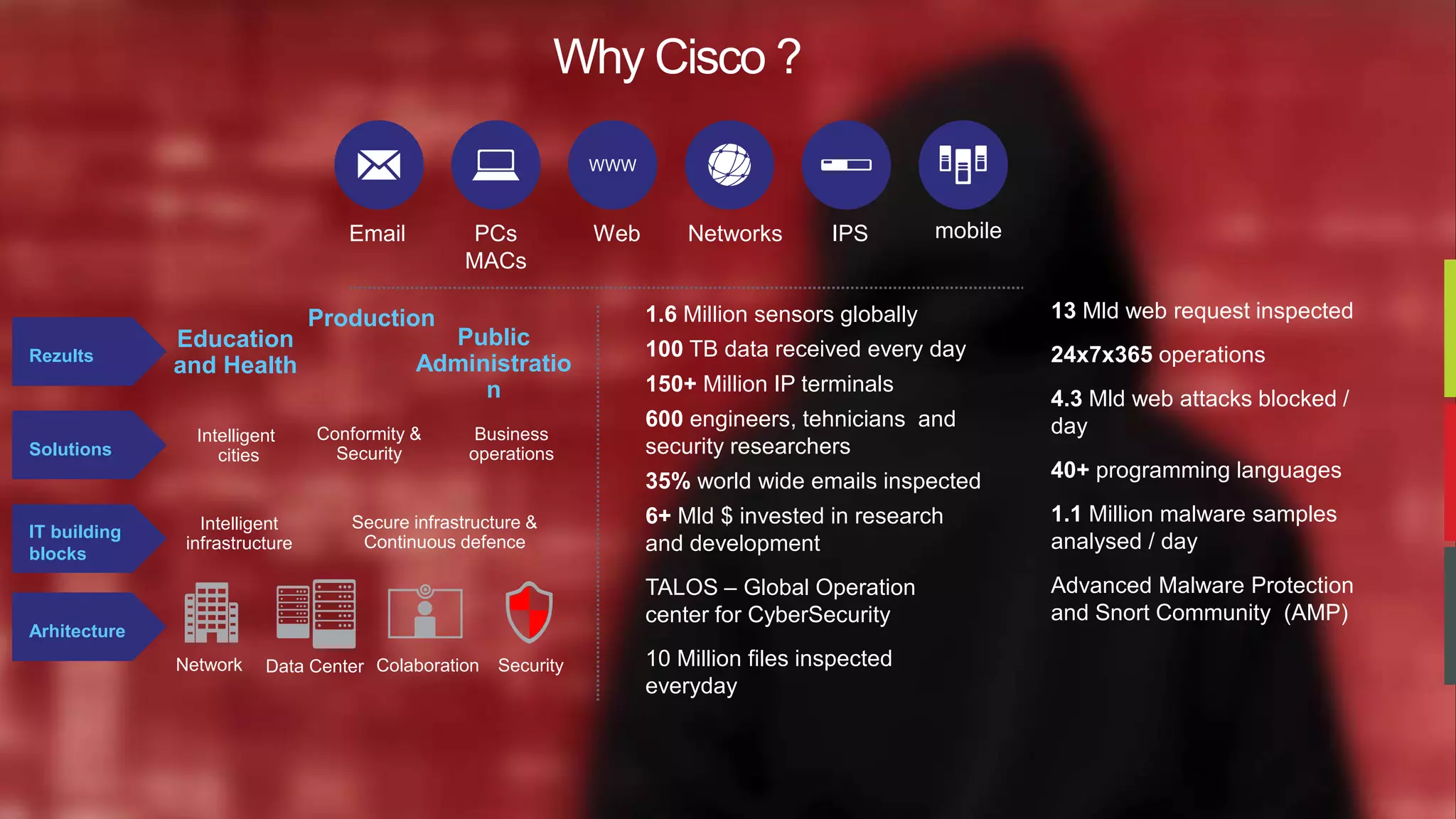
The document discusses cybersecurity threats and Cisco's approach to addressing them. It notes that hacking has become a multi-billion dollar global industry. It also discusses the growth of mobile devices, cloud apps, and the Internet of Everything. Cisco's strategies for security involve continuous advanced threat protection using a network-integrated, broad sensor base with context and automation. Cisco protects infrastructure using advanced malware protection everywhere, big data analytics, and by making infrastructure a self-defending, self-healing architecture.