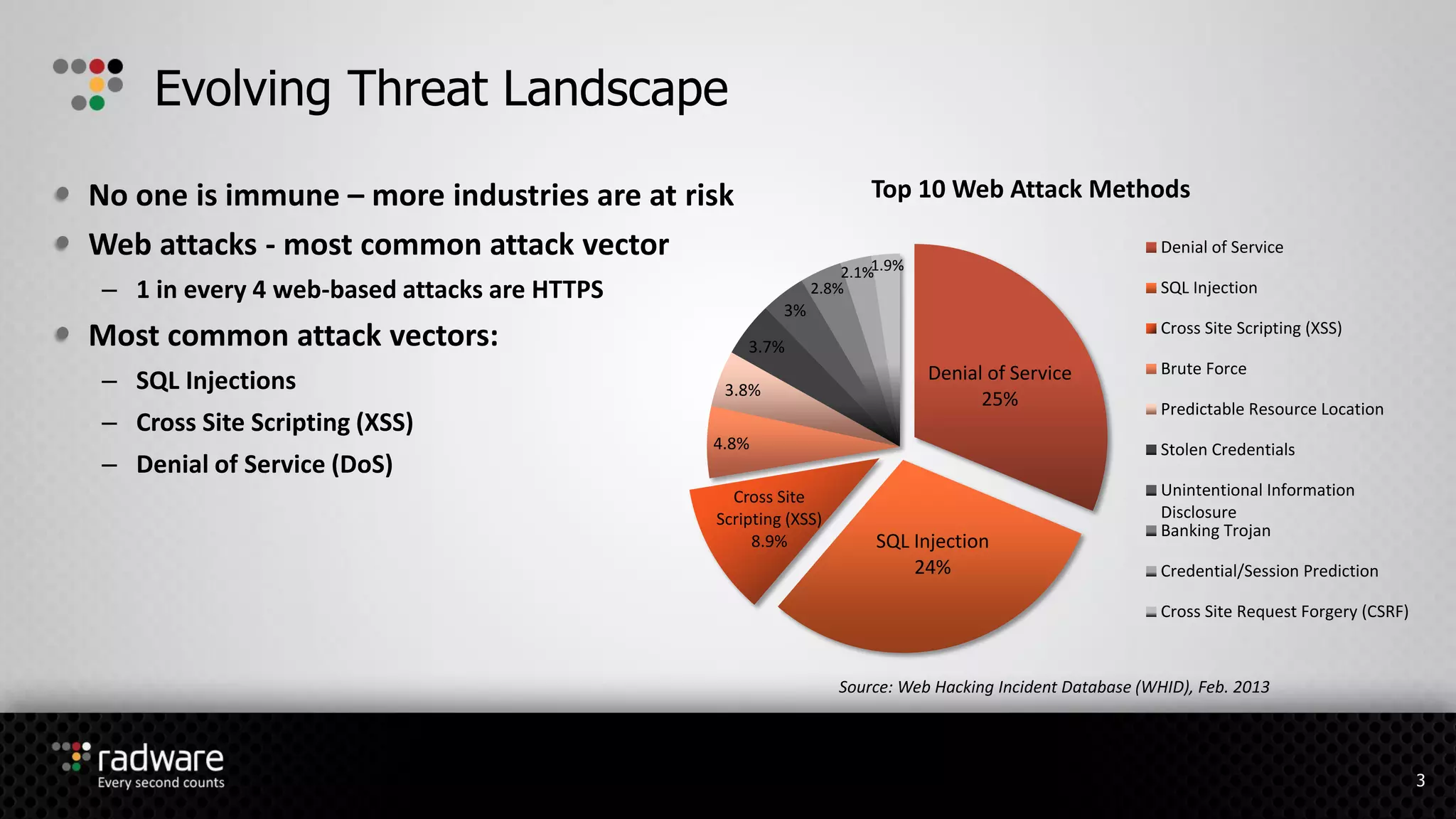
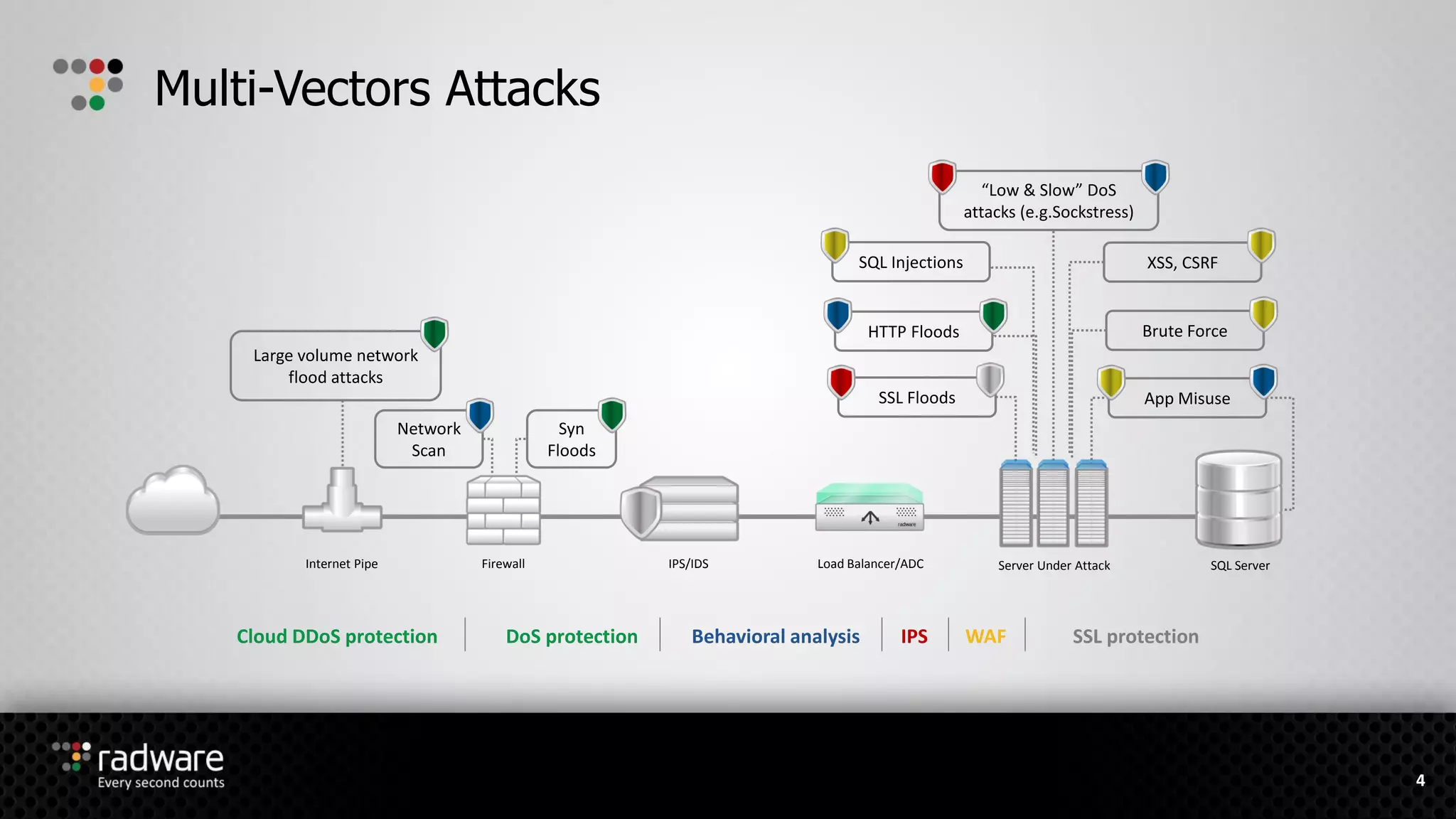
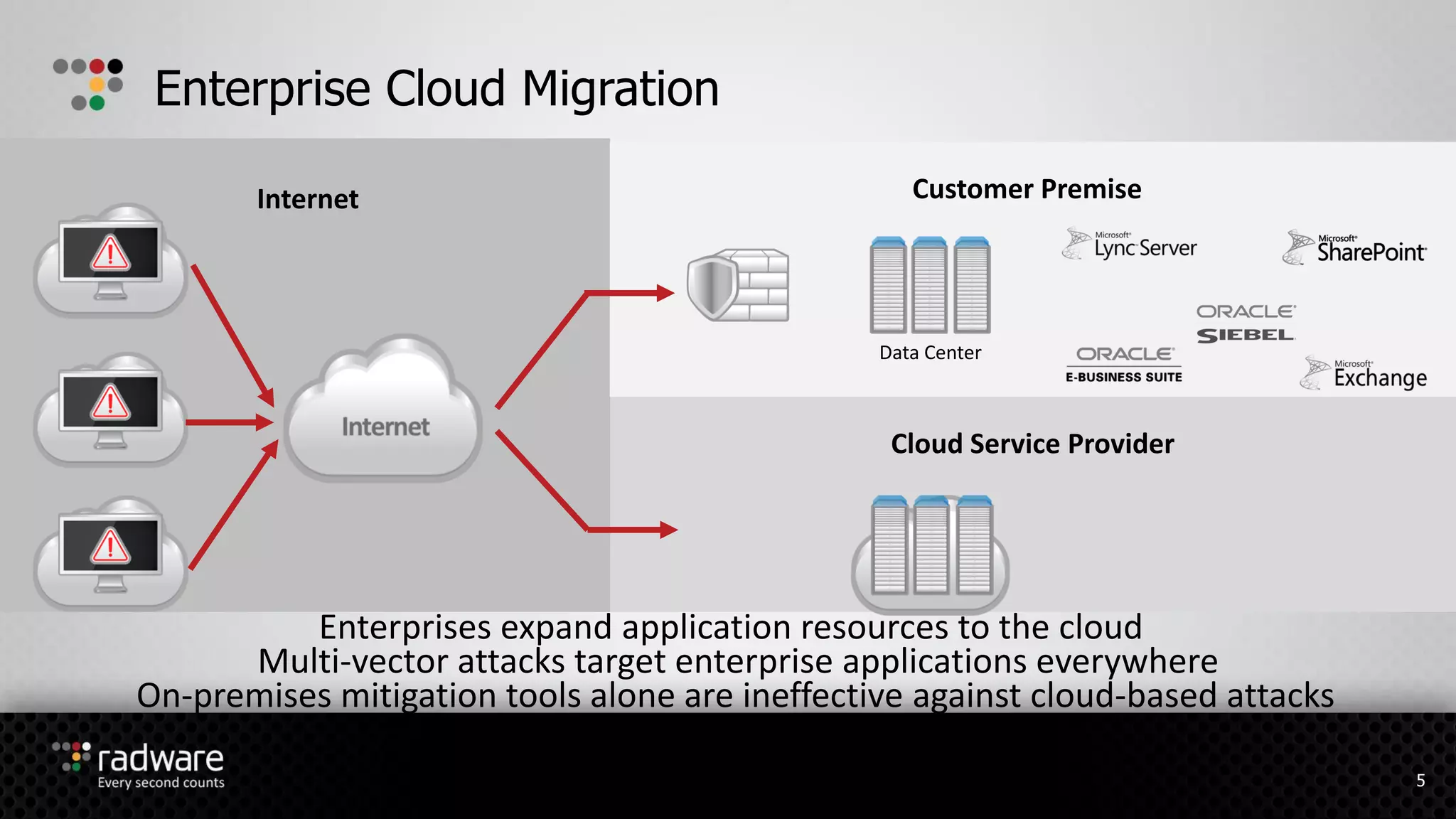
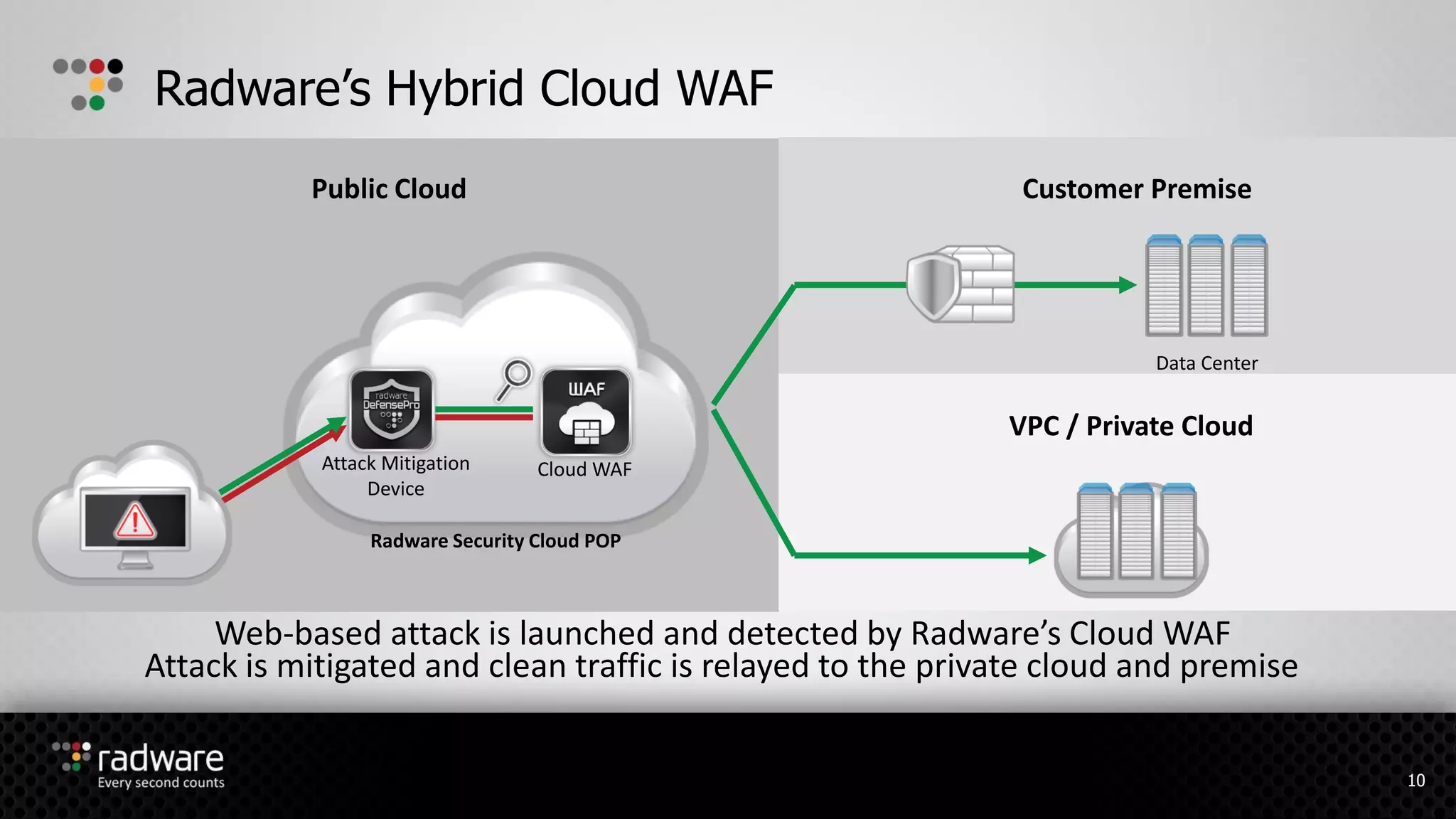
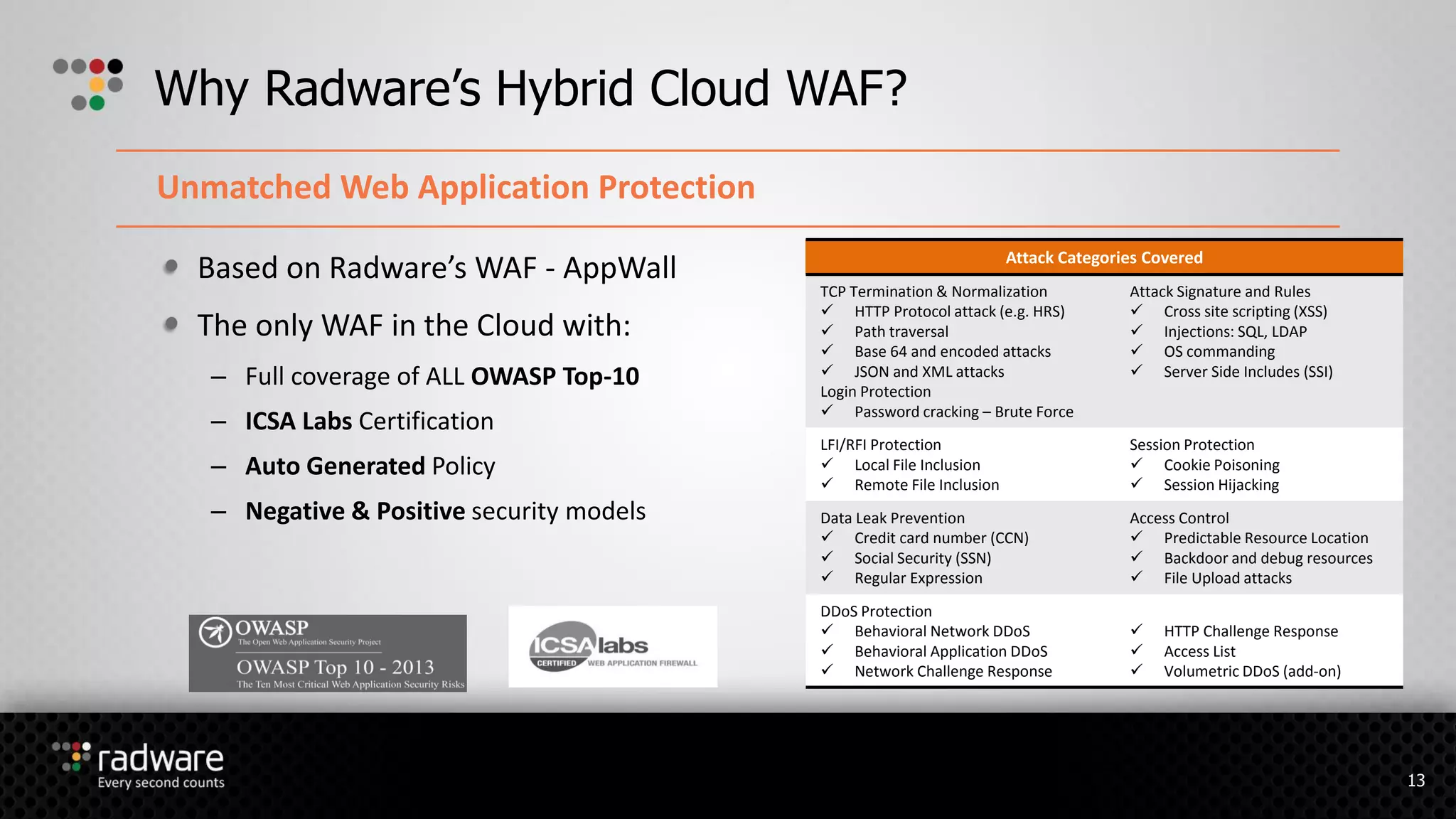
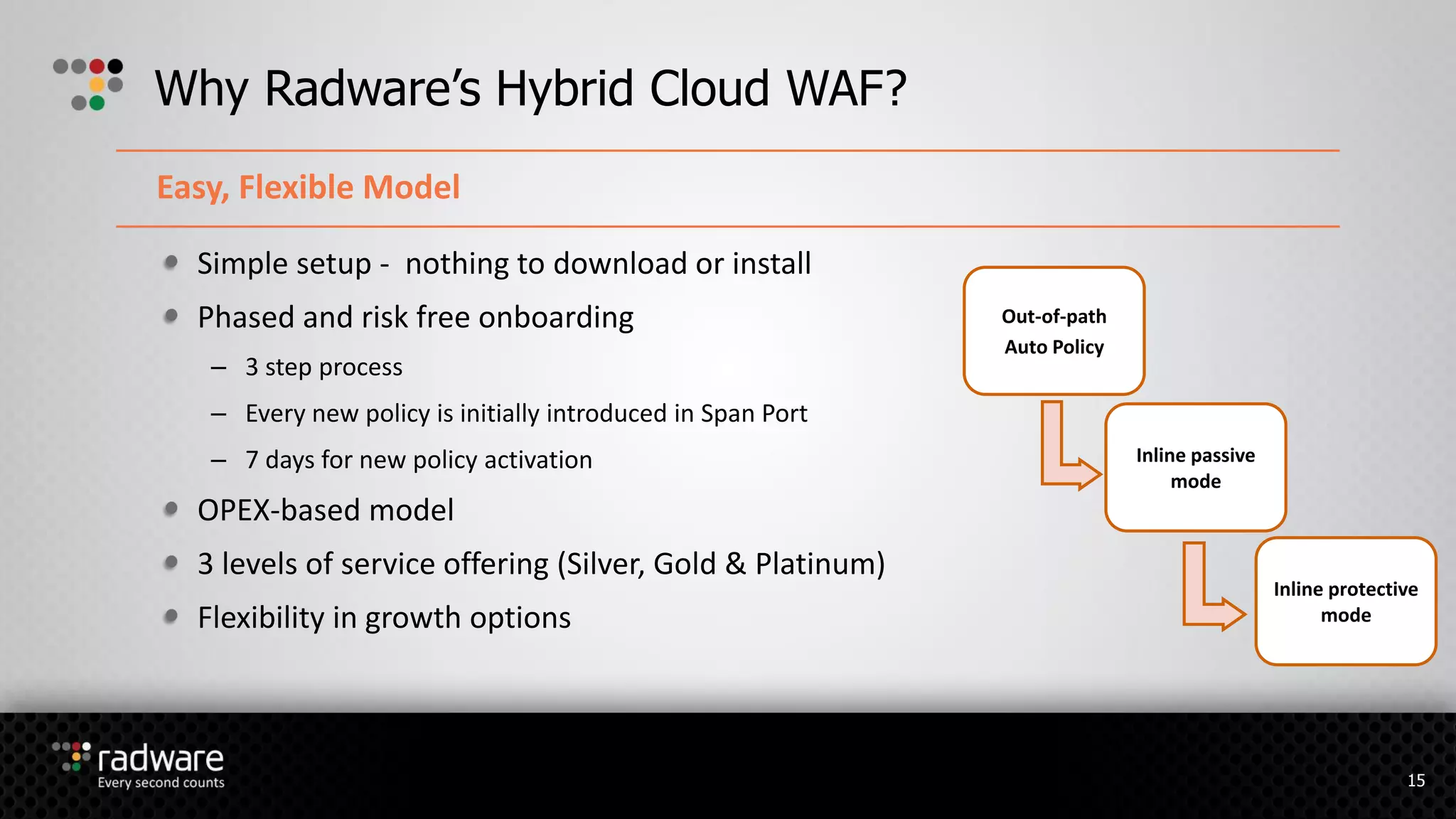
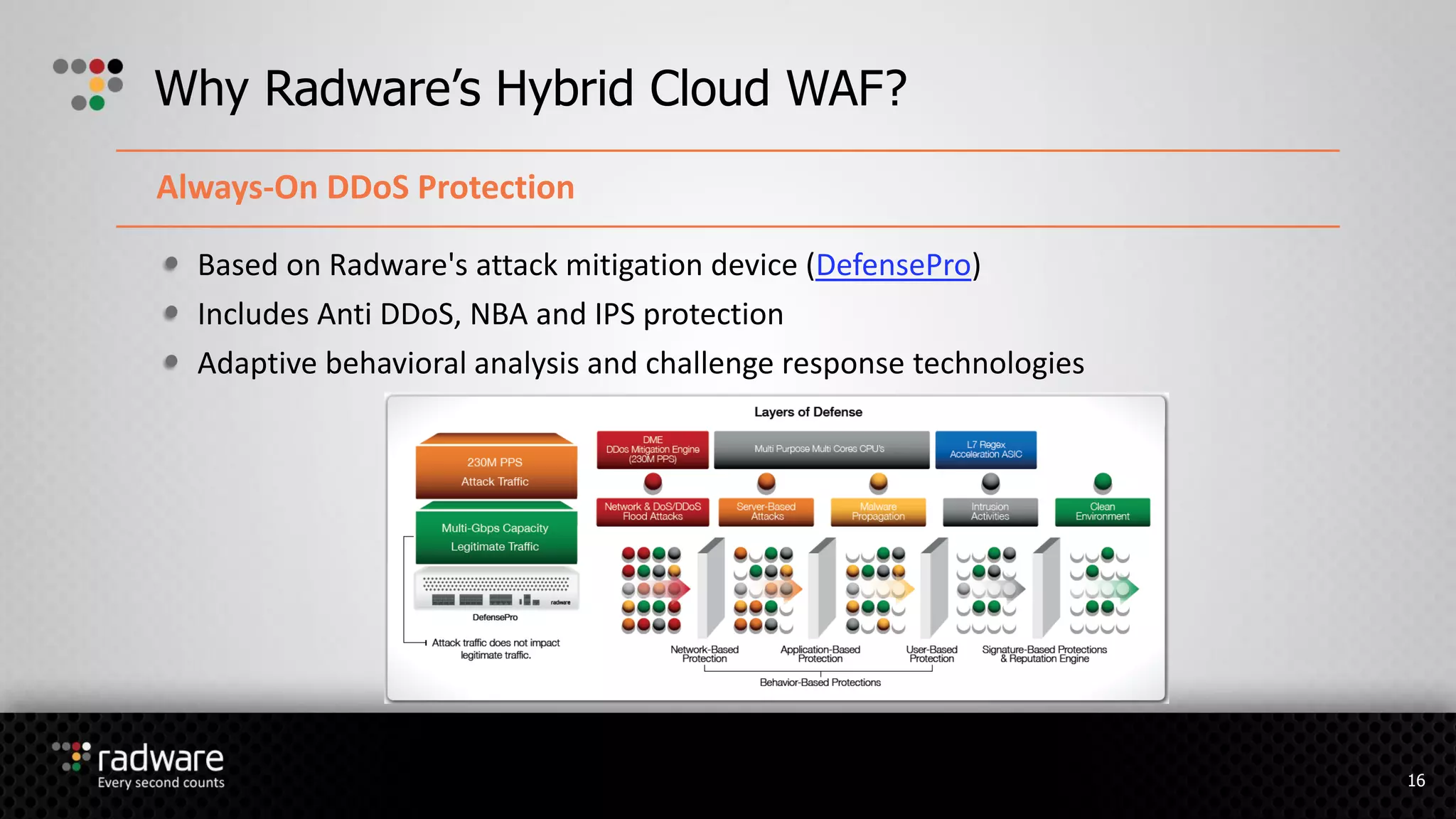
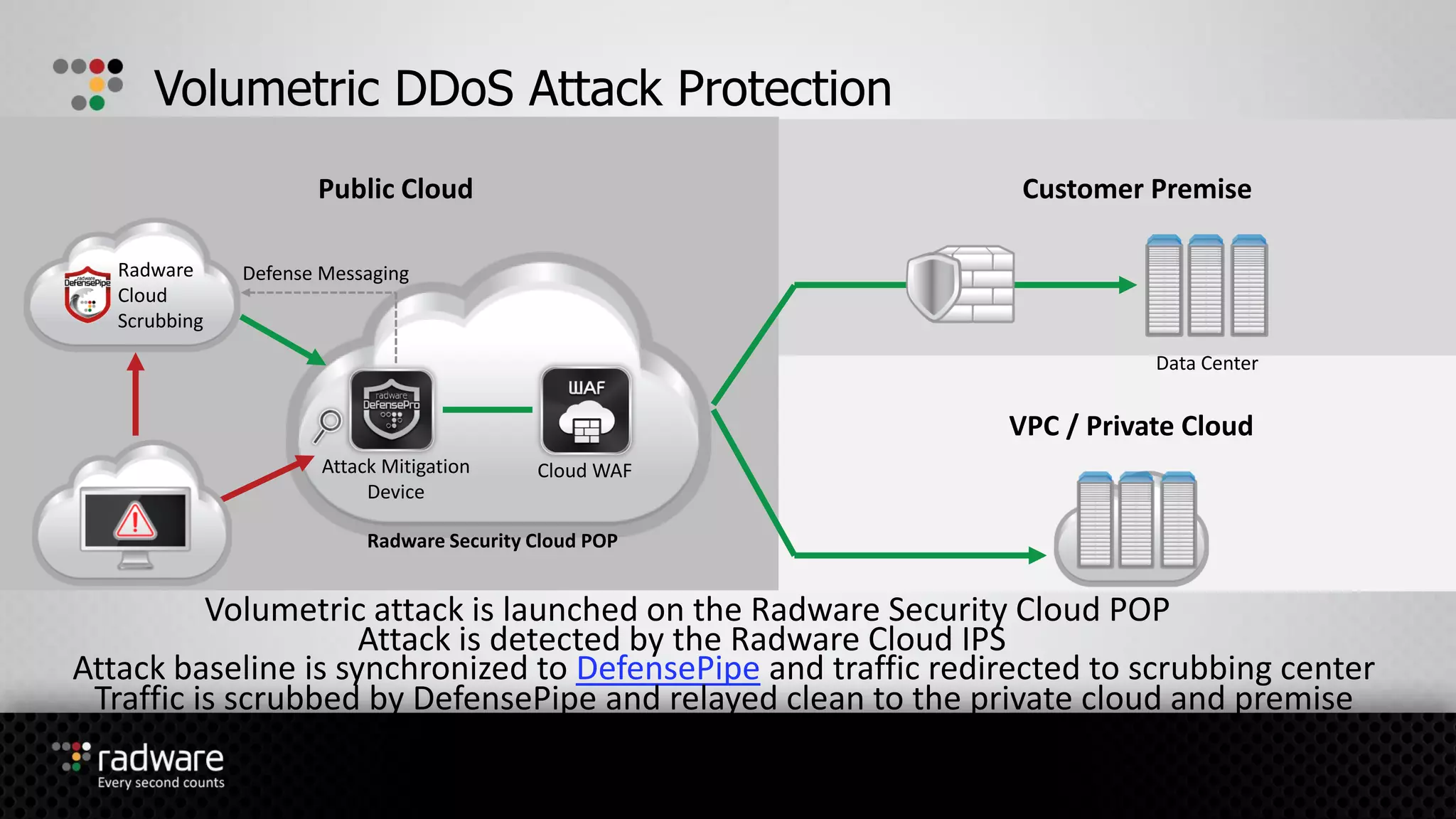
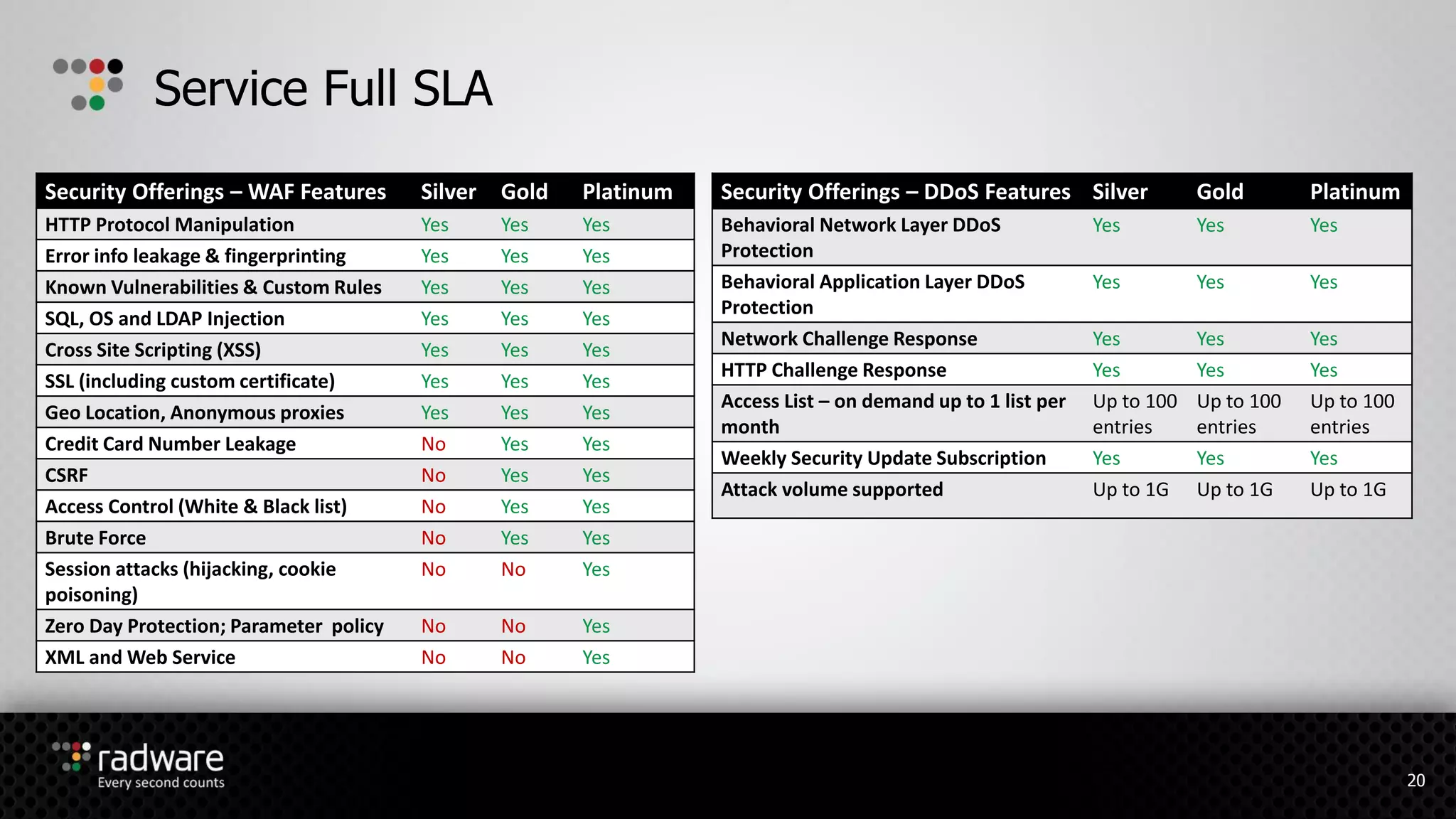
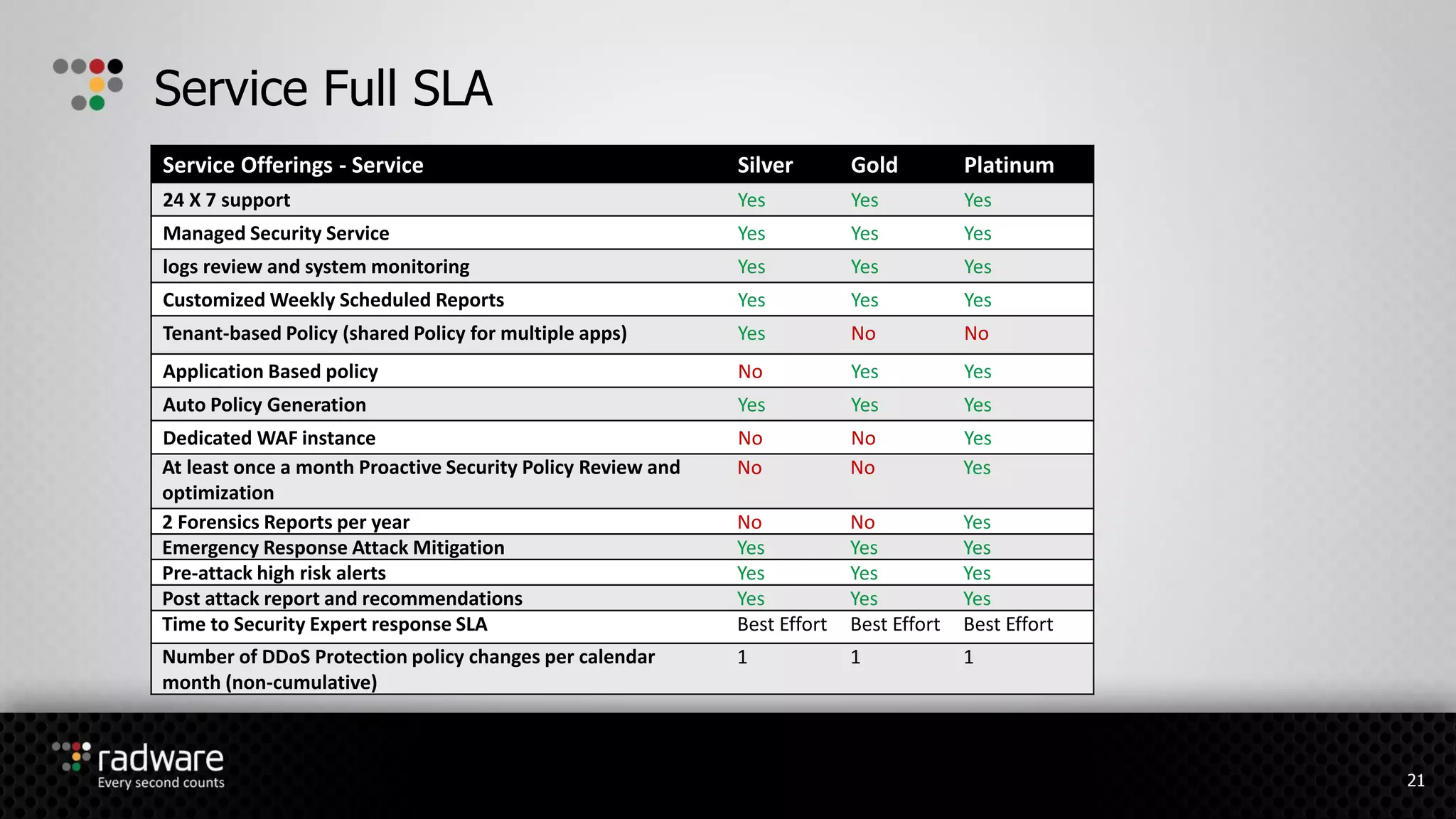
The document describes Radware's hybrid cloud WAF service, which provides fully-managed web application and DDoS protection for enterprises with applications in both cloud and on-premise environments. The service uses Radware's security technologies to integrate cloud and on-premise defenses, providing comprehensive detection and mitigation of web attacks, SQL injections, cross-site scripting, and DDoS attacks across hybrid infrastructures. It offers three service tiers with varying levels of protection and management features to suit different customer needs.