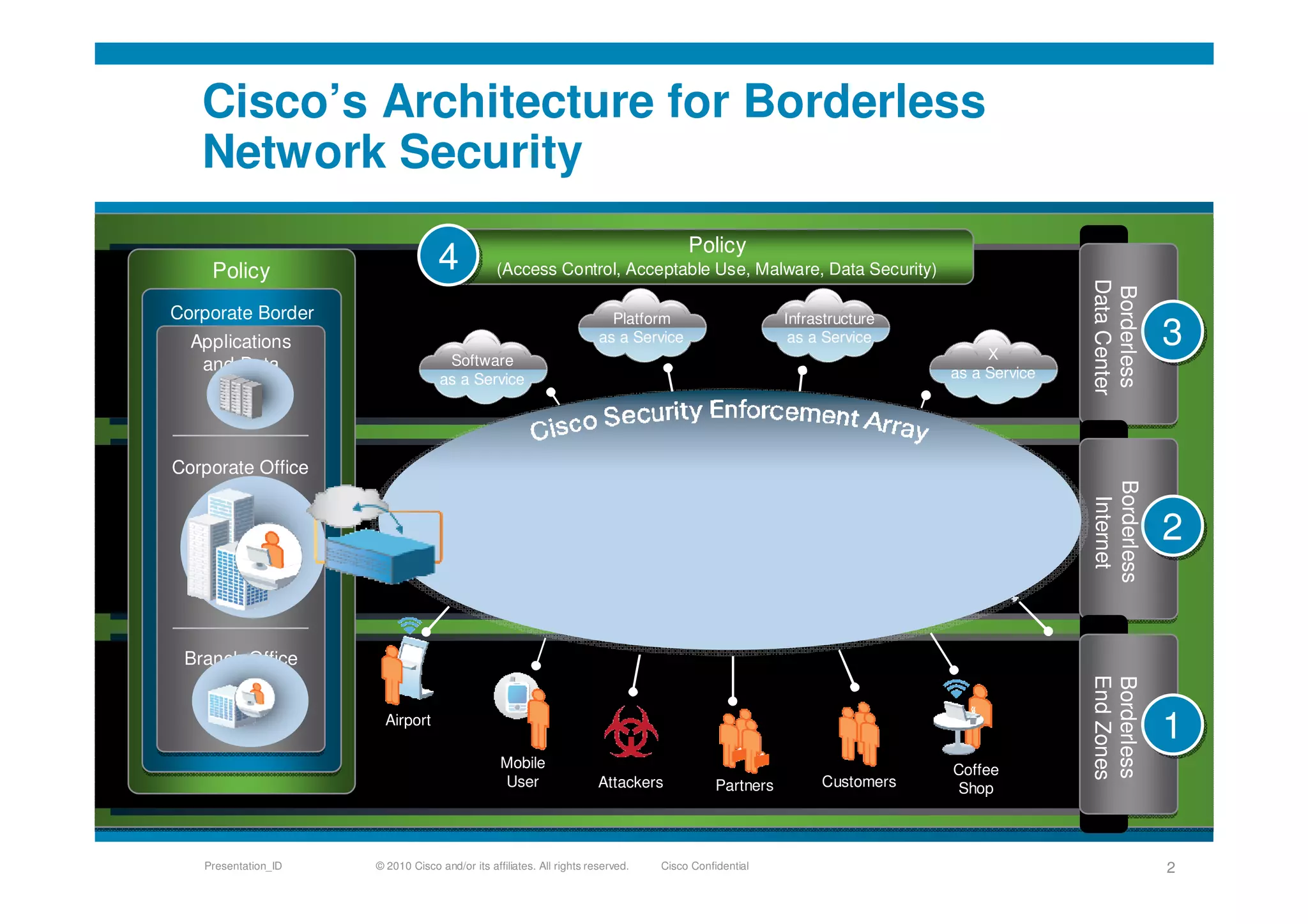
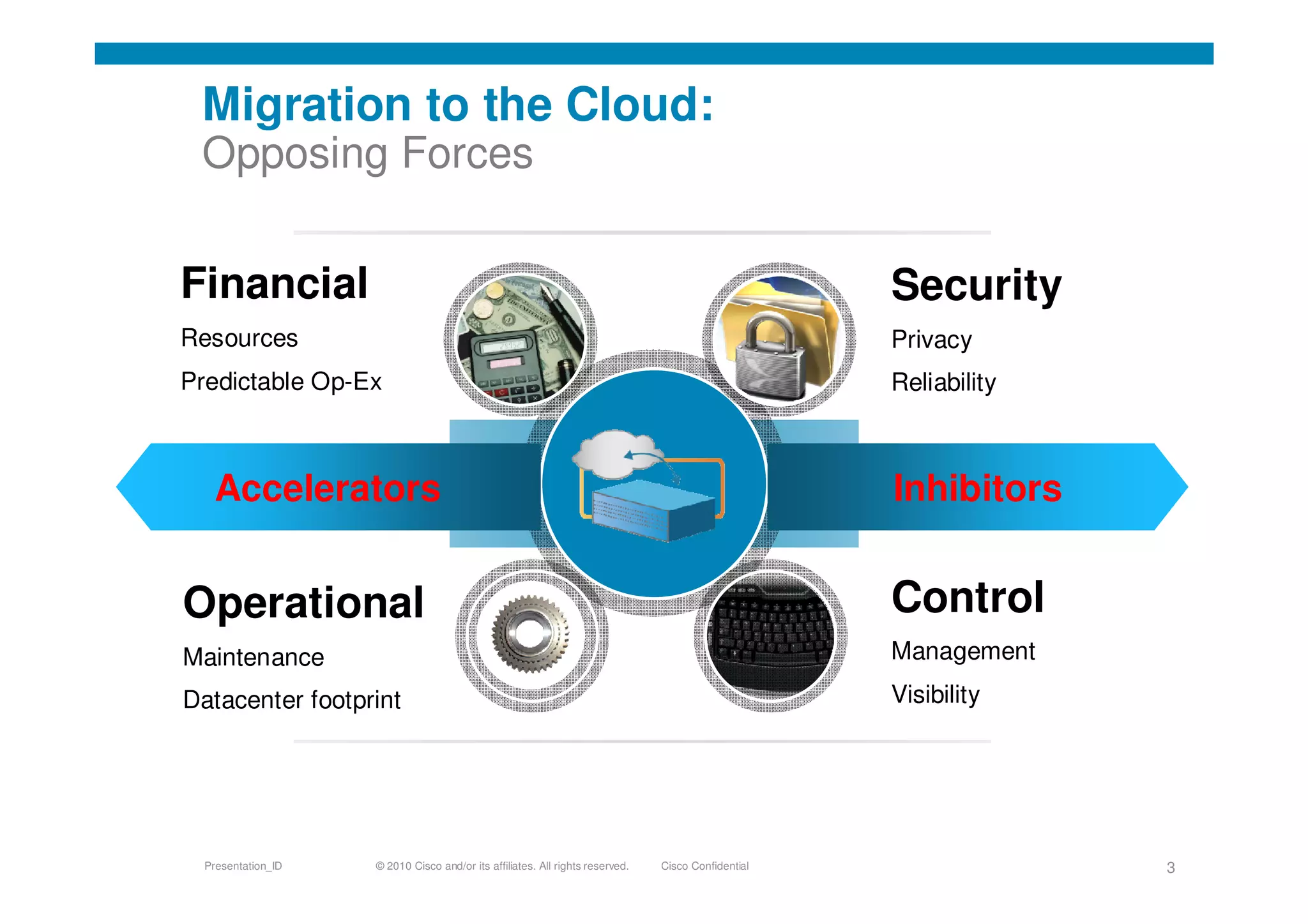
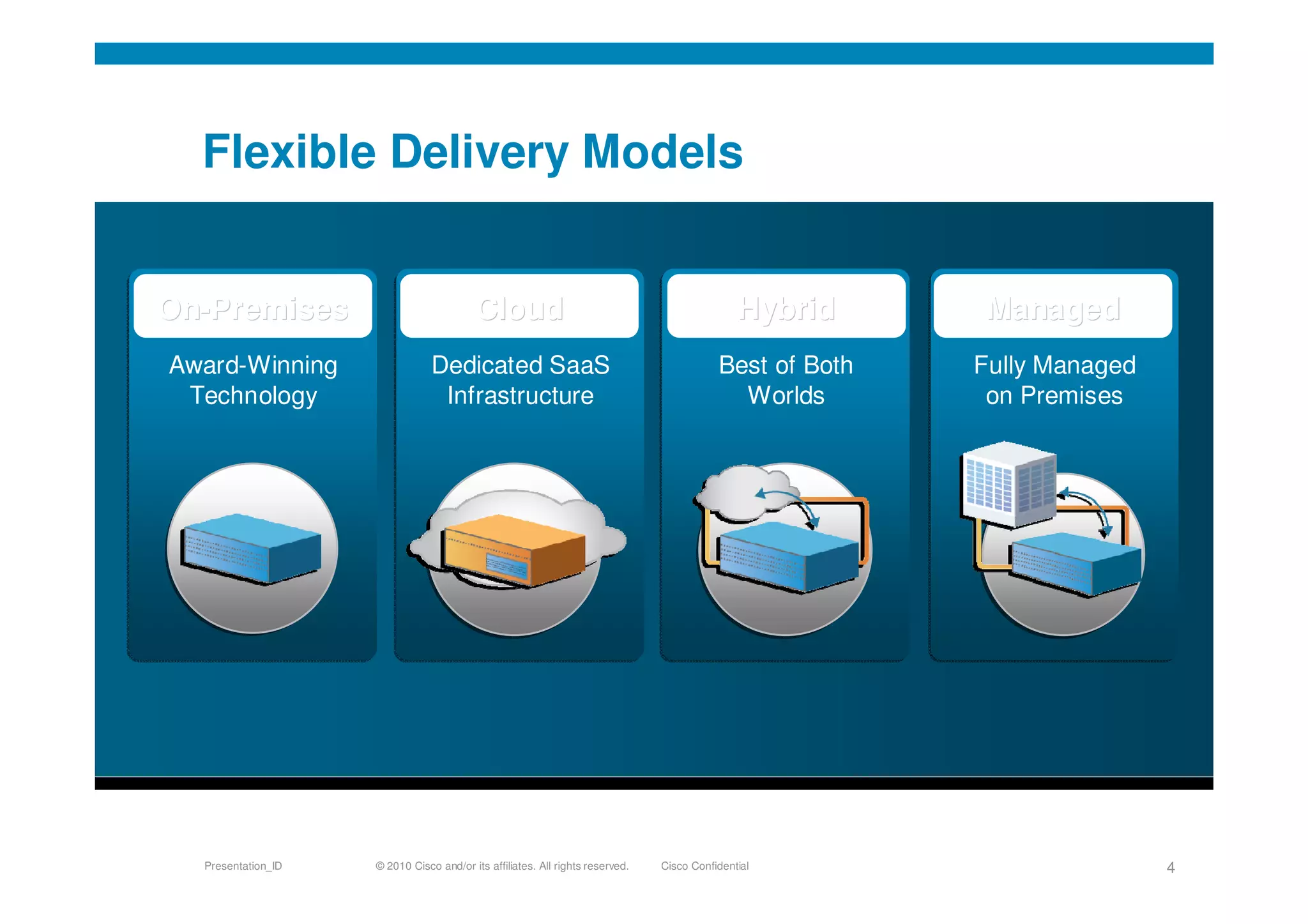
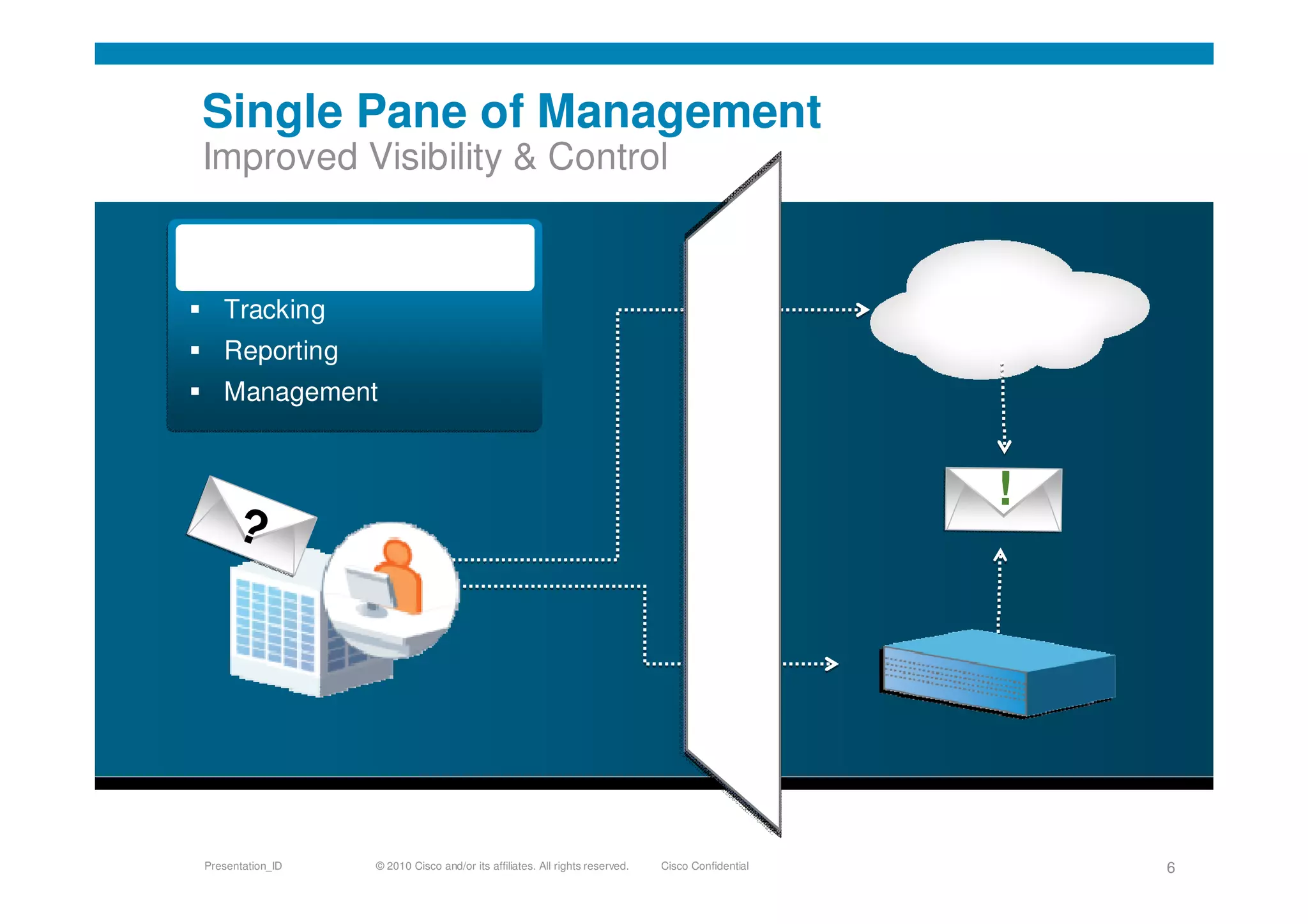
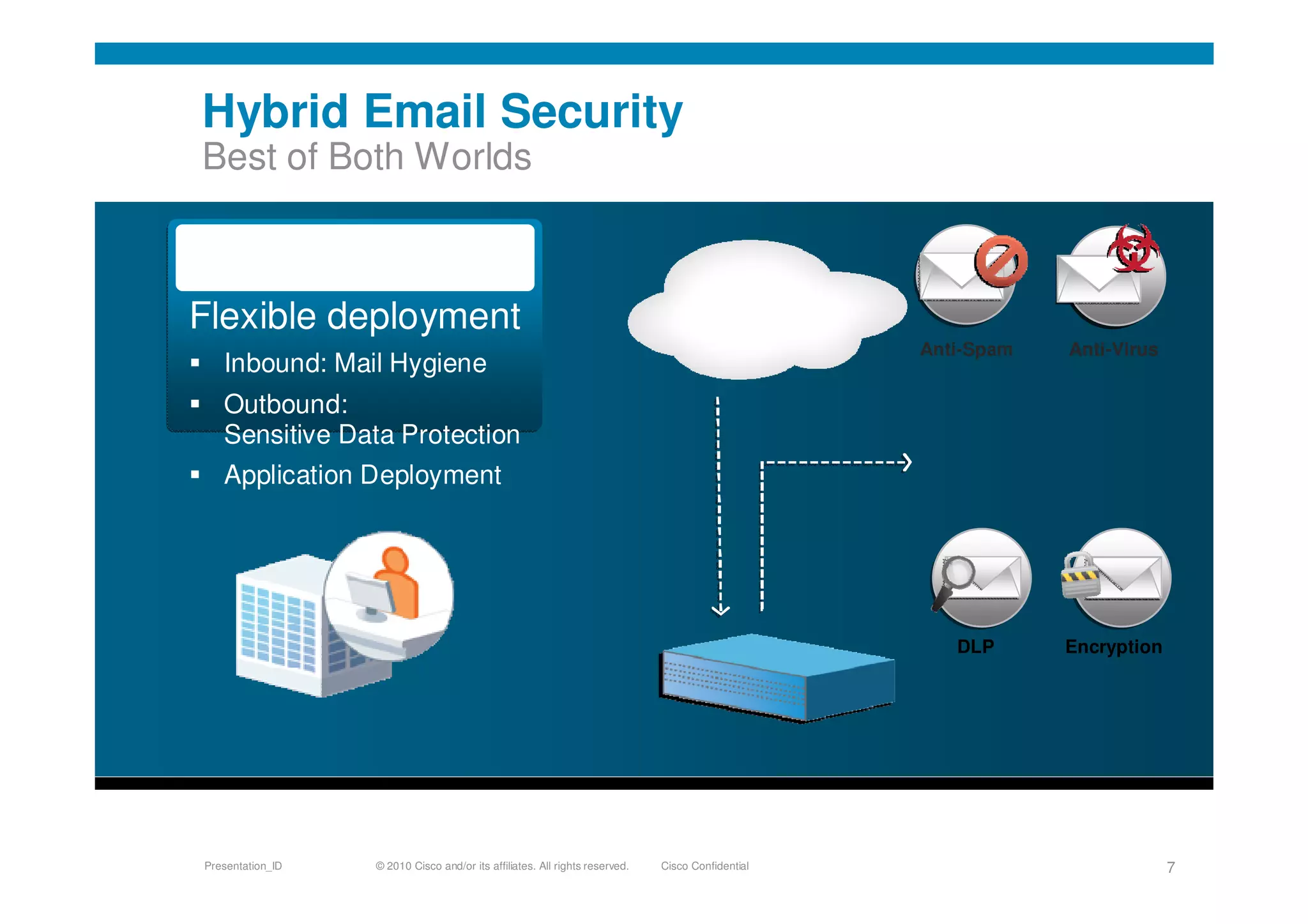
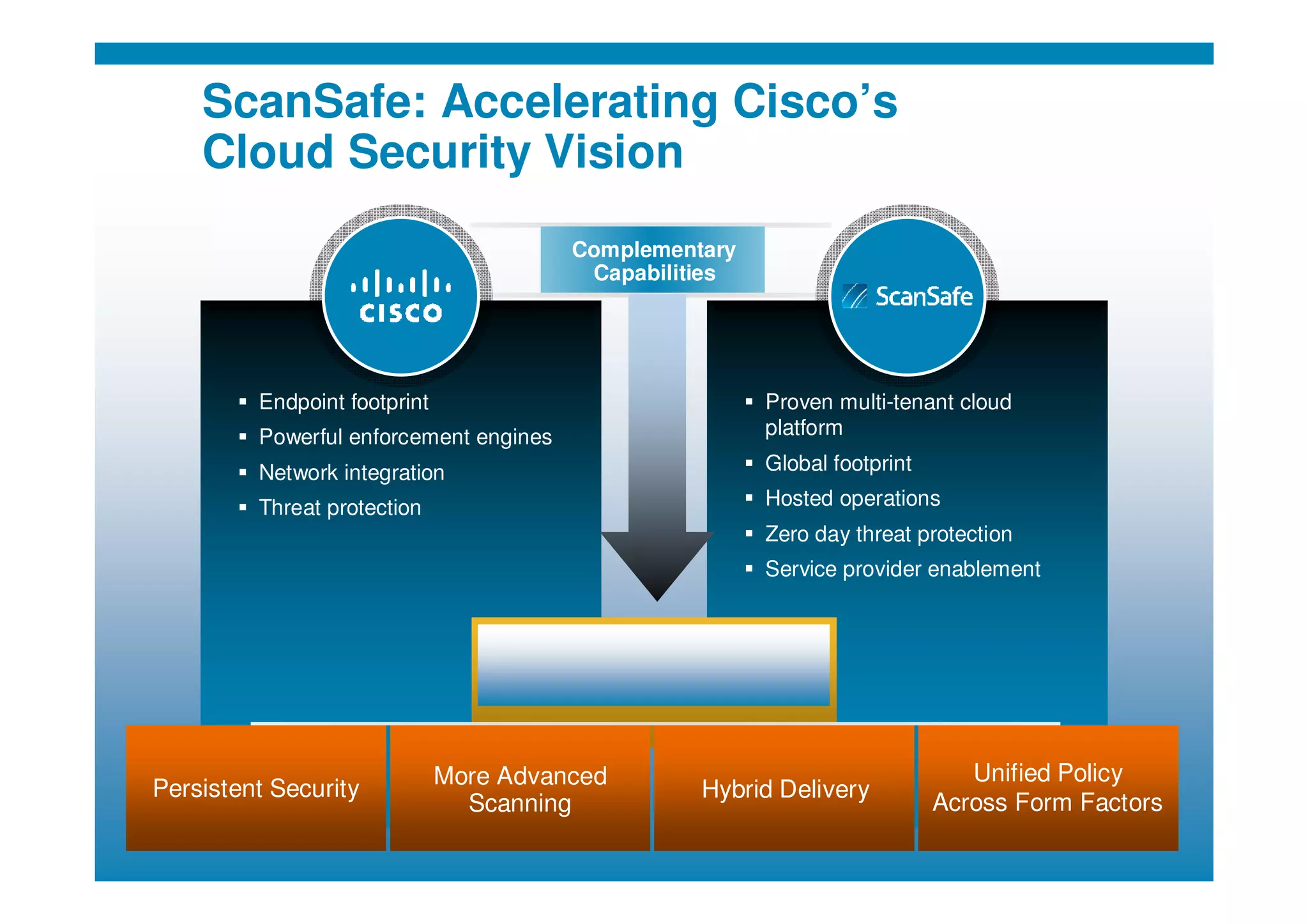
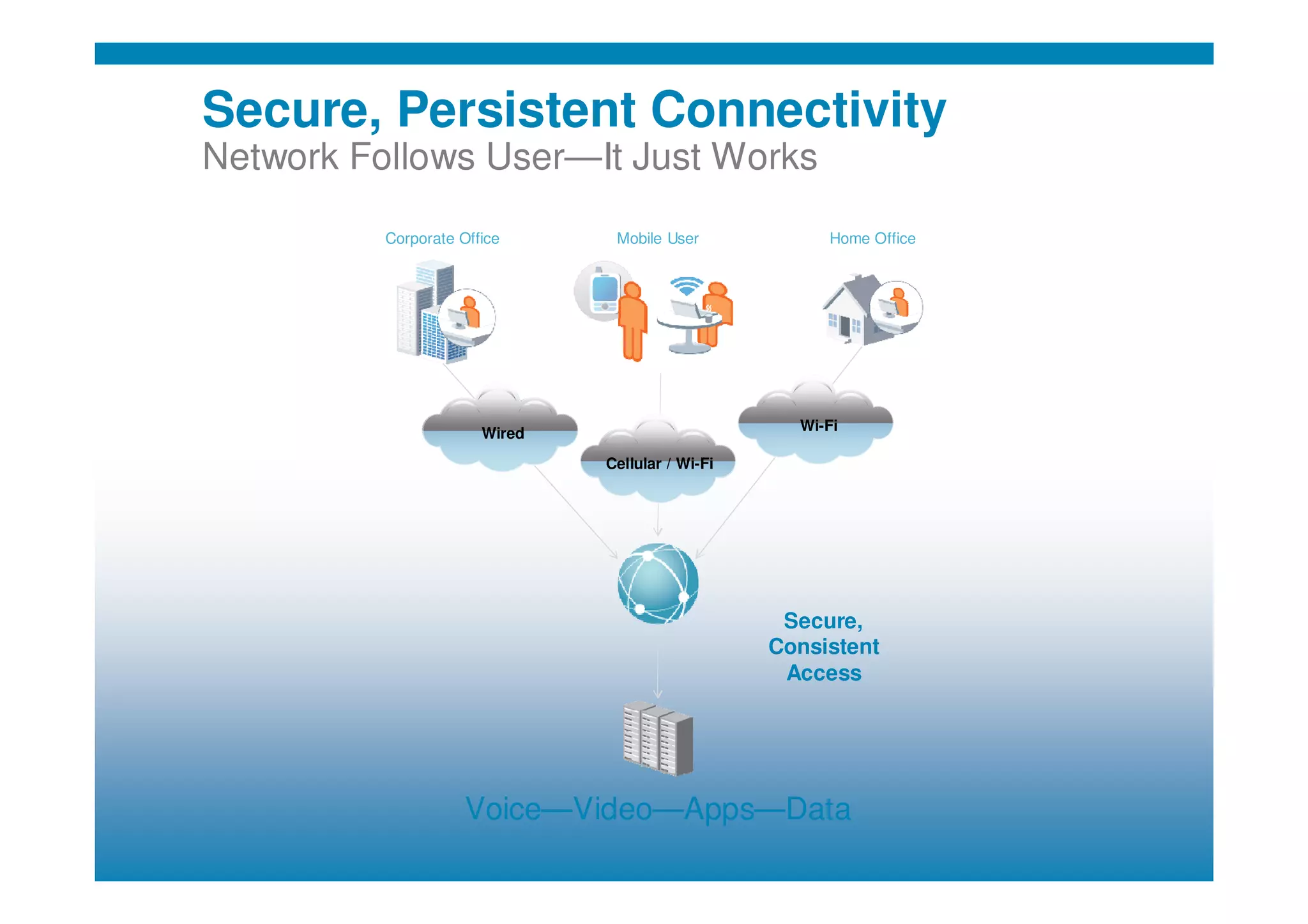
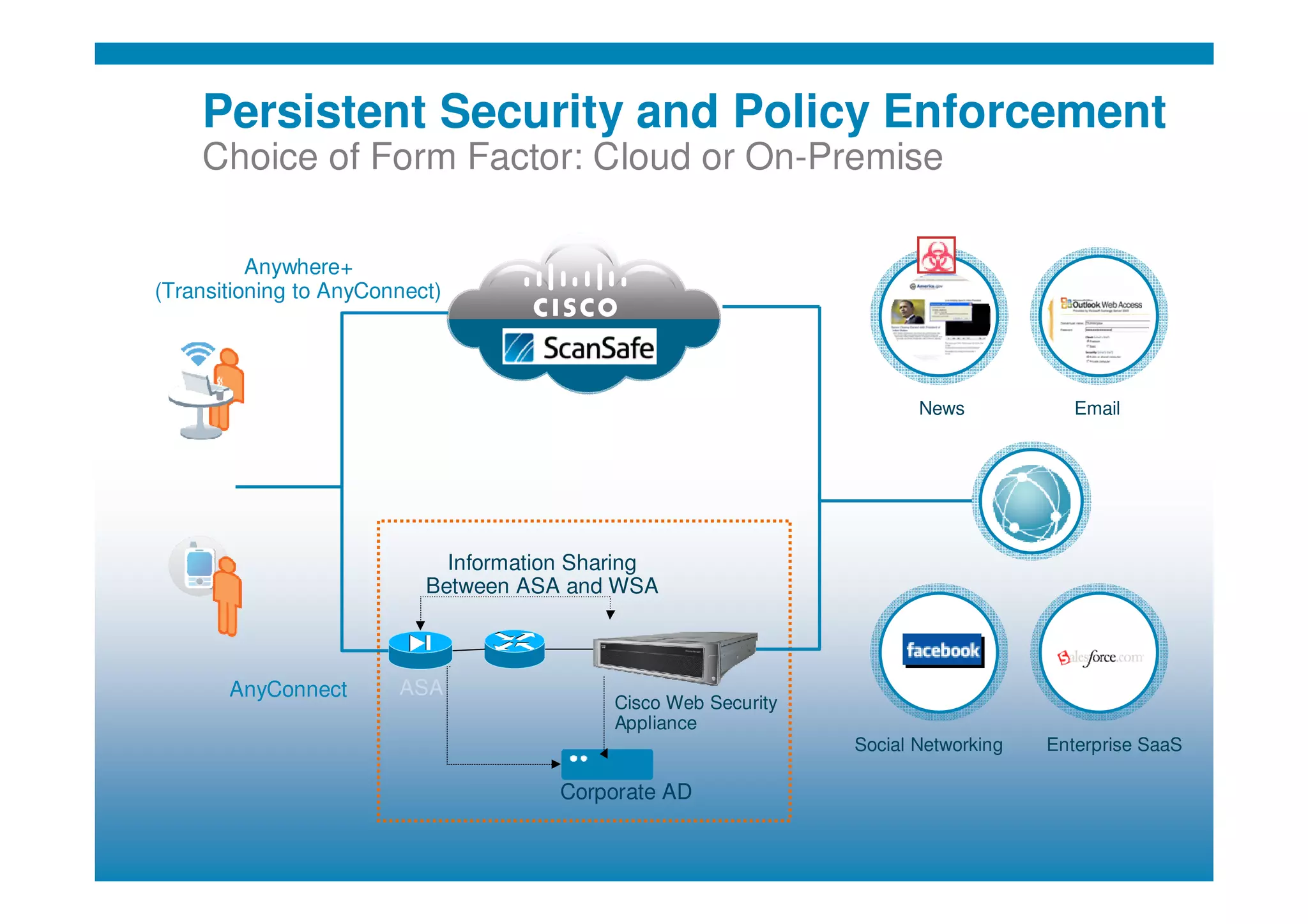
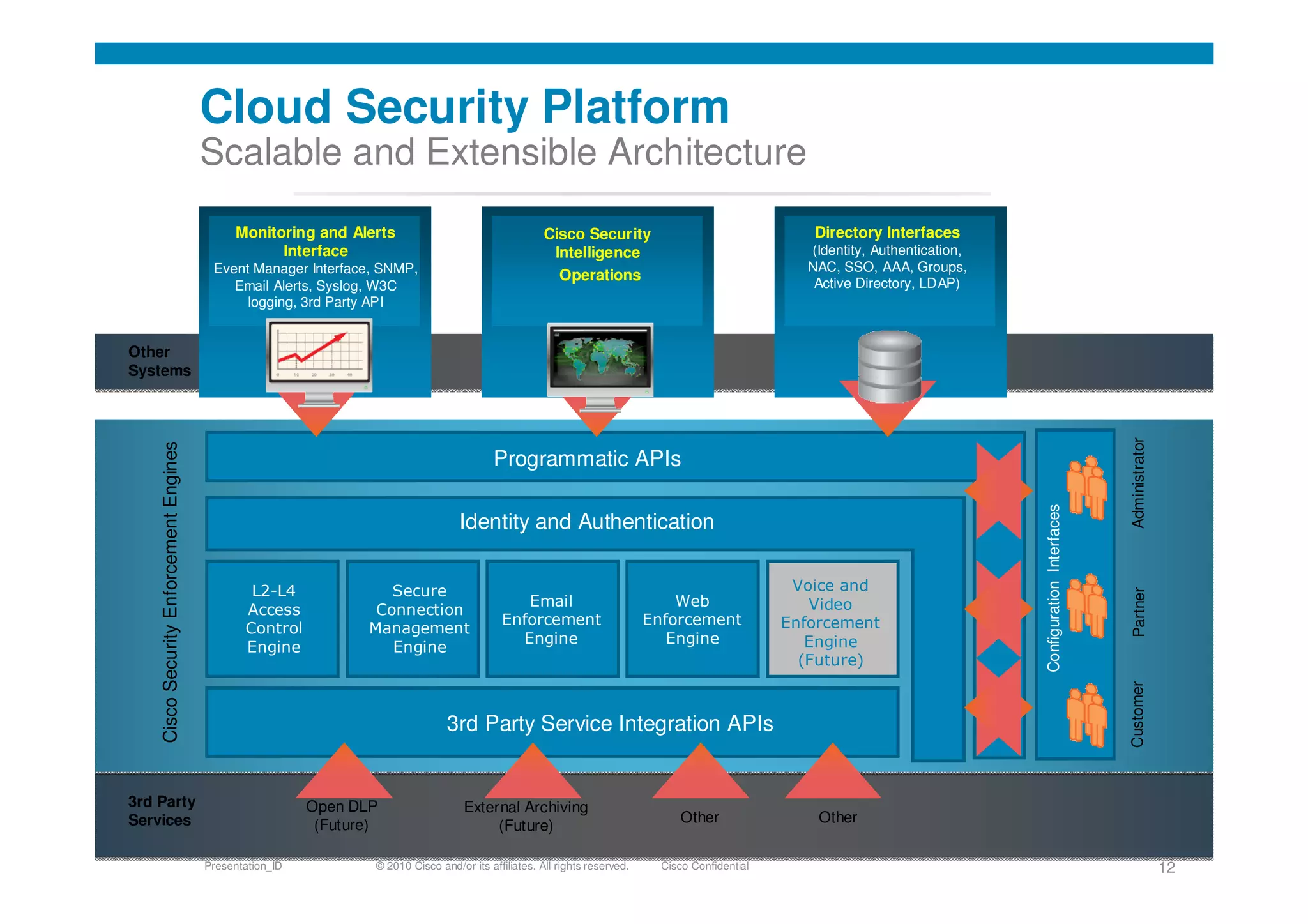
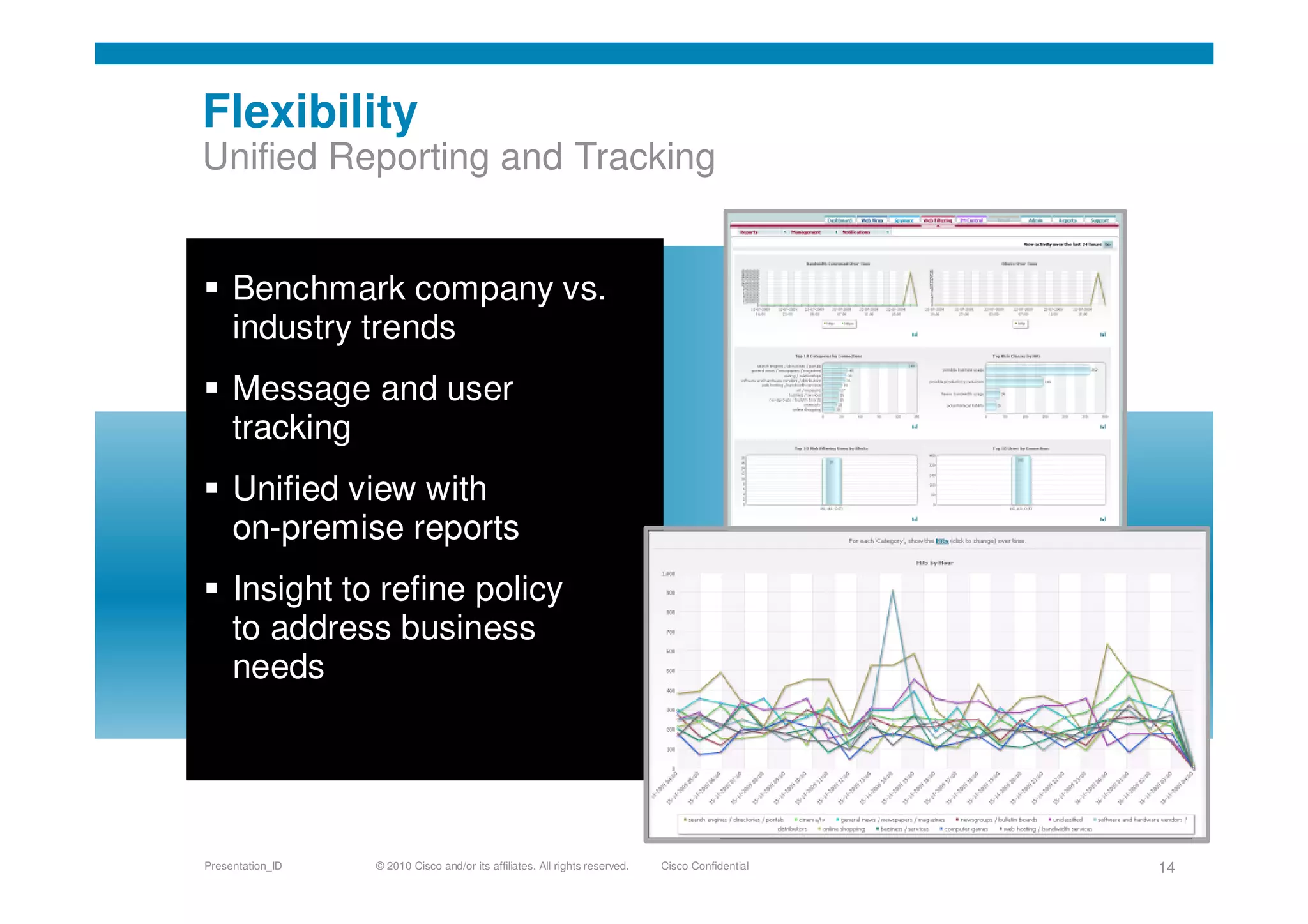
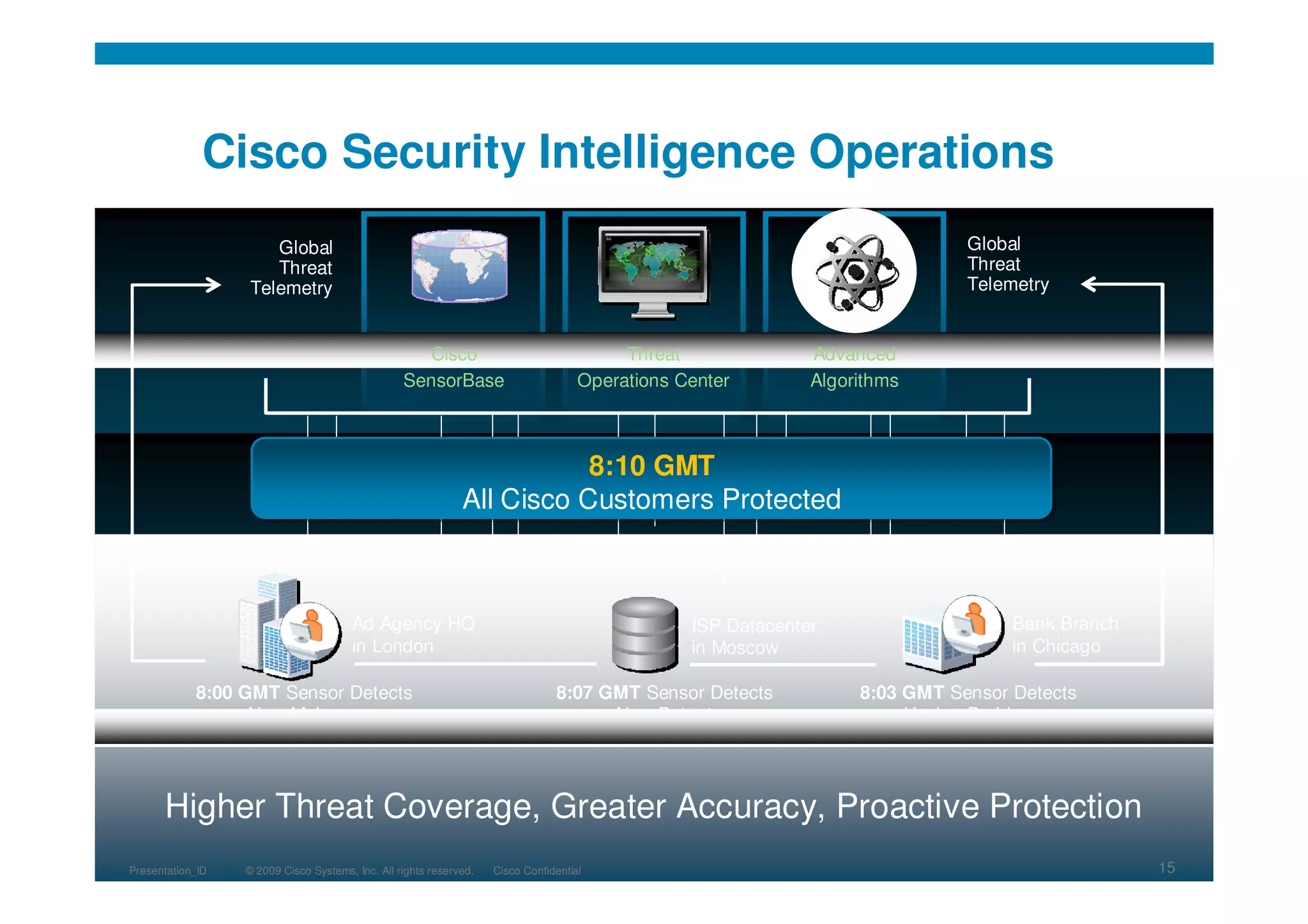
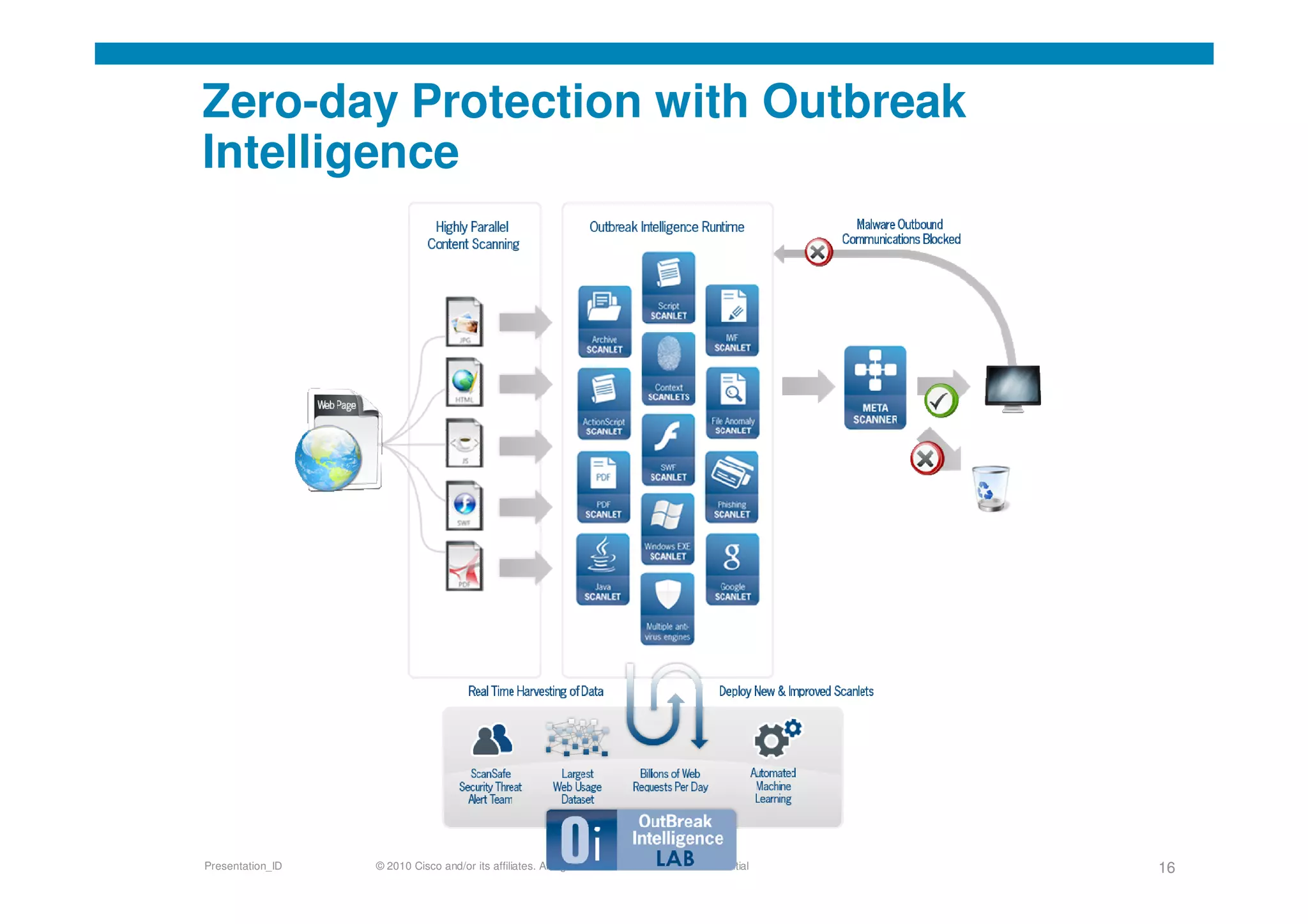
Cisco's cloud security strategy emphasizes a borderless network architecture, addressing challenges in cloud migration while balancing flexibility and security. The company offers a hybrid security platform that integrates both on-premise and cloud solutions, focusing on user mobility and persistent security. Key features include improved visibility, co-management capabilities, and proactive threat protection, supported by Cisco's global threat intelligence operations.