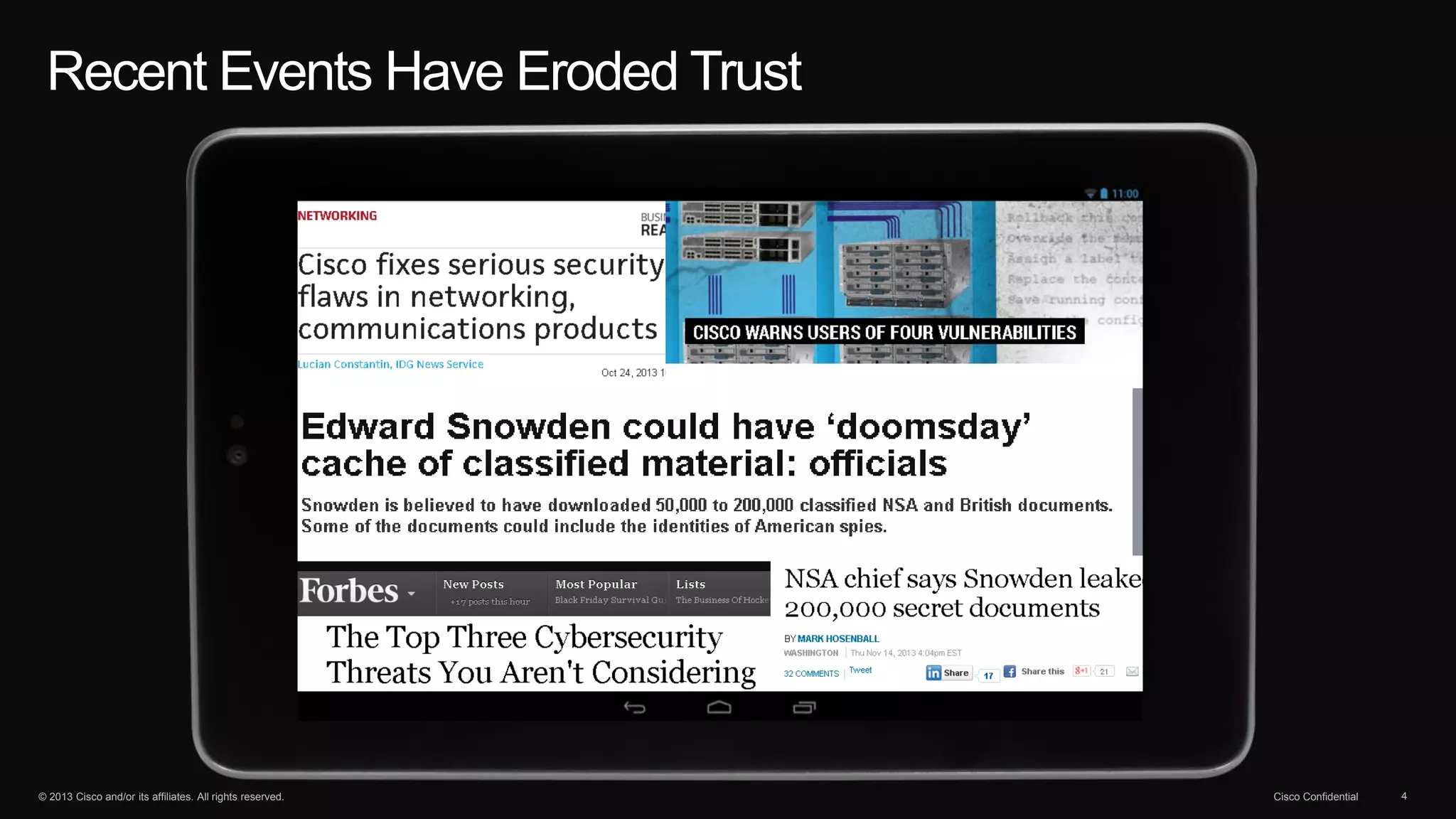
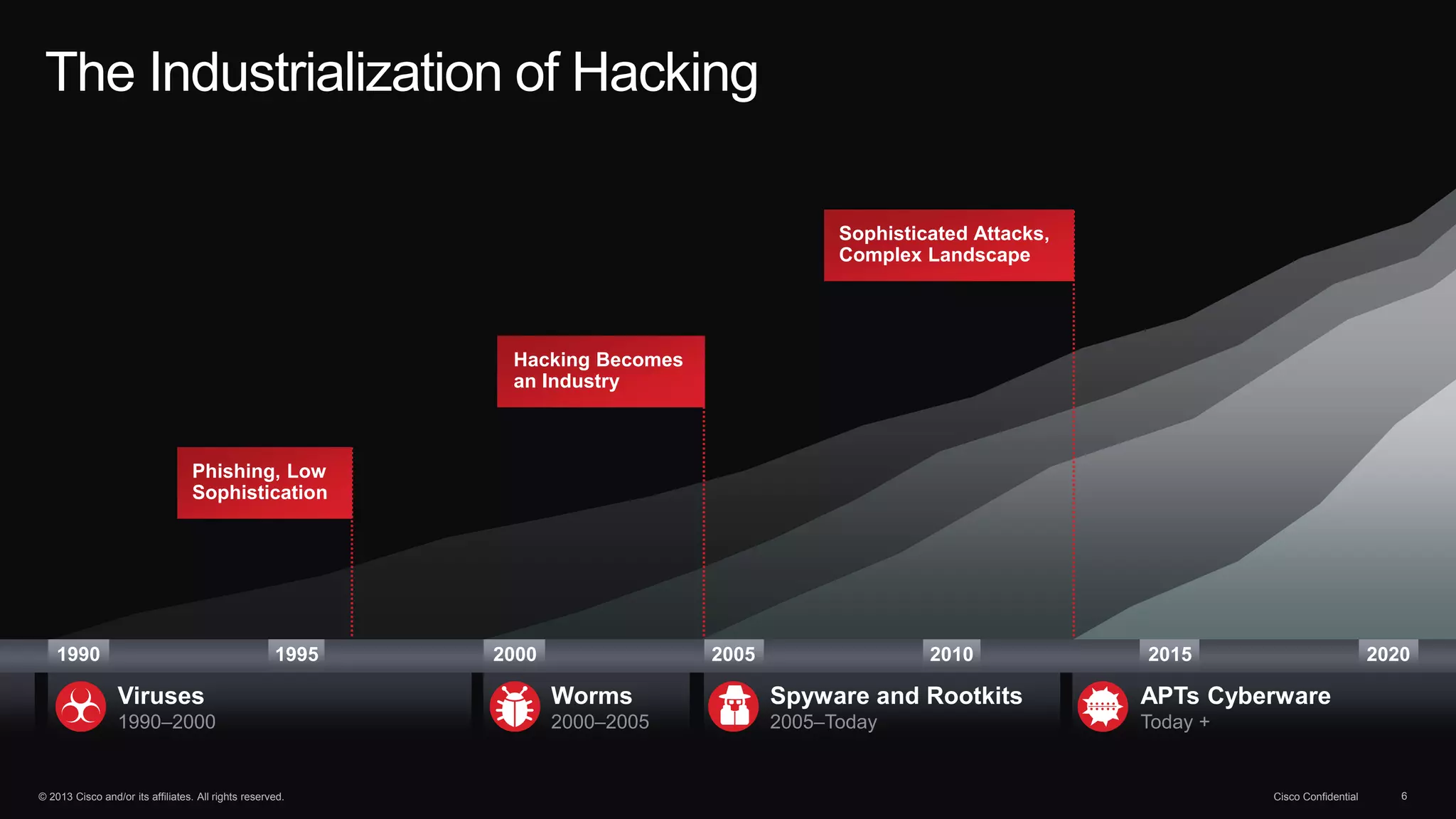
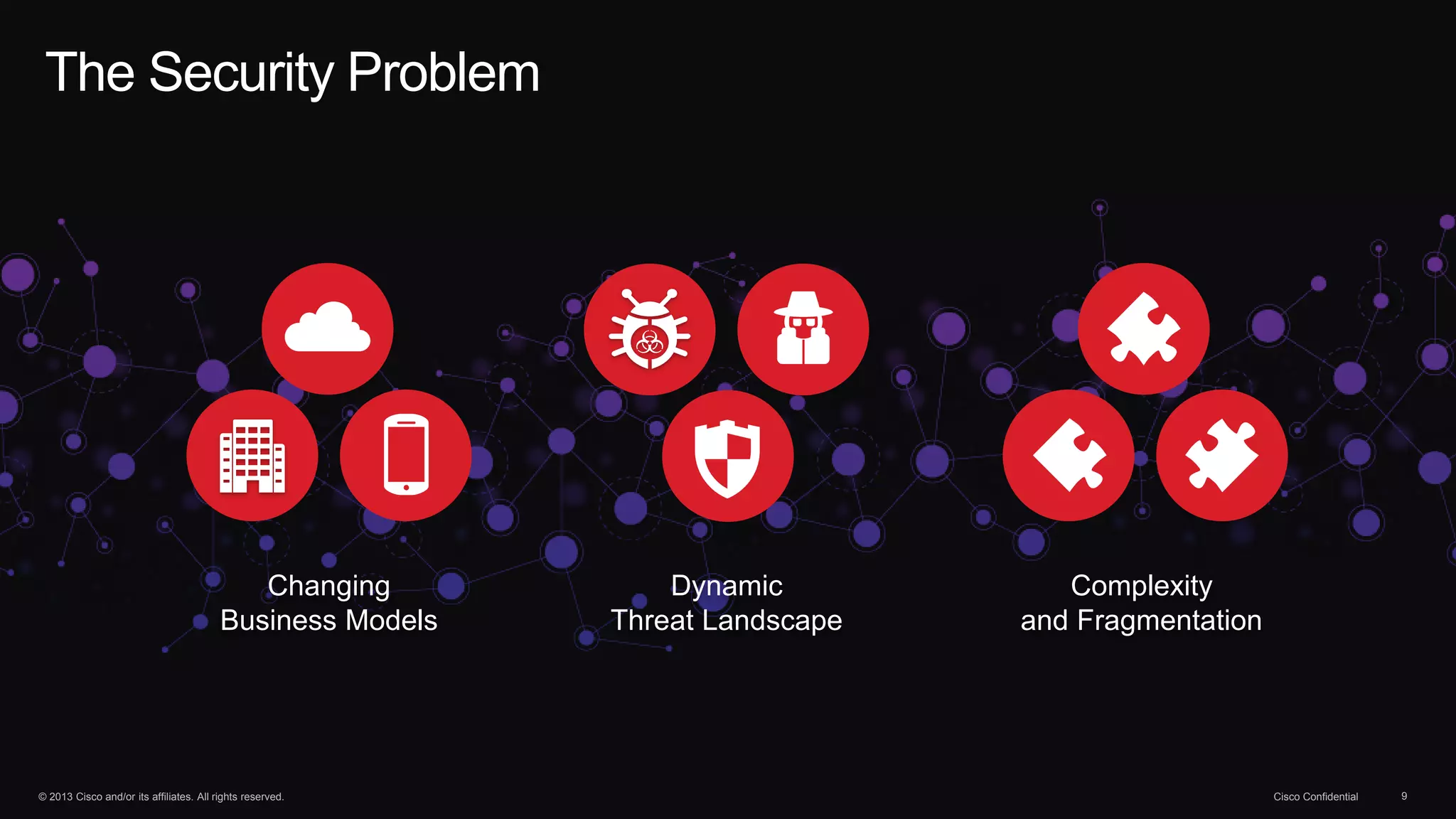
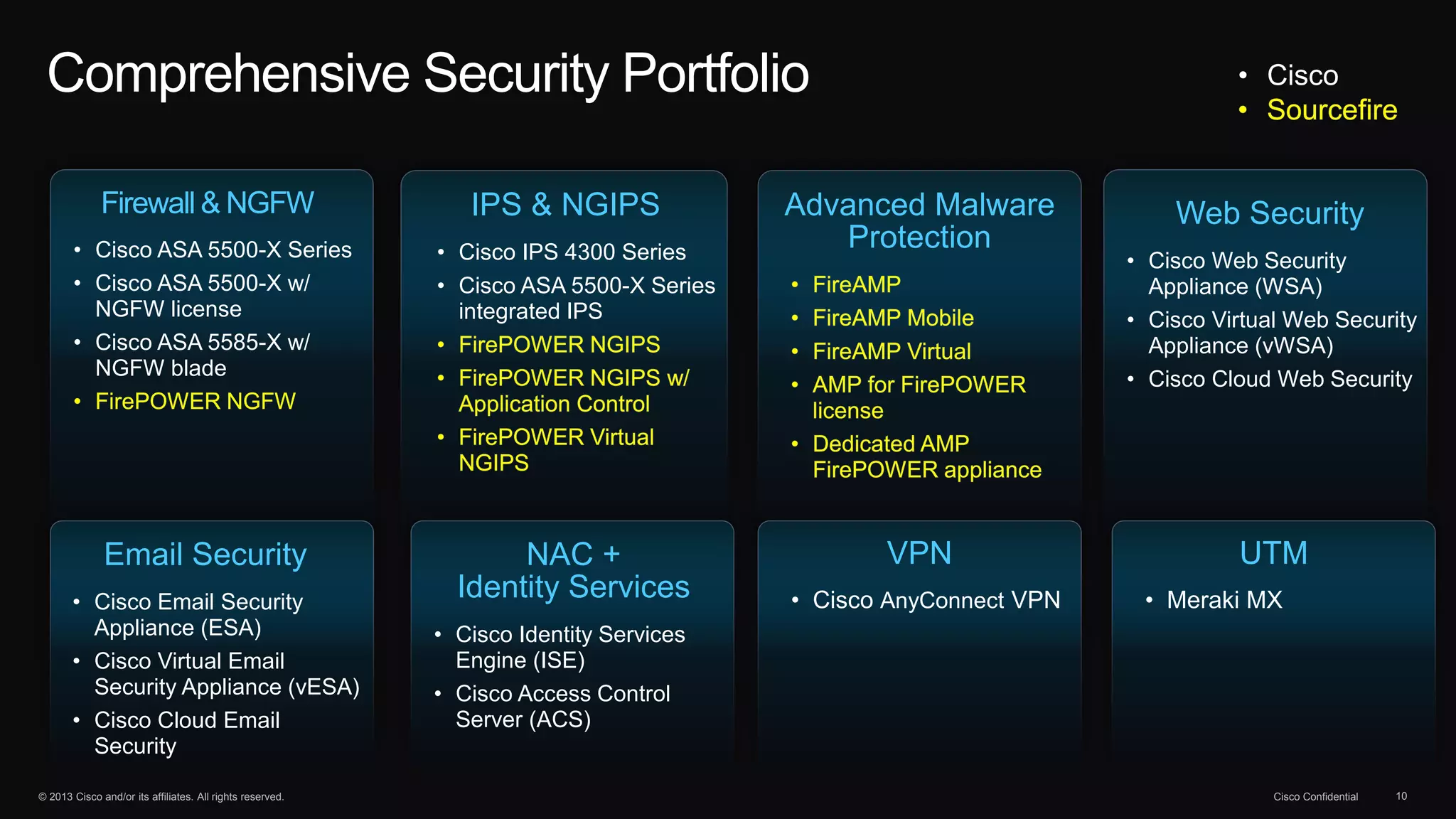
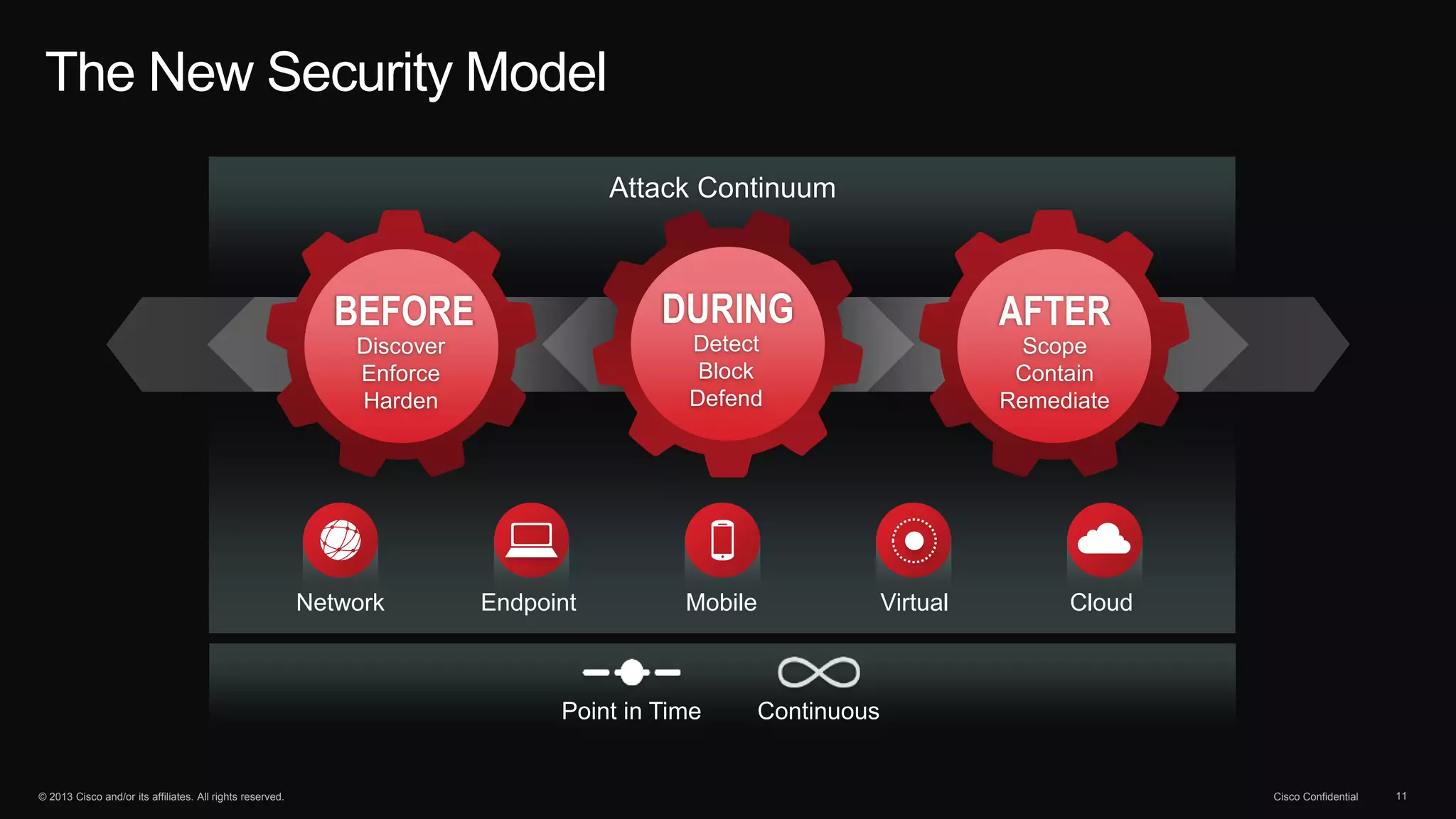
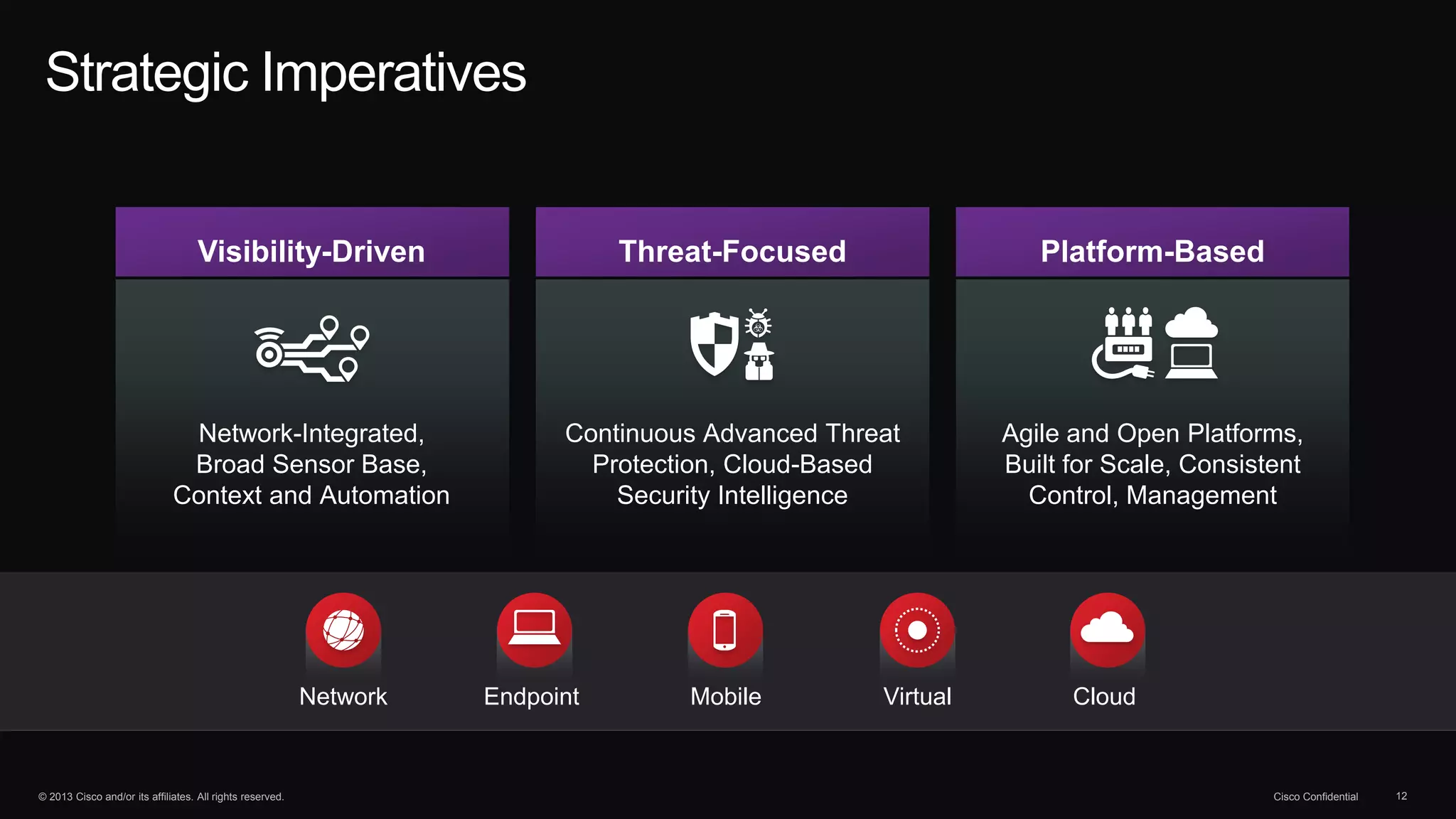
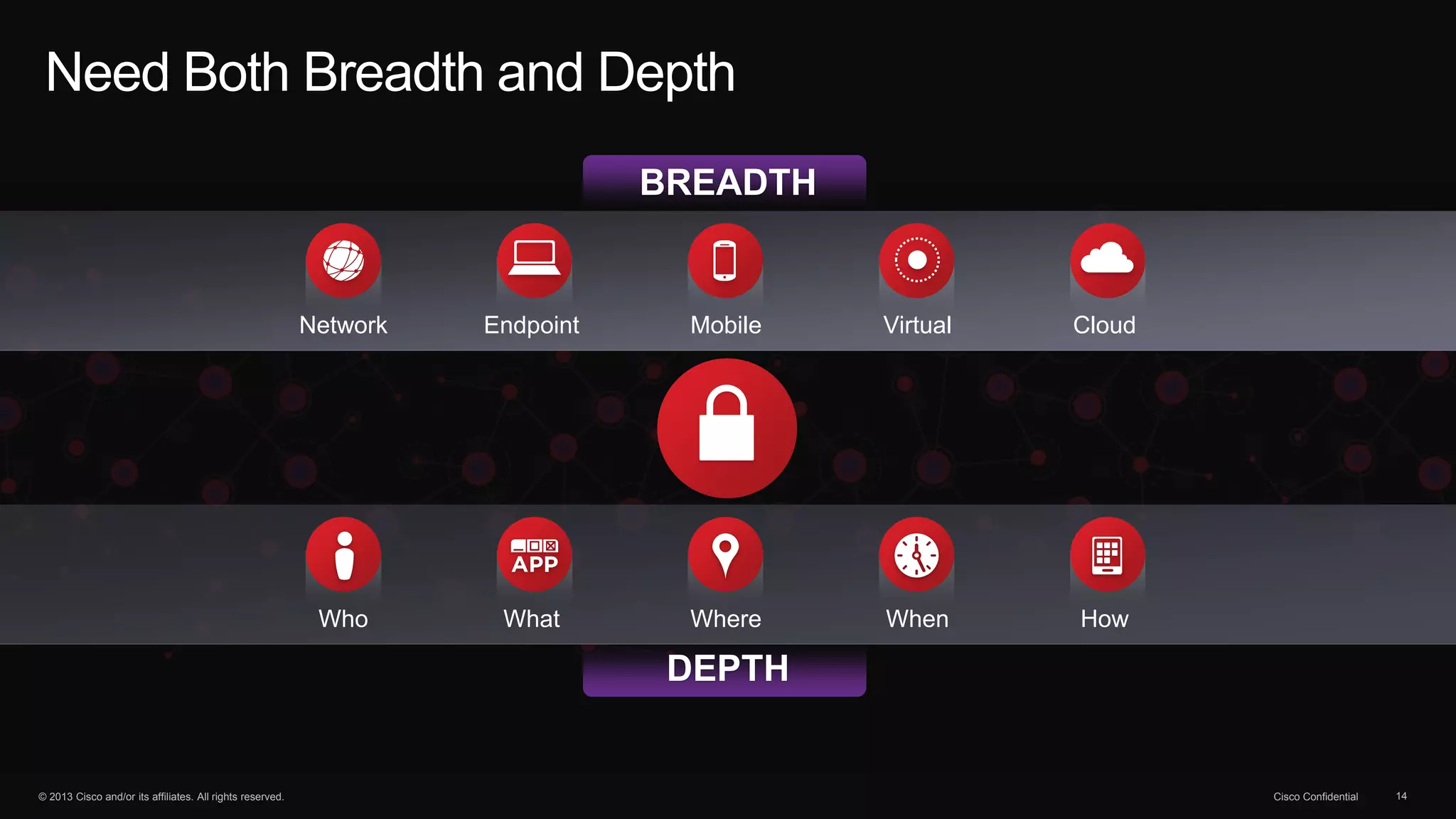
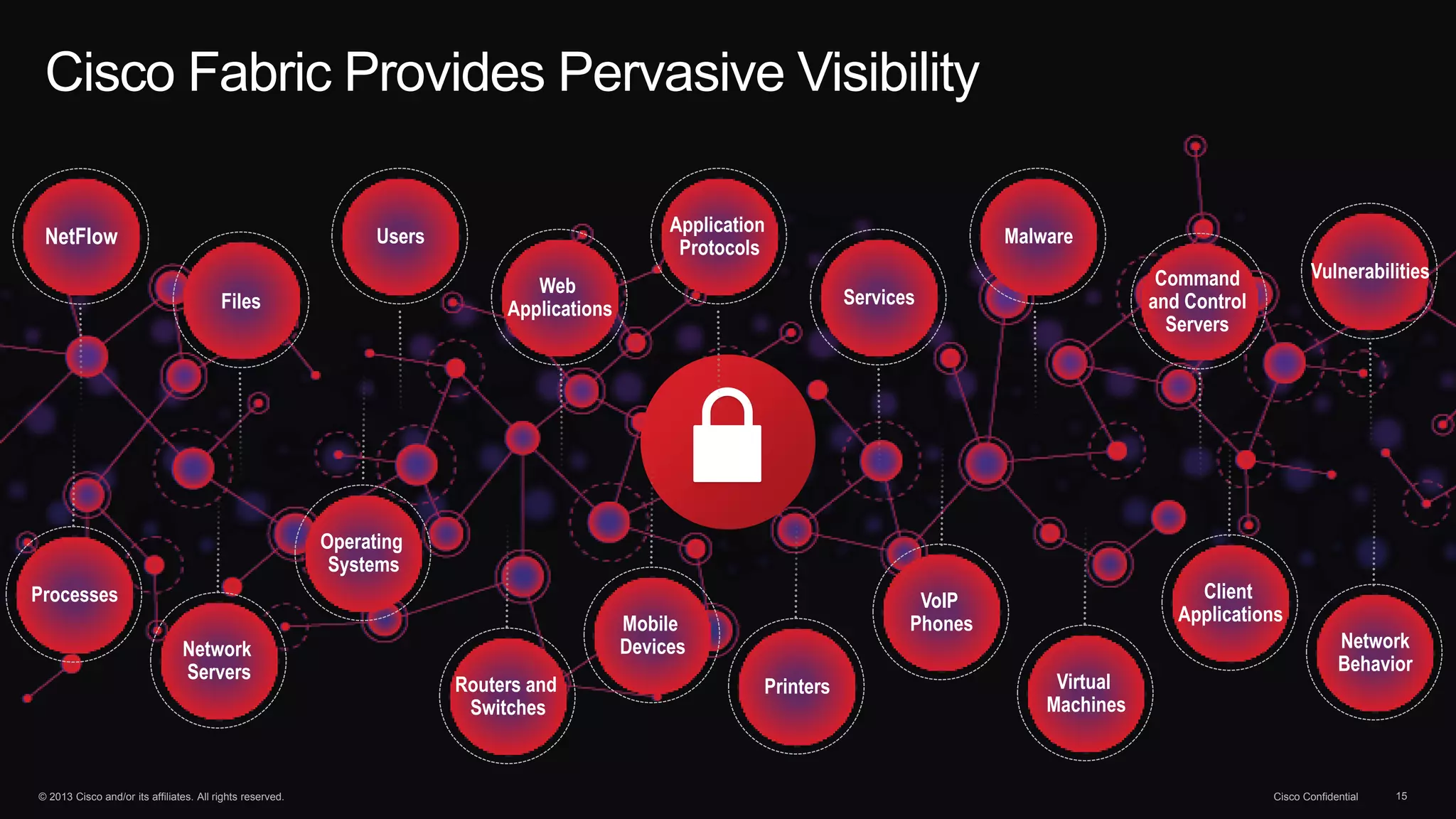
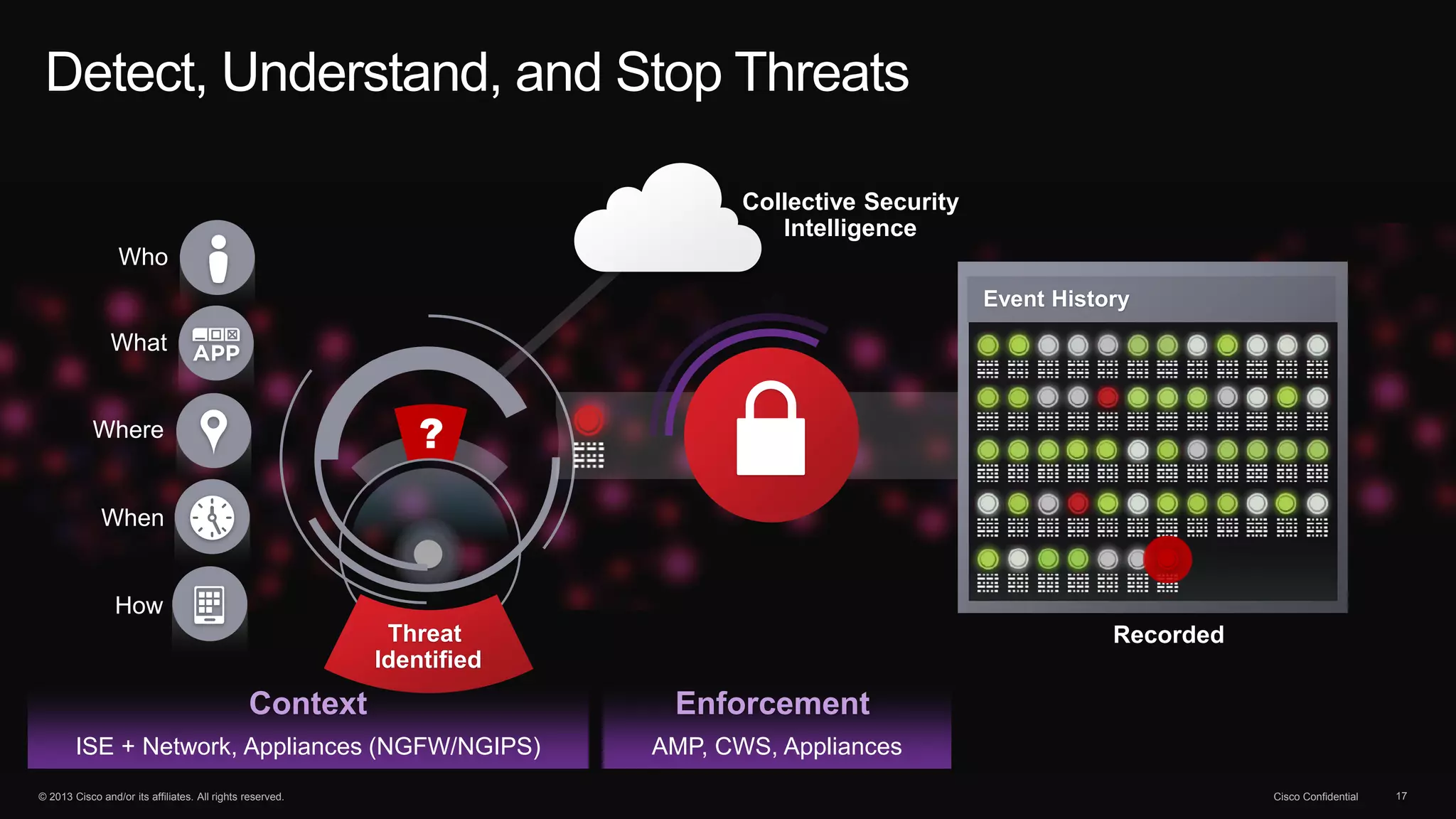
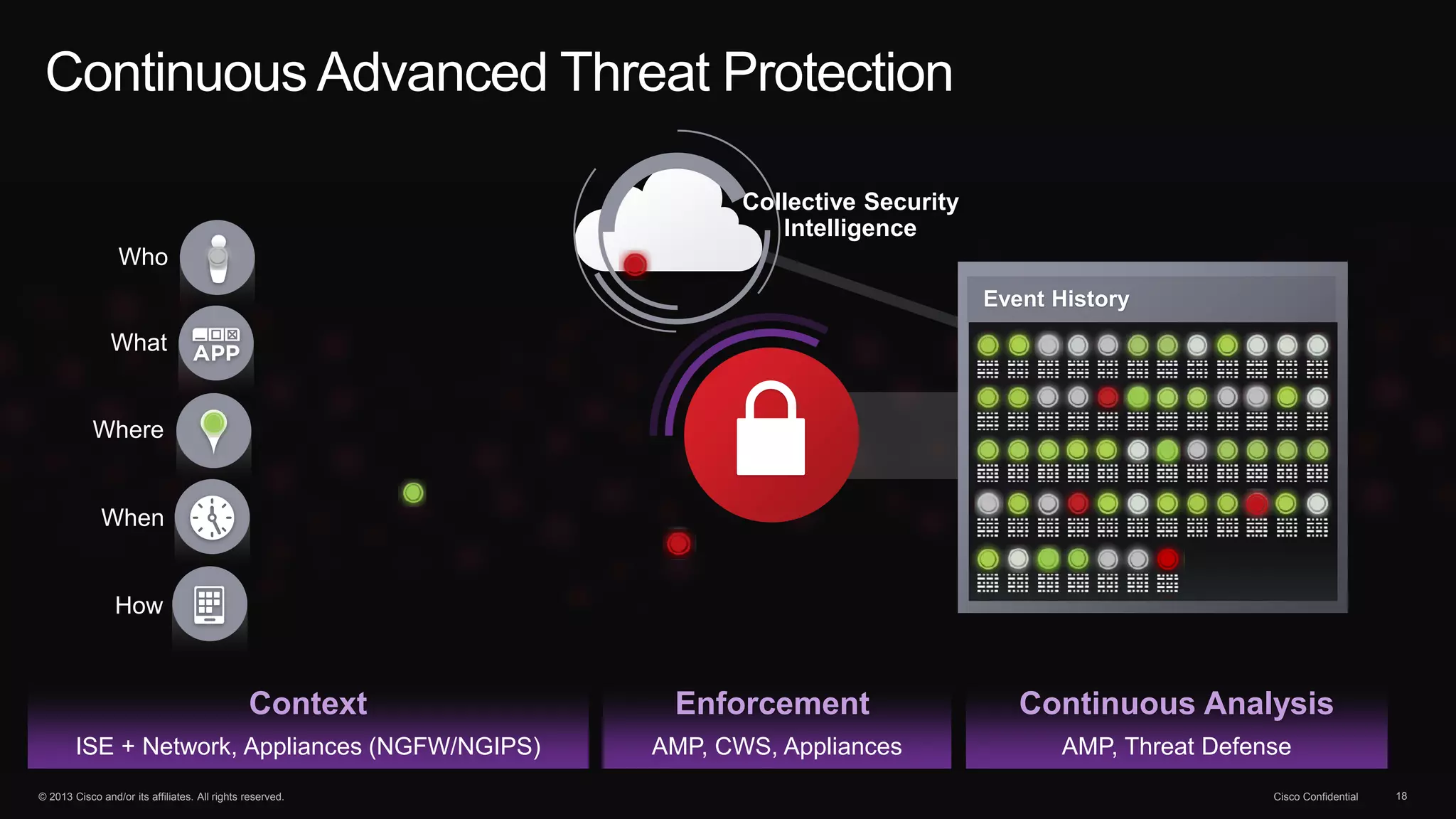
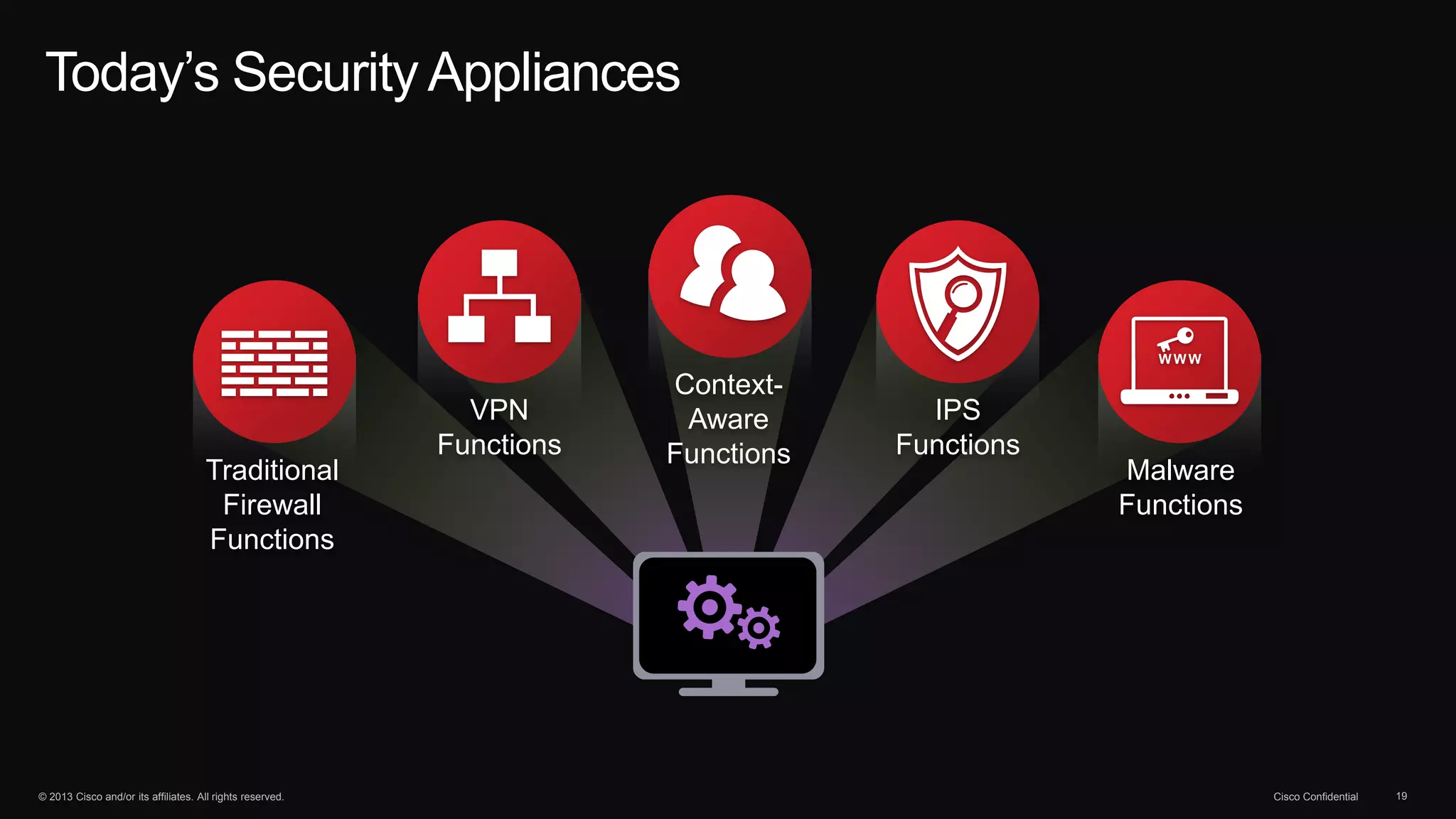
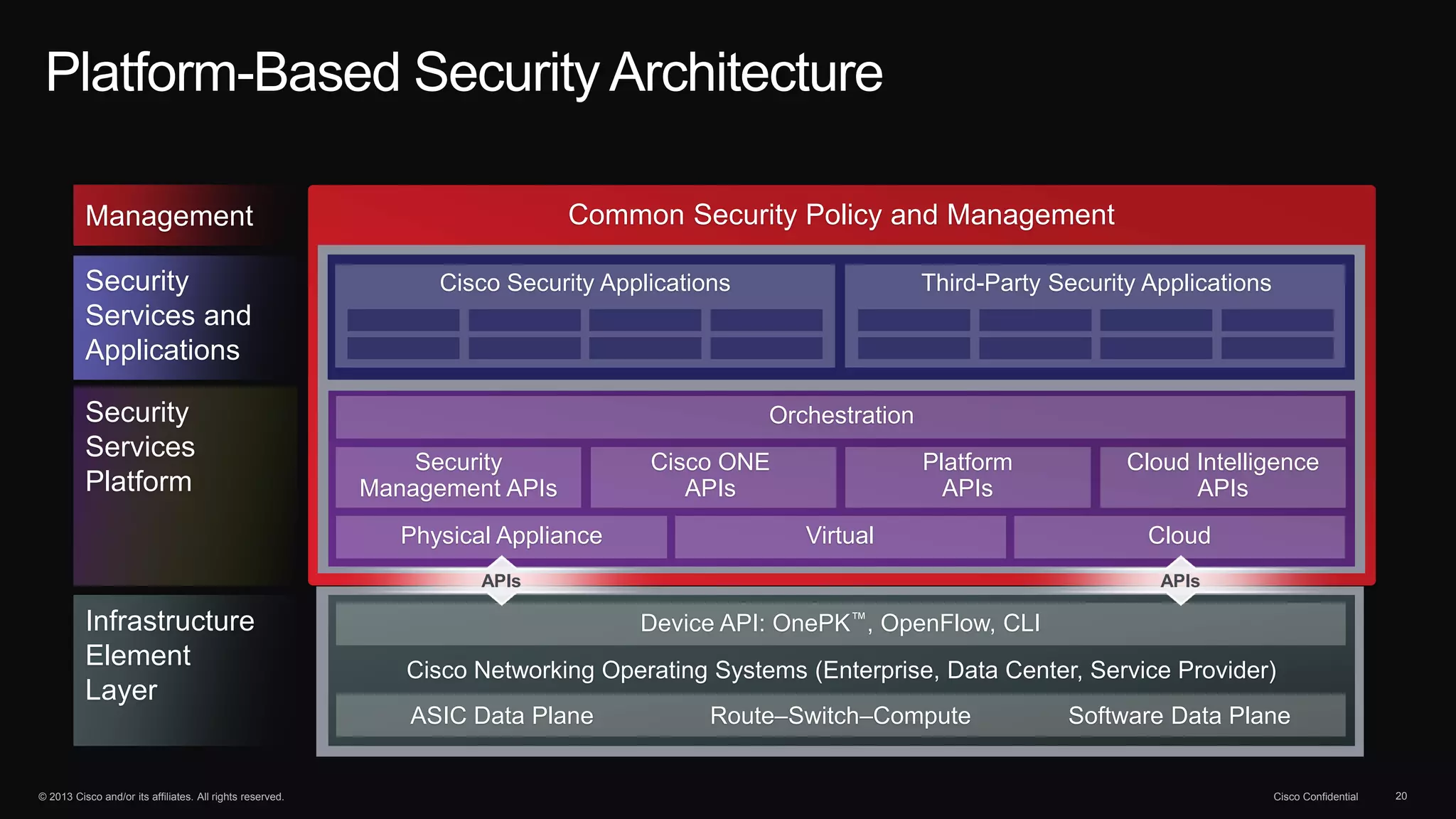
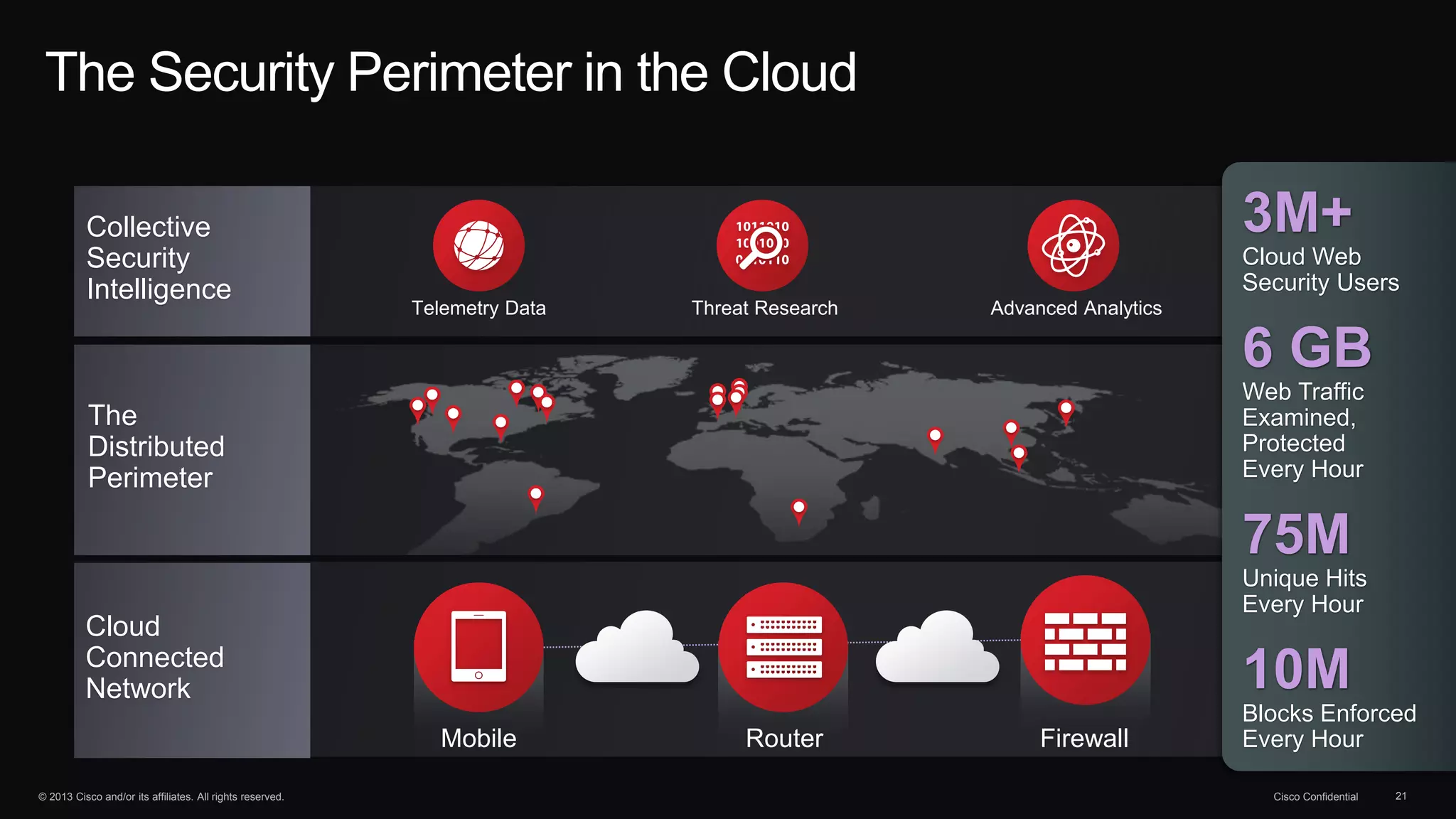
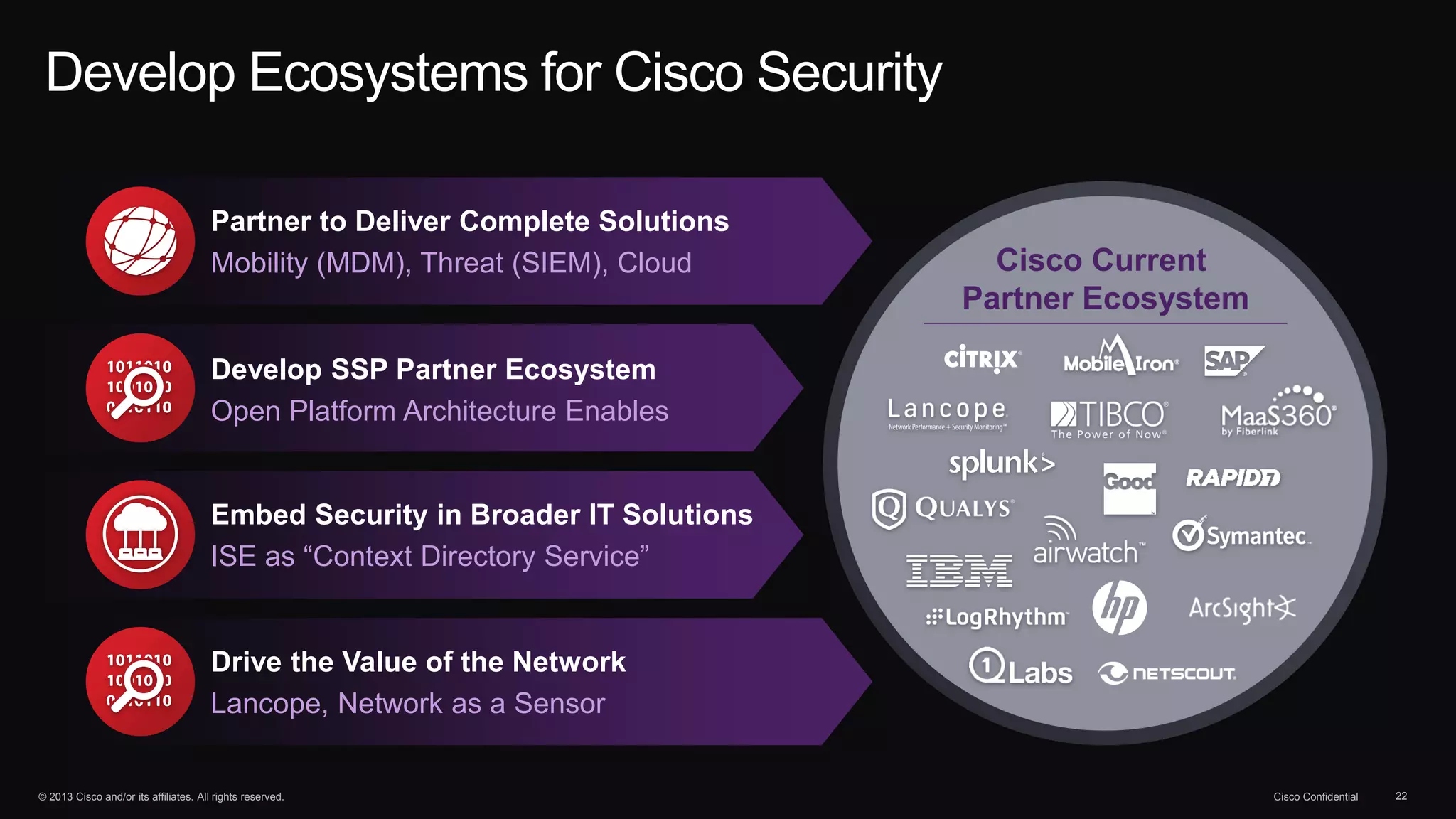
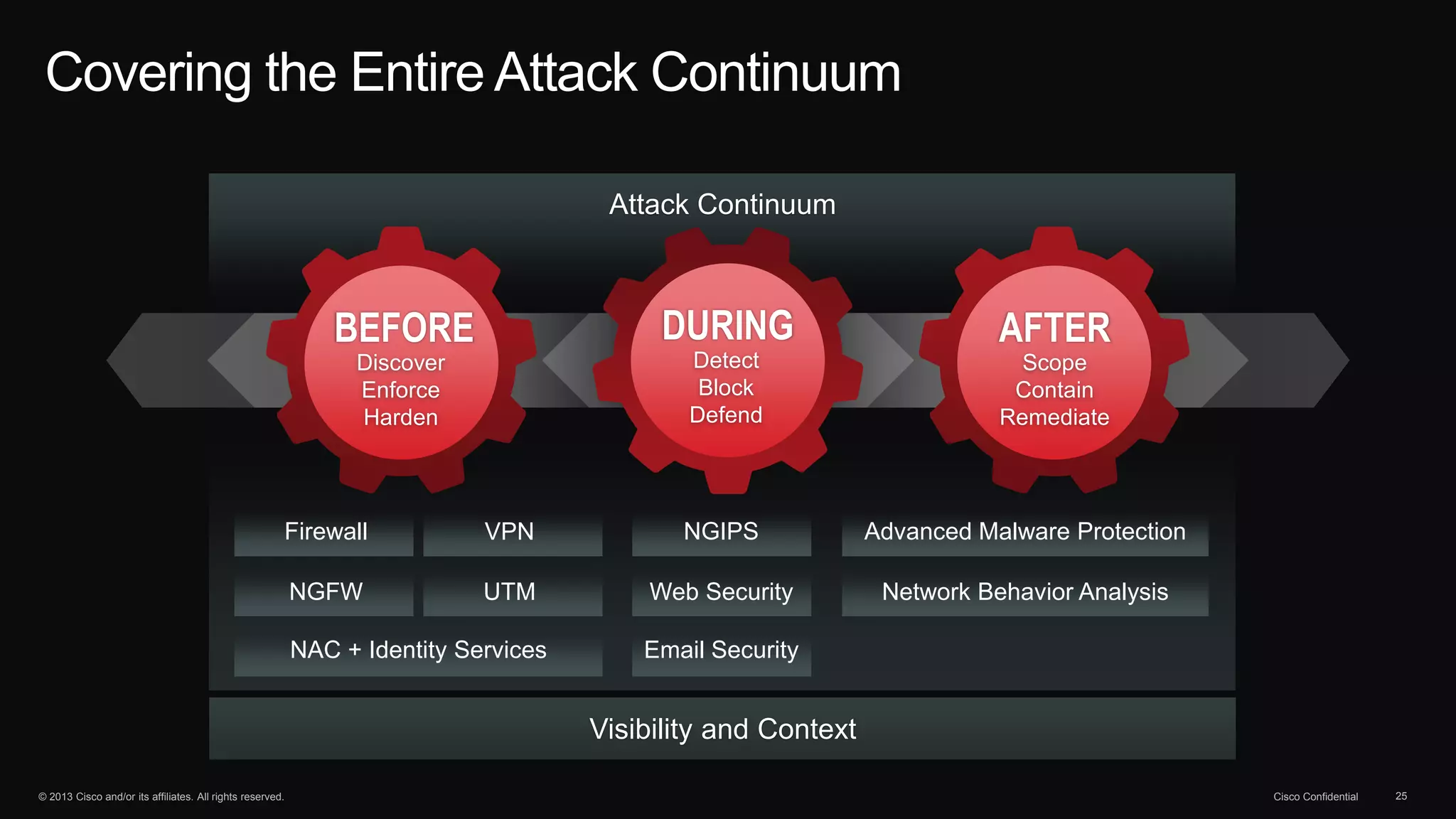
The document discusses the evolution of cybersecurity threats and emphasizes the need for a comprehensive security portfolio to address these challenges. It outlines Cisco's vision and strategy for securing next-generation networks and data centers through continuous advanced threat protection and visibility-driven security models. The importance of developing ecosystems and partnerships to enhance security measures in a dynamic threat landscape is also highlighted.