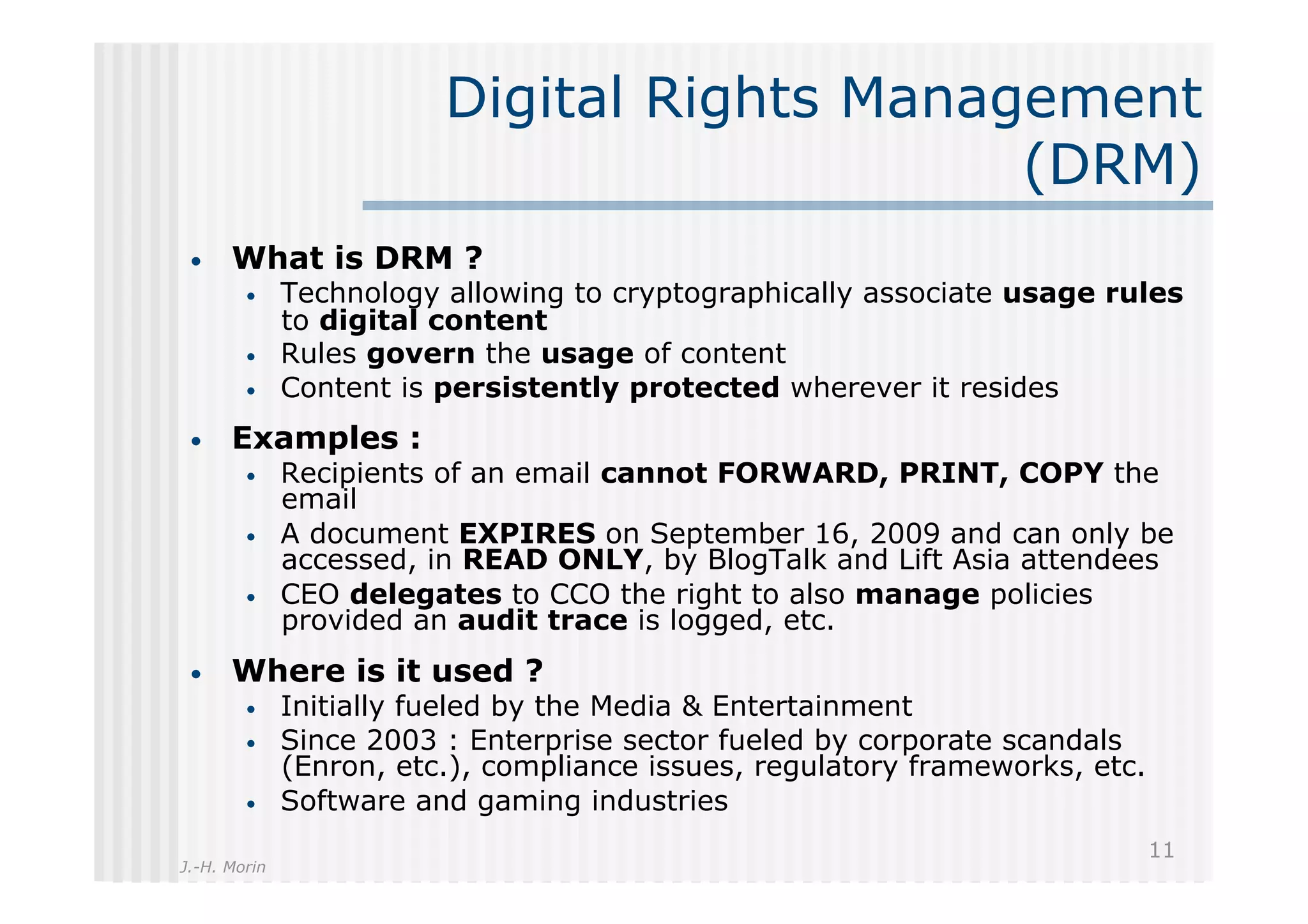
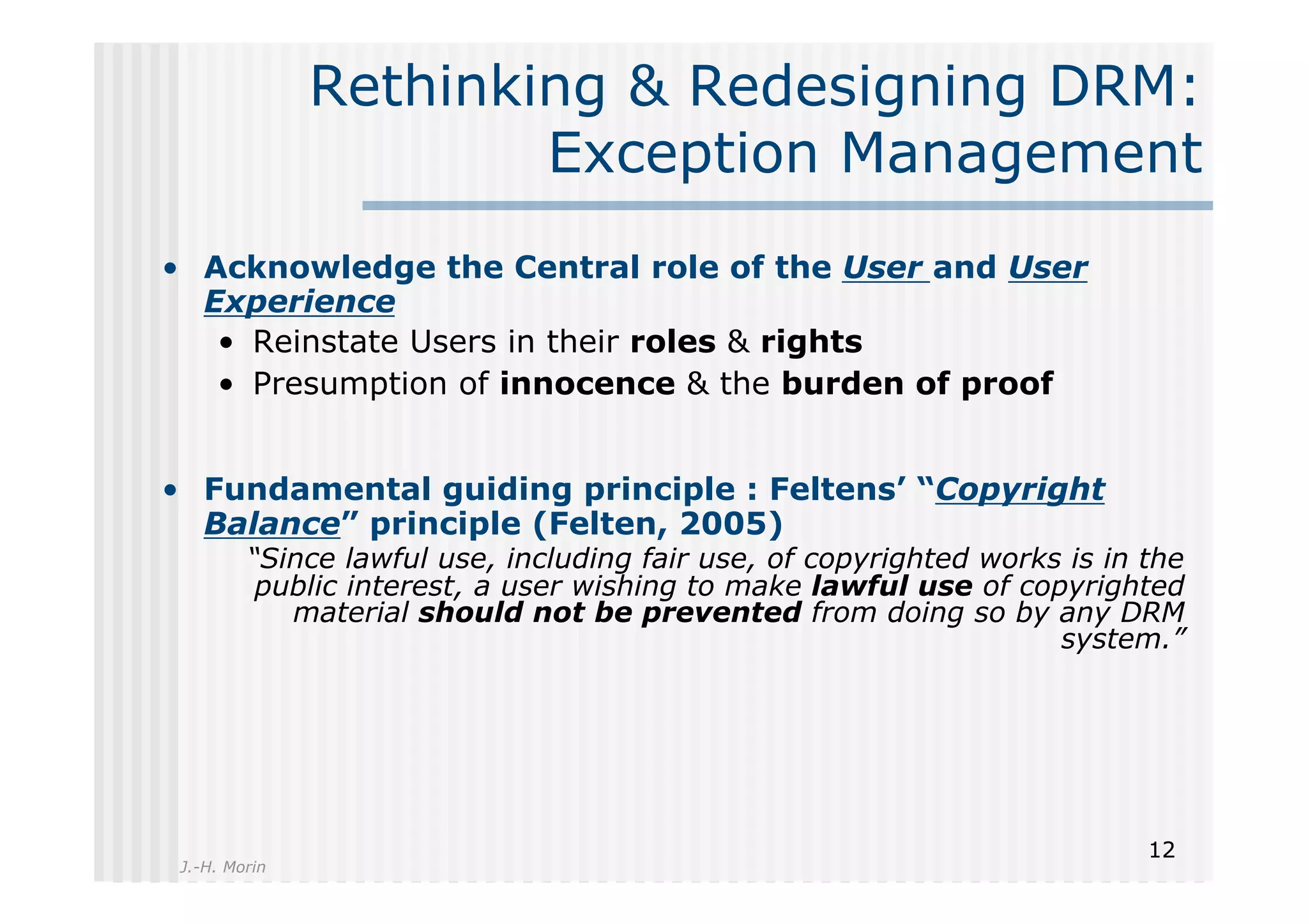
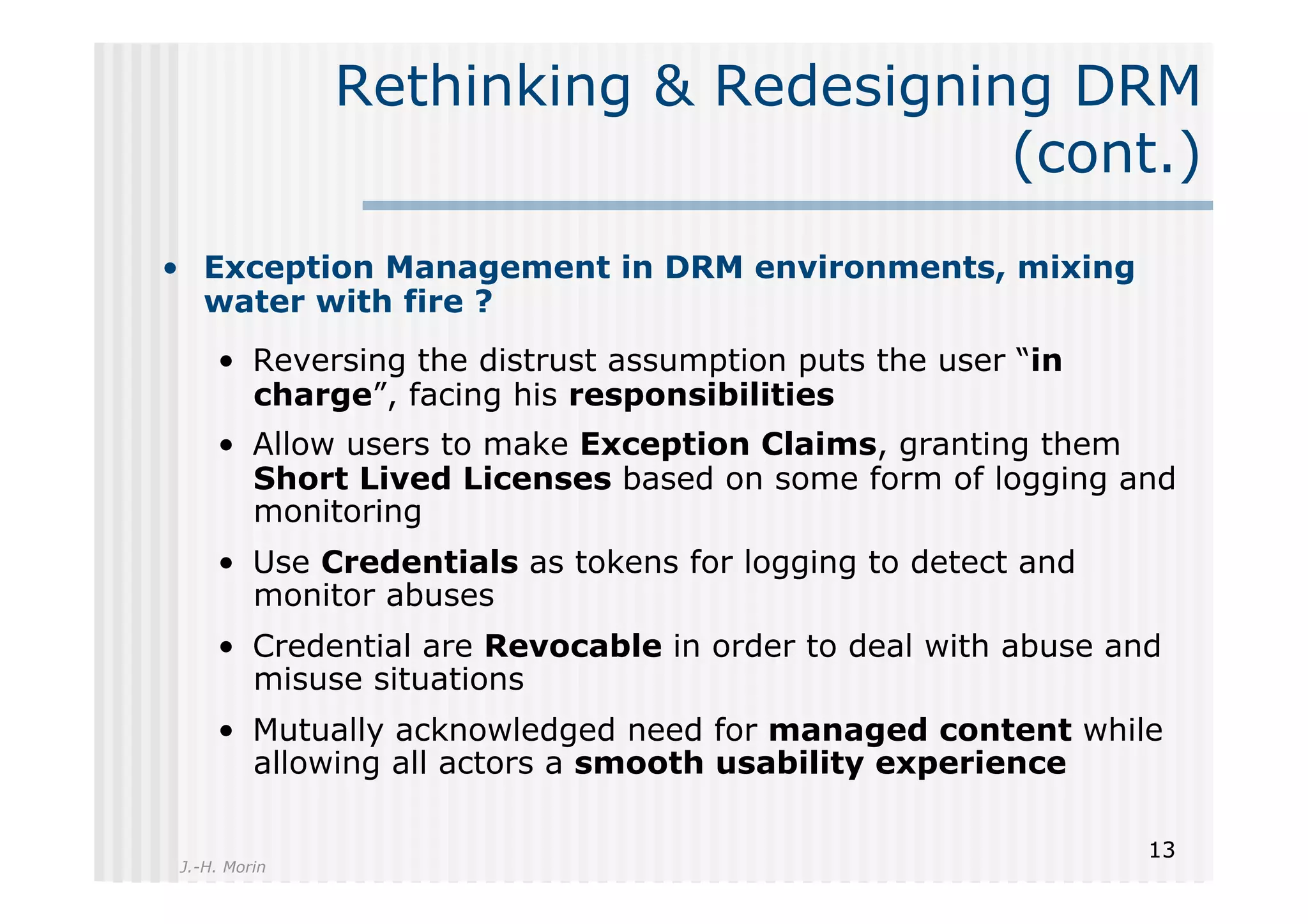
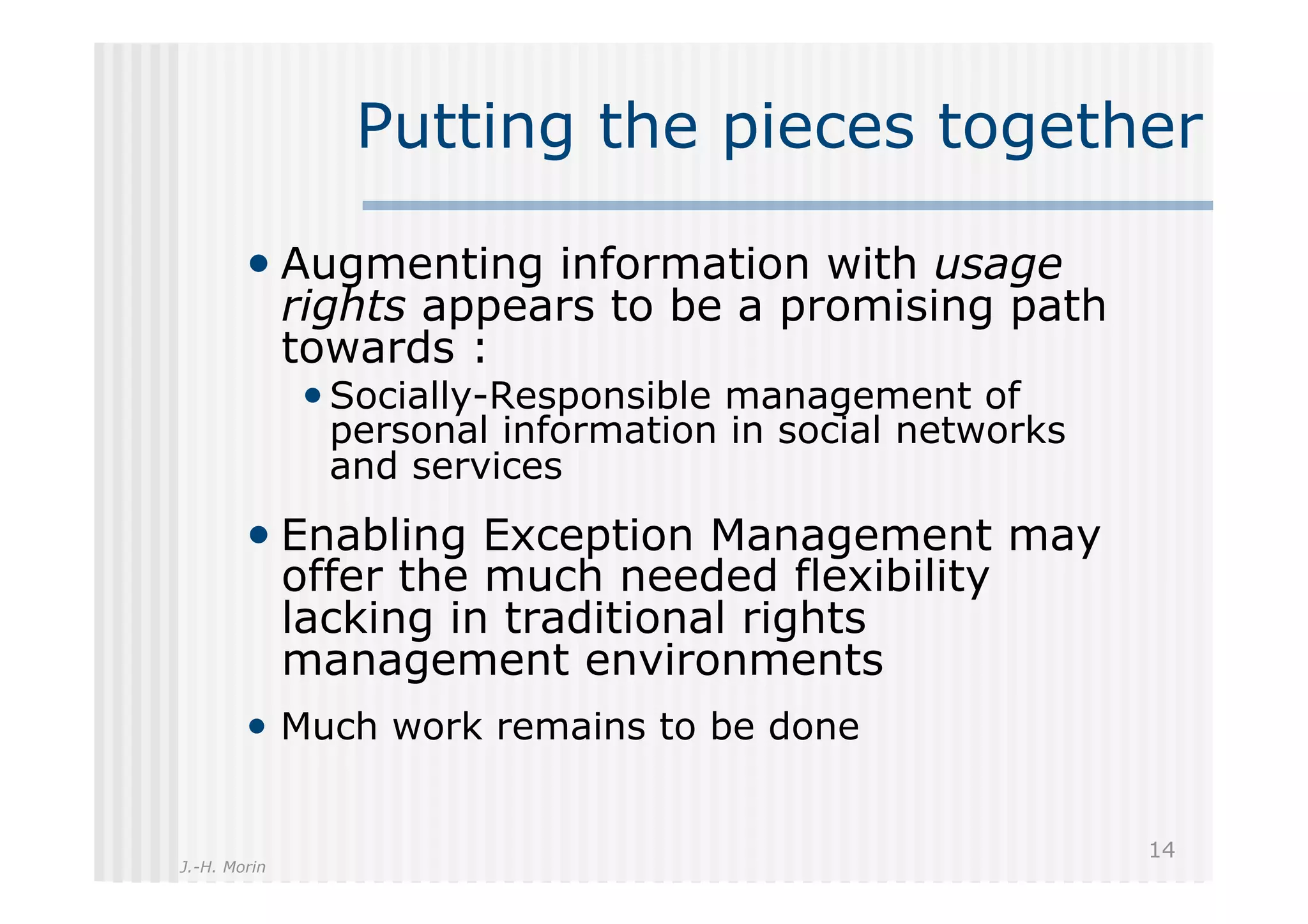
The document discusses the challenges and management of personal information in social networks, emphasizing the need for control over such information amid privacy concerns. It proposes a layered management approach that augments personal data with usage rights and discusses the implications of digital rights management (DRM) and exception management. A call to action for a transdisciplinary approach to innovate socially-responsible solutions for personal information management is also presented.