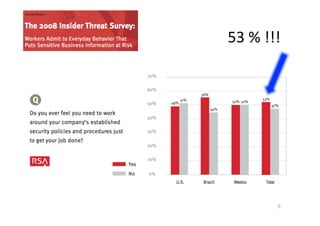
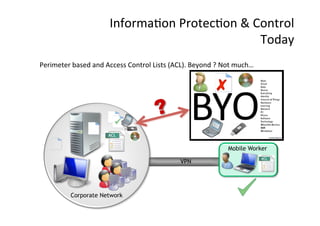
This document summarizes a presentation on reinstituting trust in the digital age. It discusses three eras of trust: before was based on suspicion, today is defined by mass breaches of trust, and tomorrow could see the rise of "informed trust". It proposes reversing the assumption of distrust by allowing users to make exception claims with short-lived licenses to put trust back in users' hands. The exception management model mixes security and usability by granting revocable credentials to detect abuse while providing smooth experiences. Overall, the presentation argues for a major paradigm shift towards digital responsibility and co-compliance based on transparency and informed trust between all stakeholders.





















![Perspec8ve…
• Take
into
account
the
Human
Factor
by
Design
(People
Centric
Security,
PCS
[T.
Scholtz,
2012])
• Data
Protec8on
in
a
digital
economy
:
– Awareness
raising
and
training
– The
EU
Data
Protec8on
reform:
re-‐appropria;on
of
data
and
personal
informa;on
by
the
people
• Public
Policies
and
Digital
Governance
:
Key
success
factors,
Emergency!](https://image.slidesharecdn.com/digitaltrust2015pwc-morin-150319175755-conversion-gate01/85/Reinstating-Trust-in-the-Digital-Age-26-320.jpg)





