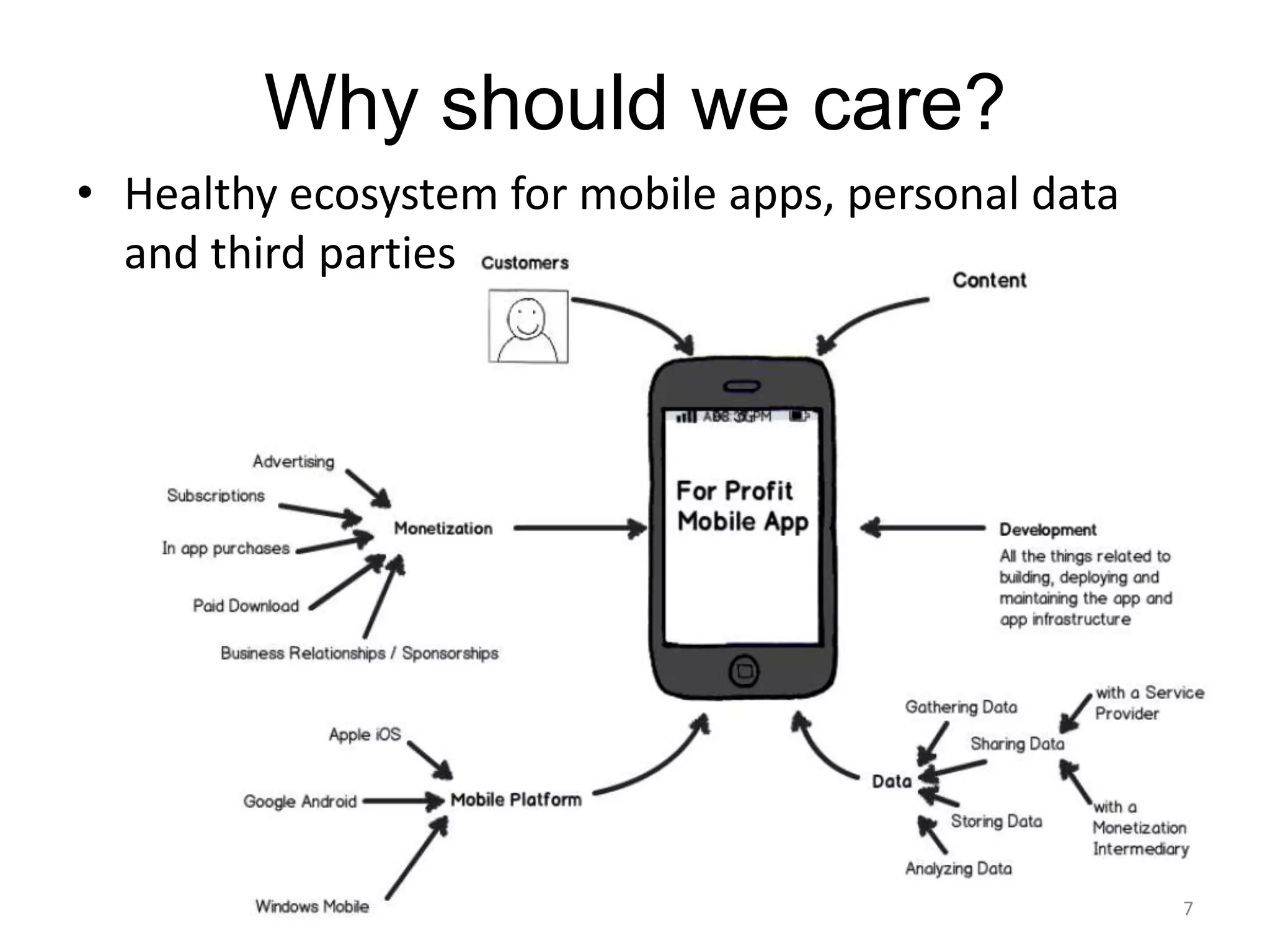
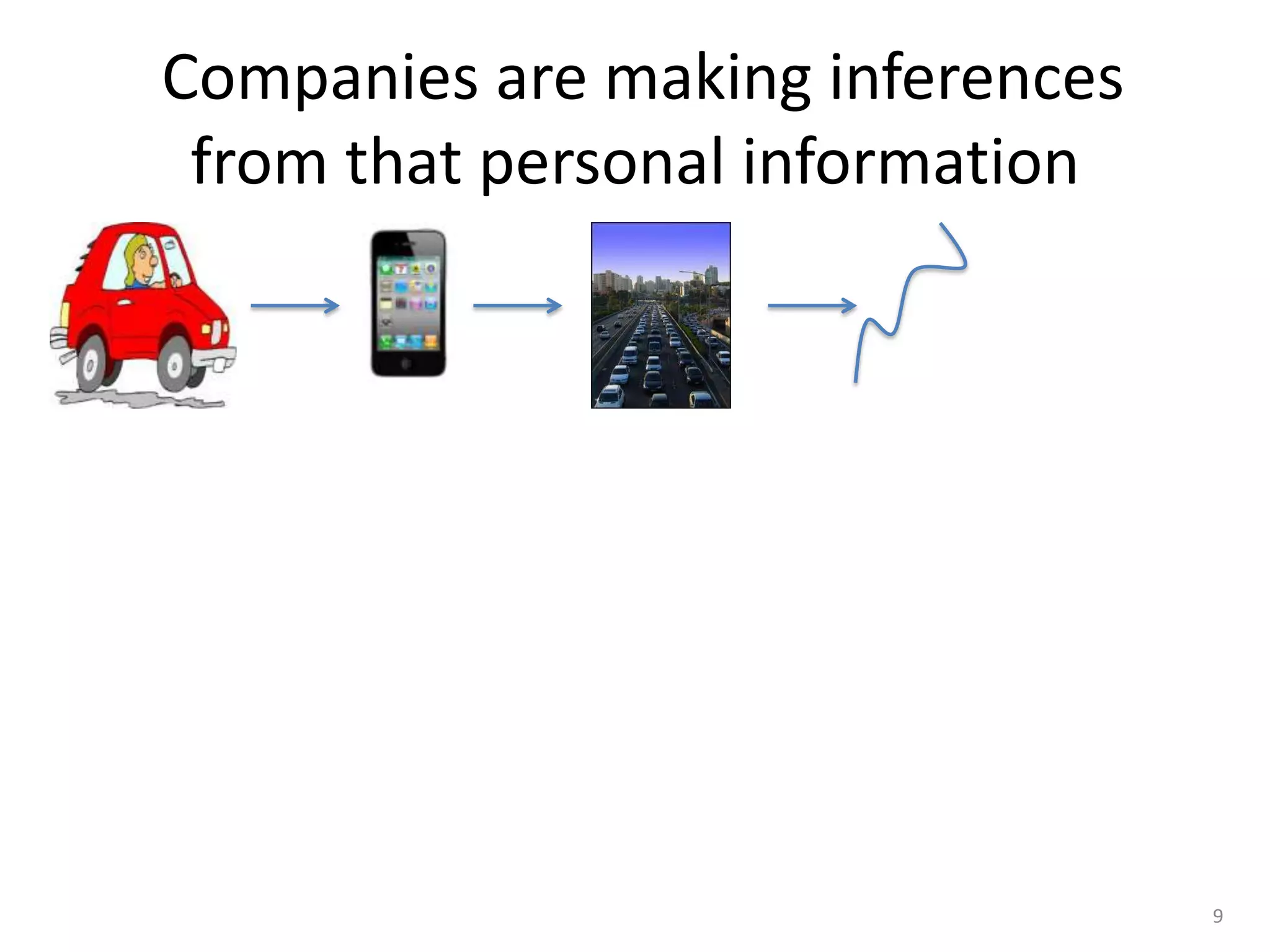
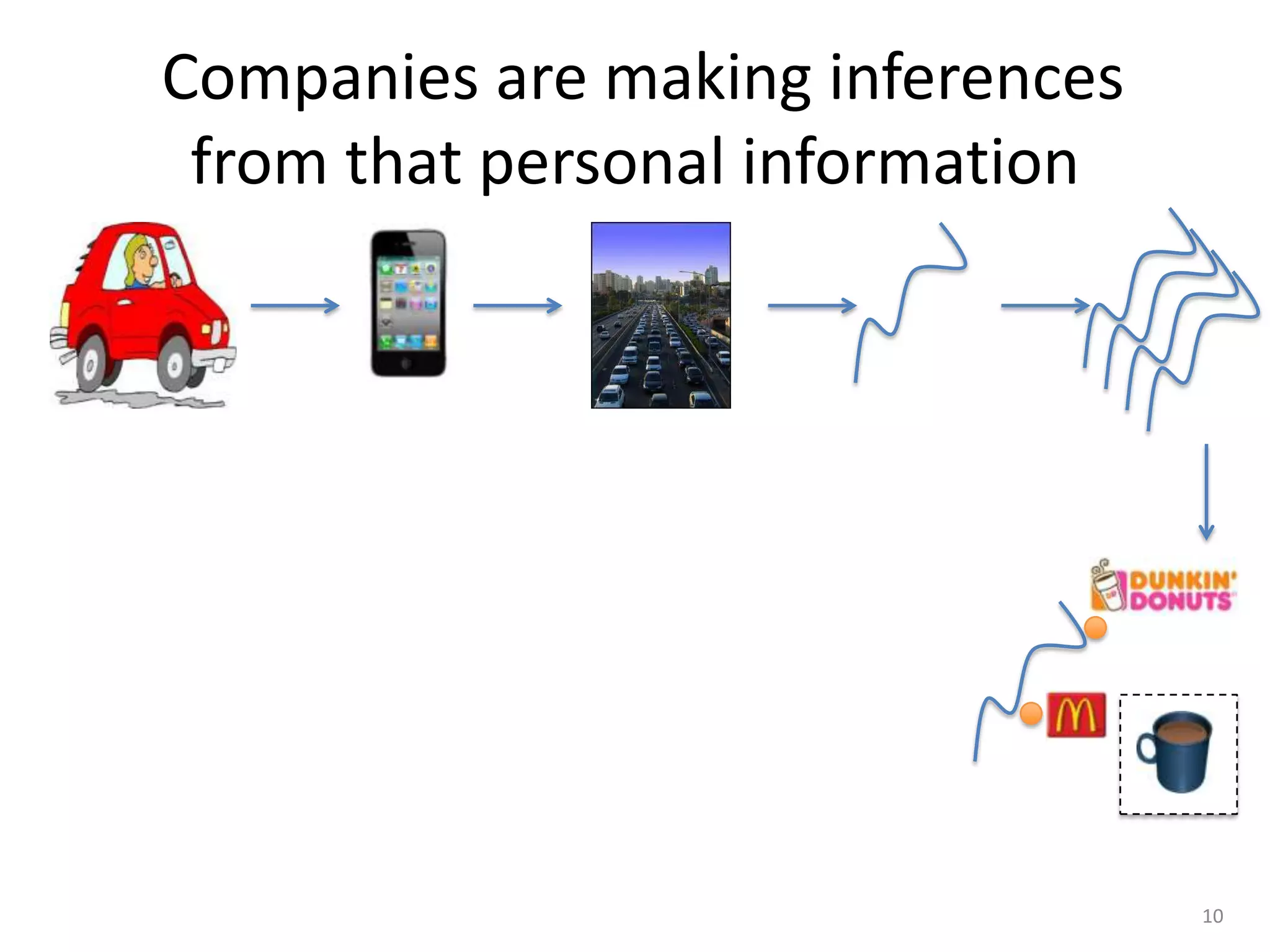
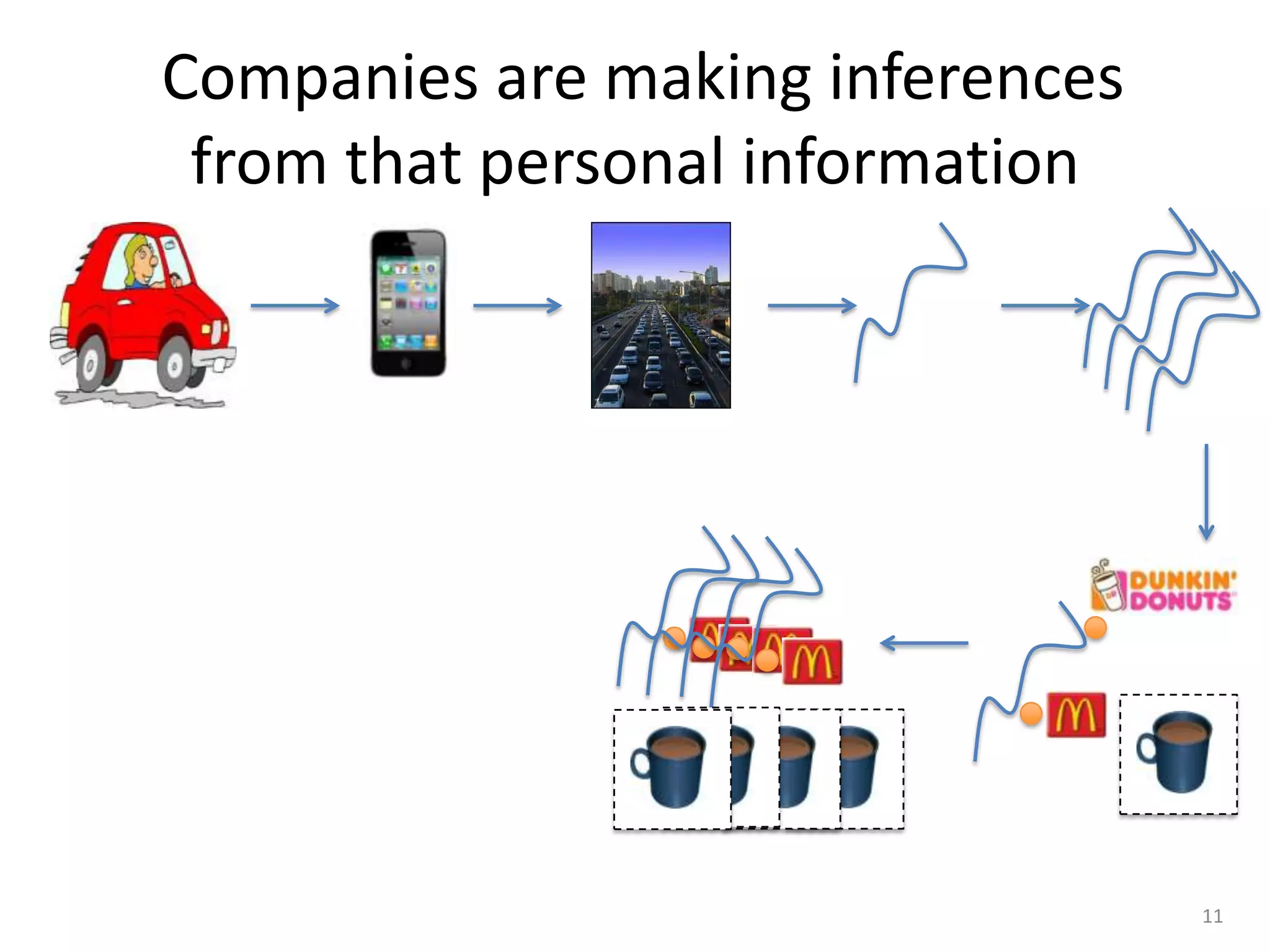
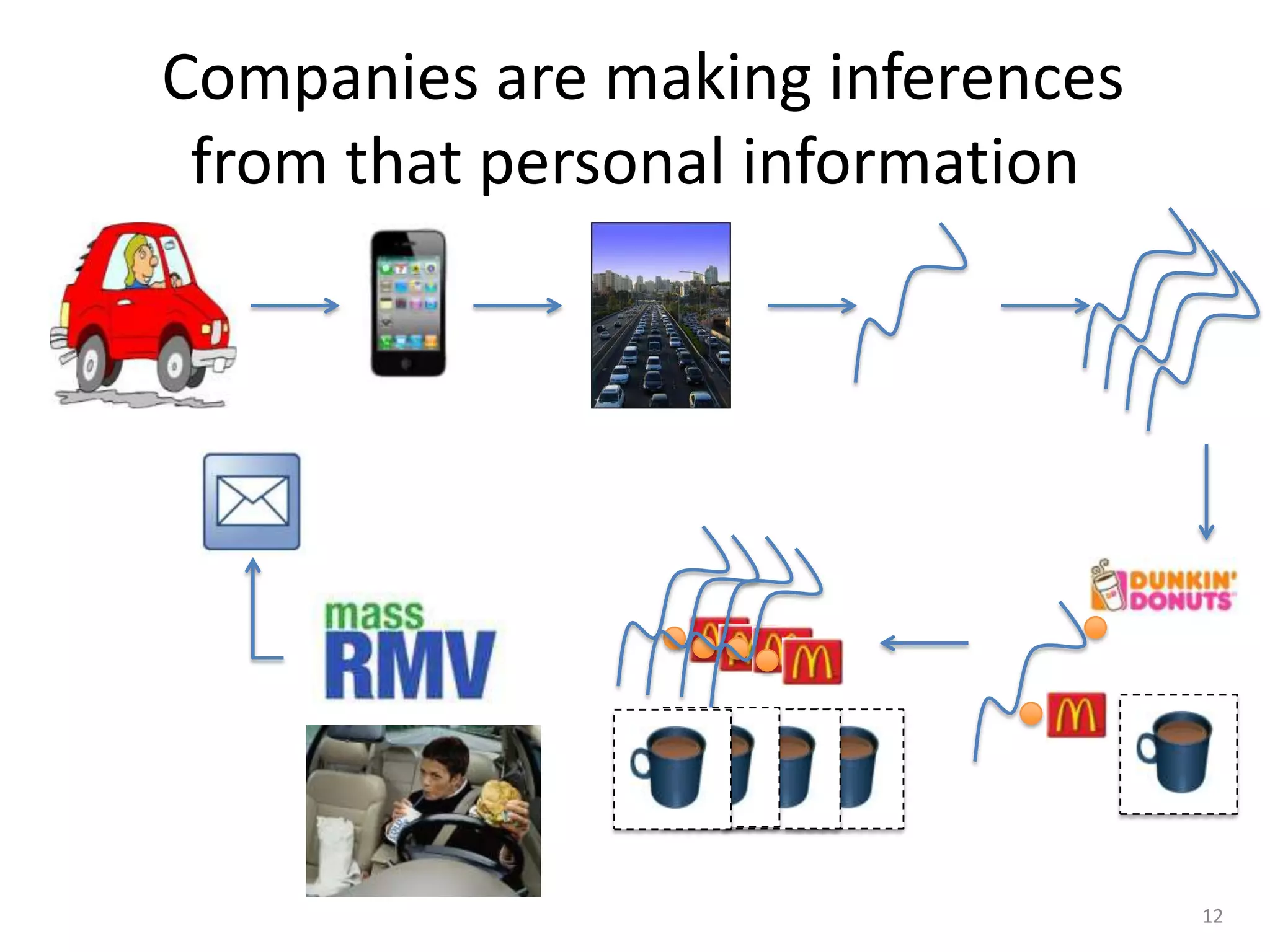
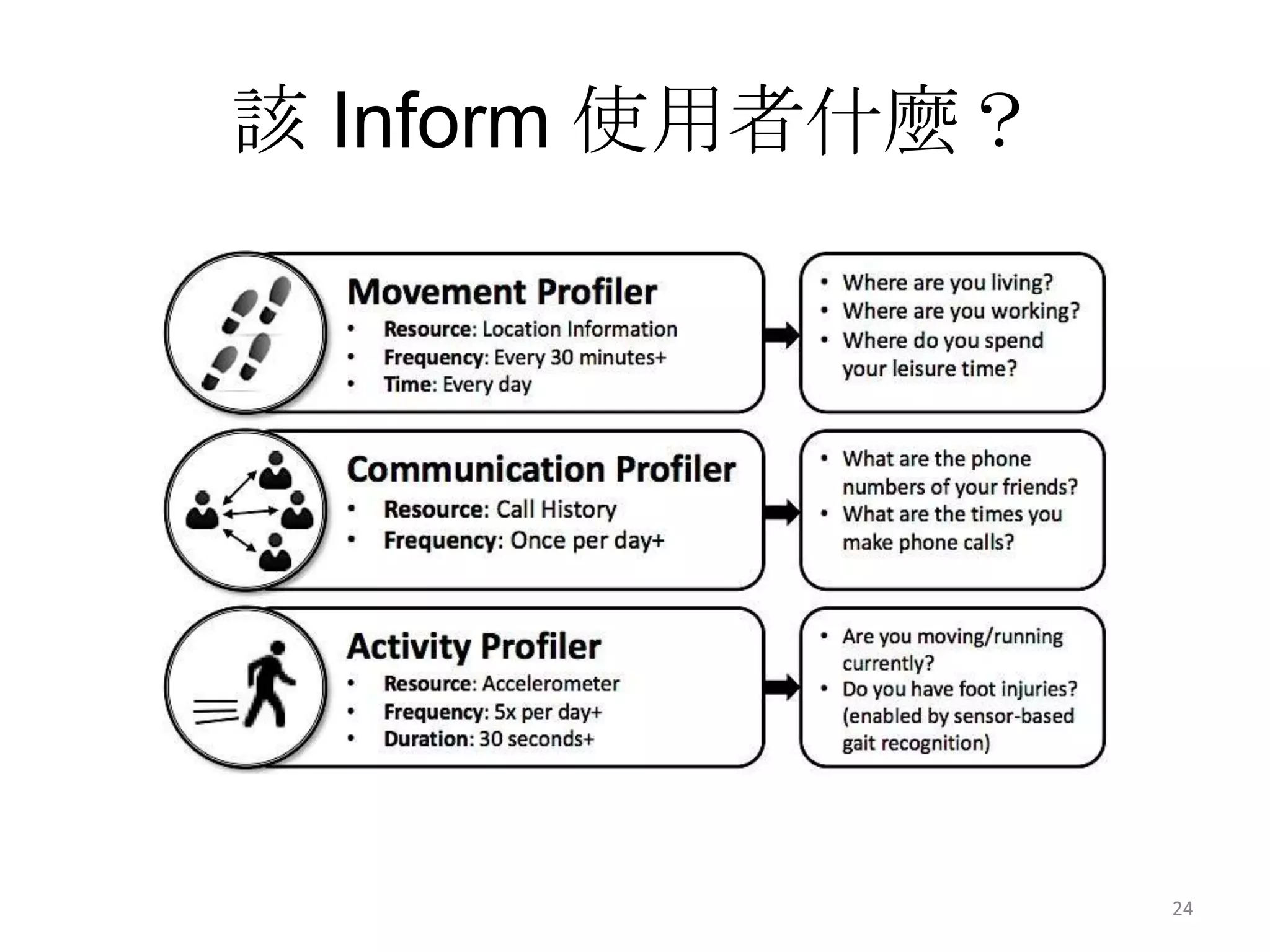
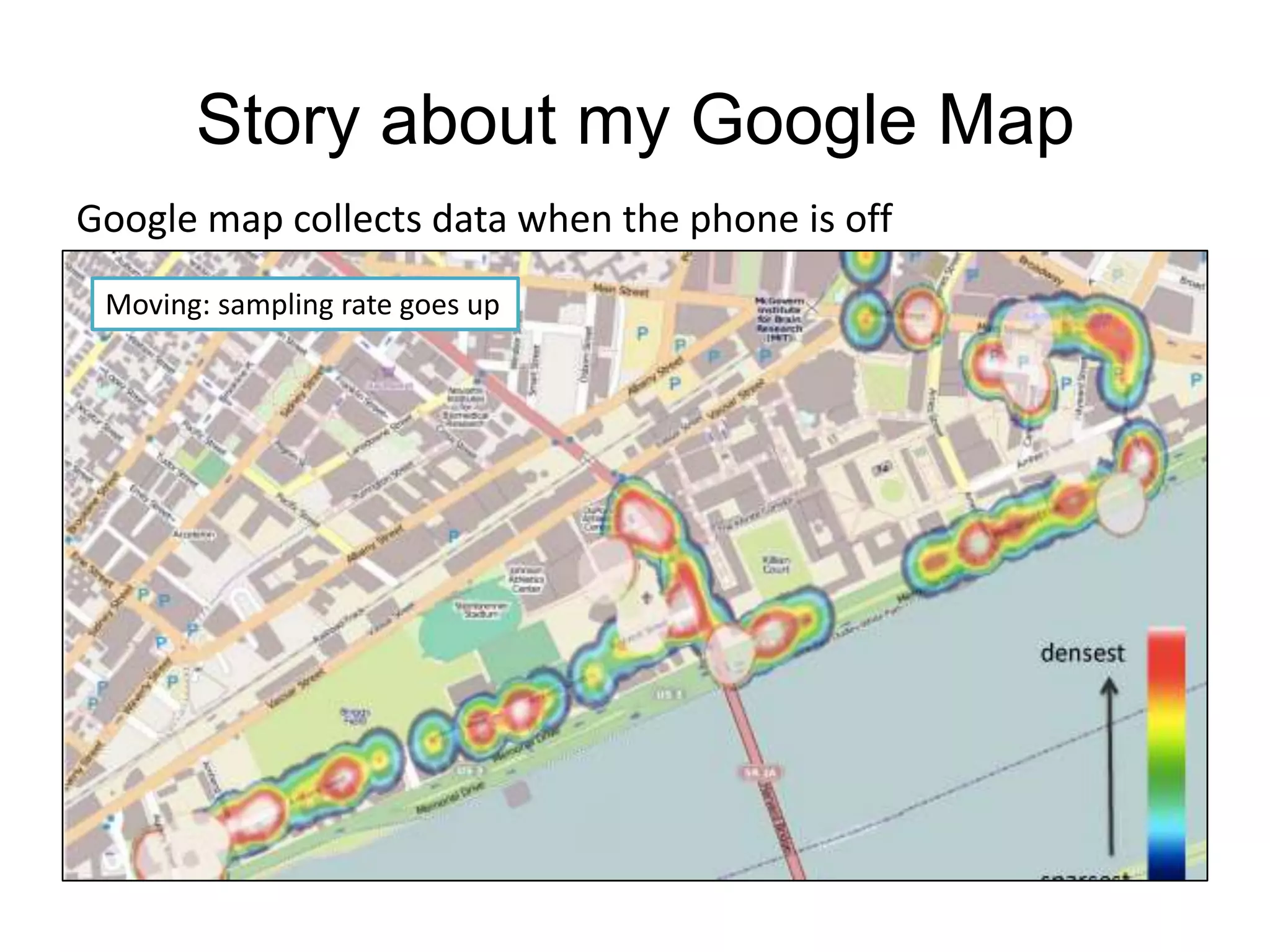
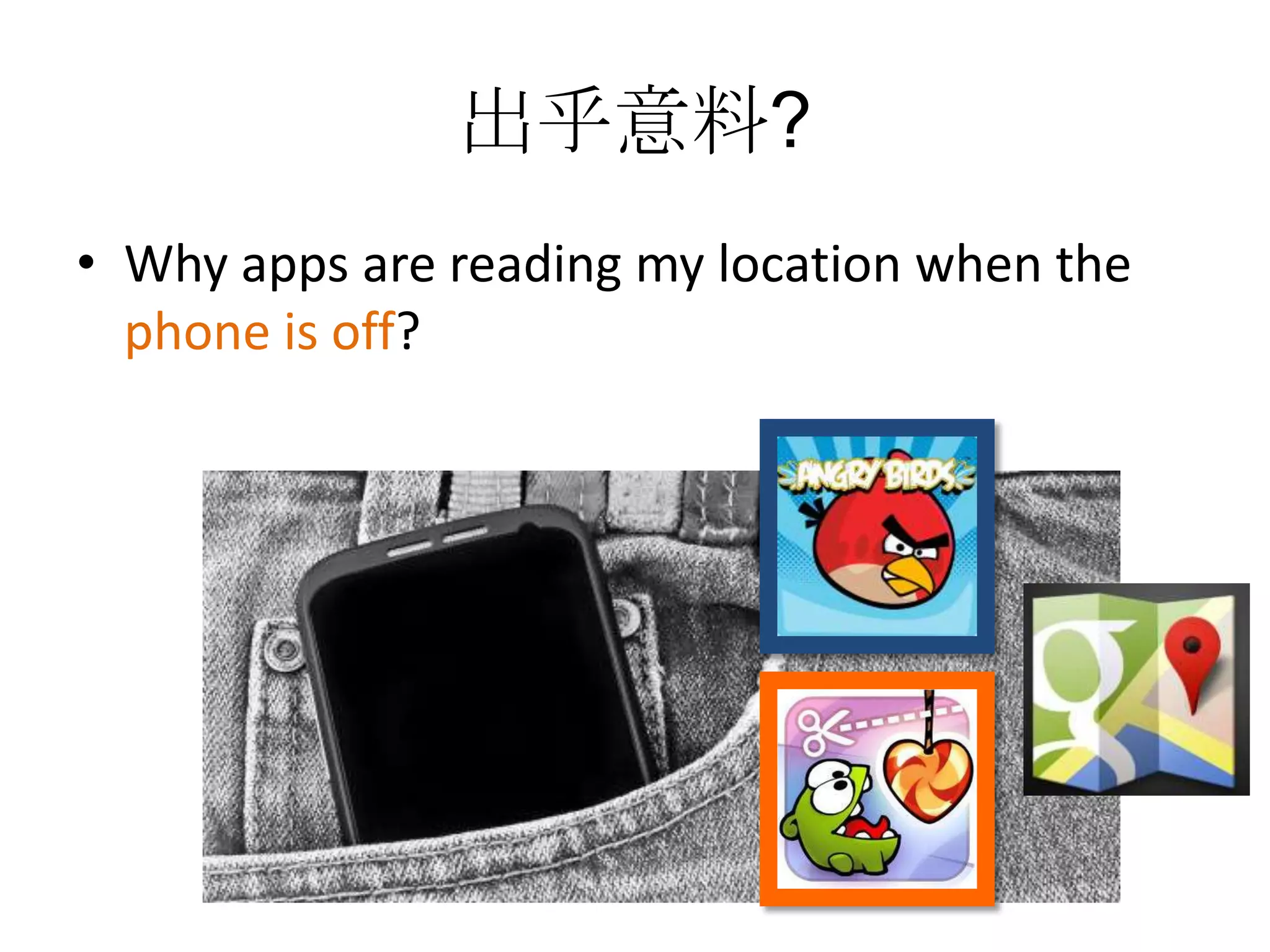
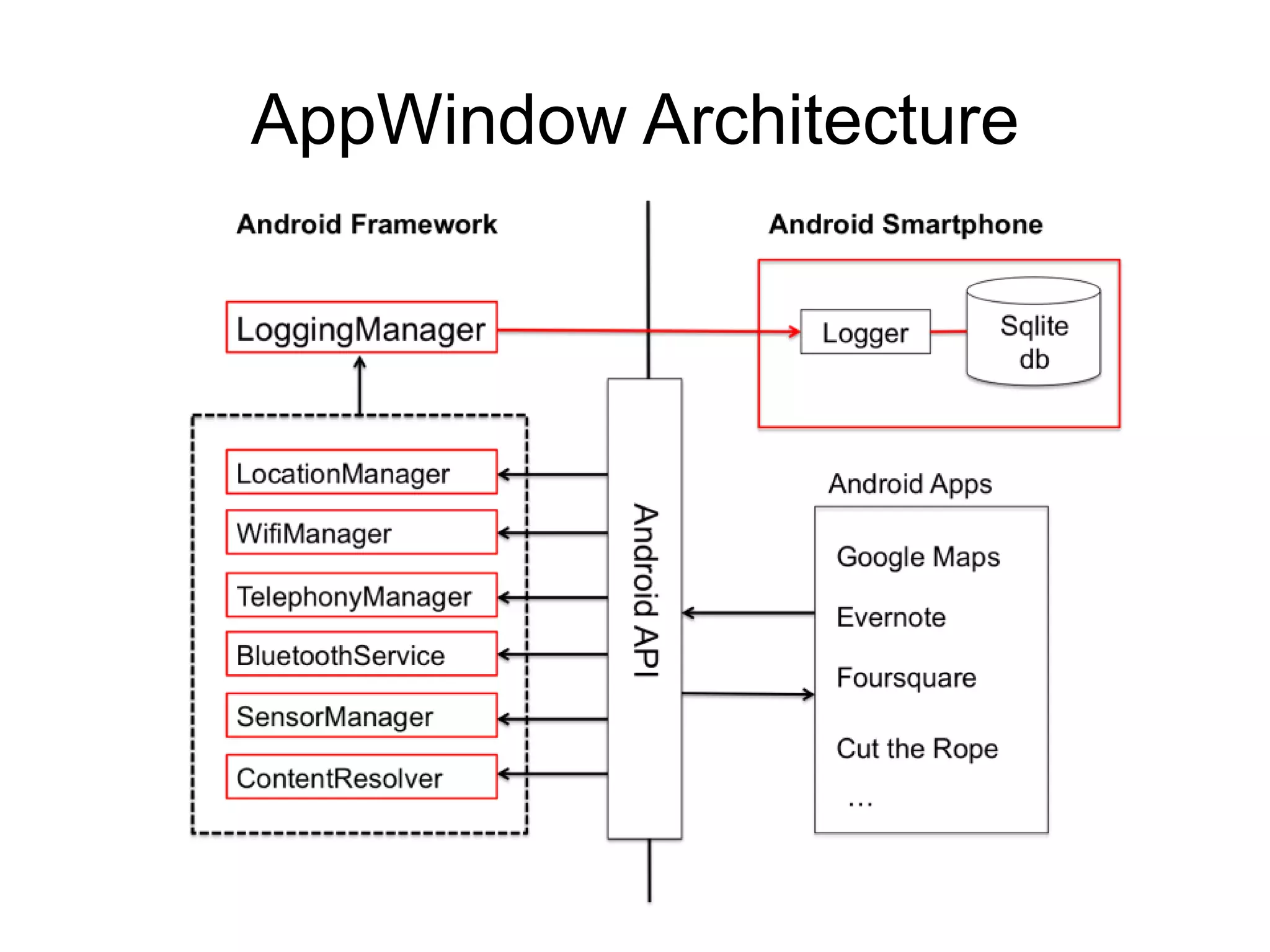
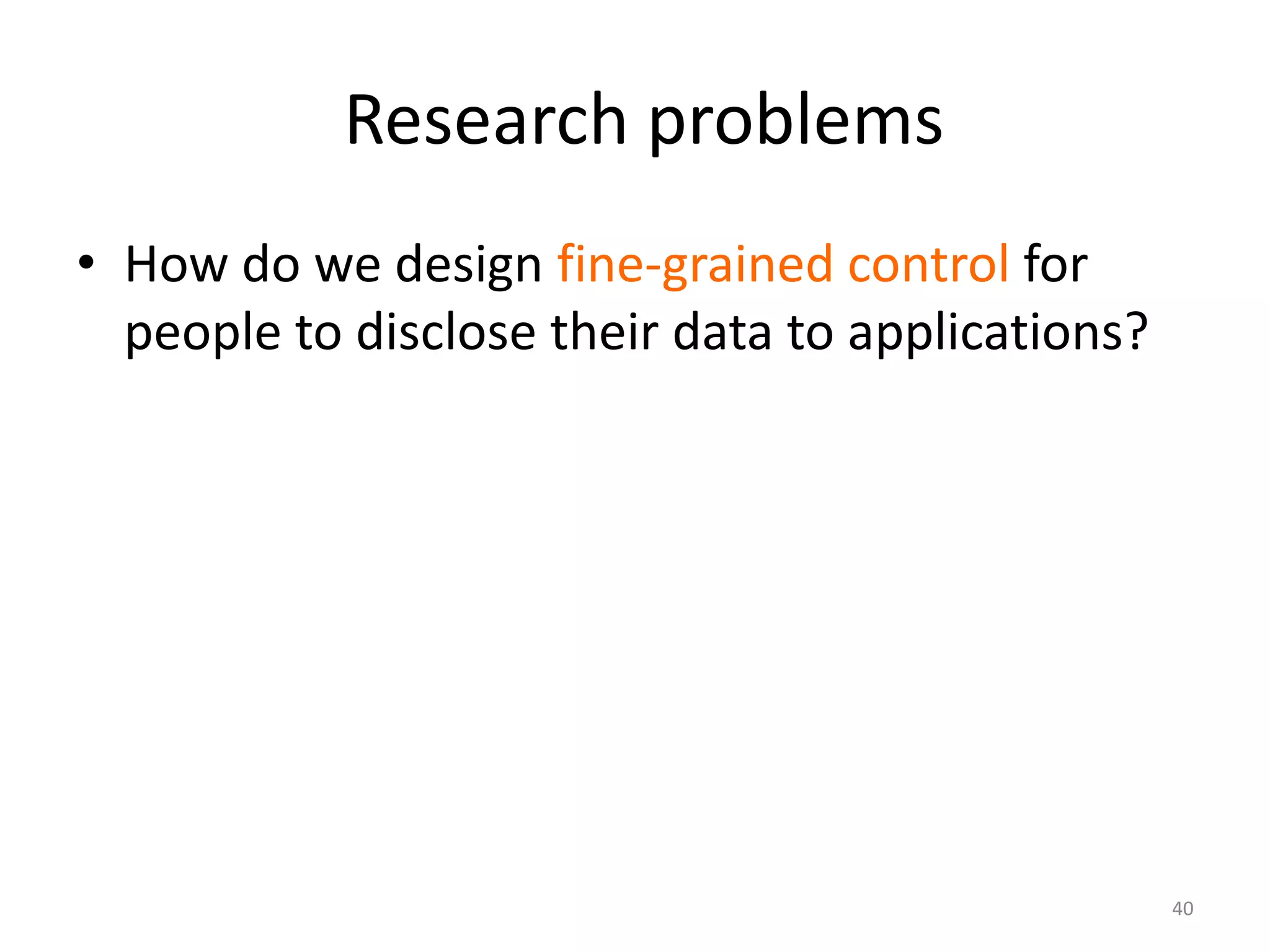
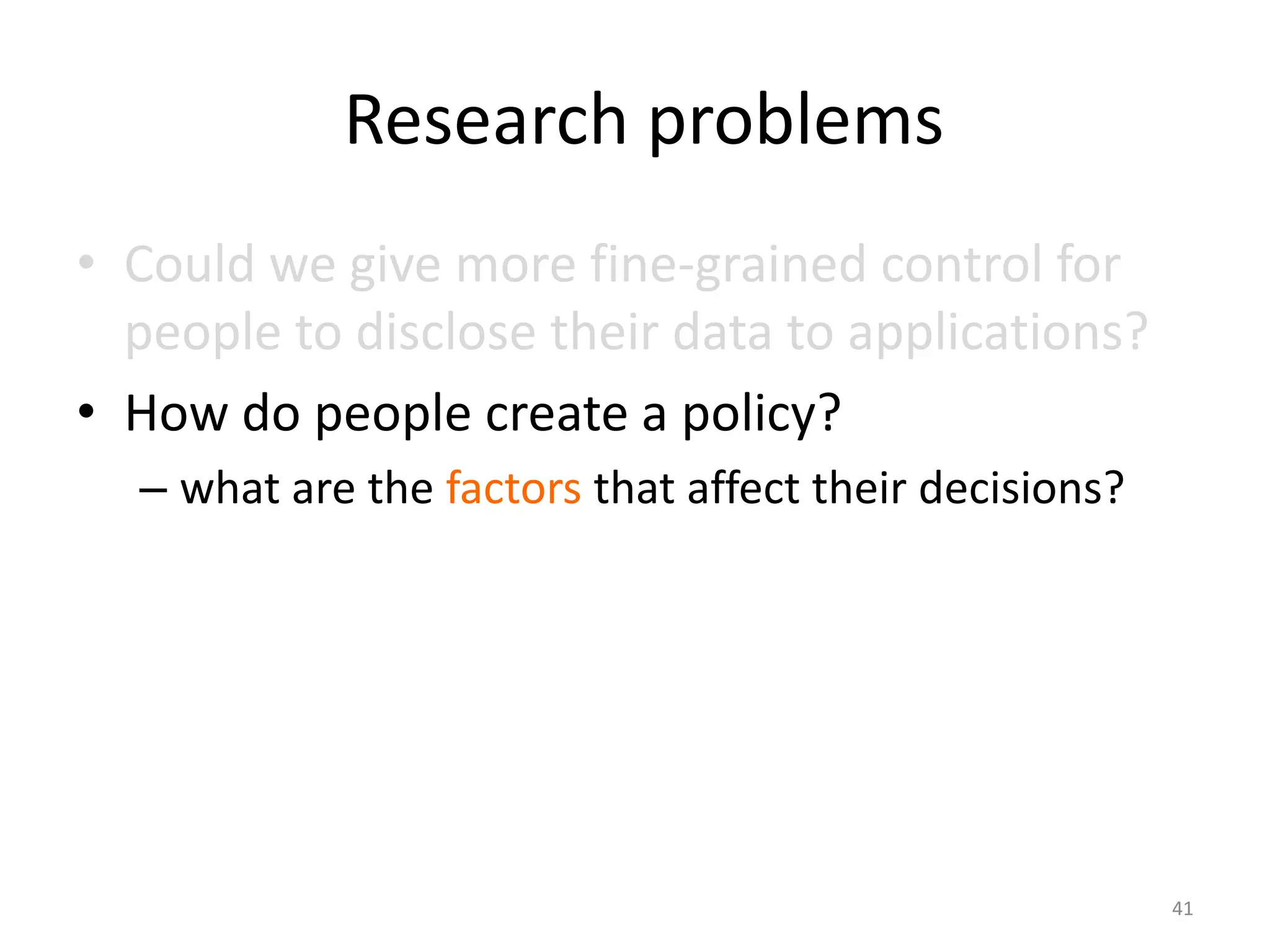
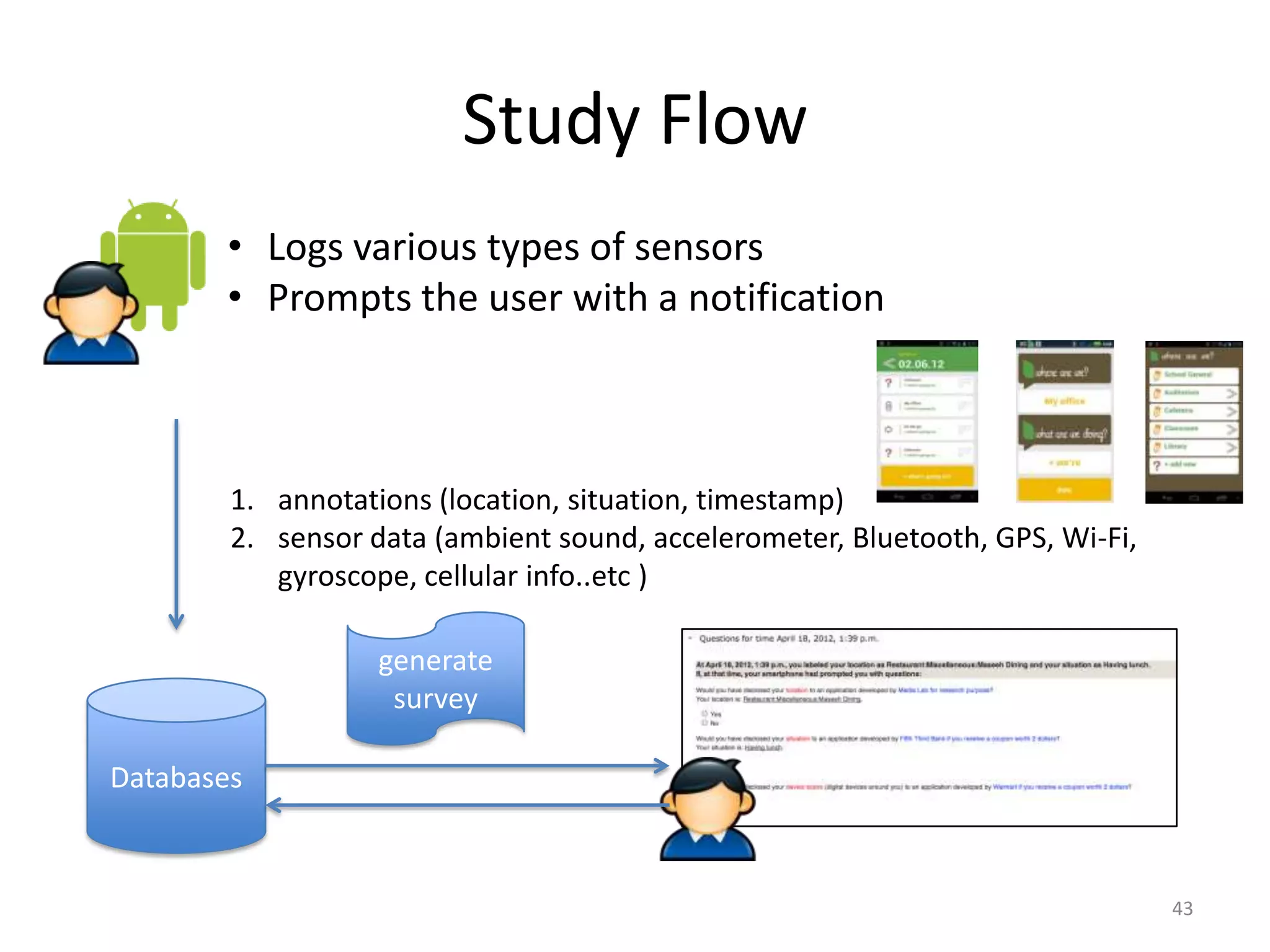
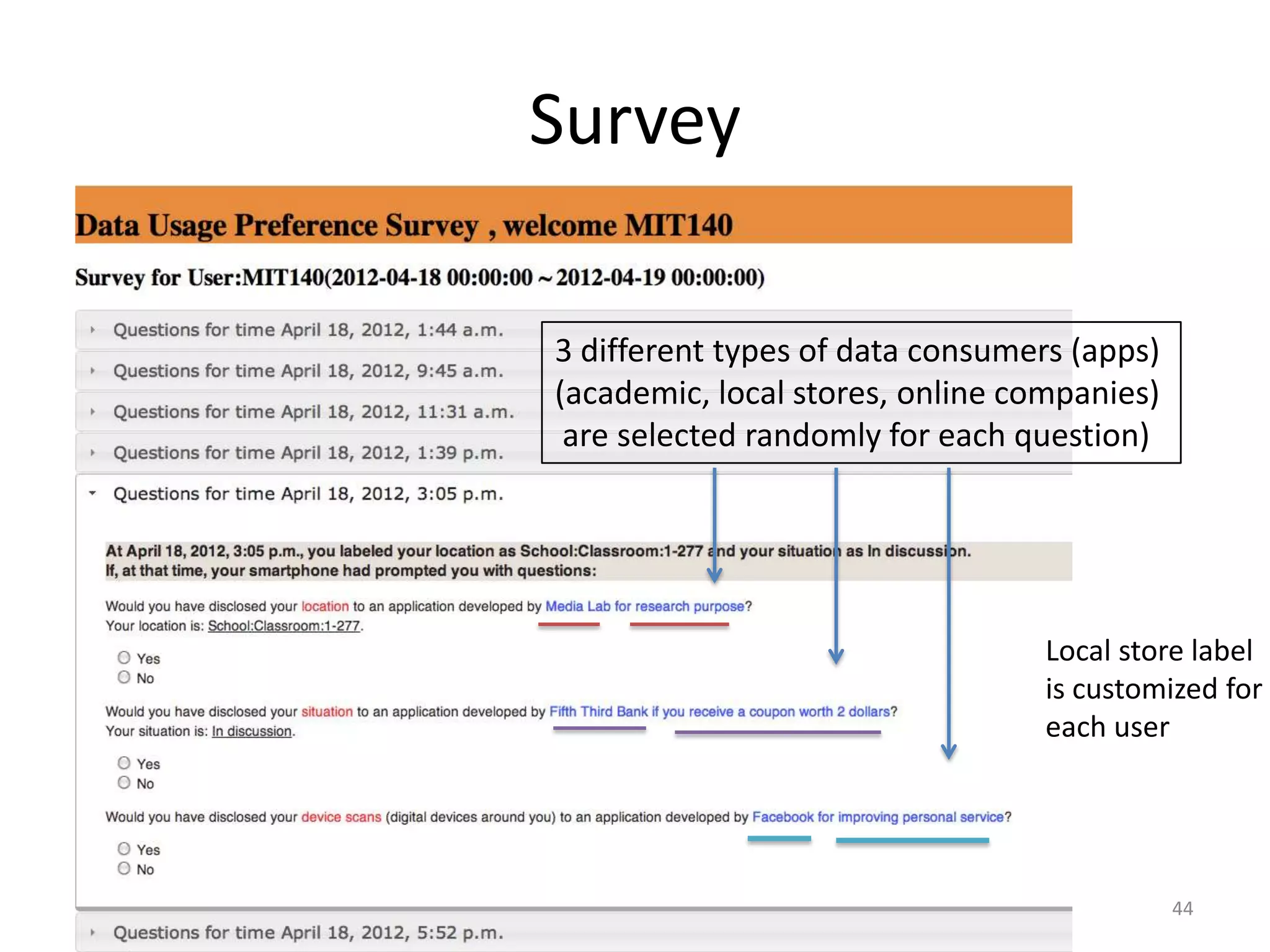
1) The document discusses privacy challenges posed by personal data and big data, focusing on data collected from smartphones.
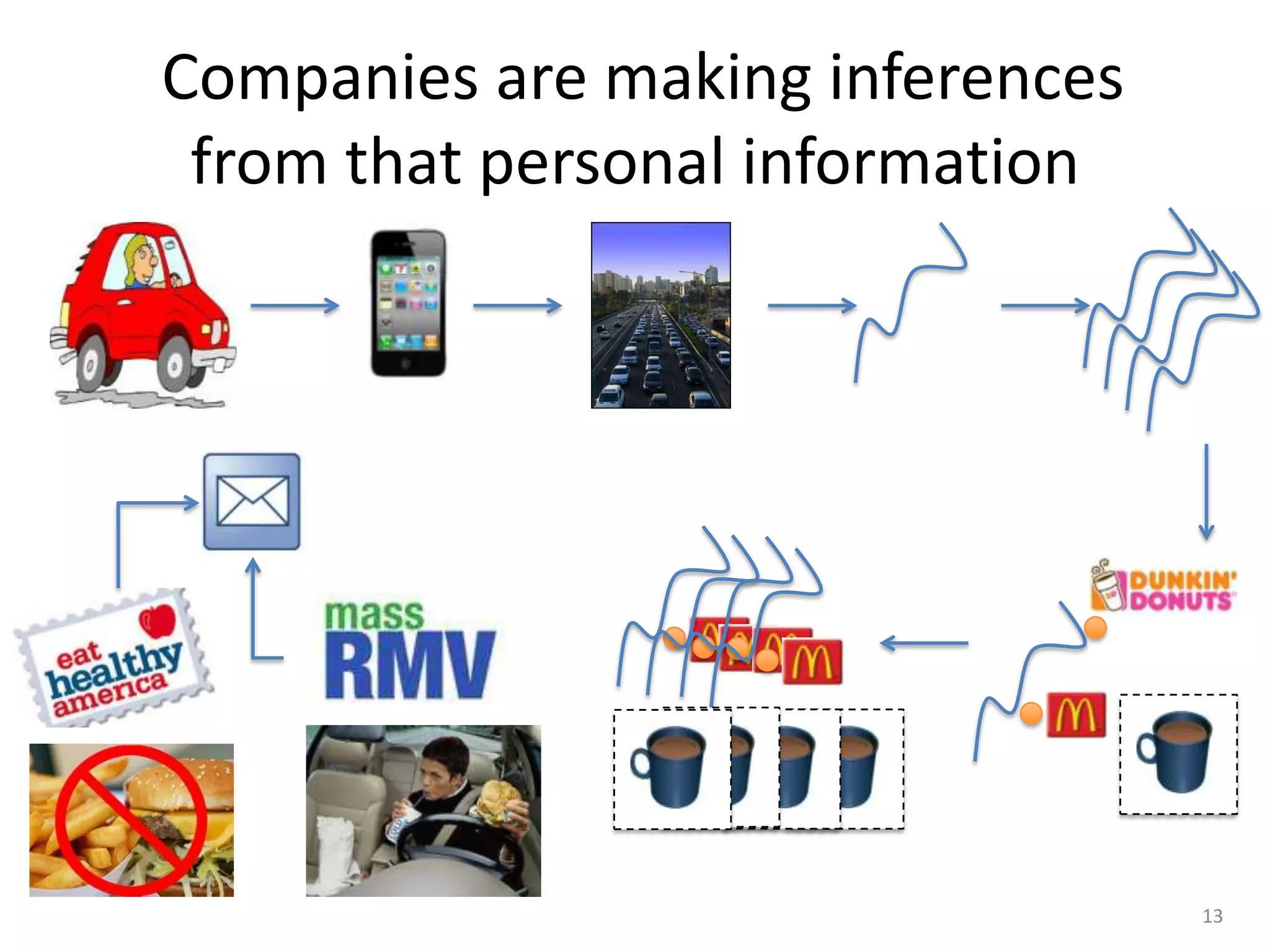
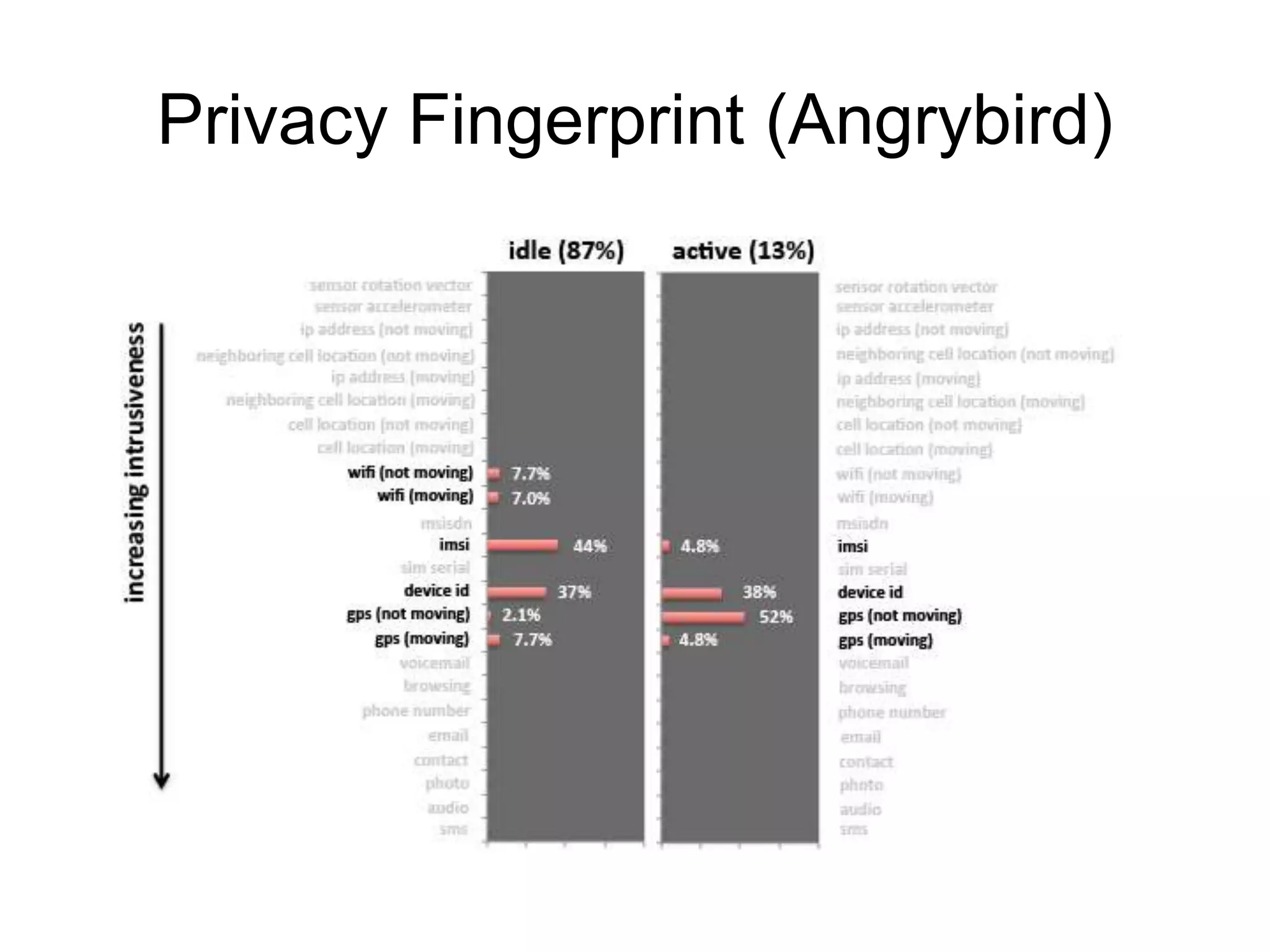
2) It notes that big data analysis is not always beneficial and can result in incorrect or harmful inferences being made about individuals from their data.
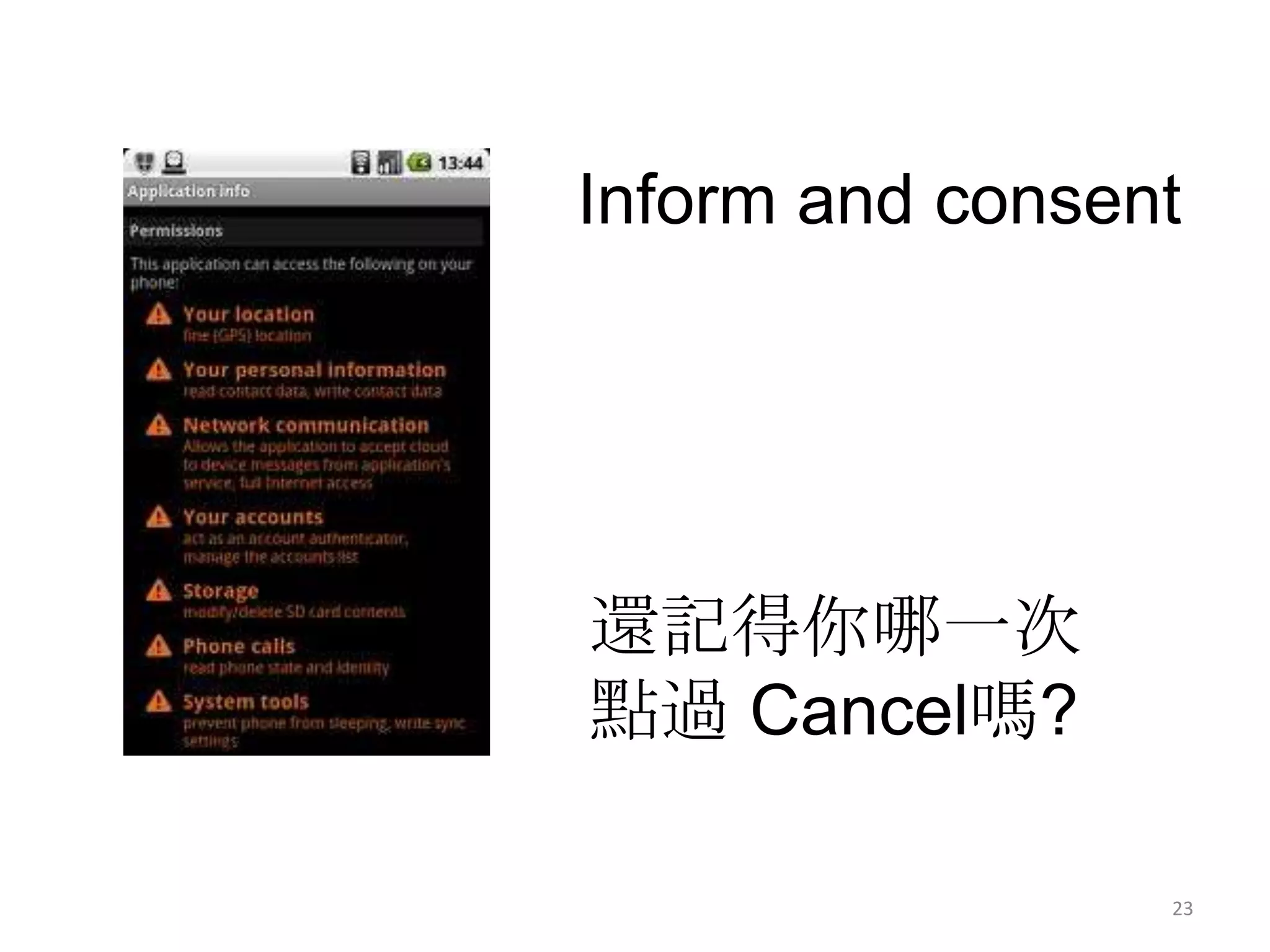
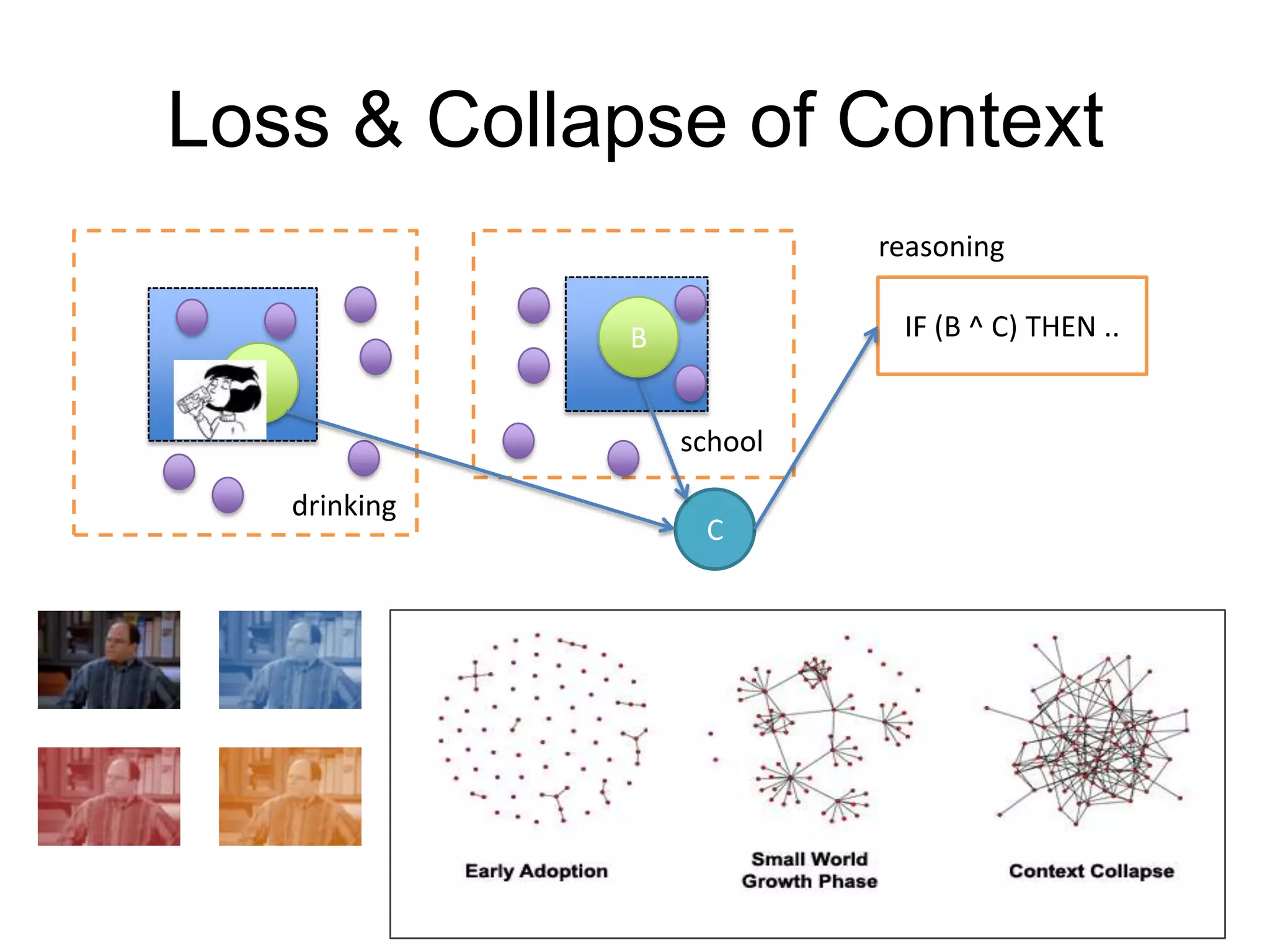
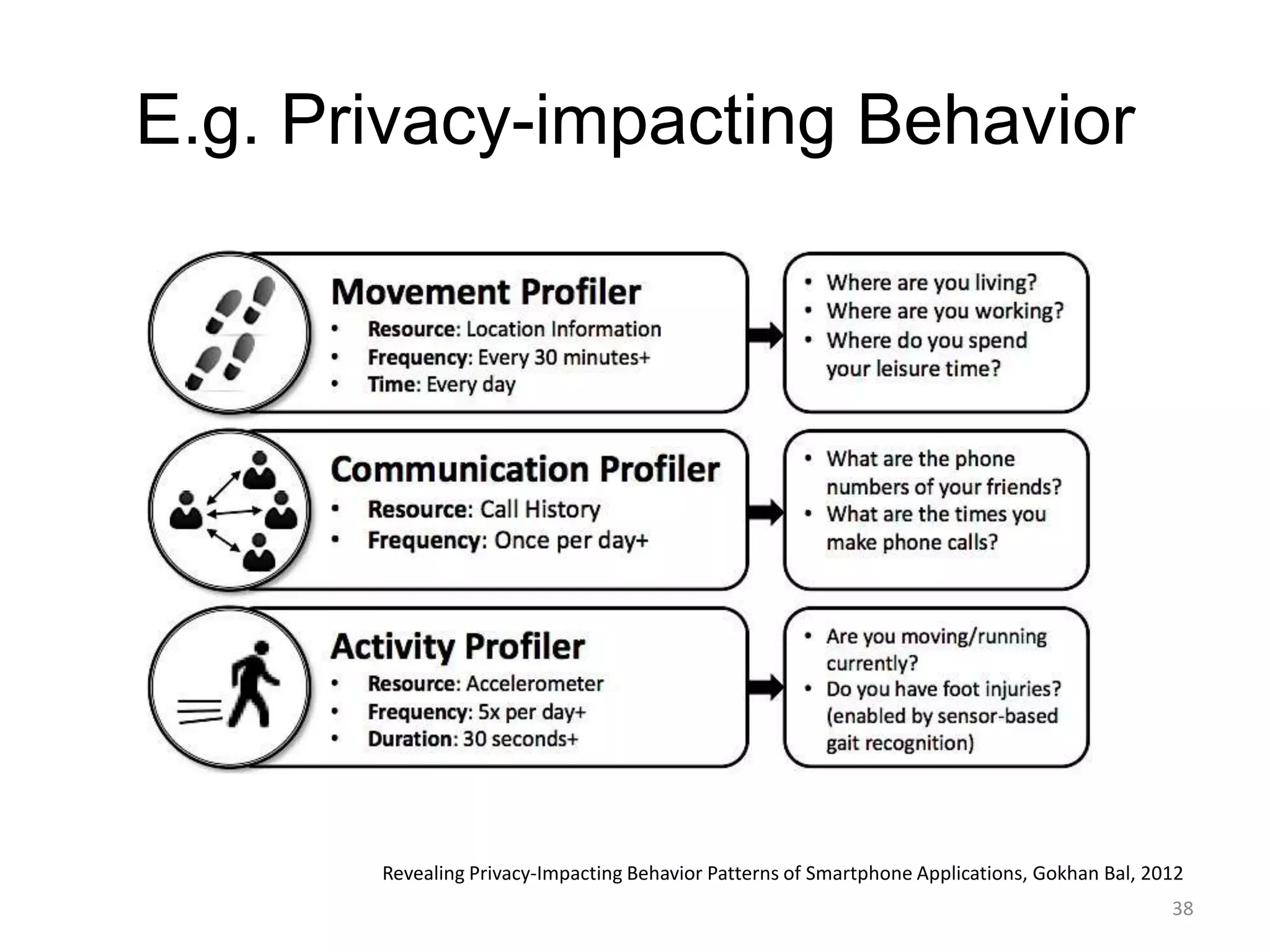
3) The document argues that privacy considerations need to be built into the design of platforms and systems from the start to help users maintain control over their data and context.






















![Recall context then respond
• Without interrupting the user to think about
*privacy* questions at the moment, we help
the user to reconstruct his situation context
later
So I was talking to
my colleagues this
morning in my
office, this app asked
for my location Yes
No
[*policy*] I don’t
want my locations
in work be disclosed
to any app
45](https://image.slidesharecdn.com/itriicl0116distribute-130126130402-phpapp02/75/Itri-icl-0116_distribute-45-2048.jpg)