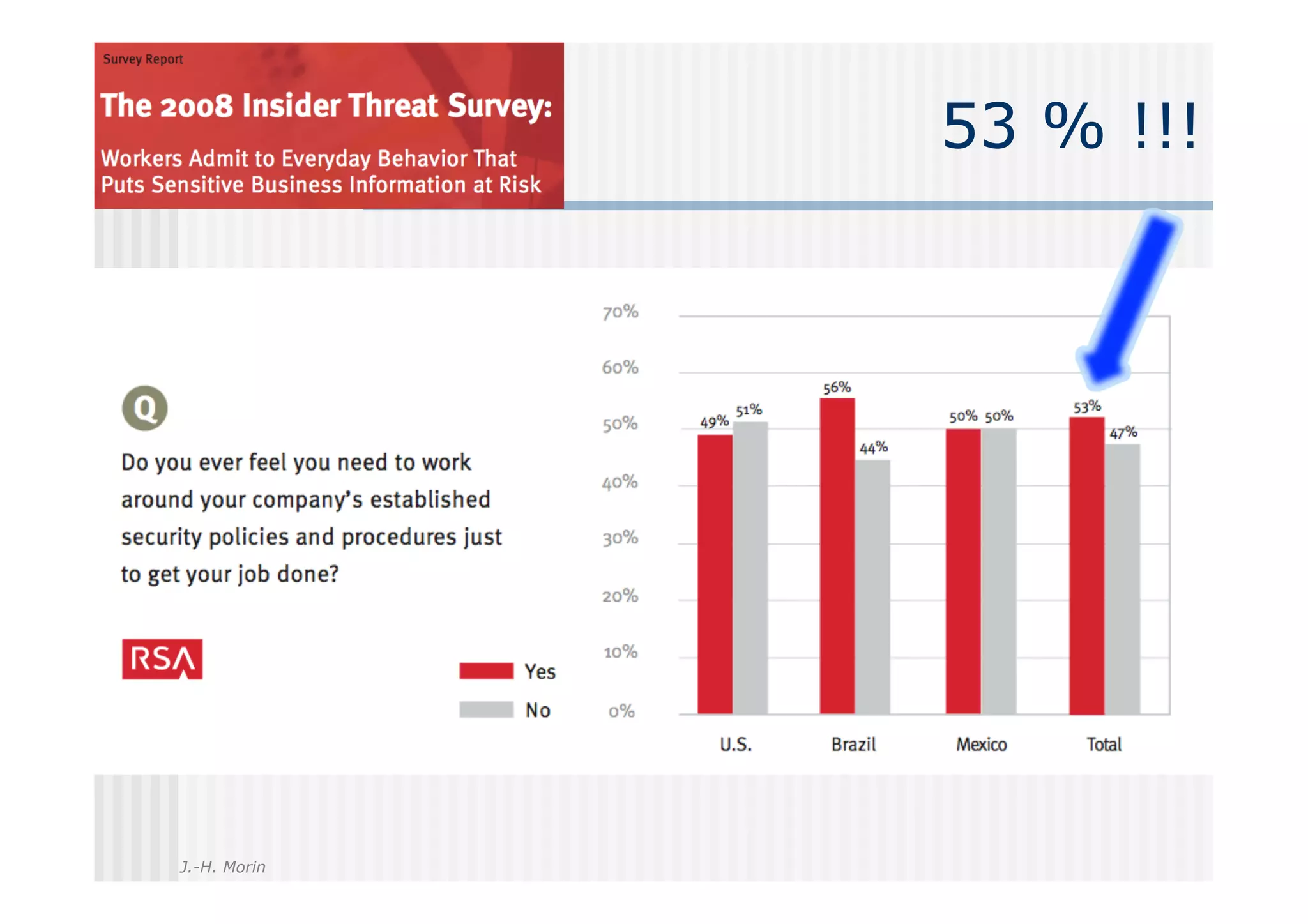
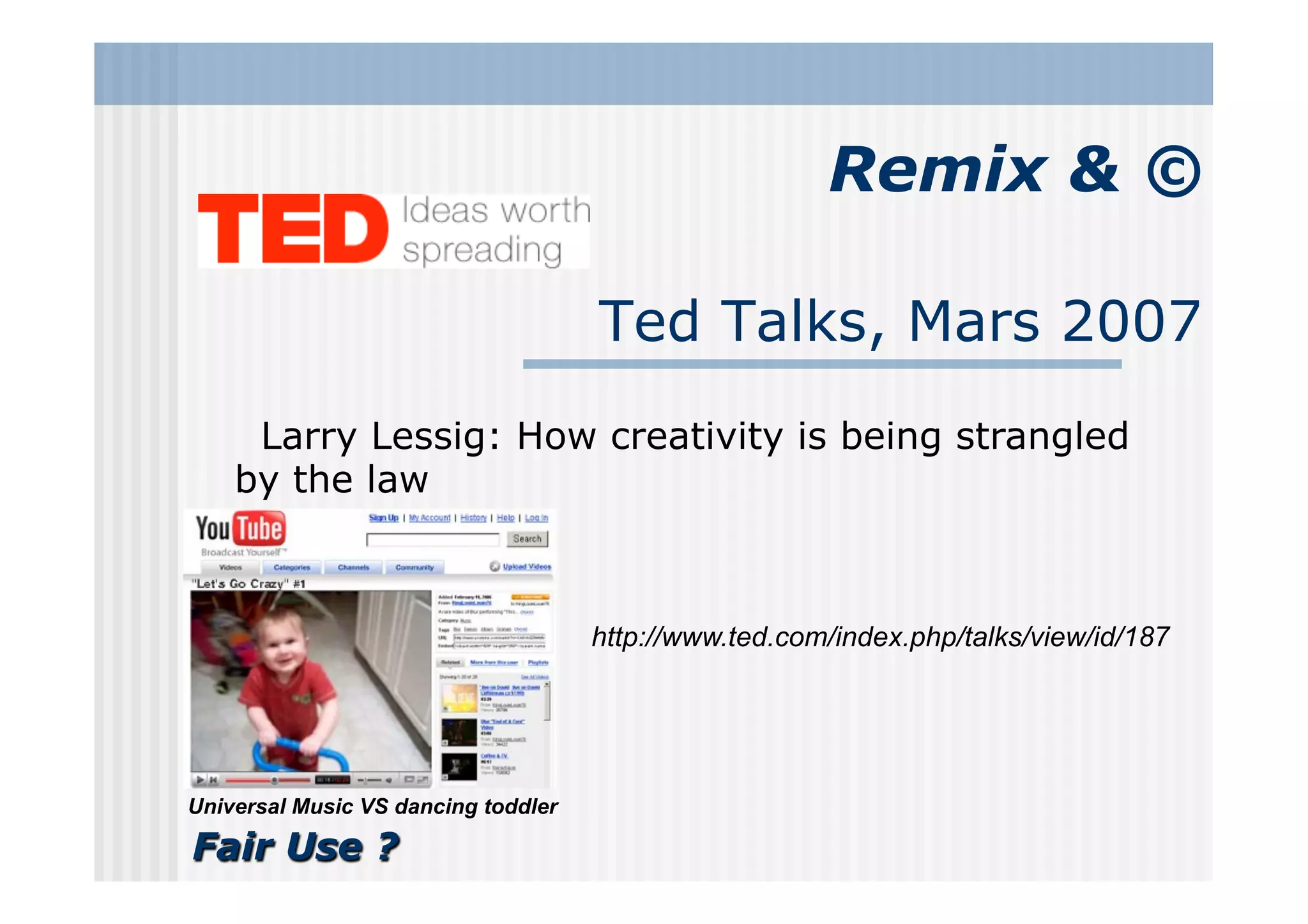
The document discusses digital responsibility and trust issues in the digital age, highlighting three main contexts: the corporate sector, entertainment and media, and cloud computing. It emphasizes the need for a paradigm shift towards user trust, rather than distrust, in information management, and calls for socially responsible management of personal information within social networks. The author posits that digital literacy and participation are essential for shaping a sustainable digital society.