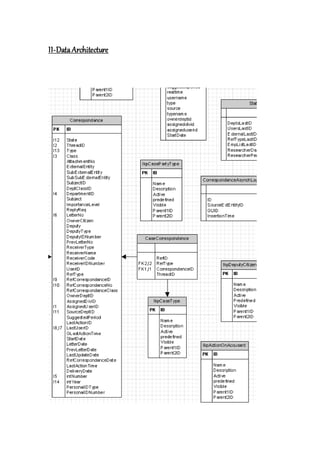
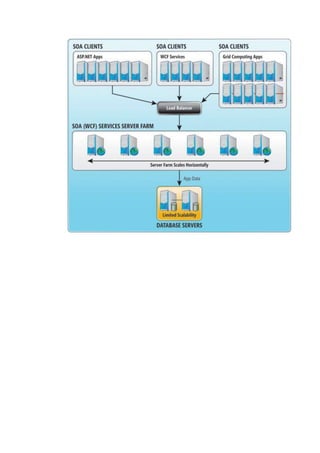
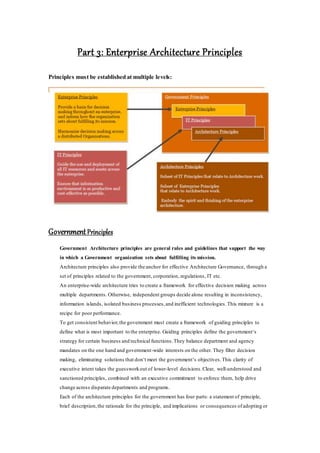
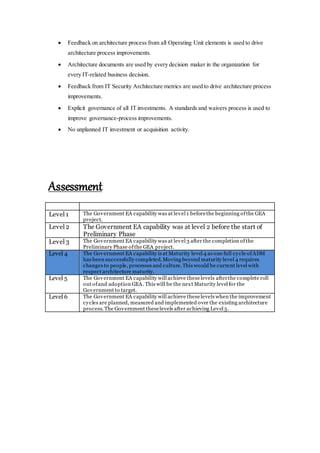
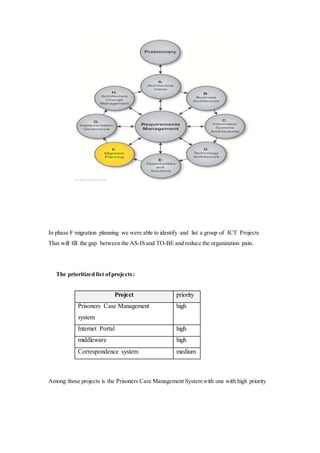
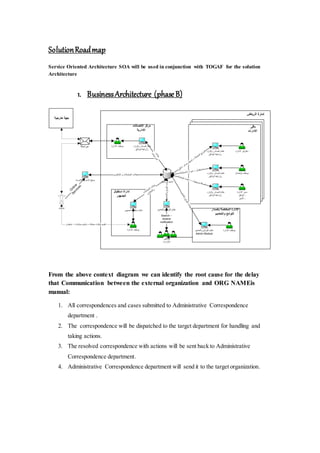
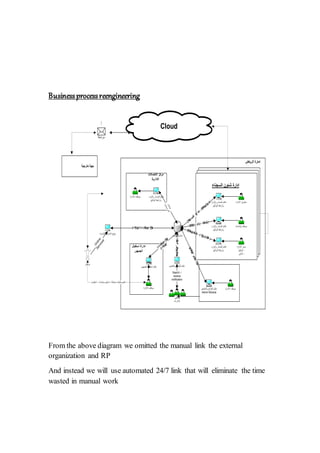
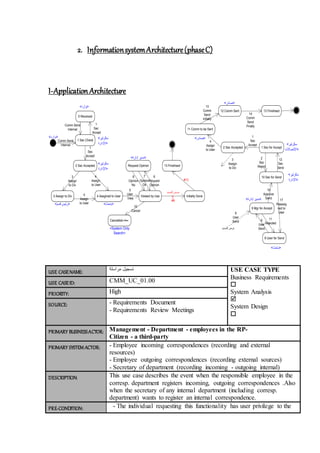
This document outlines an enterprise architecture master plan for a government organization. It includes an 8-phase architecture development method to guide the creation of the enterprise architecture. It also establishes several architecture principles for the business, data, application, and technical architectures. Finally, it assesses the organization's current enterprise architecture capability as a Level 3, with the goals of advancing to Level 4 upon completing the architecture development phases and eventually reaching Level 6 with continuous improvements.

















![backend system – As Employee of Etsalat Edarayah, Wared Employee
for registering Incoming Correspondence, Sader Employee for
registering Outgoing Correspondence, or Department Secretary for
registering Internal Correspondence.
- The privilege of the user is for the Correspondence Type assigned to
him by the admin.
- The user has logged in to the system (Correspondences Module).
TRIGGER: This use case is initiated when the user selects the option (link) to add
(register) correspondence.
TYPICALCOURSE
OF EVENTS:
Actor Action / System Response
Step 1:Create New Correspondence .
The user requests the option to add (register) new Correspondence.
oThe system responds by displaying the Correspondence form.
oThe user selects whether the correspondence is “,”وارد “,”صادر or
“داخلي .”صادر
oThe system responds by displaying the required attributes for each
option. [ِStep1, Alt1-Step1, Alt2-Step1 describe the three options
respectively].
oThe user enters the following fields:
- المراسلة نوع : cantake one of these values:
“ حكومية معامالت–أشخاص من عرائض–سري–برقية–الخاص المكتب
(األم)ير-الجمهور (استقبال الخاص المكتب ”
[Mandatory][Each group of users of the department is
responsible to handle only one type, and so this field will be
filled automatically by the system ]
- :رقمالمراسة Generated serial per each type “المراسلة نوع :”and per
each year “هجرية ”سنة [Mandatory]
- :رقمالخطاب Sender’s Issuing Number [Mandatory]
- تاريخ :الخطاب Sender’s Issuing Number [Mandatory]
- اردوال صفـة : [Mandatory][Default: “]”جديد
- عالموضو تصنيف :[List of specified to the department –
Subject Lockup Table ]
- المشفوعات :عدد [Mandatory]
- األهمية مستوى : "عاجل-"عادي
- رد؟ تتطلب : Check box
- المعاملة حالة :Set to the default value “االجراء ”تحت
Step 2: Define the Destination
oThe user requests to set the destination “إليها المرسل .”الجهة
[Mandatory]
oThe system responds by listing the hierarchy of departments, units
and employees.
oThe employee selects one of these items.
Step 3: Define the Source
oThe user requests to set the source “ الجهةالراسلة ”. [Mandatory]
oThe system responds by listing the available “external entities” in the
system (lock-up table) with ability to add new one to the list.
oThe user selects one of these items, or
- If the sender is a person or group of persons, the user enters the
name(s) in a free text.](https://image.slidesharecdn.com/togafproject-161013064826/85/Togaf-project-26-320.jpg)
![Step 3: Define the Related Individuals (Citizens)
oIf the subject (Case) is related to one person, or a group of persons,
the user requests to set the concerned persons “بـ .”متعلق [Option]
oThen, system displays (a form) with the following attributes for each
person:
- االسم [Mandatory]
- االإقامة / السجل رقم [Mandatory]
- عليه مدعي أم مدعي [Mandatory][Default=”مدعي ”]
Step 4: Add Attachment(s)
oThe user selects to attach documents.
oThe system responds by displaying the Attachments form.
oFor each document, the employee scan the document enters
attachment data by filling the following fields:
- الوثيقة رقم [Mandatory]
- اإلدخال تاريخ [Mandatory][Value=Current Date/Time]
- العنوان
- ملخص
- مالحظات
- الصفحات عدد [Mandatory]
- الدالة الكلمات [Editable List]
Step 5: Confirm sending the correspondence & saving the data
oThe user selects to save the information and forward (distribute) the
crosp. to the destination.
oThe system responds by validating the data and storing the data in the
system database.
oThe following Check (Status) Field “المراسلة ”أستلمتis set to False.
Step 6: Printing Inquiry Ticket “خارجي لوارد مراجعة ”تذكرة
oIn case of the “”,the user may request to print inquiry form.
oInvoke use case CMM_UC_08.00, Print Inquiry Ticket
ALTERNATE COURSES: Alt1-Step1: خارجي صادر
If the user selects correspondence type is “”صادرخارجي , the following
fields are changed:
- Destination will be: “ جهةاإلمارة داخل موظف ”. [Same as Step2]
- Source will be:”شخص أو خارجية .”جهة [Same as Step3]
- Both items: “الخطاب ”رقم and “ تاريخالخطاب ” will not exist.
- If to be send by mail [Optional], the following fields will be
enabled: “ البريد وزن–البريد تكلفة ” and the receipt will be scanned
and attached as a document.
- If the transaction is related to “أو أوالخاصة العامة بالحقوق خاصة قضايا
,”المتابعة the following fields are displayed:
- القضية عنو
- القضية رقم
- التحقيق جهة
- الضبط جهة
- المدعى
- عليه المدعى](https://image.slidesharecdn.com/togafproject-161013064826/85/Togaf-project-27-320.jpg)
![Alt2-Step1: صادرداخلي
If the user selects correspondence type is “”صادرخارجي , the following
fields are changed:
- Both the Destination & the Source will be: “ جهةاإلمارة داخل موظف ”.
- Both items will not exist: “الخطاب ”رقم and “الخطاب .”تاريخ
- If it is transaction transfer, invoke use case: CMM_UC_06.00,
معاملة إحالة
Alt2-Step1: إسابقة بمراسلة لحاق
- If the user selects “ صفةالوارد ” = “,”إلحاقي then the system allows
him to search for existing record of “.“وارد
- if the type = “,”صادر then the system allows him to search for
existing record of “.“صادر
Alt2-Step1: جوابمراسلةسابقة
- If the user selects “ صفةالوارد ” = “,”جوابي then the system allows
him to search for existing record of “.“صادر
- The system responds by related the 2 items and uncheck “ تحتاج
”لرد [set to False].
- Similarly, and if the type = “,”صادر then the system allows him to
search for existing record of “.“وارد
Alt1-Step1: Modify existing correspondence
The user search for existing record to modify data. This will be allowed
whenever the status of receiving correspondence by the destination
“المراسلة .”أستلمت
Alt2-Step1: Delete existing correspondence
The user search for existing record to Delete the entire record. . This
will be allowed whenever the status of receiving correspondence by the
destination “المراسلة .”أستلمت
Alt1-Step5: Invalid Data
If any mandatory field is missing the system will not allow the saving
operation to complete and will generate an error message with the
missing fields’ titles. The system will also validate the remaining fields
for their size and structure.
CONCLUSION: This use case concludes when the user receives a confirmation of
registering the correspondence.
POST-CONDITION: The correspondence has been recorded; related documents have been
archived, and released to the destination.
BUSINESS RULES
IMPLEMENTATION
CONTRAINTSAND
SPECIFICATIONS
ختم بطباعة النظام يقوم خارجى صادر / وارد خطاب كل علىStamp 1-أعلى يتم
: على ويحتوى يسار األولى الصفحة
الوارد / الصادر رقم-التاريخ-المشفوعات عدد
.Bar Code البحث عملية لتسهيل التاريخ و بالرقم
يتـم أو الصفحة يمين اسفل على الختم نفس طباعة يتم الداخلى الوارد حالة فى -2
أولى صحـفة استخدام
Cover page -. المعاملة مع ارشفتها مع المعلومات تلك على تحتوى
3-معاملة وجود حالة فىلنفس و الشخص لنفس النوع نفس من "اإلجراء "تحت
القضيةبتن النظام يقوم ، الموضوعا اتخاذ فى الحرية اعطاؤه مع المستخدم بيهأما لقرار
. بها السماح أو الجديدة المعاملة برفض](https://image.slidesharecdn.com/togafproject-161013064826/85/Togaf-project-28-320.jpg)