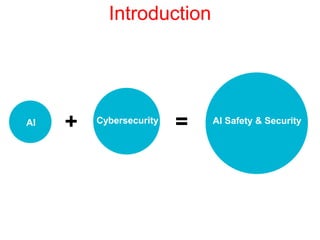
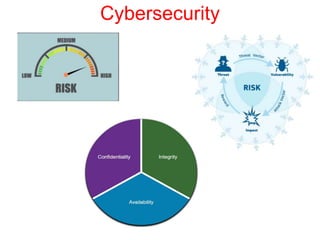
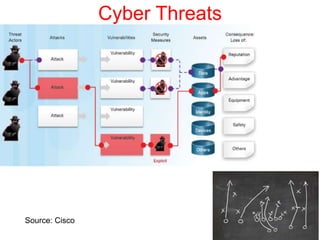
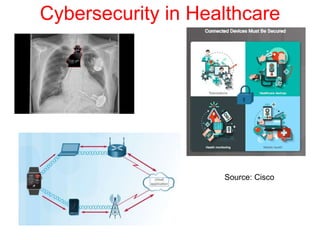
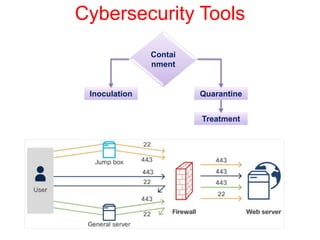
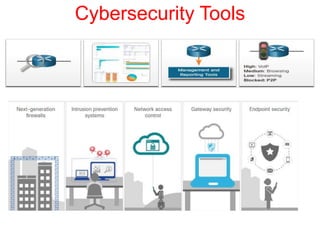
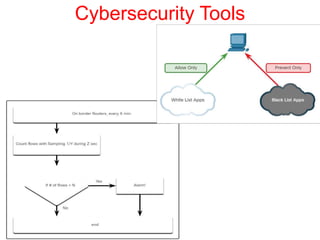
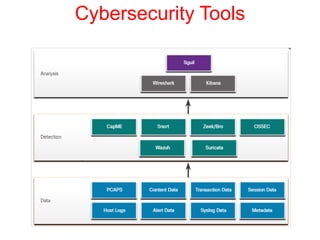
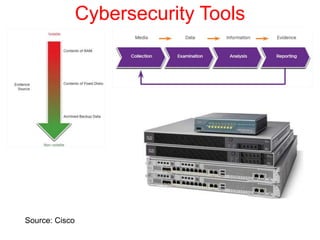
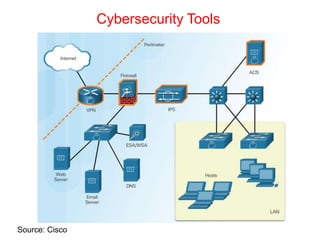
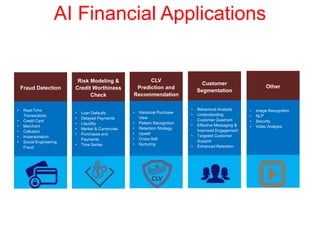
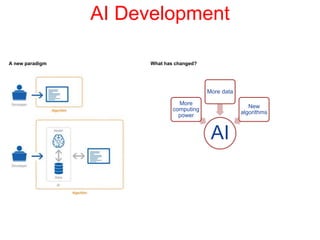
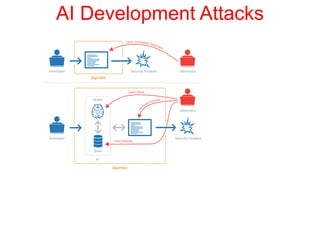
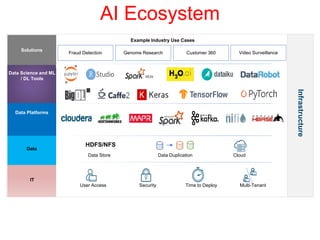
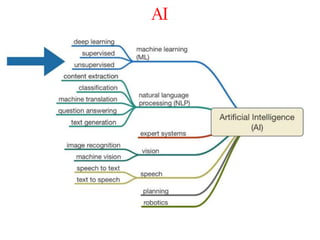
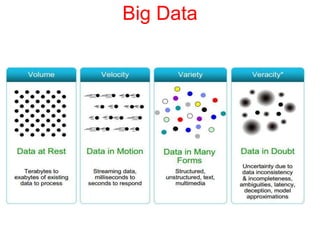
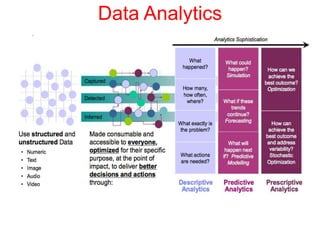
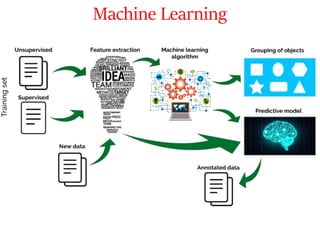
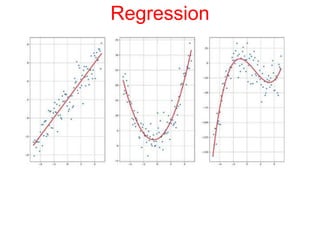
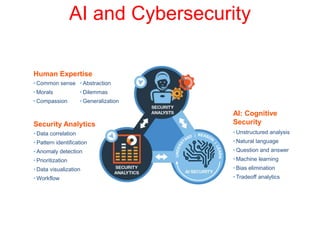
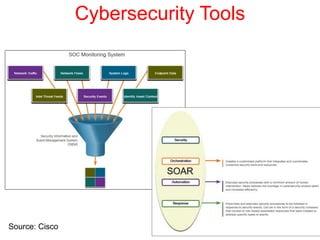
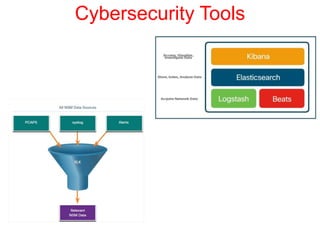
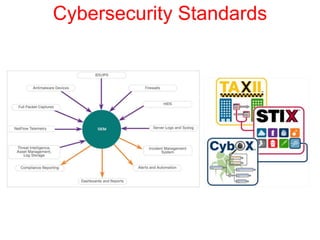
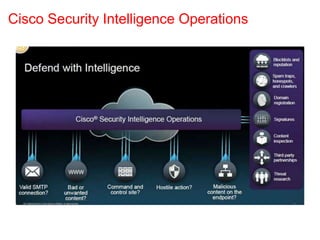
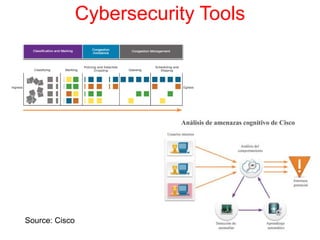
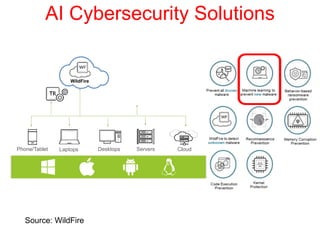
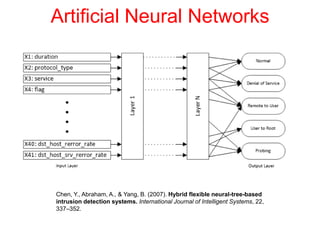
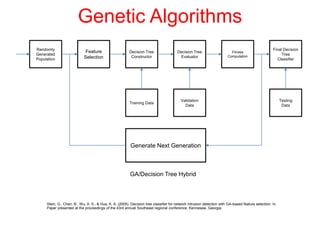
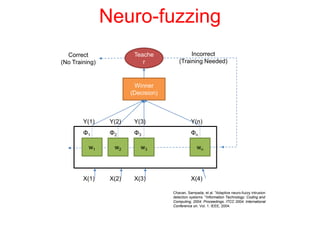
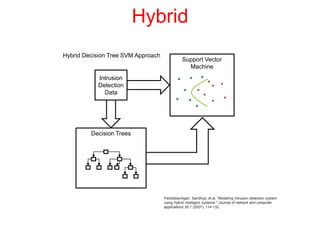
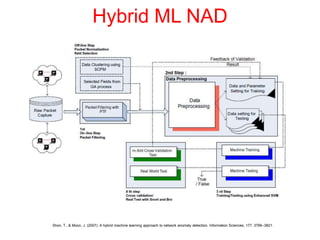
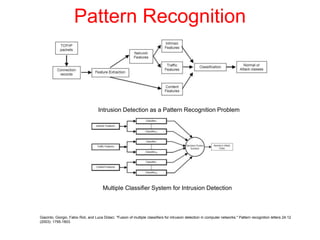
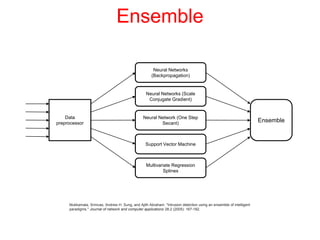
This document discusses the application of artificial intelligence techniques in cybersecurity. It begins by outlining the motivations for applying AI to cybersecurity, such as the growing amounts of data and connections between devices. It then provides an overview of cybersecurity challenges and common AI techniques like machine learning. The document concludes by presenting several examples of how AI is already being used to enhance cybersecurity, such as through anomaly detection, natural language processing for unstructured threat analysis, and AI-powered security analytics tools.