The document presents the Vellvm project, which focuses on verifying LLVM intermediate representation (IR) through formal methods and its implementation in Coq. It discusses various techniques for enhancing software reliability, safety, and correctness, highlighting the success of the CompCert C compiler in producing reliable optimizations that resist common bugs found in other compilers. The presentation details LLVM’s operational semantics, the need for high assurance software, and the integration of verification into compiler infrastructure.





![The Coq InteracGve Theorem Prover
• Based on dependent type theory
• Pure funcGonal language + datatypes
• ConstrucGve proofs ⇒ executable code
• AutomaGon: tacGcs + inference
⇒ formalizaGon tool of choice for DeepSpec team
[Developed at INRIA]](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-6-320.jpg)



![LLVM Compiler Infrastructure
LLVM
Front
Ends
Code
Gen/Jit
OpGmizaGons/
TransformaGons
Typed SSA
IR
Analysis
[LaLner et al. ]](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-10-320.jpg)
![MoGvaGon: So[Bound/CETS
• Buffer overflow vulnerabiliGes.
• Detect spaGal/temporal memory
safety violaGons in legacy C code.
• Implemented as an LLVM pass.
• What about correctness?
[NagarakaLe, et al. PLDI ’09, ISMM ‘10]
hLp://www.cis.upenn.edu/acg/so[bound/](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-11-320.jpg)
![InspiraGon: CompCert
12
[Xavier Leroy INRIA Rocquencourt]
OpGmizing C Compiler:
proved correct end-to-end
with machine-checked proof in Coq
C language
CompCert
Compiler
ISA
rich, formal,
2-sided, live](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-12-320.jpg)
![Does Such VerificaGon Work?
LLVM
Csmith Tool
Random
test-case generaGon
{8 other C compilers}
+
CompCert
79 bugs
(25 criGcal)
202 bugs
325 bugs in
total
Source
Programs
[Yang et al. PLDI 2011]](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-13-320.jpg)

![LLVM Compiler Infrastructure
LLVM
Front
Ends
Code
Gen/Jit
OpGmizaGons/
TransformaGons
Typed SSA
IR
Analysis
[LaLner et al. ]](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-15-320.jpg)
![LLVM Compiler Infrastructure
LLVM
Front
Ends
Code
Gen/Jit
OpGmizaGons/
TransformaGons
Typed SSA
IR
Analysis
[LaLner et al.]](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-16-320.jpg)
![The Vellvm Project
OpGmizaGons/
TransformaGons
Typed SSA
IR
Analysis
• Formal semanGcs
• FaciliGes for creaGng
simulaGon proofs
• Implemented in Coq
• Extract passes for use
with LLVM compiler
• Example: verified
memory safety
instrumentaGon
[Zhao et al. POPL 2012, CPP 2012, PLDI 2013]](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-17-320.jpg)




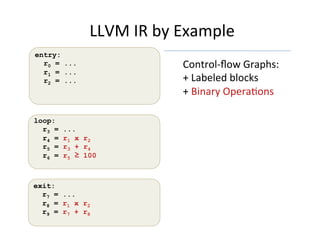


![LLVM IR by Example
entry:
r0 = ...
r1 = ...
r2 = ...
br r0 loop exit
Control-flow Graphs:
+ Labeled blocks
+ Binary OperaGons
+ Branches/Return
+ StaGc Single Assignment
+ φ nodes
exit:
r7 = φ[0;entry][r5;loop]
r8 = r1 x r2
r9 = r7 + r8
ret r9
loop:
r3 = φ[0;entry][r5;loop]
r4 = r1 x r2
r5 = r3 + r4
r6 = r5 ≥ 100
br r6 loop exit](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-25-320.jpg)
![LLVM IR by Example
entry:
r0 = ...
r1 = ...
r2 = ...
br r0 loop exit
Control-flow Graphs:
+ Labeled blocks
+ Binary OperaGons
+ Branches/Return
+ StaGc Single Assignment
+ φ nodes
(choose values based
on predecessor blocks)
exit:
r7 = φ[0;entry][r5;loop]
r8 = r1 x r2
r9 = r7 + r8
ret r9
loop:
r3 = φ[0;entry][r5;loop]
r4 = r1 x r2
r5 = r3 + r4
r6 = r5 ≥ 100
br r6 loop exit](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-26-320.jpg)

![Other Parts of the LLVM IR
28
op ::= %uid | constant | undef Operands
bop ::= add | sub | mul | shl | … OperaEons
cmpop ::= eq | ne | slt | sle | … Comparison
insn ::=
| %uid = alloca ty Stack AllocaEon
| %uid = load ty op1 Load
| store ty op1, op2 Store
| %uid = getelementptr ty op1 … Address CalculaEon
| %uid = call rt fun(…args…) FuncEon Calls
| …
phi ::=
| φ[op1;lbl1]...[opn;lbln]
terminator ::=
| ret %ty op
| br op label %lbl1, label %lbl2
| br label %lbl](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-28-320.jpg)

![LLVM IR SemanGcs
SSA CFG ≈ funcGonal program
+
• Types & Memory Layout
– structured, recursive types
– type-directed projecGon
– type casts
• Effects
– structured heap load/store
– system calls (I/O)
– nondeterminism
[Appel 1998]
We know how
to model this
and prove
properGes about
the models.](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-30-320.jpg)
![LLVM’s memory model
• Manipulate structured types.
%ST = type {i10,[10 x i8*]}
i10
i8*
i8*
i8*
i8*
i8*
i8*
i8*
i8*
i8*
i8*
High-level
RepresentaGon
%val = load %ST* %ptr
…
store %ST* %ptr, %new](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-31-320.jpg)
![LLVM’s memory model
• Manipulate structured types.
• SemanGcs is given in terms of
byte-oriented low-level
memory.
– padding & alignment
– physical subtyping
%ST = type {i10,[10 x i8*]}
b(10, 136) 0
b(10, 2) 1
uninit 2
uninit 3
ptr(Blk32,0,0) 4
ptr(Blk32,0,1) 5
ptr(Blk32,0,2) 6
ptr(Blk32,0,3) 7
ptr(Blk32,8,0) 8
ptr(Blk32,8,1) 9
ptr(Blk32,8,2) 10
ptr(Blk32,8,3) 11
… 12
… …
i10
i8*
i8*
i8*
i8*
i8*
i8*
i8*
i8*
i8*
i8*
High-level
RepresentaGon
Low-level
RepresentaGon
%val = load %ST* %ptr
…
store %ST* %ptr, %new](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-32-320.jpg)
![Dynamic Physical Subtyping
b(10, 136) 0
b(10, 2) 1
uninit 2
uninit 3
ptr(Blk32,0,0) 4
ptr(Blk32,0,1) 5
ptr(Blk32,0,2) 6
ptr(Blk32,0,3) 7
ptr(Blk32,8,0) 8
ptr(Blk32,8,1) 9
ptr(Blk32,8,2) 10
ptr(Blk32,8,3) 11
… 12
… …
Blk0 Blk1 Blk32
b(16, 1) 0
b(16, 0) 1
uninit 2
uninit 3
uninit 4
uninit 5
uninit 6
uninit 7
ptr(Blk1,0,0) 8
ptr(Blk1,0,1) 9
ptr(Blk1,0,2) 10
ptr(Blk1,0,3) 11
… 12
… …
i10
load i16*
⇒ 1
✓
load i16*
⇒ undef
✗
[Nita, et al. POPL ’08]](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-33-320.jpg)








![Big-step DeterminisGc Refinements
[Tristan, et al. POPL ’08, Tristan, et al. PLDI ’09]
Small Step Big Step
NondeterminisGc
DeterminisGc
LLVMND
LLVMD LLVM*
DFn LLVM*
DBLLVMInterp ≈︎ ≿︎ ≿︎
∋︎
SimulaGon up to “observable events”:
• useful for encapsulaGng behavior of funcGon calls
• large step evaluaGon of basic blocks](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-42-320.jpg)



![Key SSA Invariant
entry:
r0 = ...
r1 = ...
r2 = ...
br r0 loop exit
exit:
r7 = φ[0;entry][r5;loop]
r8 = r1 x r2
r9 = r7 + r8
ret r9
loop:
r3 = φ[0;entry][r5;loop]
r4 = r1 x r2
r5 = r3 + r4
r6 = r5 ≥ 100
br r6 loop exit
DefiniGon of r2.
Use of r2. Uses of r2.](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-46-320.jpg)
![Key SSA Invariant
entry:
r0 = ...
r1 = ...
r2 = ...
br r0 loop exit
exit:
r7 = φ[0;entry][r5;loop]
r8 = r1 x r2
r9 = r7 + r8
ret r9
loop:
r3 = φ[0;entry][r5;loop]
r4 = r1 x r2
r5 = r3 + r4
r6 = r5 ≥ 100
br r6 loop exit
DefiniGon of r2.
Use of r2. Uses of r2.
The definiGon of a
variable must dominate
its uses.](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-47-320.jpg)


![Well-formed States
entry:
r0 = ...
r1 = ...
r2 = ...
br r0 loop exit
exit:
r7 = φ[0;entry][r5;loop]
r8 = r1 x r2
r9 = r7 + r8
ret r9
loop:
r3 = φ[0;entry][r5;loop]
r4 = r1 x r2
r5 = r3 + r4
r6 = r5 ≥ 100
br r6 loop exit
pc
State σ is:
pc = program counter
δ = local values](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-50-320.jpg)
![Well-formed States
entry:
r0 = ...
r1 = ...
r2 = ...
br r0 loop exit
exit:
r7 = φ[0;entry][r5;loop]
r8 = r1 x r2
r9 = r7 + r8
ret r9
loop:
r3 = φ[0;entry][r5;loop]
r4 = r1 x r2
r5 = r3 + r4
r6 = r5 ≥ 100
br r6 loop exit
pc
State σ is:
pc = program counter
δ = local values
sdom(f,pc) = variable defns.
that strictly dominate pc.](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-51-320.jpg)
![Well-formed States
entry:
r0 = ...
r1 = ...
r2 = ...
br r0 loop exit
exit:
r7 = φ[0;entry][r5;loop]
r8 = r1 x r2
r9 = r7 + r8
ret r9
loop:
r3 = φ[0;entry][r5;loop]
r4 = r1 x r2
r5 = r3 + r4
r6 = r5 ≥ 100
br r6 loop exit
pc
State σ contains:
pc = program counter
δ = local values
sdom(f,pc) = variable defns.
that strictly dominate pc.
wf(f,σ) =
∀r∊sdom(f,pc). ∃v. δ(r) = ⎣v⎦
“All variables in scope
are iniGalized.”](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-52-320.jpg)
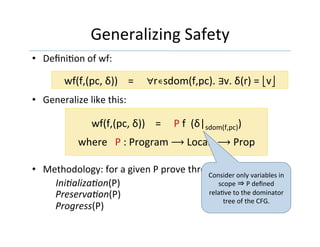
![InstanGaGng
• For usual safety:
• For semanGc properGes:
• Useful for verifying correctness of:
– code moGon, dead variable eliminaGon, common
expression eliminaGon, etc.
Psafety f δ = ∀r∊dom(δ). ∃v. δ(r) = ⎣v⎦
Psem f δ = ∀r. f[r] = ⎣rhs⎦ ⇒ δ(r) = ⟦rhs⟧δ](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-54-320.jpg)


![So[Bound
So[Bound
C Source
Code
Other
OpGmizaGons
LLVM
IR
LLVM
IR
Target
%p = call malloc [10 x i8]
%q = gep %p, i32 0, i32 255
store i8 0, %q
%p = call malloc [10 x i8]
%p_base = gep %p, i32 0
%p_bound = gep %p, i32 0, i32 10
%q = gep %p, i32 0, i32 255
%q_base = %p_base
%q_bound = %p_bound
assert %q_base <= %q
/ %q+1 < %q_bound
store i8 0, %q
Maintain base and bound for all pointers
Propagate metadata on assignment
Check that a pointer is within its
bounds when being accessed](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-57-320.jpg)

![Proving So[Bound Correct
1. Define So[Bound(f,σ) = (fs,σs)
– TransformaGon pass implemented in Coq.
2. Define predicate: MemoryViolaGon(f,σ)
3. Construct a non-standard operaGonal semanGcs:
– Builds in safety invariants “by construcGon”
4. Show that the instrumented code simulates the “correct”
code:
SB
f ⊢ σ ⟼ σ’
SB
f ⊢ σ ⟼* σ’ ⇒ ¬MemoryViolaGon(f,σ’)
So[Bound(f,σ) = (fs,σs) ⇒ [f ⊢ σ ⟼* σ’] ≿ [fs ⊢ σs ⟼* σ’s] SB](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-59-320.jpg)





![mem2reg Example
int x = 0;
if (y > 0)
x = 1;
return x;
l1: %p = alloca i32
store 0, %p
%b = %y > 0
br %b, %l2, %l3
l2:
store 1, %p
br %l3
l3:
%x = load %p
ret %x
The LLVM IR in the trivial SSA form
l1:
%b = %y > 0
br %b, %l2, %l3
l2:
br %l3
l3:
%x = φ[ 1,%l2] [ 0,%l1]
ret %x
Minimal SSA a[er mem2reg
mem2reg](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-65-320.jpg)

![vmem2reg Algorithm
• Incremental algorithm
• Pipeline of "micro transformaGons"
– Preserves SSA semanGcs
– Preserves well-formedness
See: [Aycock & Horspool 2002.]
max φs
LAS/
LAA
DSE
DAE
elim φ
Find
alloca](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-67-320.jpg)


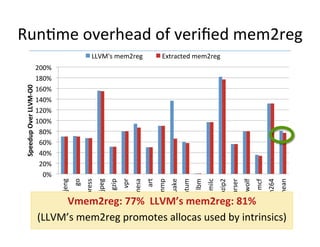

![Ongoing Work
• Modular SemanGcs
– Factor out memory model [CAV 15]
– Linking/separate compilaGon
• For:
– more extensibility/robustness to changes
– verifying more analyses and opGmizaGons / program transformaGons
– support for (relaxed) concurrency
– beLer support for casts [PLDI 15]
LLVM SSA
core IR
Memory
Model / IO Concurrency](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-72-320.jpg)
![• Deep SpecificaGons
– rich, formal, 2-sided, live
• Layers of abstracGon
– Layer Calculus in CerGKOS [Shao et al.]
– Good for proofs!
– Bad for performance?
– ImplicaGons for theory / proof engineering?
• ComposiGonal specificaGon
– ComposiGonal CompCert [Stewart, et al. PLDI 15]
• So[ware Engineering ⇒ Proof Engineering
– Coq development methodology [CPDT: Chlipala]
What engineering principles enable
large-scale deep specifications?](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-73-320.jpg)
![Conclusions
• Proof techniques for verifying LLVM transformaGons
• Verified:
– So[bound & vmem2reg
– Similar performance to naGve implementaGons
• Future:
– IntegraGon with other DeepSpec projects
[hLp://www.cis.upenn.edu/~stevez/vellvm/]](https://image.slidesharecdn.com/10-00zdancewic-tmpa2017-170323080808/85/TMPA-2017-Vellvm-Verifying-the-LLVM-74-320.jpg)