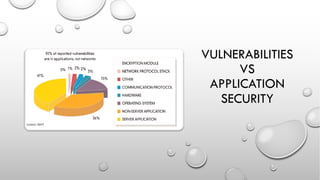
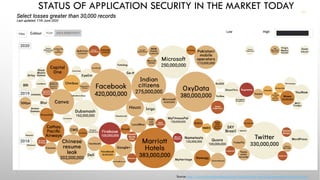
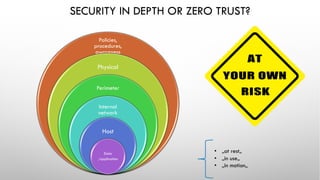
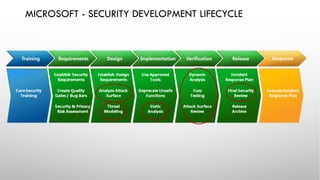
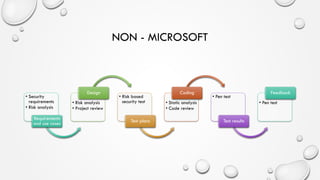
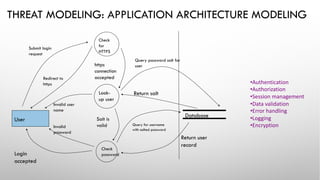
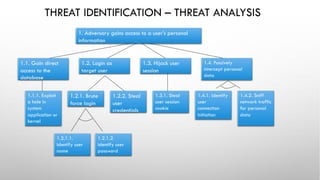
The document discusses threat modeling and application security testing. It begins by noting a lack of secure coding knowledge among developers and testers. It then uses an analogy comparing building applications to building cars, noting many similarities in unsecure practices. This is followed by sections on vulnerabilities versus security, common application vulnerabilities, and industry solutions. The document concludes by discussing threat modeling and provides an example using the OWASP Threat Dragon tool.