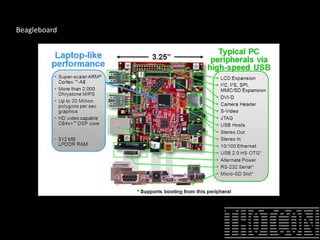
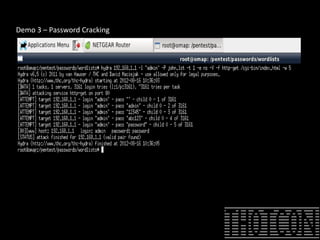
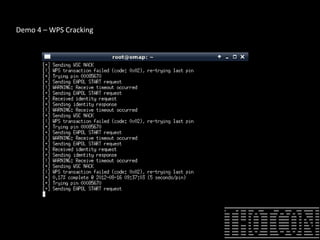
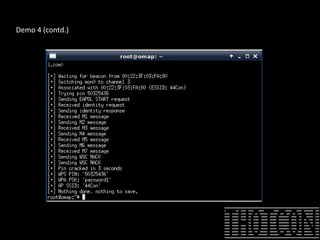
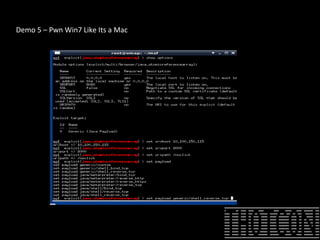
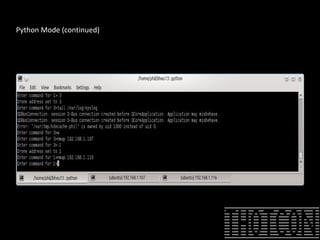
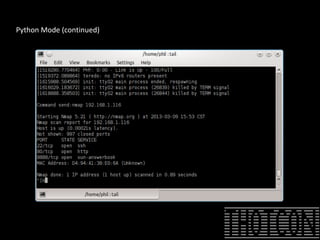
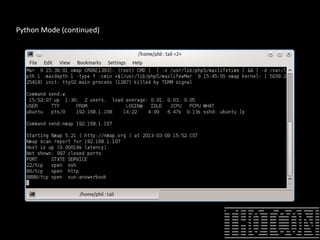
The document discusses how to perform penetration testing using low-power networked devices like BeagleBoard and BeagleBone, covering platform selection, base operating systems, and building tools. It emphasizes the advantages of these devices over alternatives like Raspberry Pi and provides guidance on setting up hardware accessories and networking configurations for coordinated attacks. The presentation also includes practical demonstrations of various hacking techniques and potential future developments in this field.