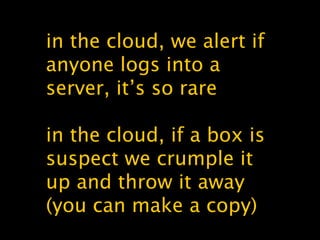
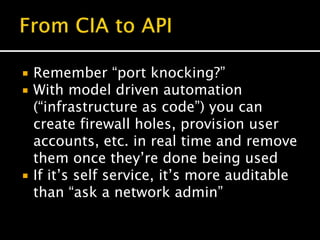
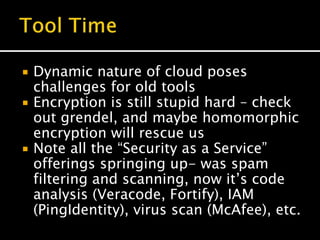
The document discusses cloud computing, highlighting its evolution, benefits, and security aspects. It compares traditional IT operations with cloud solutions, emphasizing improvements in scalability, resilience, and security while addressing common misconceptions. The author argues that cloud services can enhance security posture and operational efficiency, advocating for a shift toward agile development and better integration of security practices within the cloud environment.


![(ISP -> colo) + virtualization + HPC
+ (AJAX + SOA -> REST APIs) = IaaS
IDE/4GLs + EAI + SaaS + IaaS = PaaS
((web site -> web app) -> ASP) +
virtualization + fast network + [RIA
browsers && mobile] = SaaS
[IaaS | PaaS | SaaS ] + [ devops |
open source | noSQL ] = cloud](https://image.slidesharecdn.com/whythecloudismoresecure-101101101613-phpapp01/85/Why-the-cloud-is-more-secure-than-your-existing-systems-3-320.jpg)