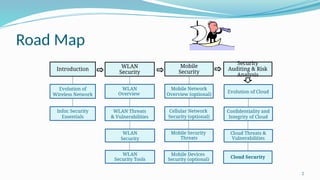
The document discusses cloud computing security, emphasizing the importance of security auditing, risk analysis, and the evolving threats to wireless and mobile networks. It asserts that while cloud services can be secure if managed appropriately, risks such as data location and provider reliability must be carefully considered. Additionally, the document outlines essential management, operation, and technology strategies for implementing effective cloud security measures.