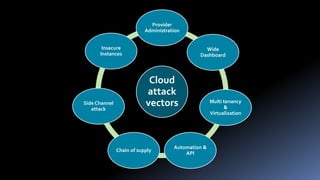
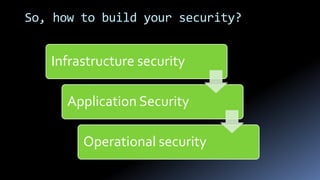
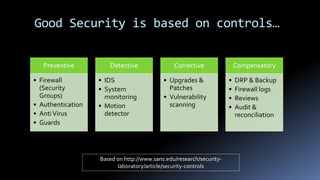
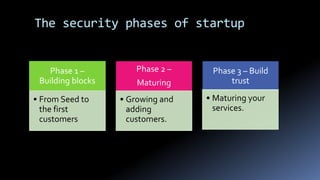
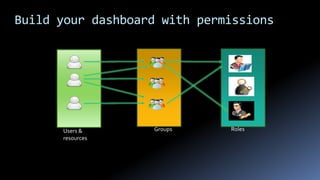
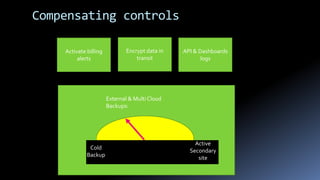
Moshe Ferber is an information security expert with over 20 years of experience and is actively involved in cloud security for startups. The document outlines the benefits and risks of cloud computing, emphasizing the importance of building a robust security framework in three phases to ensure safety and compliance. It provides best practices for managing infrastructure security, application security, and operational security throughout the lifecycle of a startup.