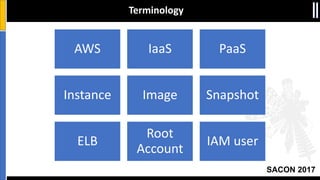
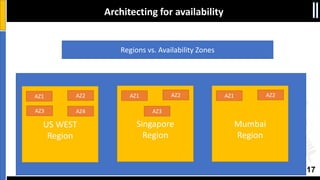
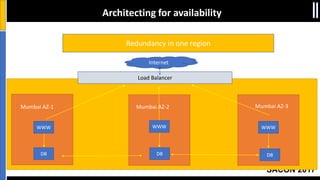
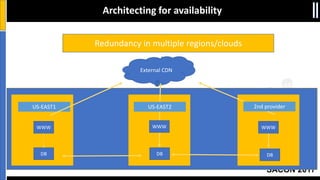
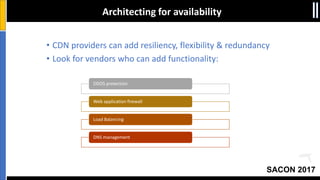
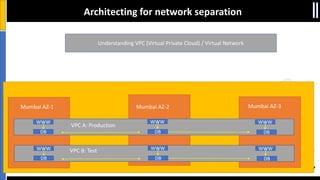
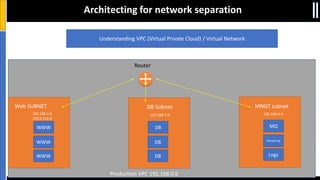
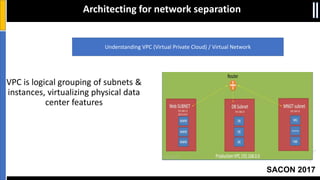
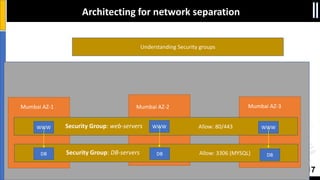
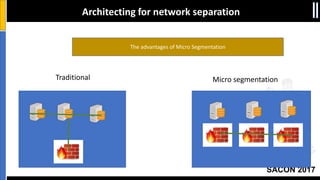
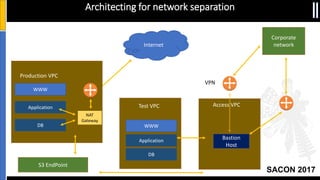
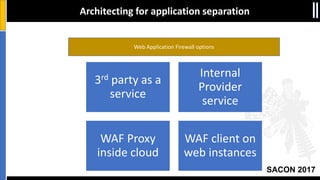
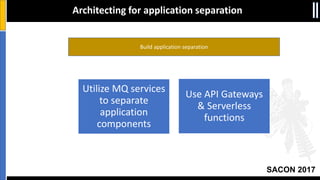
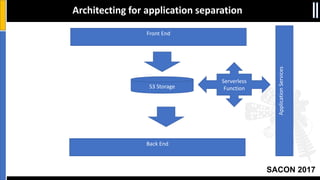
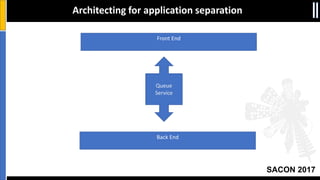
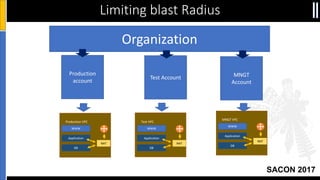
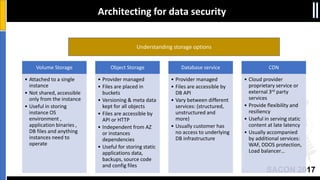
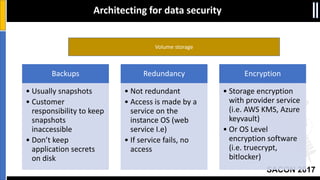
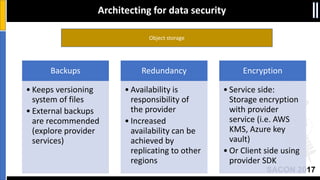
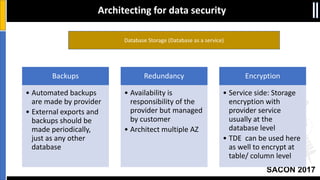
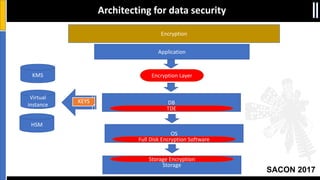
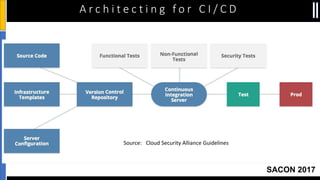
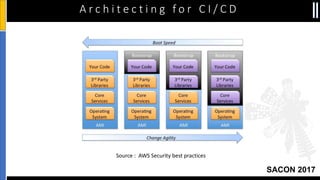
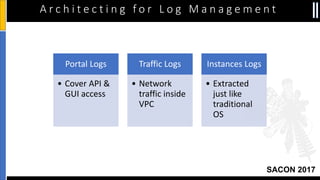
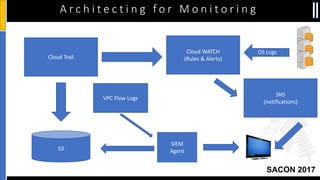
The document is a presentation by Moshe Ferber, an information security professional, focused on architecting secure cloud services and emphasizing the variations between IaaS, PaaS, and SaaS cloud services. It discusses strategic principles for security in cloud architecture, including availability, network separation, application separation, and data security, highlighting tools and practices like micro-segmentation and encryption. Additionally, it covers the importance of audit and monitoring for secure cloud environments and provides a resource for further cloud security course schedules.