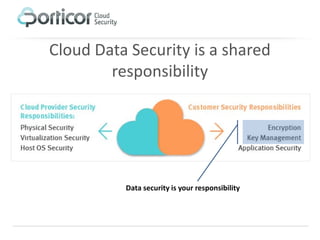
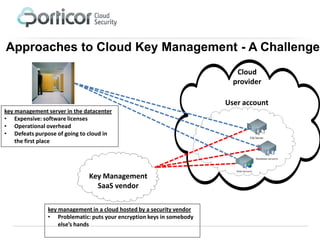
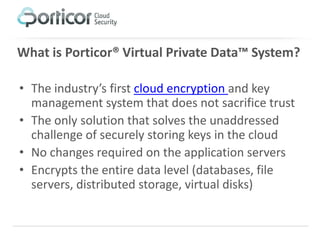
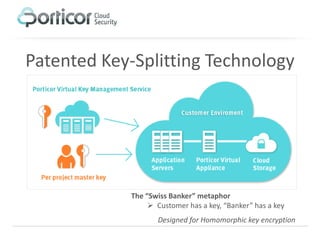
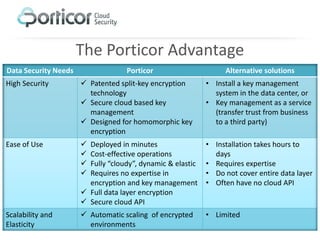
Porticor offers a cloud encryption and key management system that addresses the challenge of securely storing encryption keys in the cloud without compromising trust. The solution employs patented split-key technology for full data layer encryption and is designed for efficiency, scalability, and compliance with regulatory standards. It enables businesses to manage their data security easily and cost-effectively in the cloud of their choice.