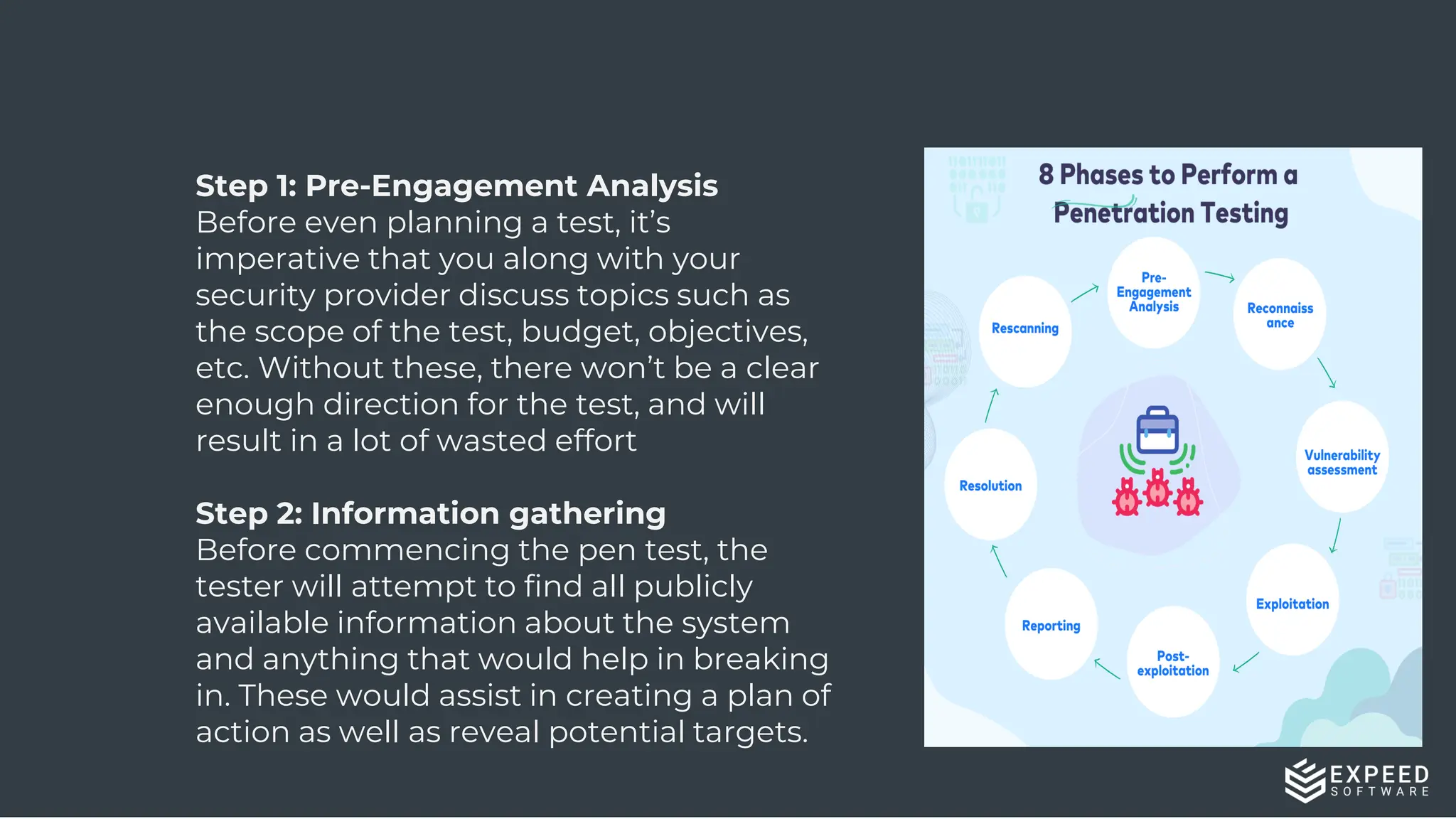
The document outlines the importance and methodologies of penetration testing in cybersecurity, highlighting various testing types such as network, web application, and wireless testing. It details the phases involved in penetration testing, from pre-engagement analysis to reporting, resolution, and rescanning of vulnerabilities. The document also discusses the advantages and challenges of penetration testing, emphasizing the need for skilled resources to address evolving cyber threats.