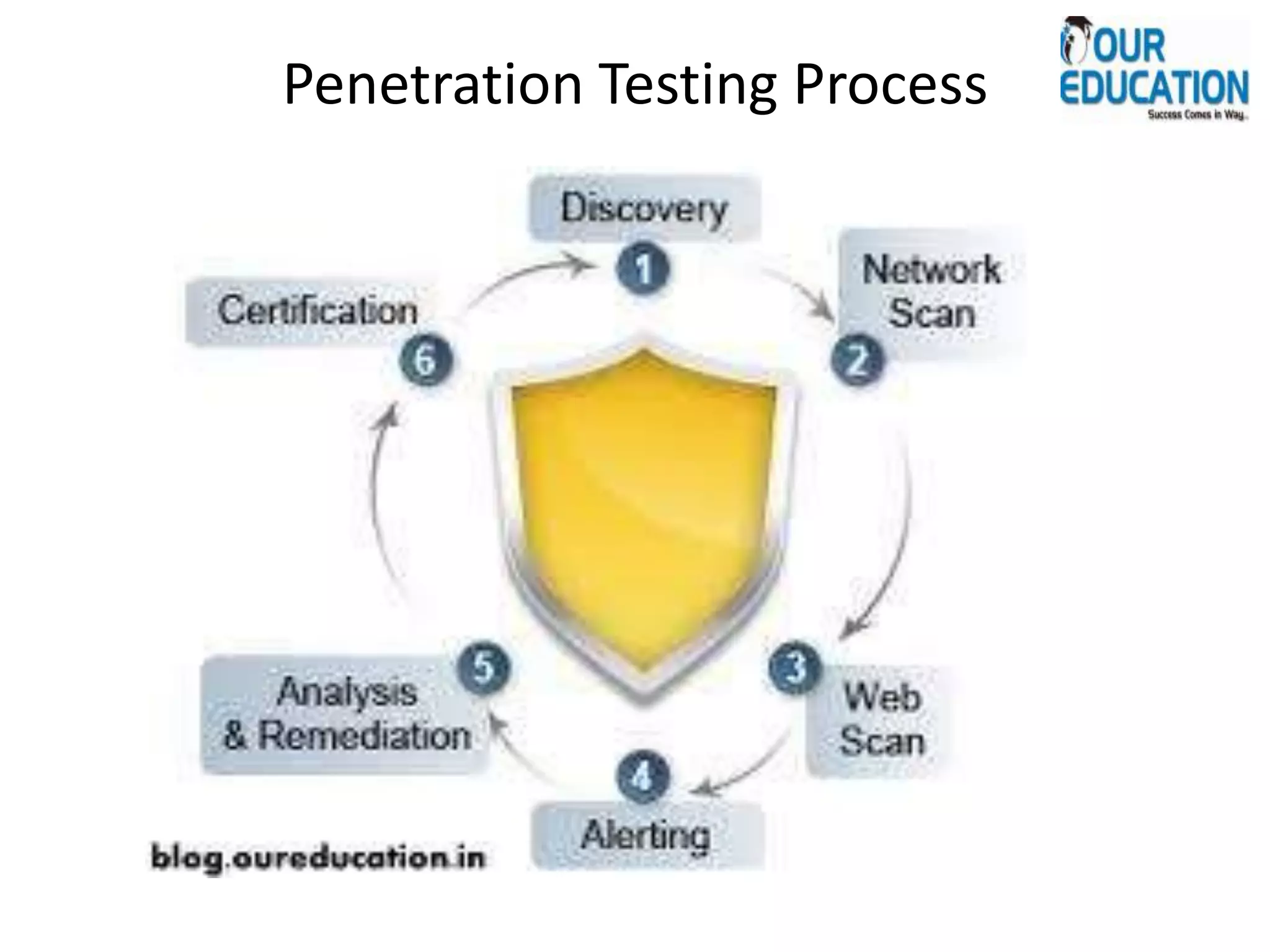
Penetration testing involves attempting to exploit vulnerabilities in a system to evaluate security. It can be used to test network, application, and endpoint security as well as user awareness. There are different types including targeted, external, internal, and blind testing. The objective is to determine vulnerabilities by simulating attacks from both inside and outside the system to identify security weaknesses and validate defensive measures. It helps prioritize risks and assess potential impacts of attacks.