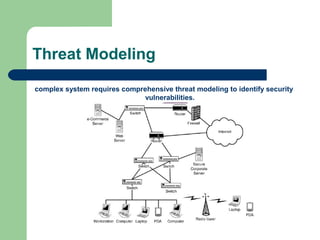
A secure product protects customers' information and system resources from unauthorized access. As a software tester, it is important to understand why hackers may try to break into software in order to think of where security vulnerabilities could exist. Threat modeling involves assembling a team to identify assets, architecture, potential threats, and their risks to find areas of the software's features that may be vulnerable to security issues. Testing for security bugs should approach testing as "test-to-fail" by attacking the software like a hacker would to assume every feature could have a vulnerability.