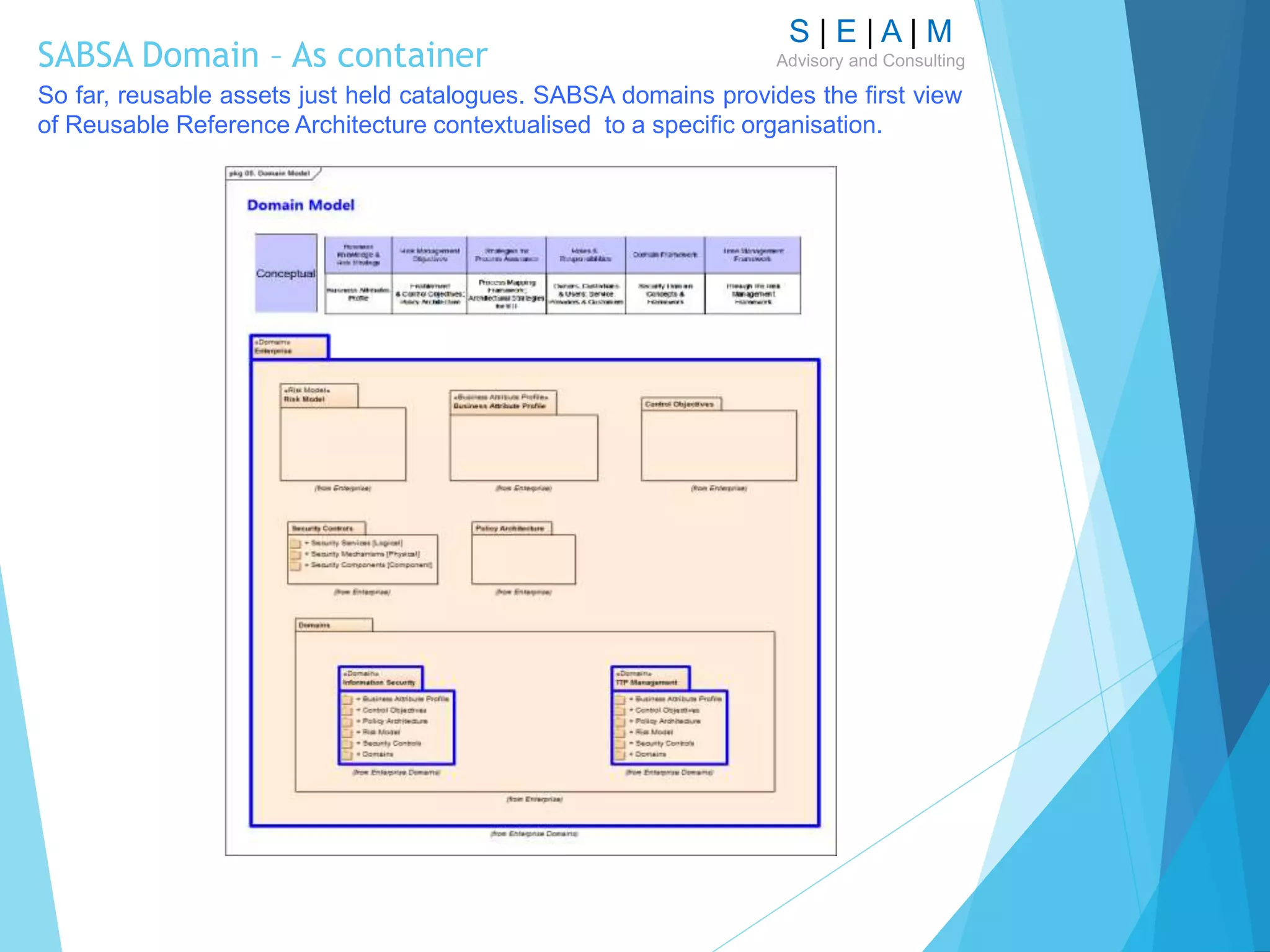
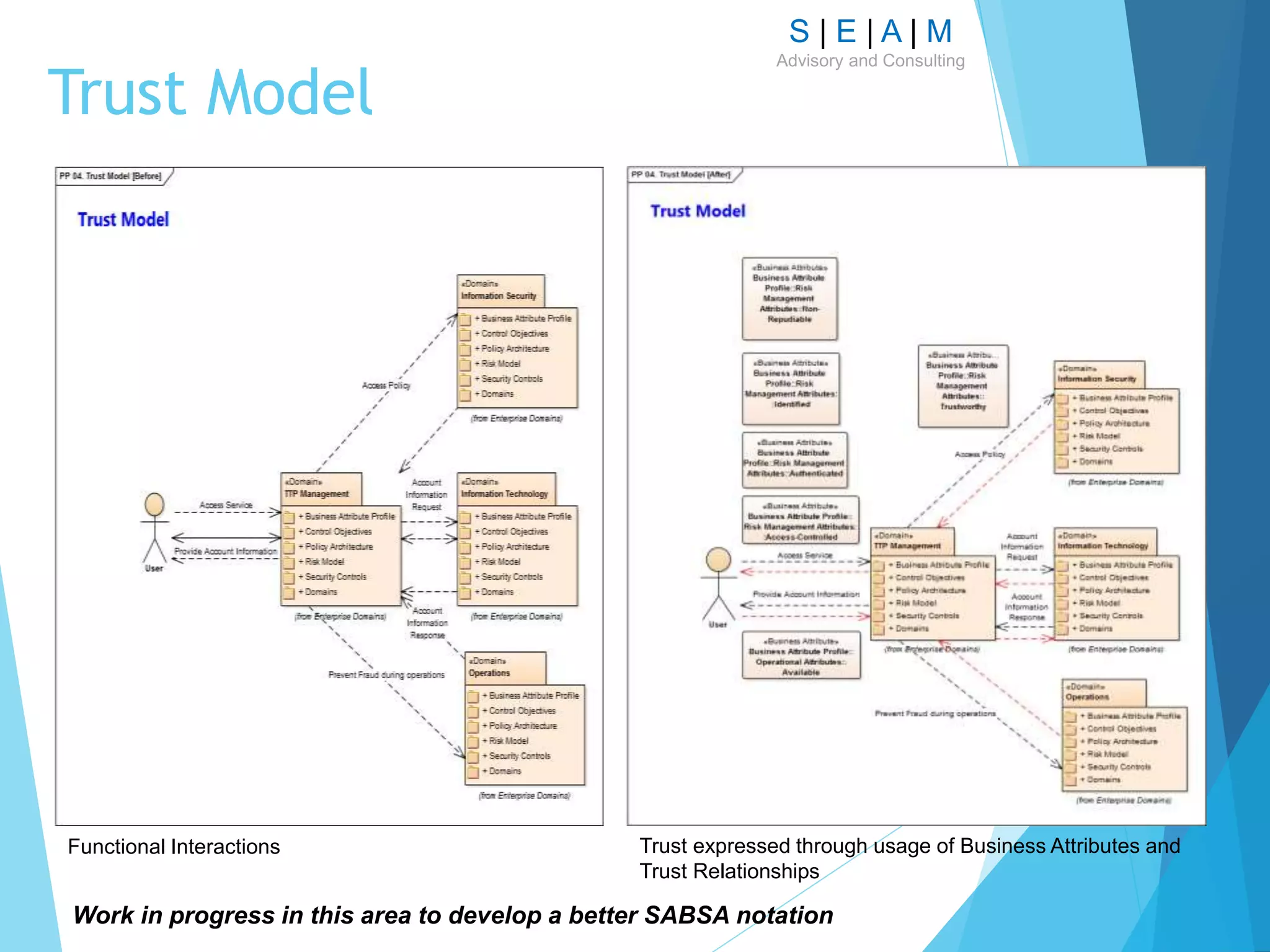
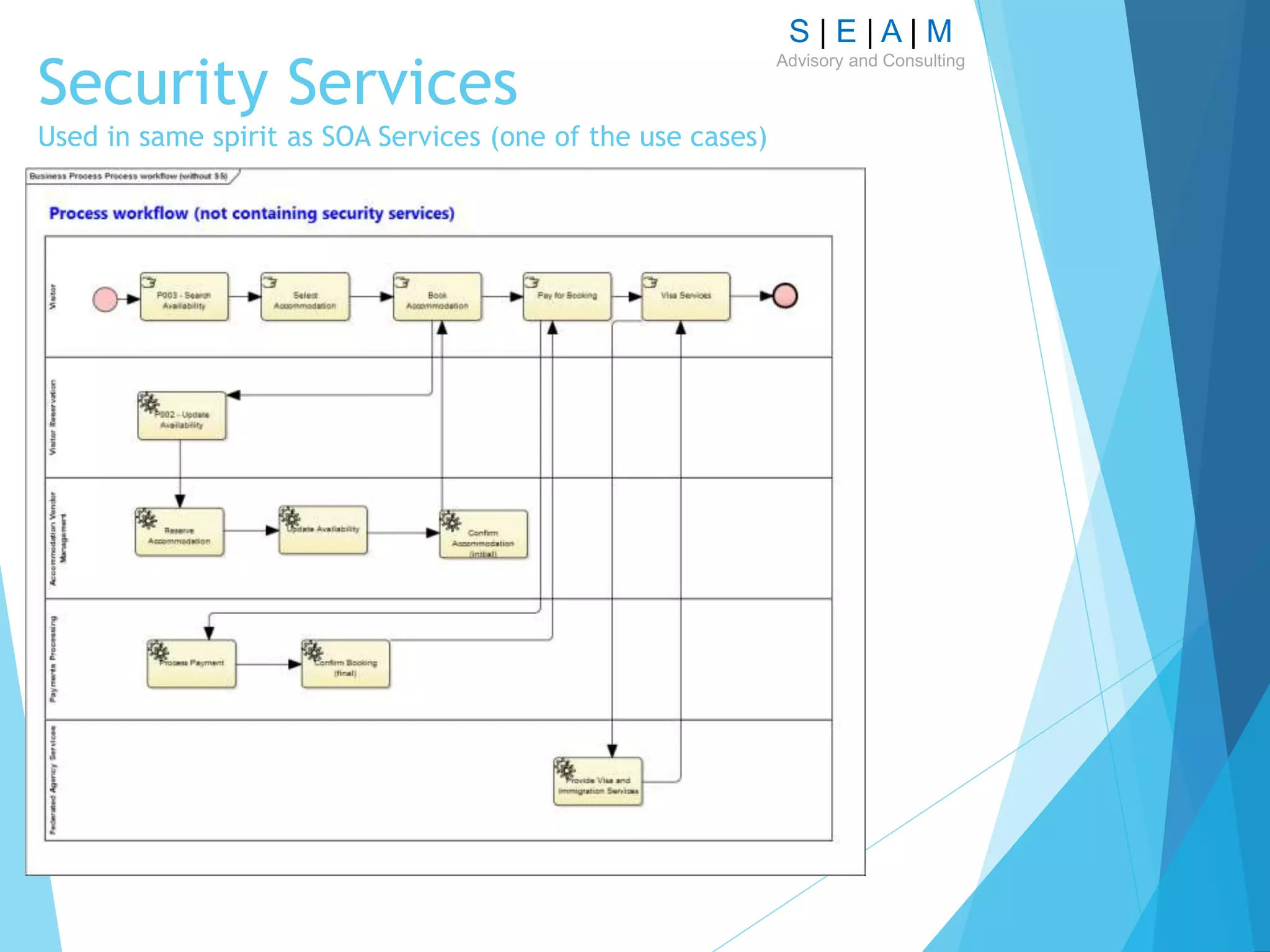
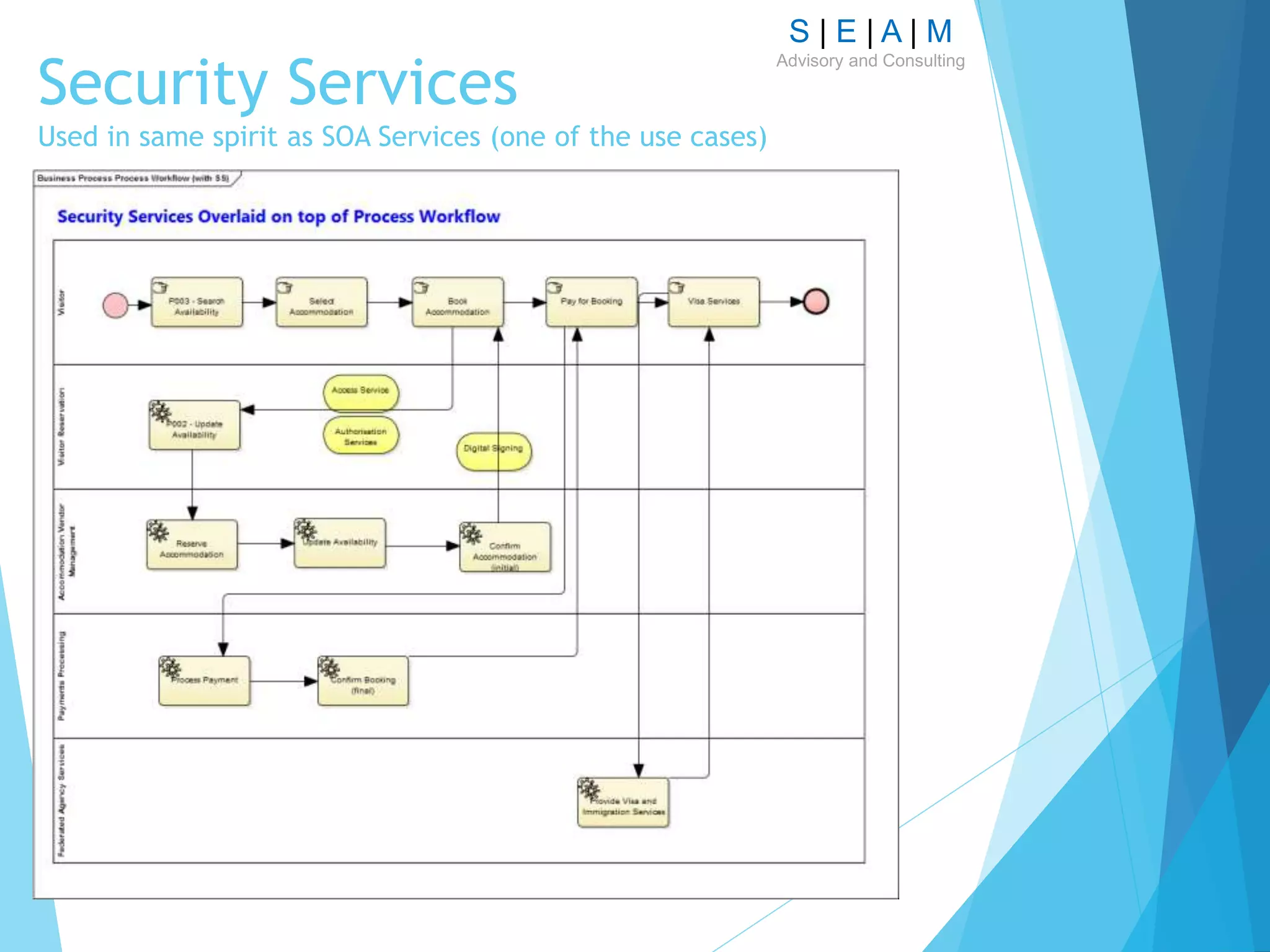
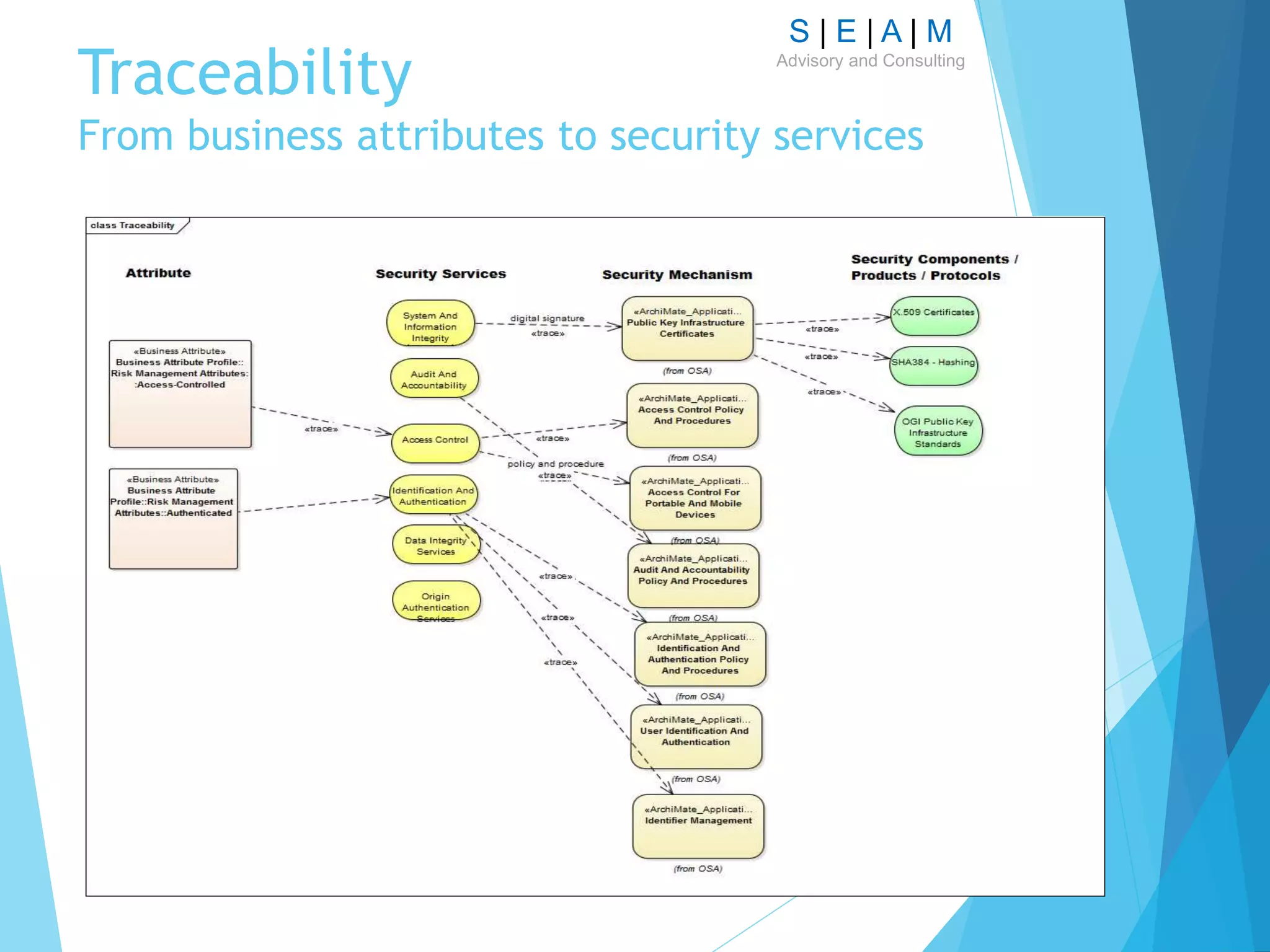
The document outlines a proposal for a comprehensive technique to model enterprise security architecture using the SABSA framework, emphasizing standardization, reusability of model artifacts, and the creation of a library for various essential components. It highlights the importance of aligning security architecture with business needs through a structured modeling notation and discusses the practical application of this approach in the context of financial services, specifically in relation to the PSD2 initiative. The paper also addresses the concept of integrating risk and trust models within the architecture to enhance design and collaboration across departments.



![S | E | A | M
Advisory and ConsultingExample Used: PSD/2 for Banks
What is PSD/2?
Extension to European Payments Service Directive with
significant changes
Aspires to establish a level playing field for financial institutions
Simplifies financial transactions for customers with use cases
such as unified accounts management, single payments
application etc. along with number of other use cases.
Before and After PSD/2 – Account Information
Bank 1 App
Bank 1 App
Bank 1 App
BEFORE PSD/2
Third
Party
App
AFTER PSD/2 Accounting
Information Service
Providers [AISP]
https://openbankproject.com](https://image.slidesharecdn.com/modellingsecurityarchitecturev11-161007124729/75/Modelling-Security-Architecture-11-2048.jpg)

![S | E | A | M
Advisory and Consulting
Are we modelling PSD/2
Architecture fully?
This is for illustration ONLY
The modelling reflects salient features of SABSA that
other notations don’t support out-of-box
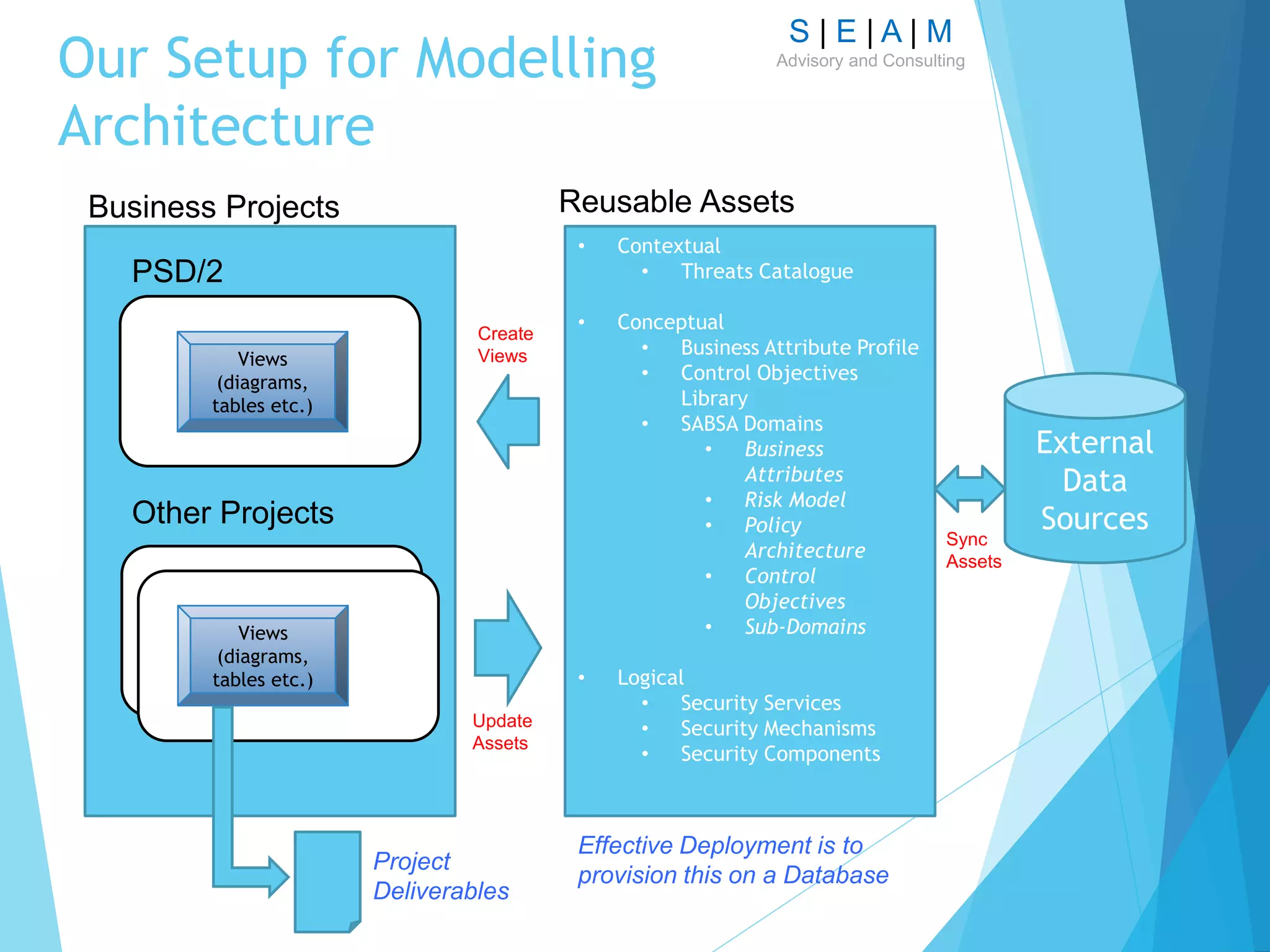
So, what are we modelling?
Contextual Architecture – mainly uses Archimate 2.0 –
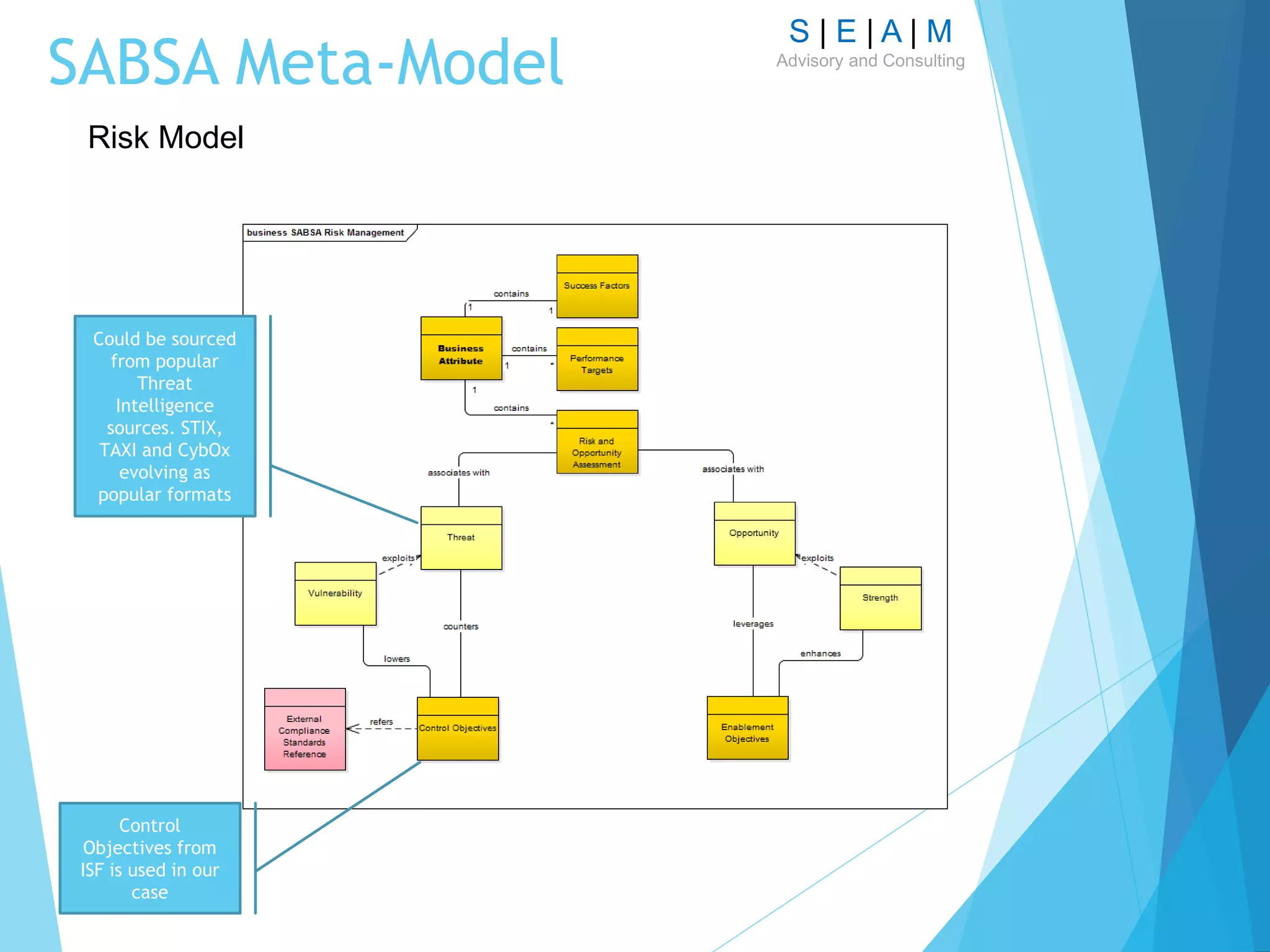
Motivation Extensions; we will do ‘Risk Modelling’
[Business Risks]
Conceptual Architecture – key modelling illustrates
Business Attribute Profile, Control Objectives [Library] and
Domain modelling
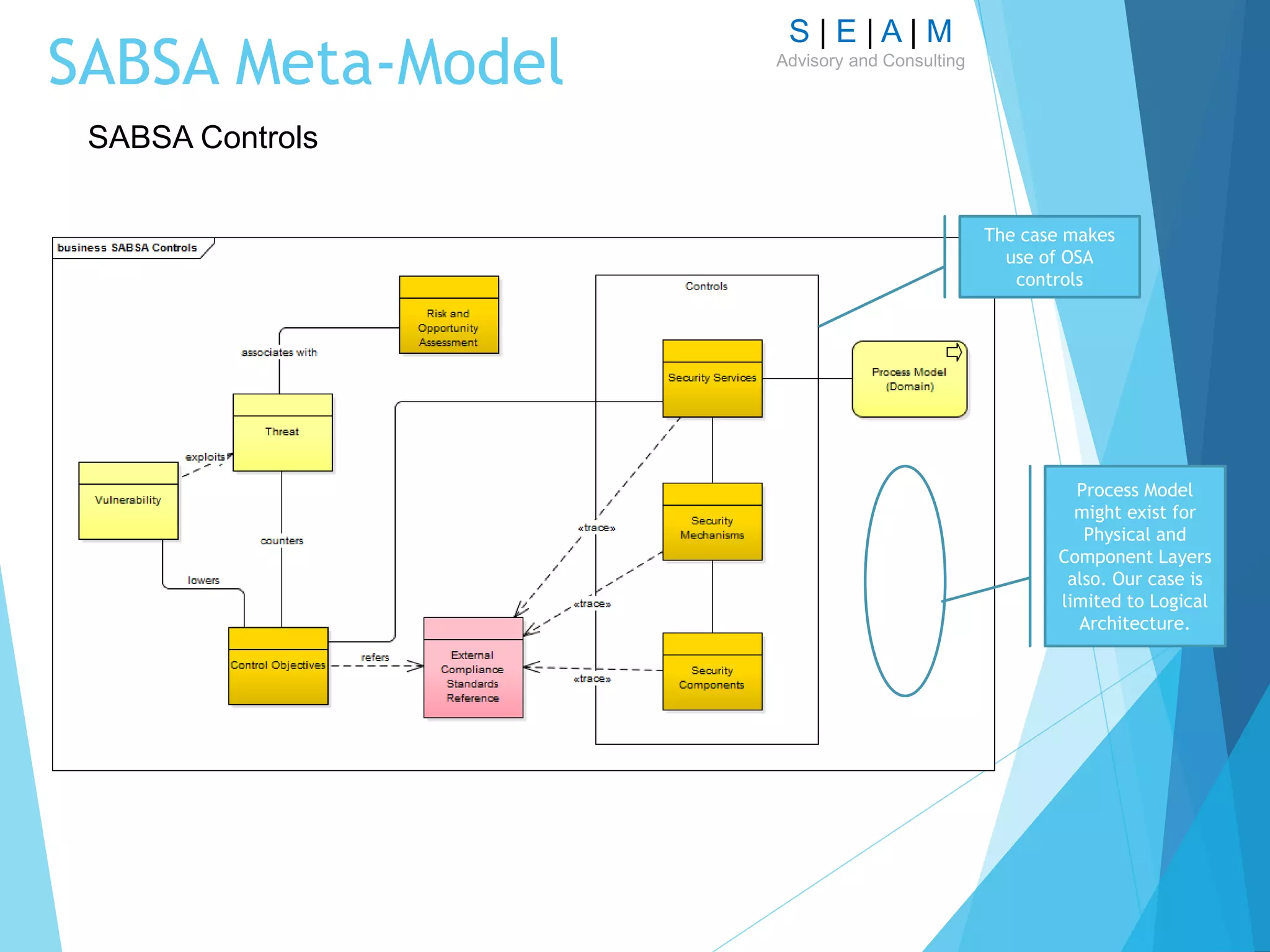
Logical Architecture – main focus is on Security Services,
alignment of Security Services with process modelling and
Trust Modelling](https://image.slidesharecdn.com/modellingsecurityarchitecturev11-161007124729/75/Modelling-Security-Architecture-13-2048.jpg)
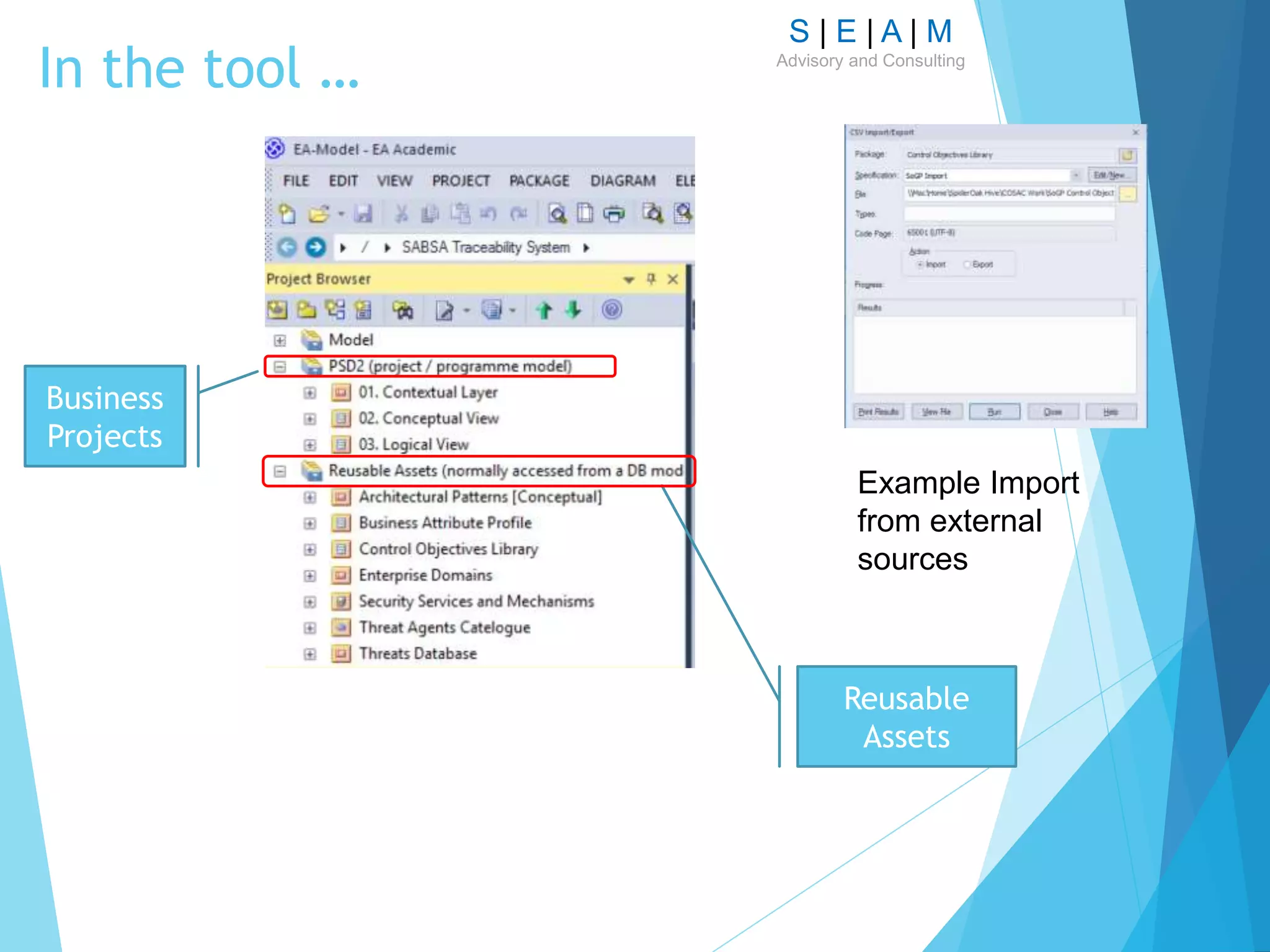
![S | E | A | M
Advisory and Consulting
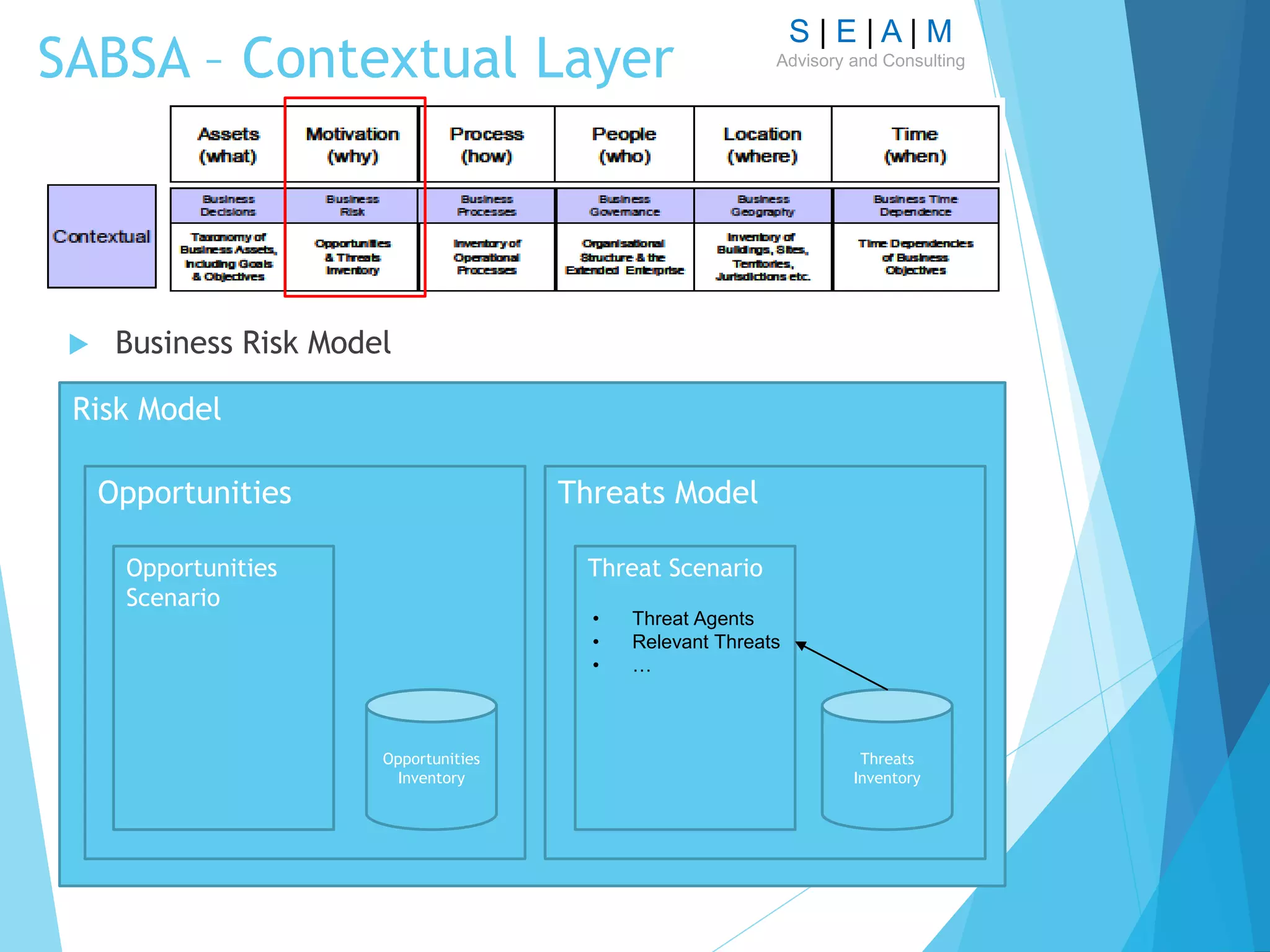
Contextual Architecture
Mainly focusing on Risk Model [Threats]](https://image.slidesharecdn.com/modellingsecurityarchitecturev11-161007124729/75/Modelling-Security-Architecture-16-2048.jpg)
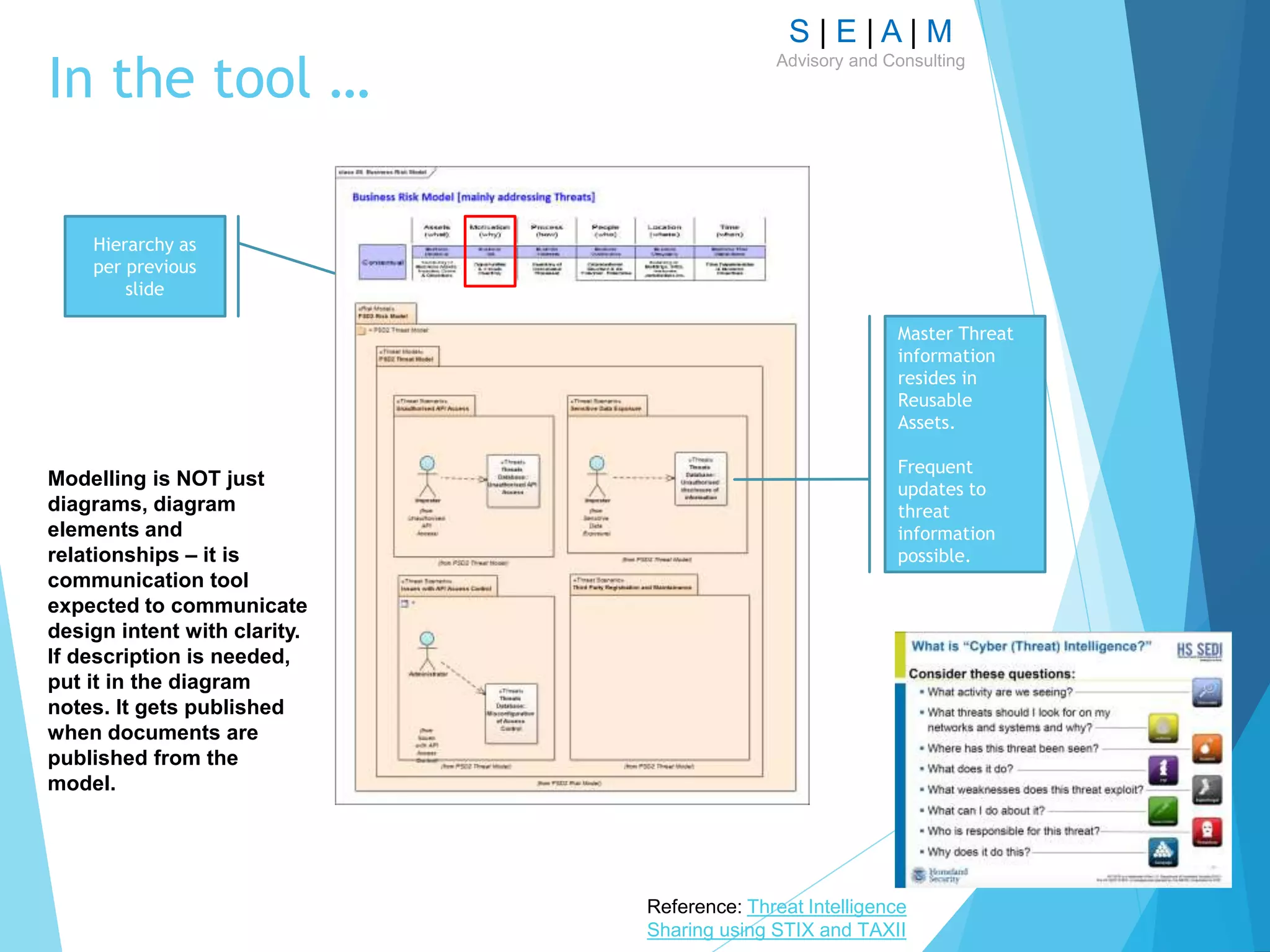
![S | E | A | M
Advisory and Consulting
Contextual Architecture
Other Views
Business Model [Assets] Business Capabilities [Process Inventory]
Organisation Structure [People] Business Geography [Location] Business Time Dependencies [Time]](https://image.slidesharecdn.com/modellingsecurityarchitecturev11-161007124729/75/Modelling-Security-Architecture-19-2048.jpg)

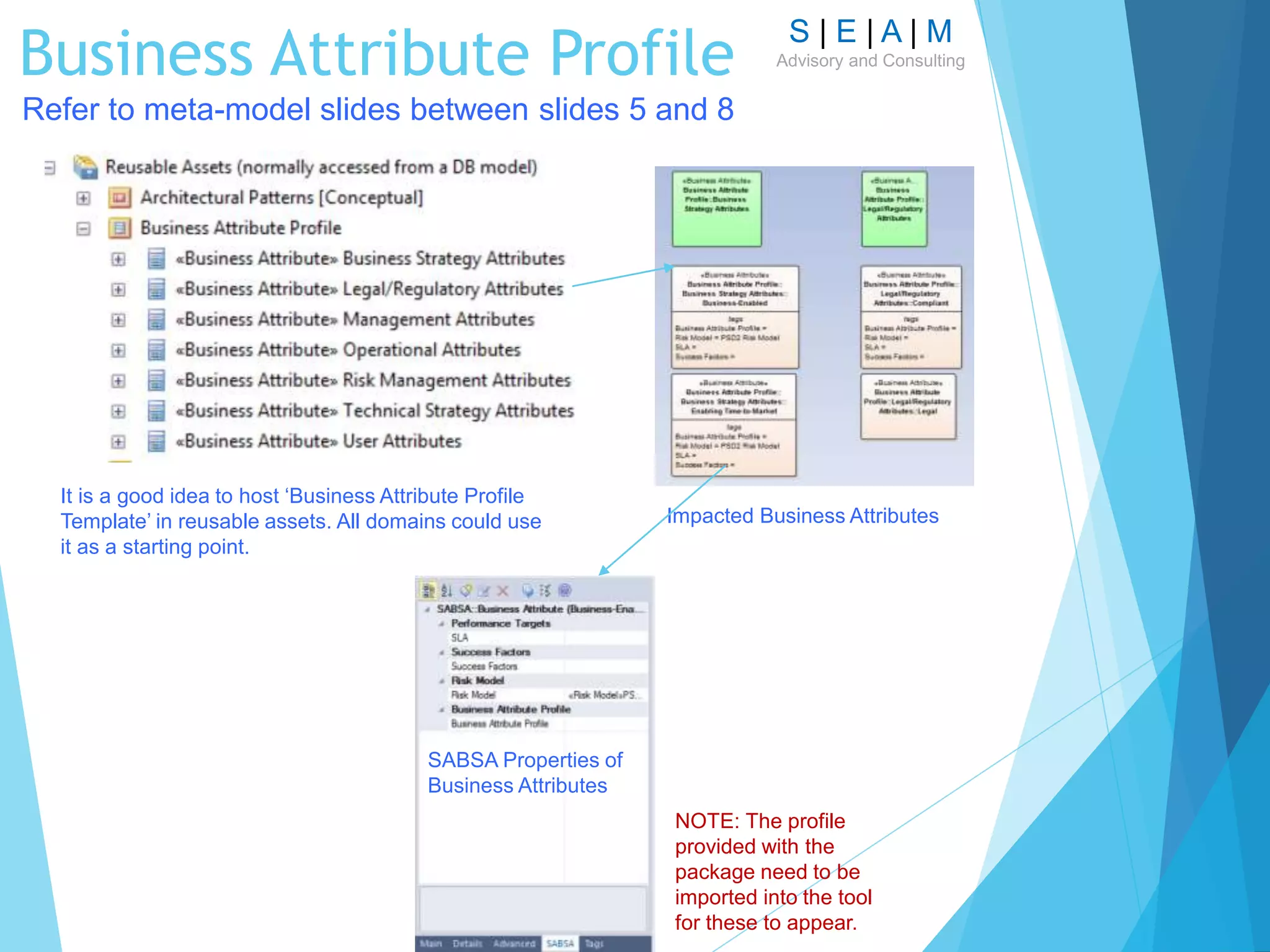
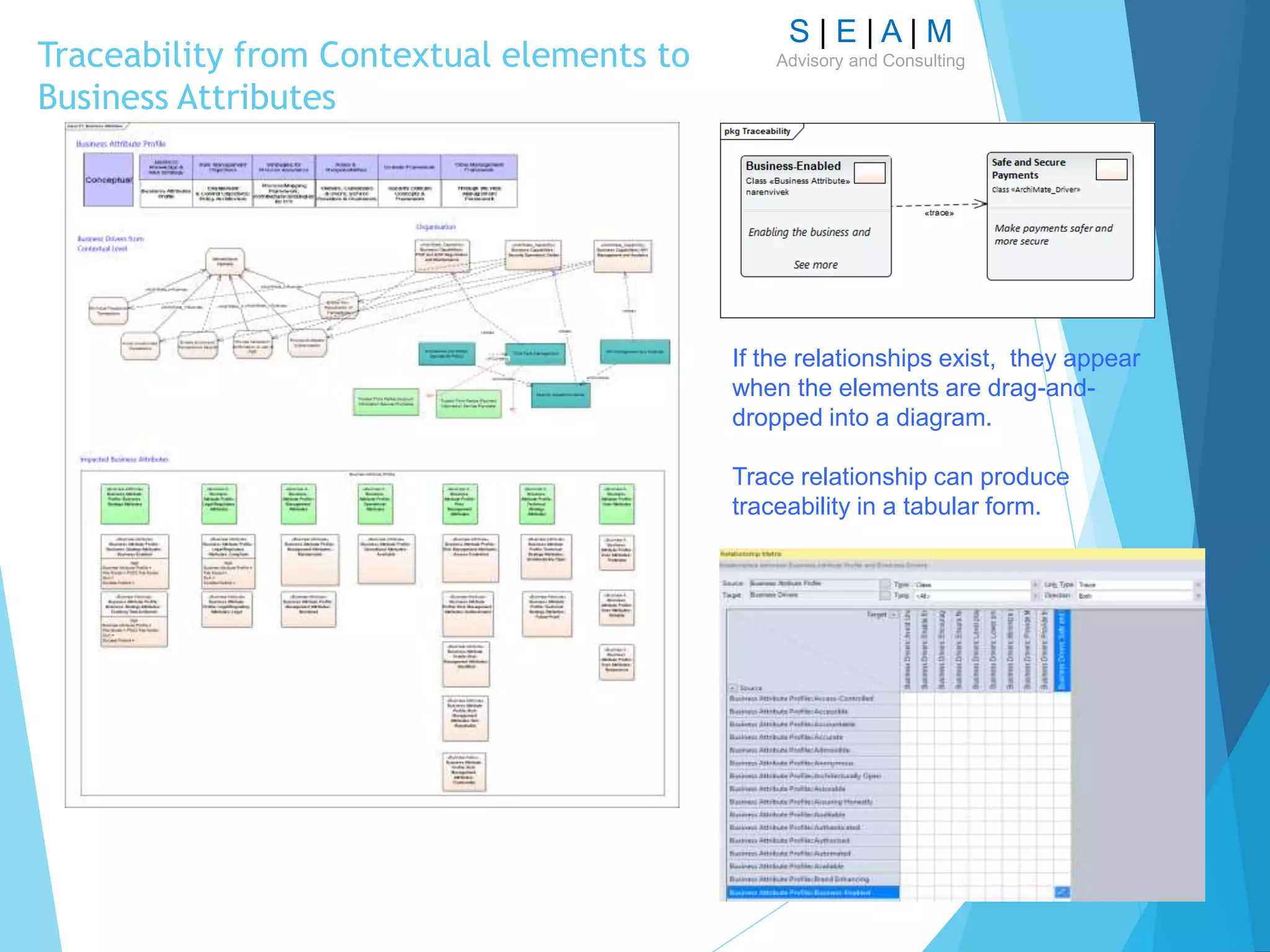
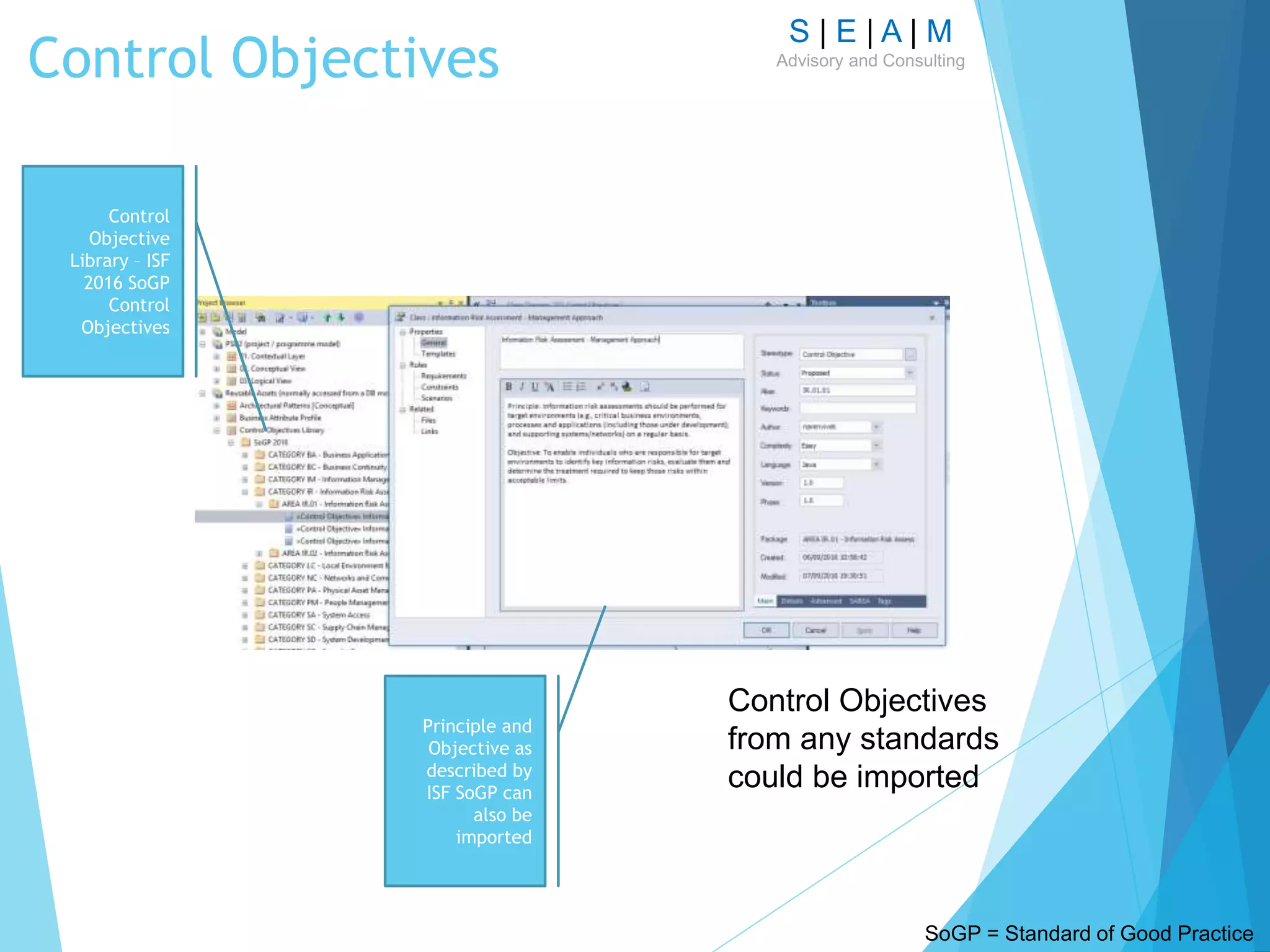
![S | E | A | M
Advisory and ConsultingLinking Control Objectives to Business
Attributes
Tags are the best way
to specify additional,
context-specific
information without
impacting model
integrity.
However, tooling
vendors seems to
support tags in
multiple ways.
Trace relationships
could automatically
provide relationship
matrix [tool
dependent].](https://image.slidesharecdn.com/modellingsecurityarchitecturev11-161007124729/75/Modelling-Security-Architecture-24-2048.jpg)