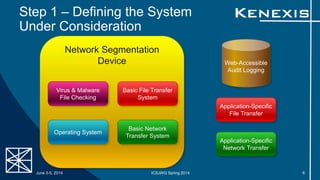
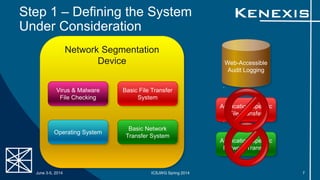
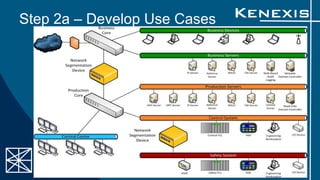
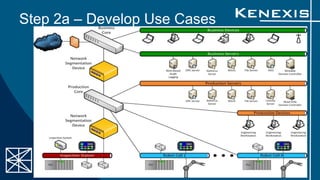
The document presents an evaluation of system-level cyber security in alignment with ANSI/ISA-62443-3-3 standards, detailing a project by Kenexis Consulting. It outlines a step-by-step approach to assessing a vendor-assembled system's security requirements, from defining the system to reporting results. Key steps include determining applicable requirements, developing use cases, and reassessing requirements based on system features and configurations.