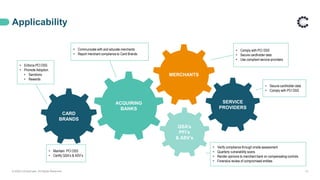
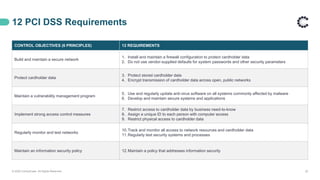
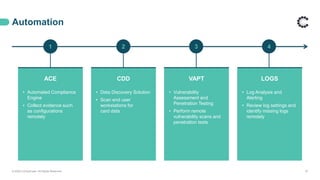
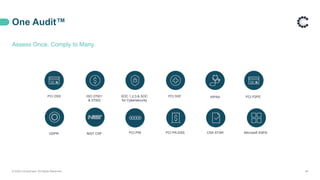
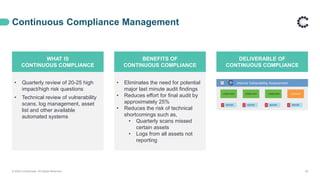
This webinar discusses PCI DSS compliance and how ControlCase can help organizations achieve and maintain compliance. It covers the basics of PCI DSS including the six principles and twelve requirements. It then outlines how ControlCase uses automation, continuous compliance management, and their One Audit approach to assess multiple standards at once to help clients comply in a cost-effective way. The webinar emphasizes that ControlCase can significantly reduce the effort and resources needed for PCI compliance.