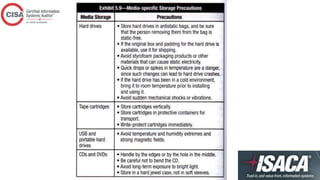
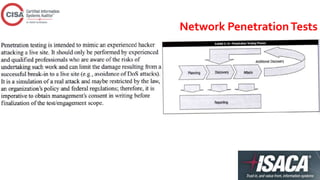
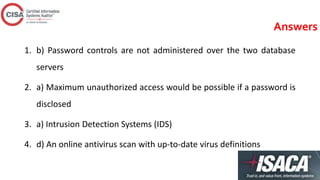
This document contains an outline for a CISA review course covering topics such as information security management, logical access controls, network security, and auditing frameworks. It includes sections on inventorying and classifying assets, access permissions, privacy issues, risks from external parties, and incident response. Self-assessment questions test on weaknesses like uncontrolled database passwords, the risks of single sign-on, uses of intrusion detection systems, and effective antivirus controls.
![2016 CISA® Review Course
Hafiz Sheikh Adnan Ahmed – CISA, COBIT 5, ISO 27001 LA
[PECB Certified Trainer]](https://image.slidesharecdn.com/chapter5cisa-training2016-161104181655/85/CISA-Training-Chapter-5-2016-1-320.jpg)