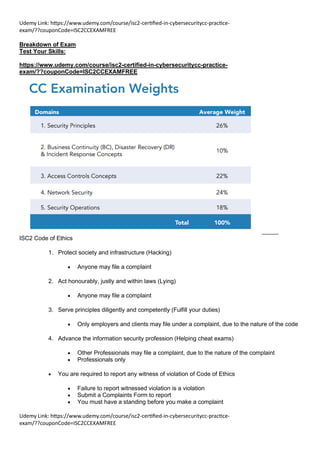
The document provides notes on topics for the ISC2 Cybersecurity exam, including a Udemy practice exam link. It covers the ISC2 Code of Ethics, the goals of information security (confidentiality, integrity, availability), common security threats and how to mitigate them. It also discusses authentication methods, risk assessment, security controls, security policies, business continuity planning, and other cybersecurity concepts.