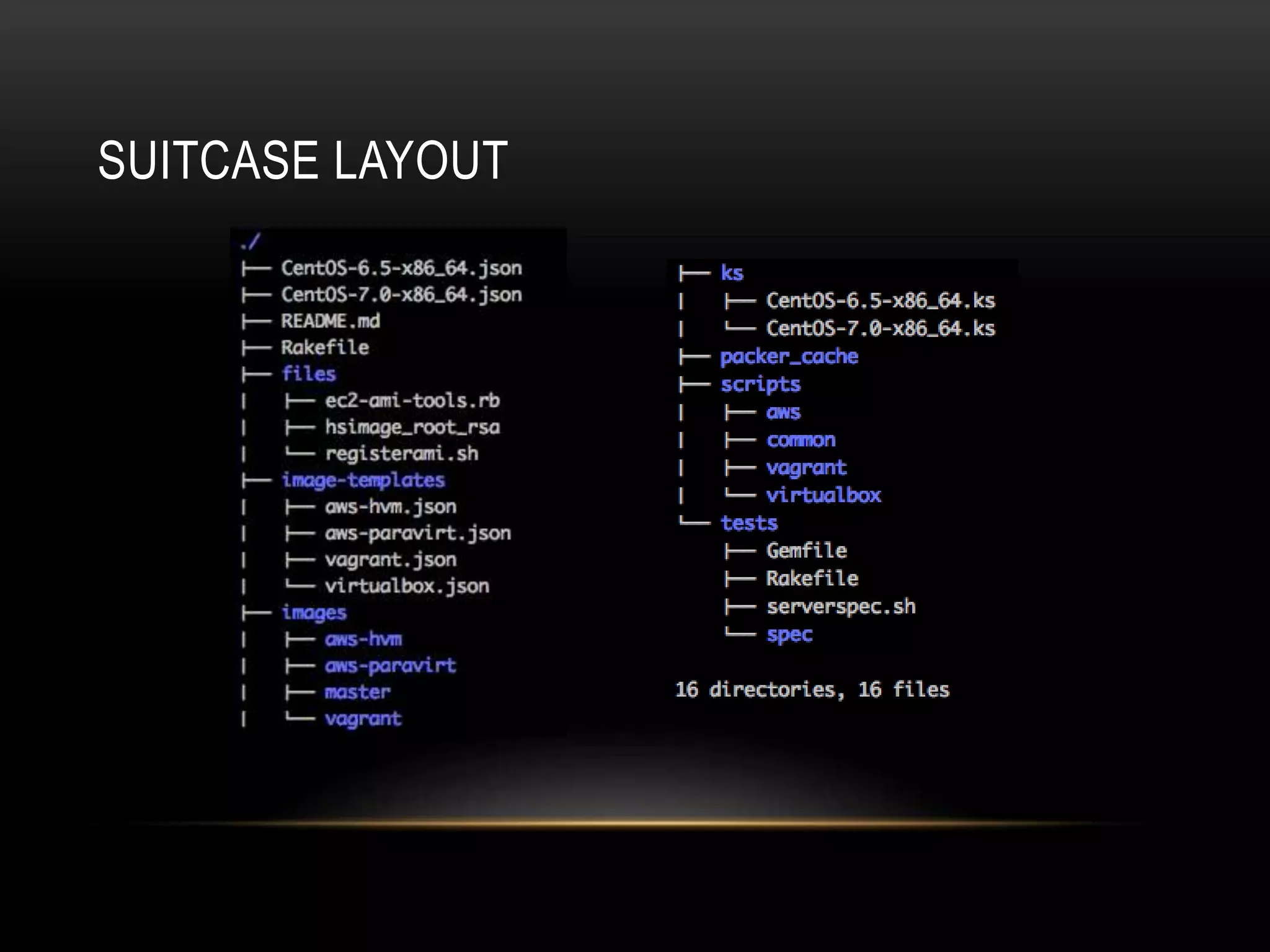
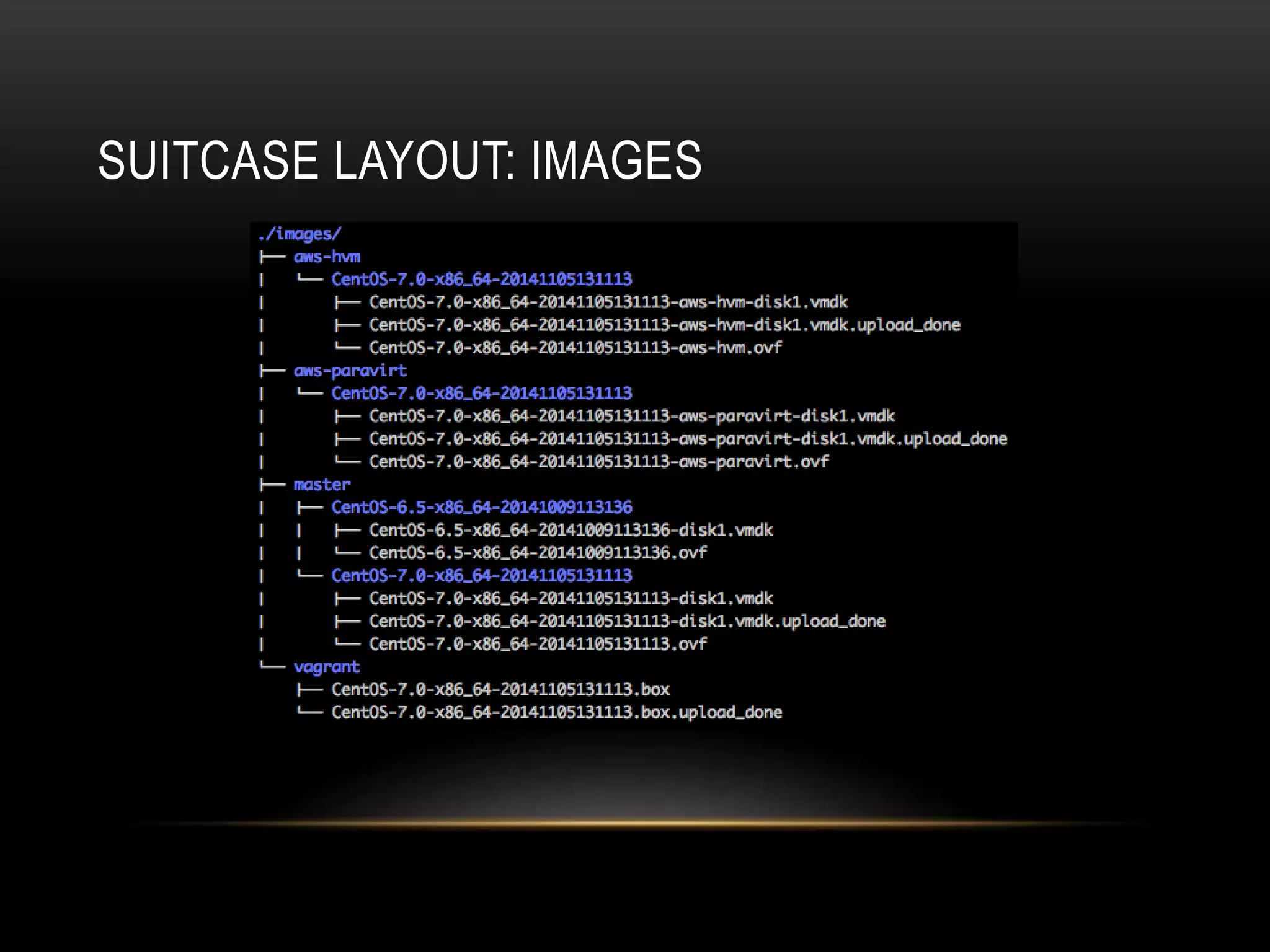
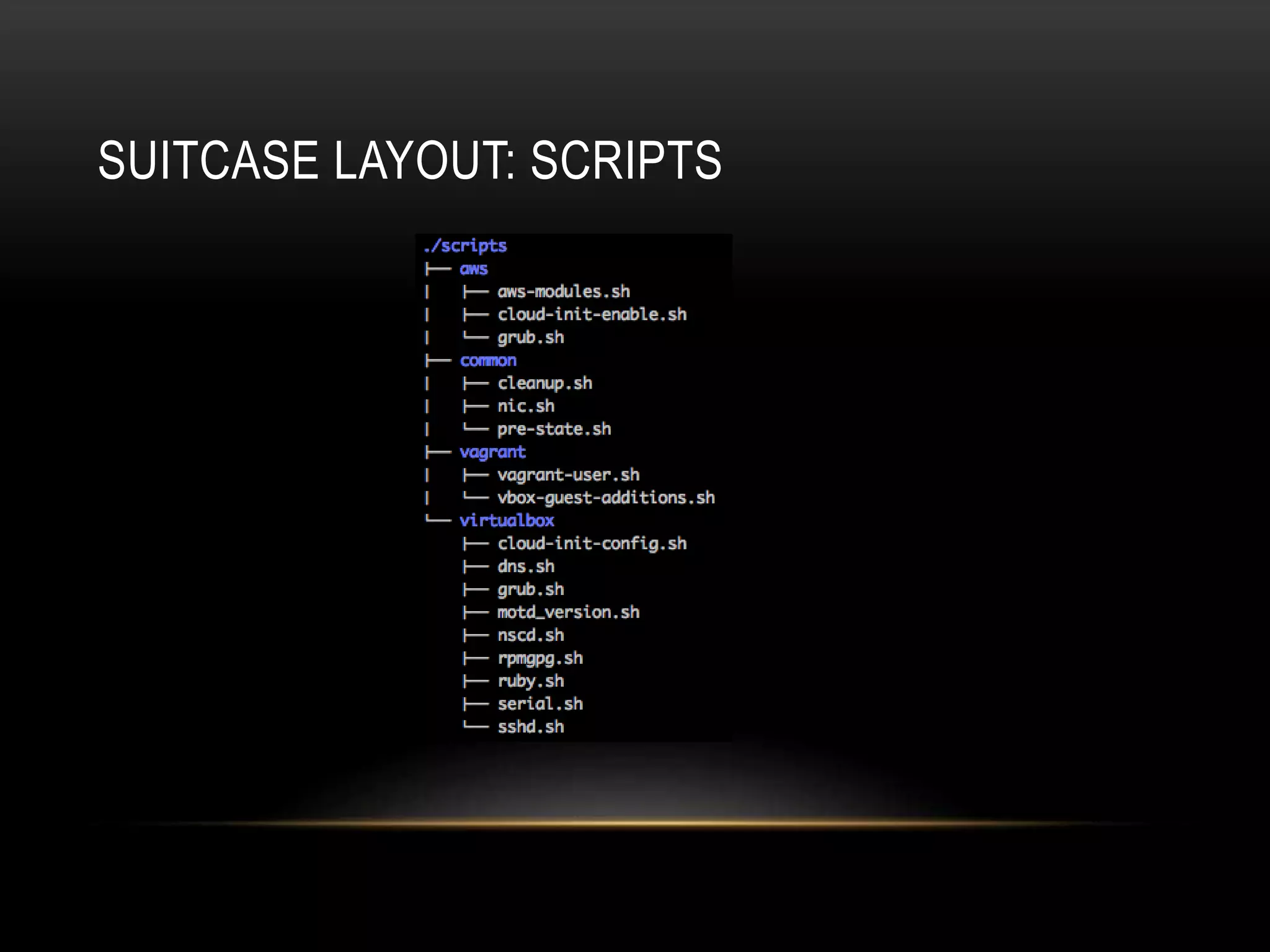
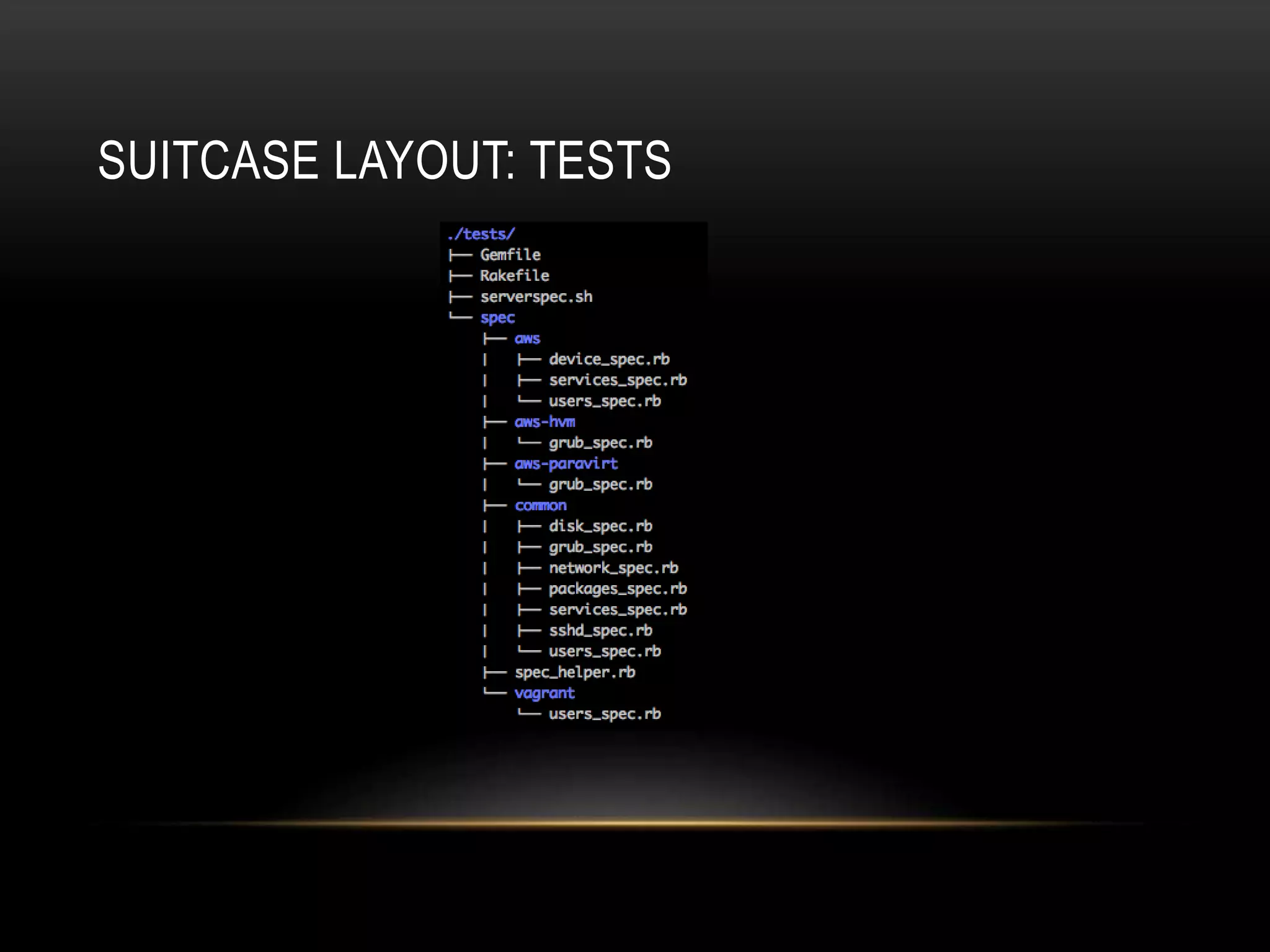
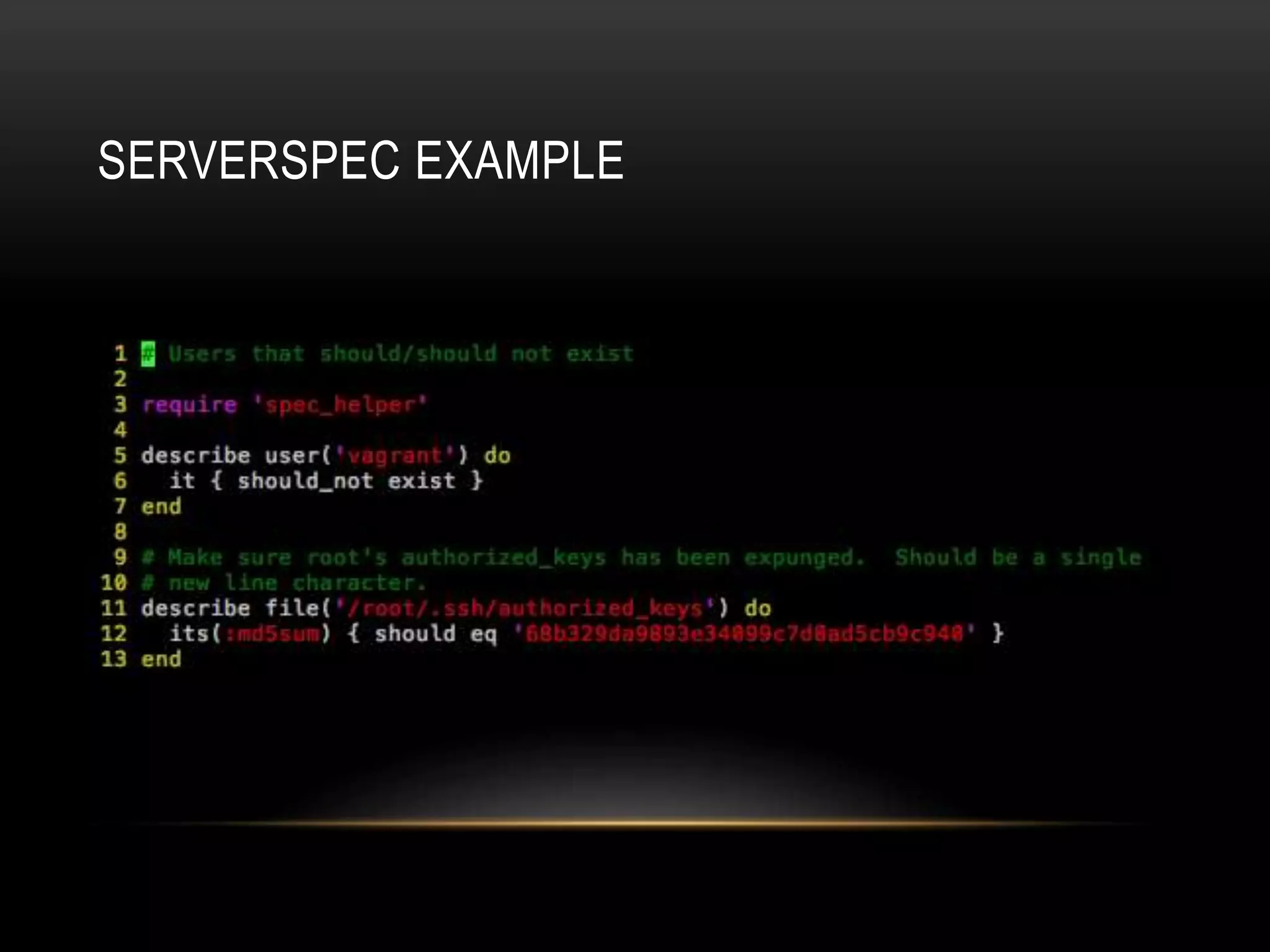
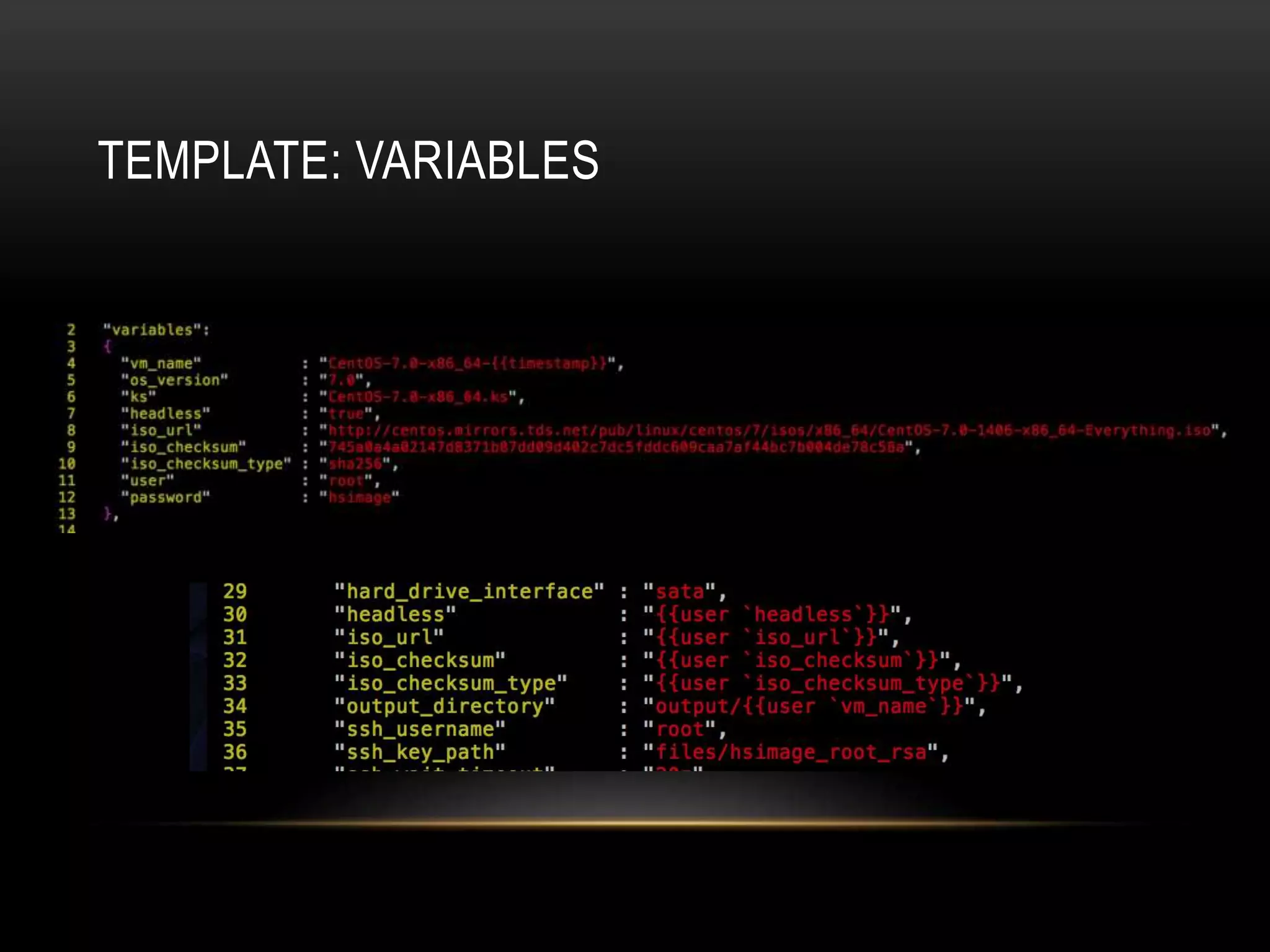
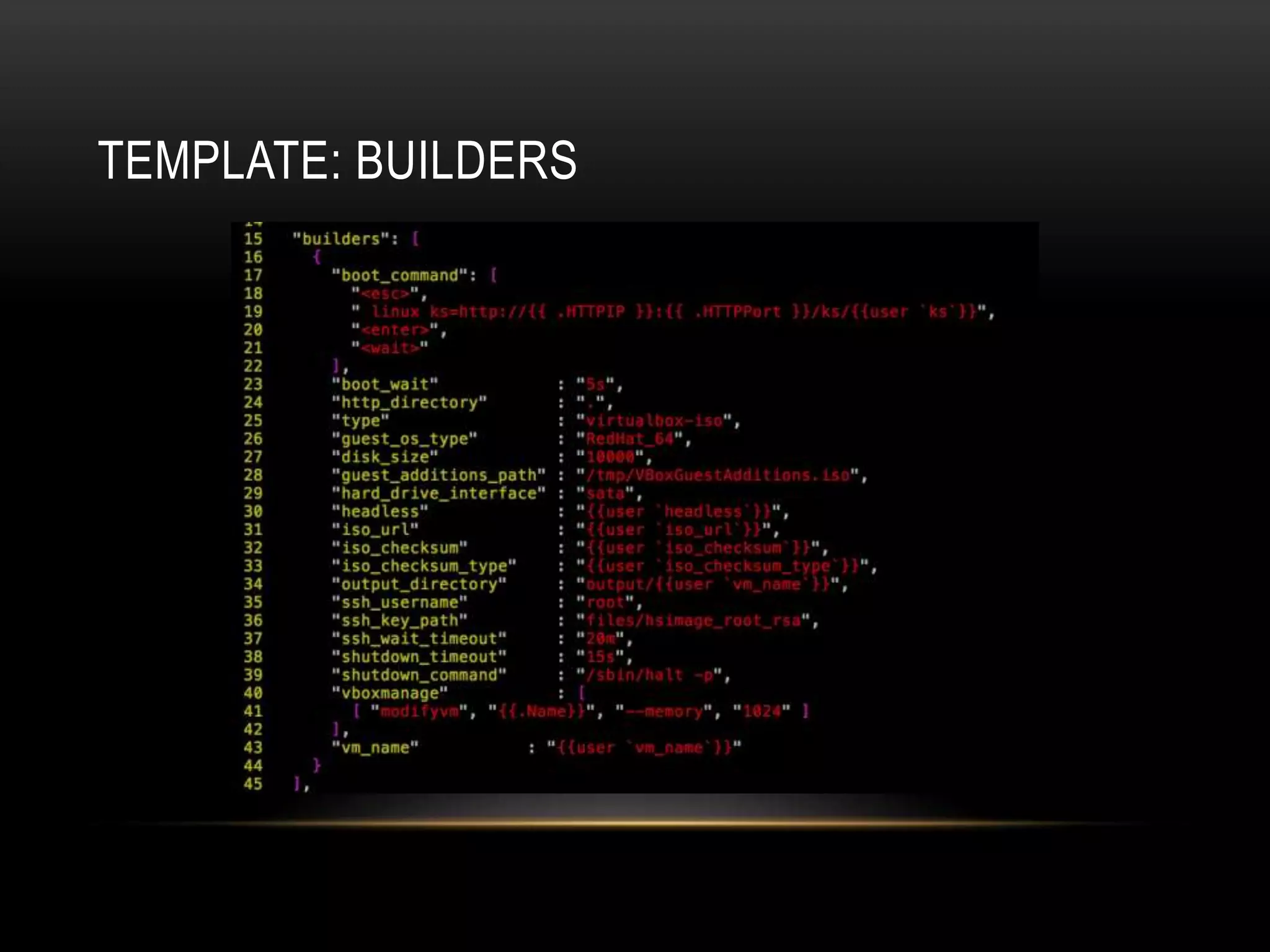
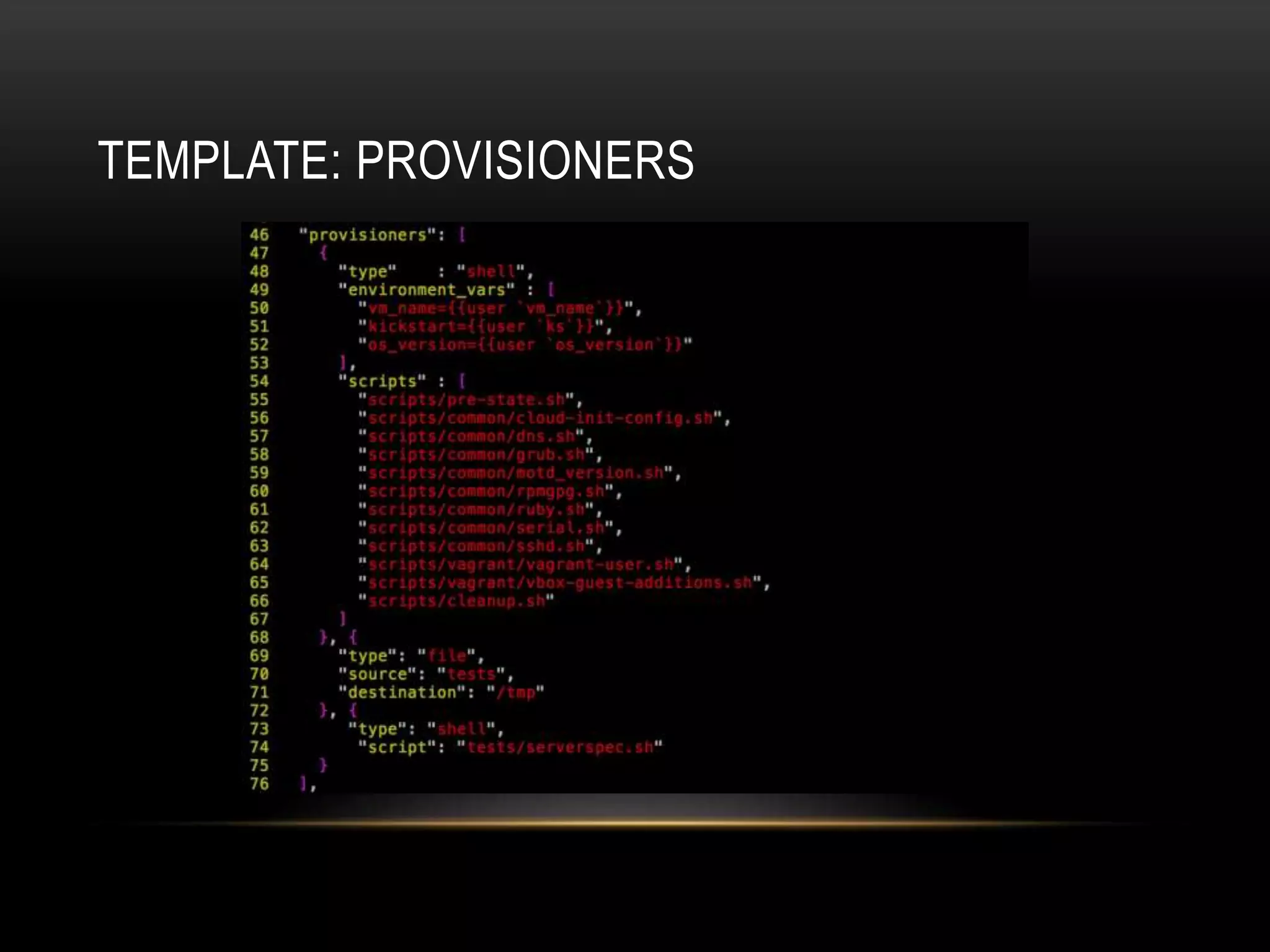
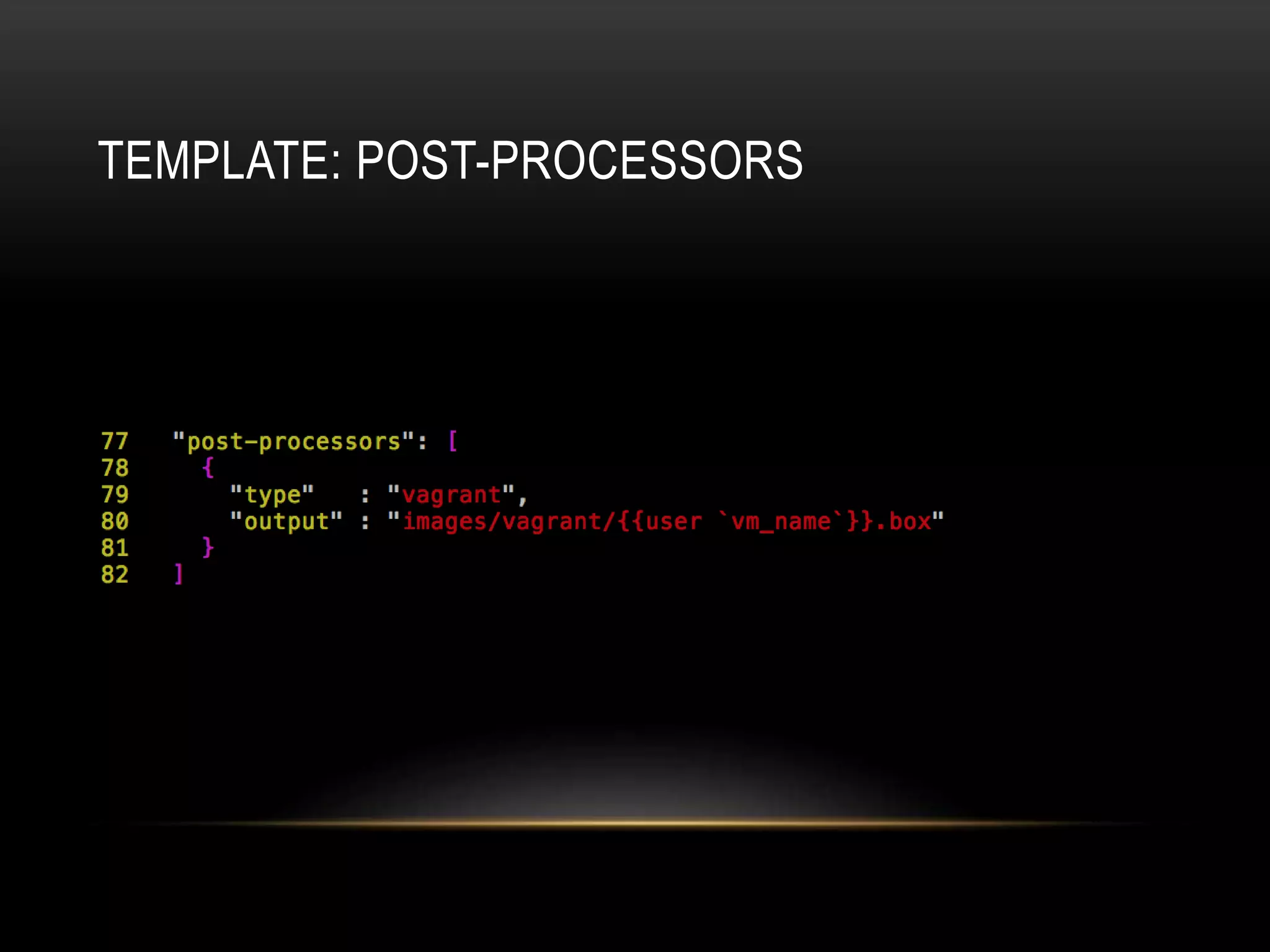
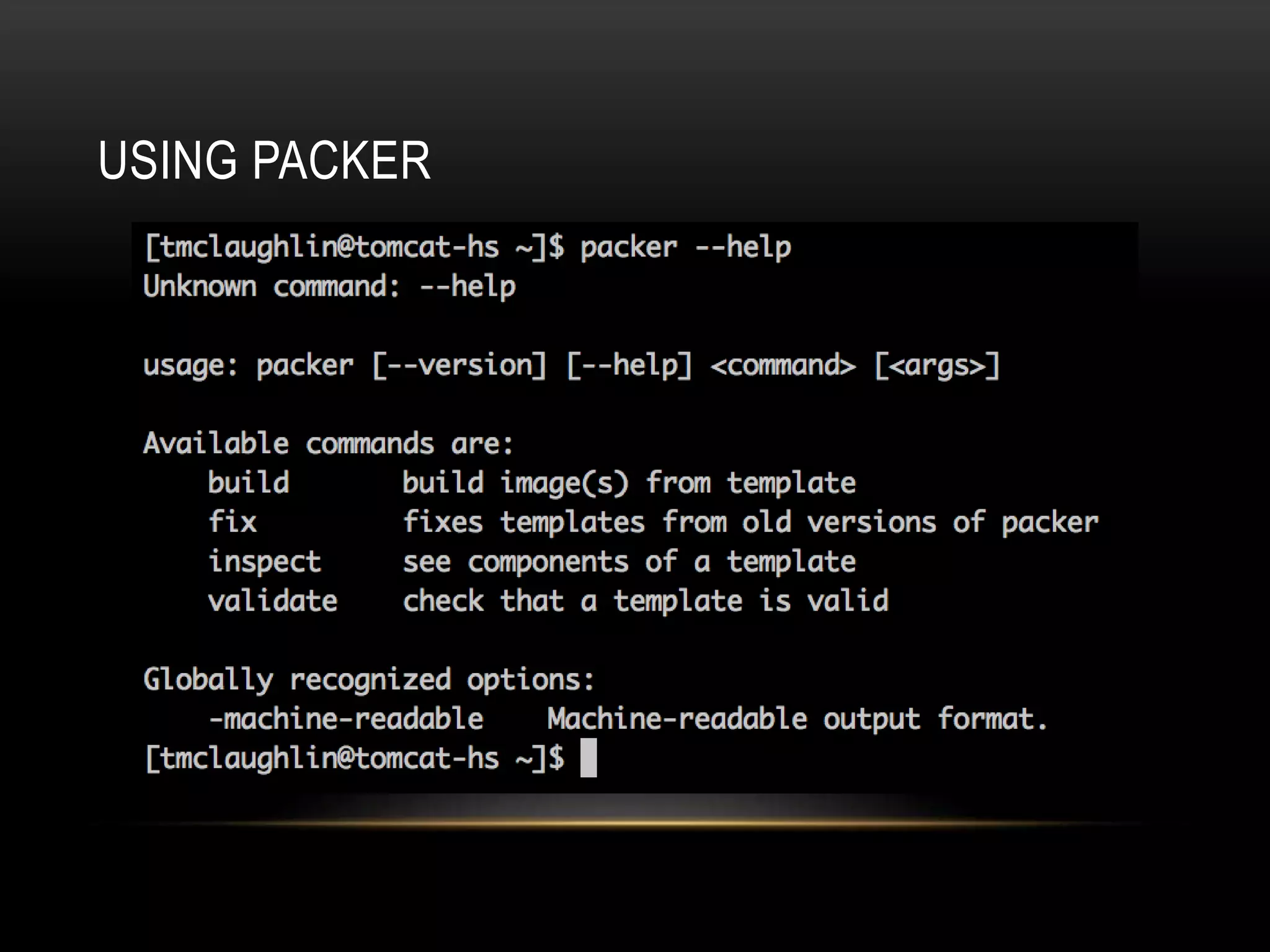
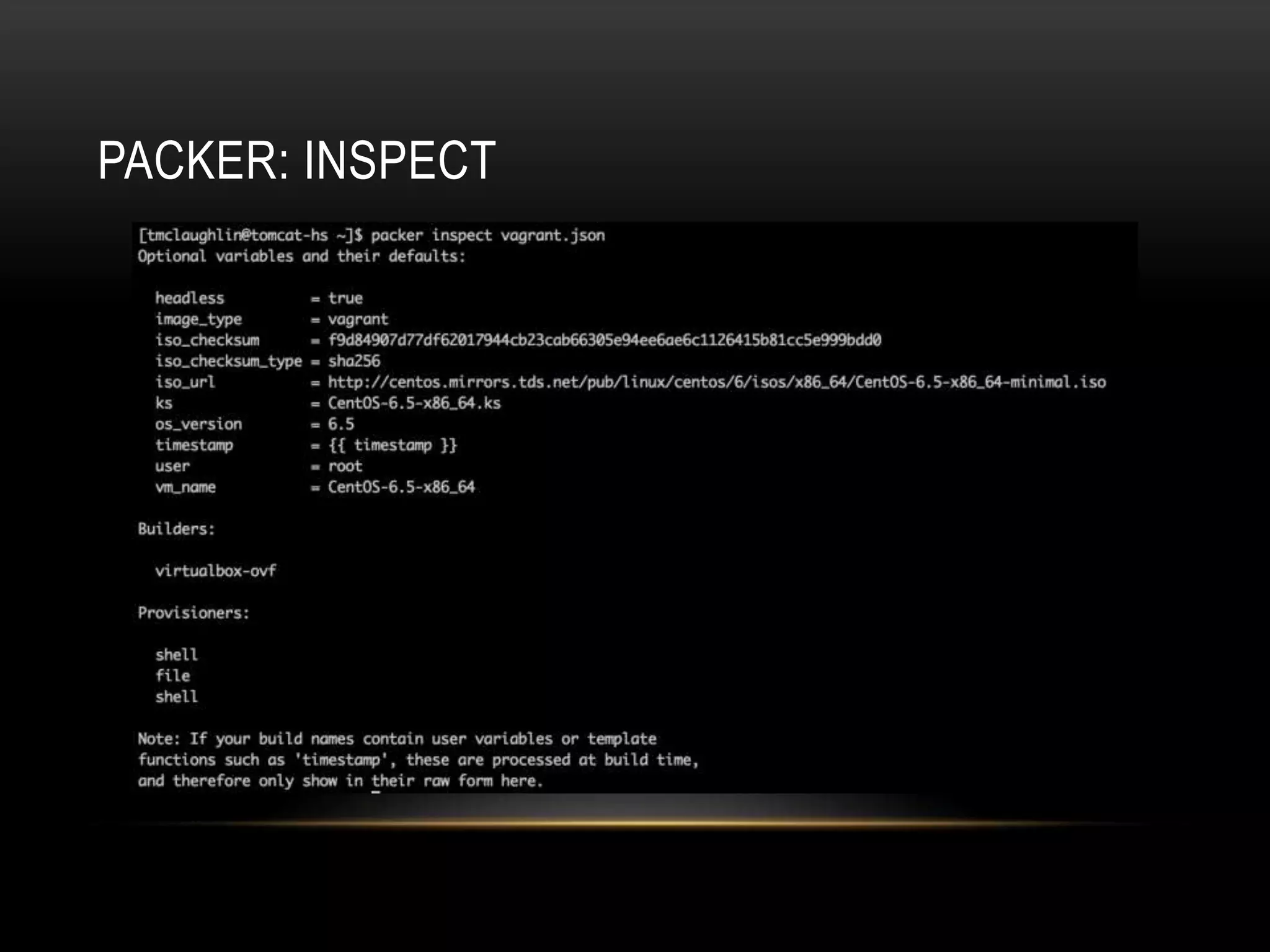
The document provides an introduction to Packer, a tool by HashiCorp for creating identical OS images across multiple platforms using a single description source. It highlights the limitations of Packer and introduces 'Suitcase', a framework designed to enhance the Packer image building process by managing builds through distinct stages and incorporating testing with Serverspec. The information also details example commands and configurations for building and registering images, emphasizing the improved workflow and reduced reliance on specific team members.







![TYING IT ALL TOGETHER WITH RAKE
• rake packer:build[<image>] os=<var-file> [timestamp=<YYYYMMDDhhmm>]
• Build given image
• Build the master image if it doesn’t already exist
• rake packer:upload[<image>] os=<var-file> [timestamp=<YYYYMMDDhhmm>]
• Uploads the artifact to S3 for safe keeping
• rake packer:register[<image>] os=<var-file> [timestamp=<YYYYMMDDhhmm>]
• Uploads and registers an AMI
• rake packer:clean[<image>] os=<var-file> [timestamp=<YYYYMMDDhhmm>]
• Cleans image artifacts from your workspace](https://image.slidesharecdn.com/onp0kp96qkijnh0xno1w-signature-e648026d2fba786a70e371c66511210a05100e4d25046def00ab9624e5ede82f-poli-141110134103-conversion-gate01/75/Introduction-to-Packer-and-Suitcase-A-Packer-based-OS-Image-Build-System-21-2048.jpg)

![SUITCASE EXAMPLES (CONT.)
• Build and register an AWS HVM image
• $ rake packer:register[awshvm] os=CentOS-7.0-x86_64](https://image.slidesharecdn.com/onp0kp96qkijnh0xno1w-signature-e648026d2fba786a70e371c66511210a05100e4d25046def00ab9624e5ede82f-poli-141110134103-conversion-gate01/75/Introduction-to-Packer-and-Suitcase-A-Packer-based-OS-Image-Build-System-23-2048.jpg)
![SUITCASE EXAMPLES (CONT.)
• Building an image from an existing master.
• $ rake packer:build[master] os=CentOS-7.0-x86_64
• (observe image timestamp from output. ex. 201410031904)
• $ rake packer:build[awshvm] os=CentOS-7.0-x86_64
timestamp=<timestamp>](https://image.slidesharecdn.com/onp0kp96qkijnh0xno1w-signature-e648026d2fba786a70e371c66511210a05100e4d25046def00ab9624e5ede82f-poli-141110134103-conversion-gate01/75/Introduction-to-Packer-and-Suitcase-A-Packer-based-OS-Image-Build-System-24-2048.jpg)