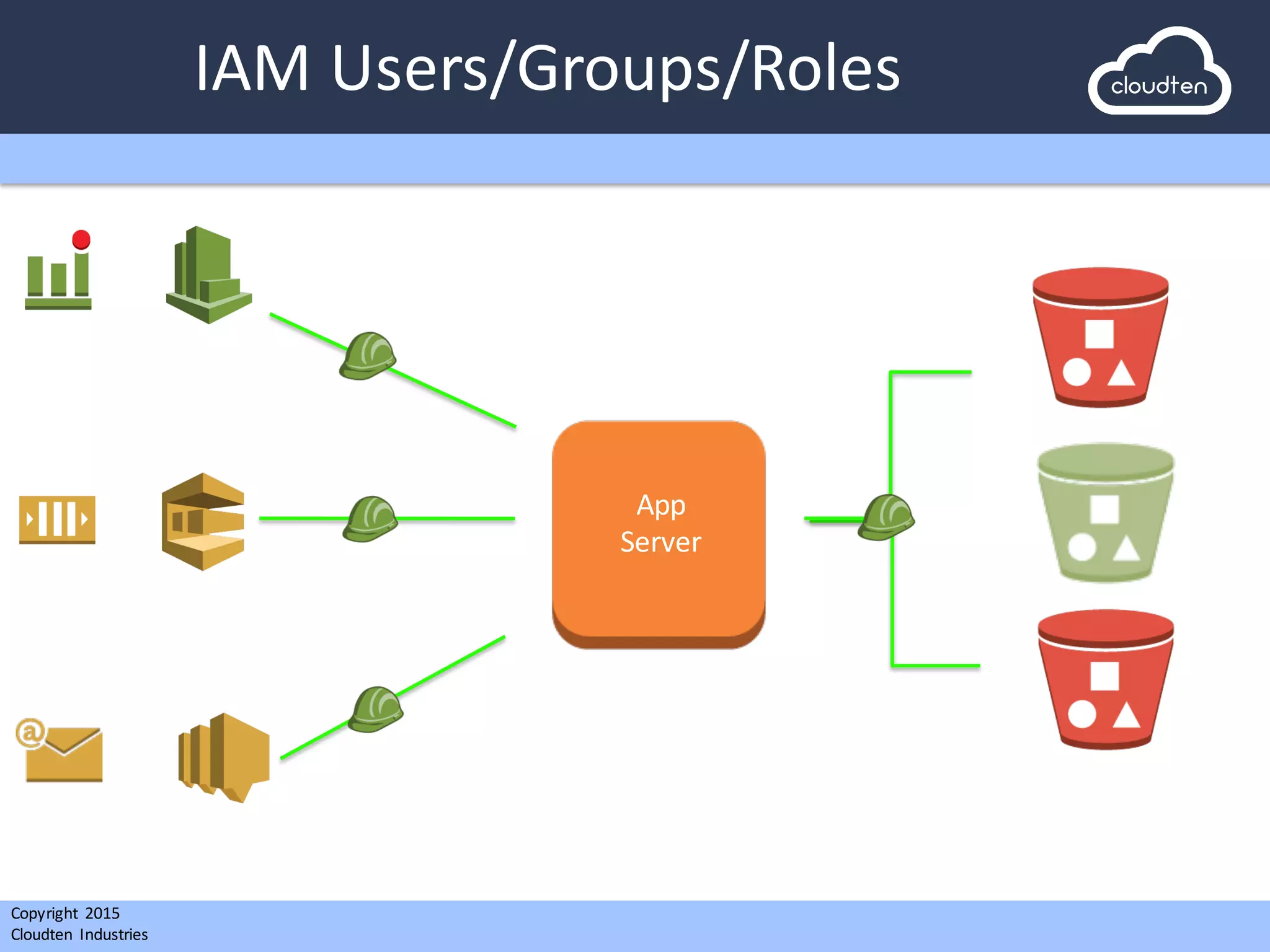
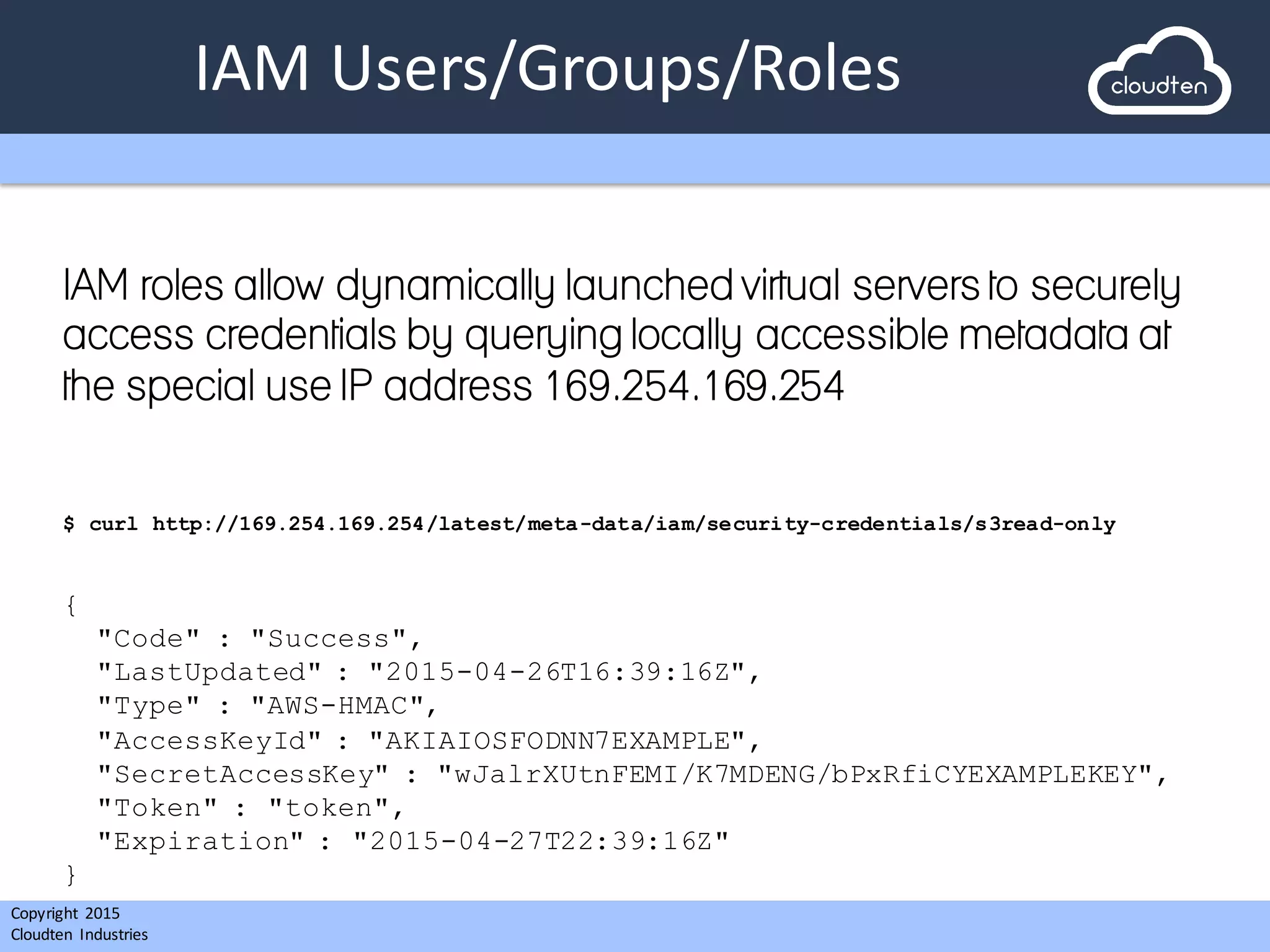
The document outlines a presentation by Cloudten Industries for a startup client intending to develop a mobile social media app with scalable architecture and robust security features. It details the technology stack, including the use of AWS for infrastructure management, automated server builds, and deployment strategies using Puppet for configuration management. The presentation also addresses challenges faced during the project, emphasizing Cloudten's expertise in cloud-based infrastructure and compliance with security best practices.





![Copyright 2015
Cloudten
Industries
EC2
Tagging
with
Facter
# Sets hostname
class common::hostname {
require aws
file { '/etc/hostname':
ensure => 'present',
owner => 'root',
group => 'root',
mode => '0644',
content => template('common/hostname.erb'),
notify => [ Exec['Set Hostname'],
Exec['Set EC2 Name-tag']
],
}
...
exec { 'Set Hostname':
command => "/bin/hostname -F /etc/hostname",
unless => "/usr/bin/test `hostname` = `/bin/cat /etc/hostname`",
refreshonly => 'true',
}
exec { 'Set EC2 Name-tag':
command => '/usr/local/bin/setec2nametag',
unless => '/usr/bin/test `/usr/local/bin/facter ec2_tag_Name` = `/bin/cat /etc/hostname`',
}
}](https://image.slidesharecdn.com/cloudten-masterless-puppet-no-lego-160115004308/75/Masterless-Puppet-Using-AWS-S3-Buckets-and-IAM-Roles-13-2048.jpg)
![Copyright 2015
Cloudten
Industries
Kernel
Tuning
# sysctl class
class common::sysctl {
file { '/etc/sysctl.conf':
source => 'puppet:///modules/common/sysctl.conf',
owner => 'root',
group => 'root',
mode => '0644',
notify => Exec['Refresh sysctl'],
}
exec { 'Refresh sysctl':
command => '/sbin/sysctl -q -p',
refreshonly => 'true',
}
}](https://image.slidesharecdn.com/cloudten-masterless-puppet-no-lego-160115004308/75/Masterless-Puppet-Using-AWS-S3-Buckets-and-IAM-Roles-14-2048.jpg)
![Copyright 2015
Cloudten
Industries
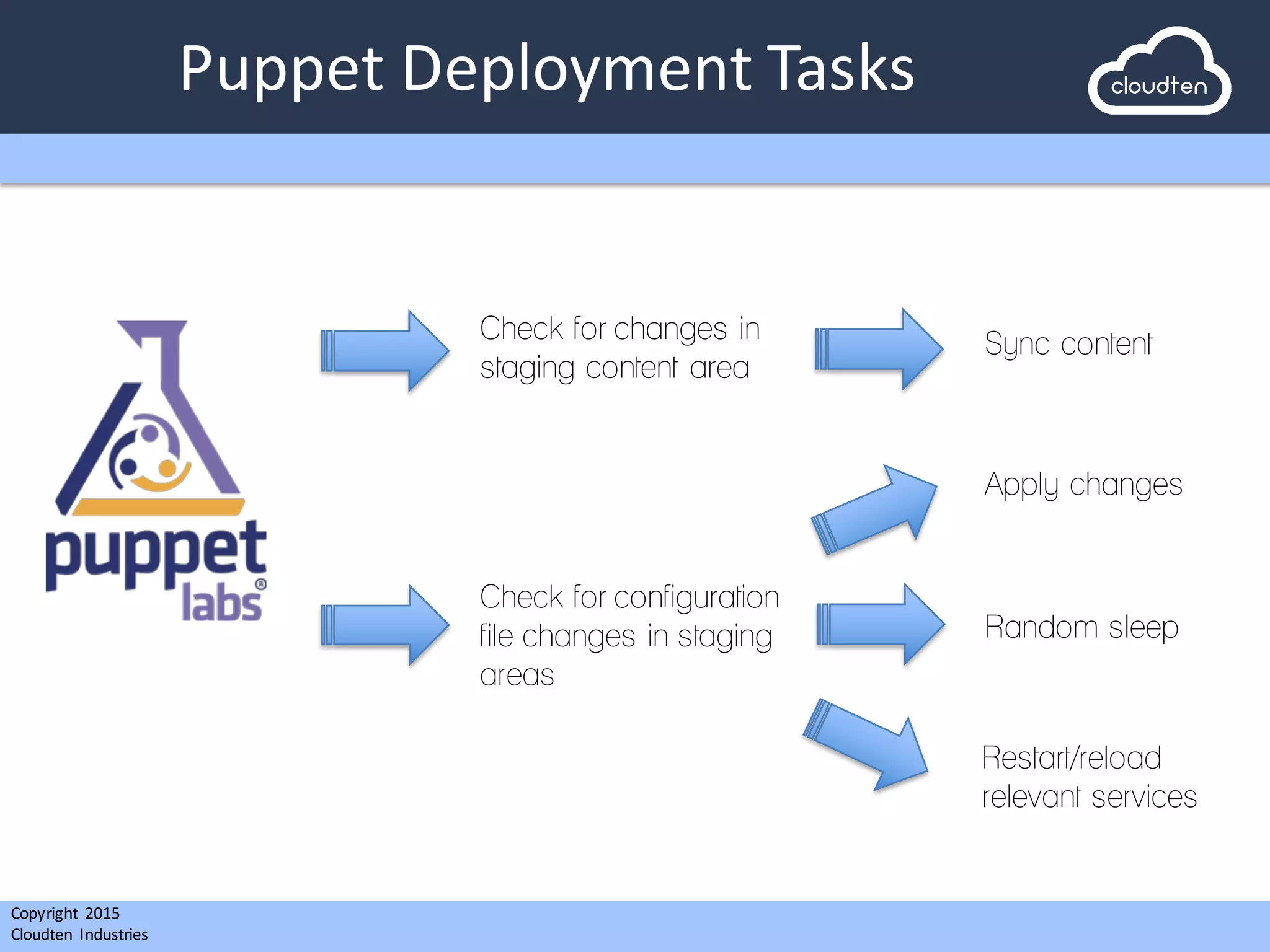
Puppet
Deployment
Tasks
# Conf dir file { '/etc/nginx/conf':
ensure => ‘directory’,
source => 'puppet:///modules/nginx/conf',
recurse => true
notify => Service[’nginx'],
require => Package[’nginx'],
}
# WAF rules
file { '/etc/nginx/waf/modsec_waf.rules':
source => 'puppet:///modules/nginx/waf/modsec_waf.rules',
...
notify => Service[’waf'],
require => Service[‘nginx’].
require => Package[’nginx'],
}](https://image.slidesharecdn.com/cloudten-masterless-puppet-no-lego-160115004308/75/Masterless-Puppet-Using-AWS-S3-Buckets-and-IAM-Roles-19-2048.jpg)
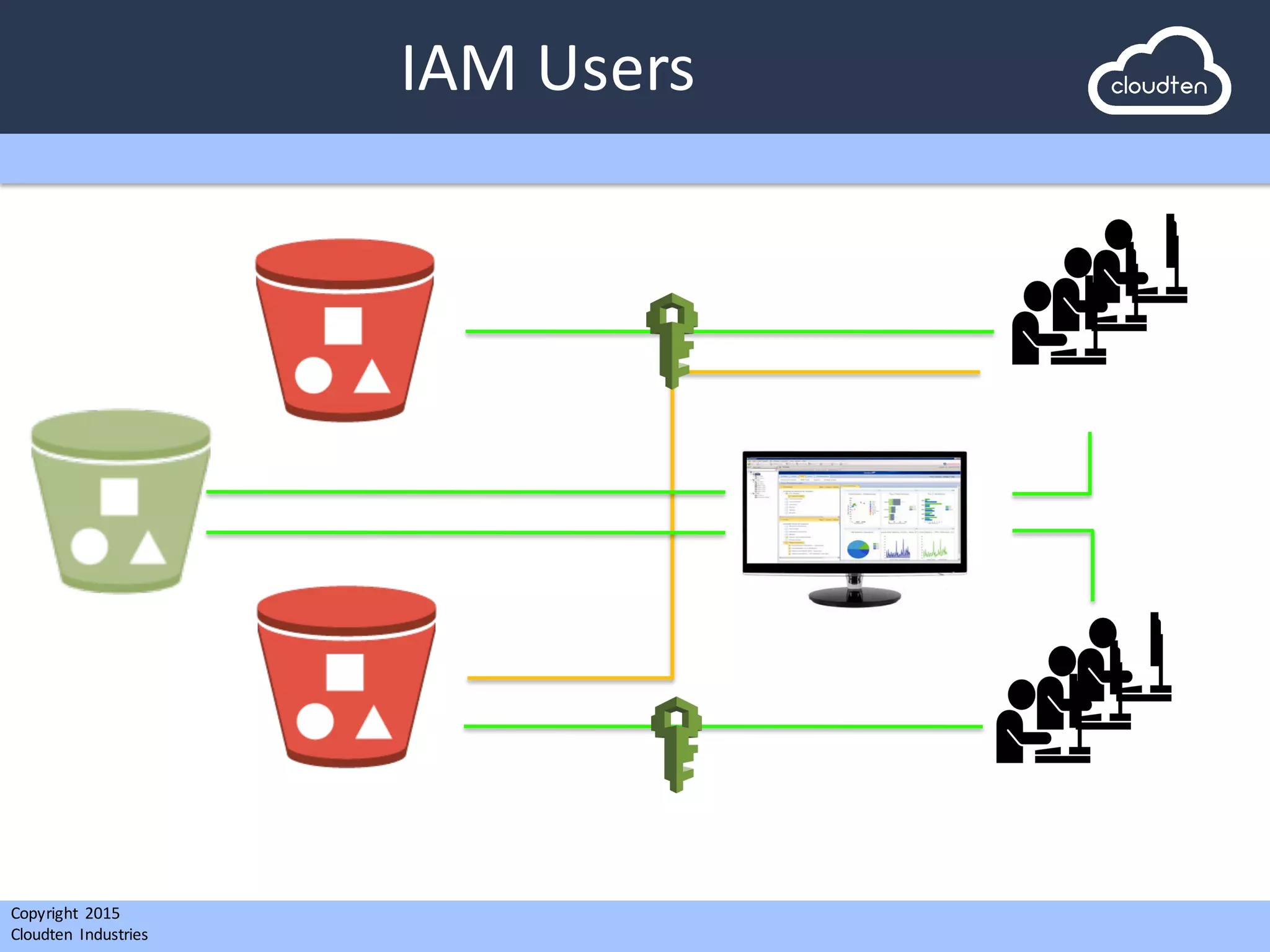
![Copyright 2015
Cloudten
Industries
IAM
Users
{
…
{
"Sid":
"AllowS3ListAccessToBucket",
"Effect":
"Allow",
"Principal":
{
"AWS":
"arn:aws:iam::123456789101:group/webdevs"
},
"Action":
"s3:ListBucket",
"Resource":
"arn:aws:s3:::fdsr-‐webcontent-‐puppet-‐prod"
},
{
"Sid":
"AllowS3AccessToModules",
"Effect":
"Allow",
"Principal":
{
"AWS":
[
"arn:aws:iam::123456789101:group/webdevs",
"arn:aws:iam::123456789101:role/iam-‐ec2-‐webrole",
]
},
"Action":
[
"s3:AbortMultipartUpload",
"s3:GetObjectAcl",
"s3:DeleteObject",
"s3:GetObject",
"s3:PutObjectAcl",
"s3:PutObject"
],
"Resource":
"arn:aws:s3:::fdsr-‐webcontent-‐puppet-‐prod/modules/webapp/files*"
}
]
}](https://image.slidesharecdn.com/cloudten-masterless-puppet-no-lego-160115004308/75/Masterless-Puppet-Using-AWS-S3-Buckets-and-IAM-Roles-22-2048.jpg)