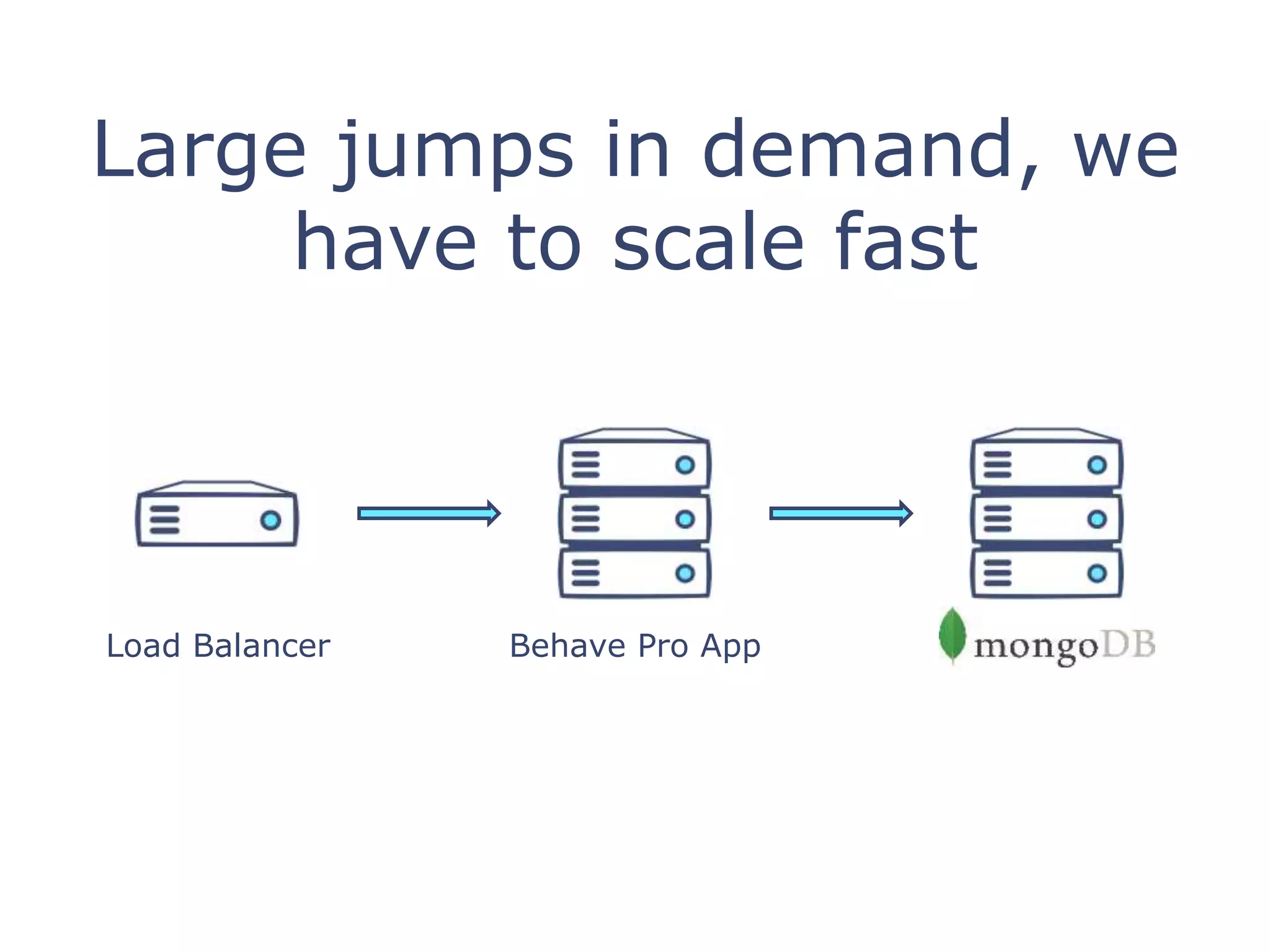
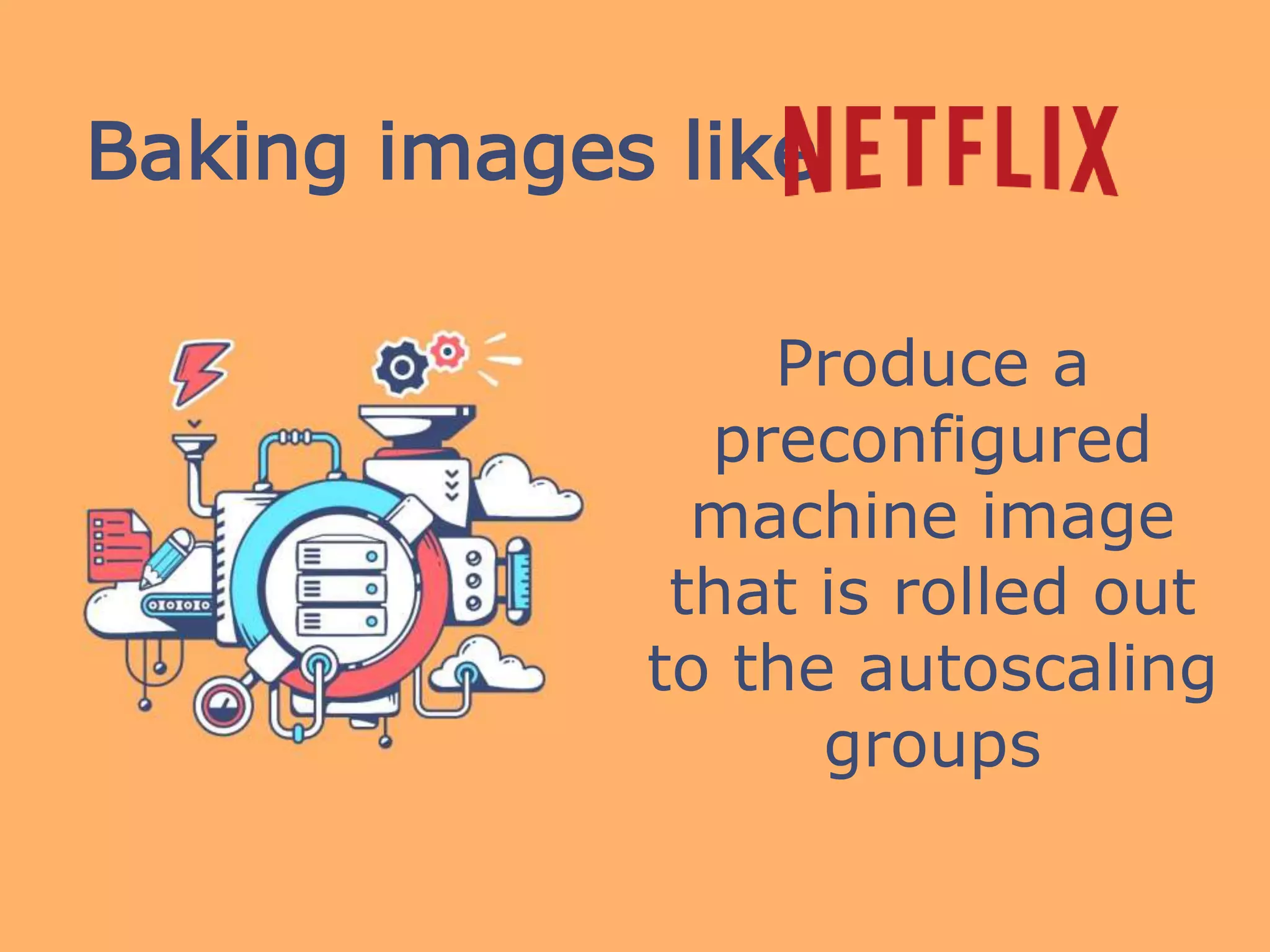
The document discusses using Packer and Puppet for cloud infrastructure provisioning, emphasizing the importance of creating preconfigured machine images for reliability and speed. It highlights how Packer can build identical images across platforms and suggests using Git for managing Puppet configurations and sensitive data through hiera-eyaml for encryption. Additionally, it outlines the process of integrating IAM roles for accessing sensitive keys from an S3 bucket during the build process.





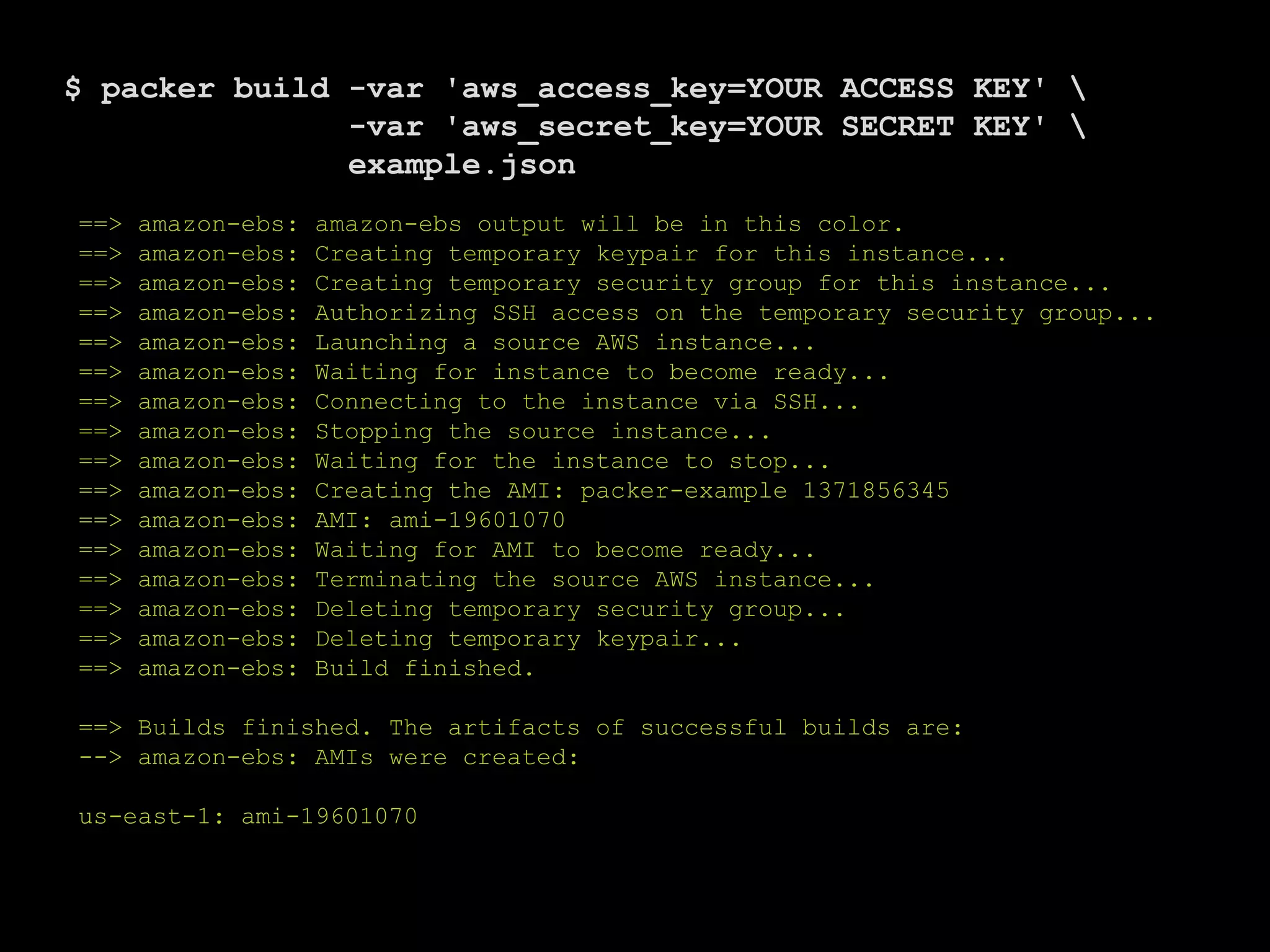
![PACKER.IO A HASHICORP PROJECT
packer.json
{
"variables": {
"aws_access_key": "",
"aws_secret_key": ""
},
"builders": [{
"type": "amazon-ebs",
"access_key": "{{user `aws_access_key`}}",
"secret_key": "{{user `aws_secret_key`}}",
"region": "us-east-1",
"source_ami": "ami-9eaa1cf6",
"instance_type": "t2.micro",
"ssh_username": "ubuntu",
"ami_name": "packer-example {{timestamp}}"
}]
}](https://image.slidesharecdn.com/bakinginthecloudwithpackerandpuppet-150522091746-lva1-app6892/75/Baking-in-the-cloud-with-packer-and-puppet-9-2048.jpg)
![Add some provisioners
{
"variables": {…},
"builders": […],
"provisioners": [
{
"type": "shell",
"script": "../common/install-puppet.sh"
},
…
{
"inline": [
"sudo apt-get purge --yes puppet",
"sudo apt-get autoremove --yes"
],
"type": "shell"
}
]
}](https://image.slidesharecdn.com/bakinginthecloudwithpackerandpuppet-150522091746-lva1-app6892/75/Baking-in-the-cloud-with-packer-and-puppet-11-2048.jpg)
![No need for a Puppet Master
"provisioners": [
…
{
"type": "puppet-masterless",
"hiera_config_path": "../puppet/hiera.yaml",
"manifest_file": "../puppet/manifests/default.pp",
"module_paths": [ "../puppet/modules" ]
},
…
]
Manifests, modules and hiera data can all be
stored in git and git submodules](https://image.slidesharecdn.com/bakinginthecloudwithpackerandpuppet-150522091746-lva1-app6892/75/Baking-in-the-cloud-with-packer-and-puppet-12-2048.jpg)

![hiera-eyaml
backend for Hiera that provides per-value
encryption of sensitive data within yaml files
---
duo-security-skey: ENC[PKCS7,MIIBmQYJKoZIh……Anc=]
behave_pro:
logentries_api_key: ENC[PKCS7,MIIBmQYJKoZIh……uW8=]
application_secret: ENC[PKCS7, MIIBmQYJKoZIh……FRg==]
common.eyaml](https://image.slidesharecdn.com/bakinginthecloudwithpackerandpuppet-150522091746-lva1-app6892/75/Baking-in-the-cloud-with-packer-and-puppet-14-2048.jpg)
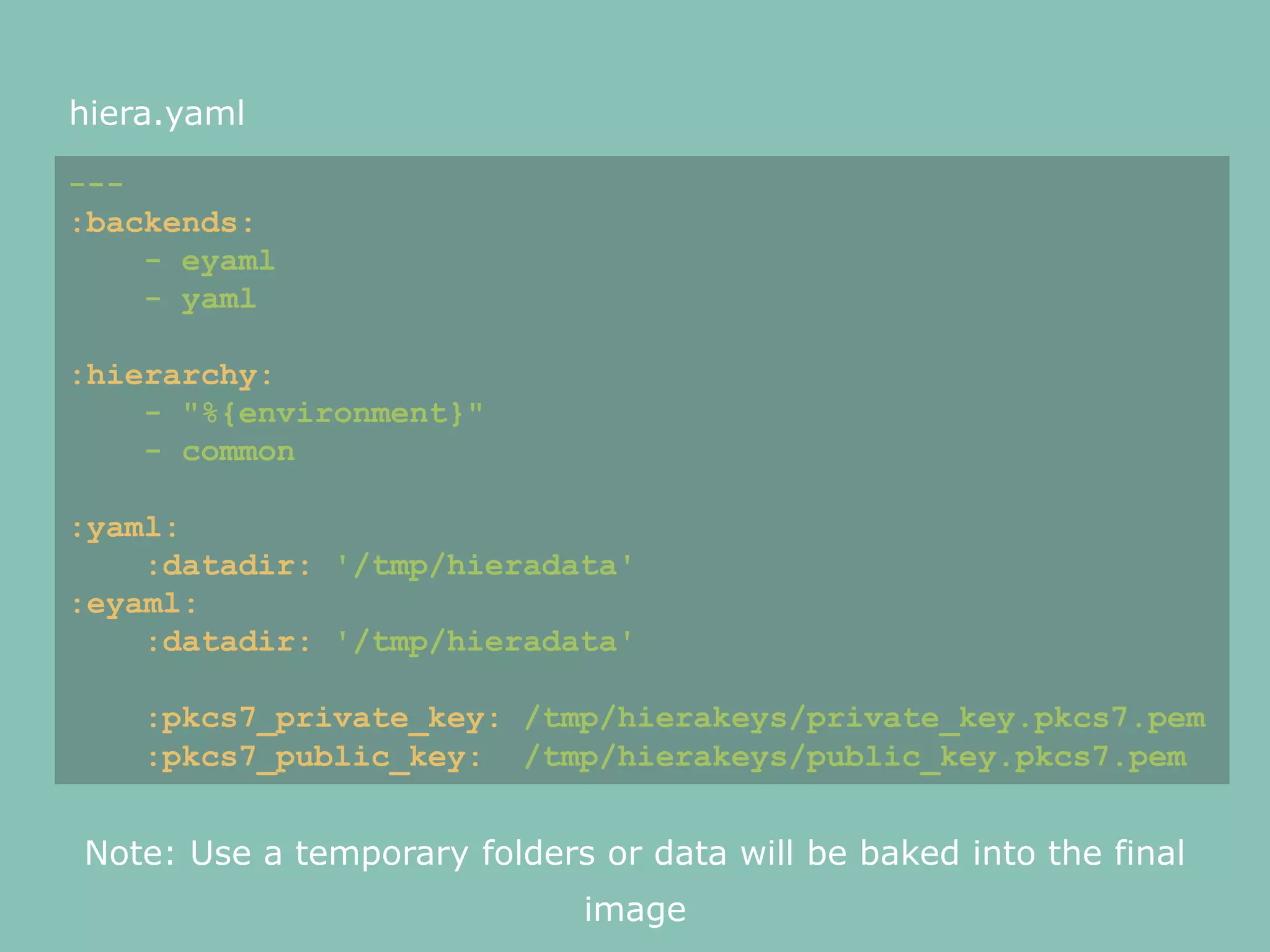

![The eyaml keys are stored in a private S3
bucket with access controlled by a IAM
Policy
Distributing the keys
to the Bakery
Use a IAM Role in Packer to access the S3
bucket
"builders": [{
"type": "amazon-ebs",
…
"iam_instance_profile" : "puppet-provisioner",
…
}]](https://image.slidesharecdn.com/bakinginthecloudwithpackerandpuppet-150522091746-lva1-app6892/75/Baking-in-the-cloud-with-packer-and-puppet-17-2048.jpg)
![IAM Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1425244502000",
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::puppet.behave.pro/*"
]
}
]
}](https://image.slidesharecdn.com/bakinginthecloudwithpackerandpuppet-150522091746-lva1-app6892/75/Baking-in-the-cloud-with-packer-and-puppet-18-2048.jpg)
![install-heira-key.sh
Download the keys to the EC2
Instance
sudo apt-get install --yes python-pip
sudo pip install s3cmd
s3cmd get s3://puppet.behave.pro/private_key.pkcs7.pem
/tmp/hierakeys/private_key.pkcs7.pem
s3cmd get s3://puppet.behave.pro/public_key.pkcs7.pem
/tmp/hierakeys/public_key.pkcs7.pem
"provisioners": [
{
"type": "shell",
"script": "../common/install-hiera-key.sh"
},
]
packer.json](https://image.slidesharecdn.com/bakinginthecloudwithpackerandpuppet-150522091746-lva1-app6892/75/Baking-in-the-cloud-with-packer-and-puppet-19-2048.jpg)

