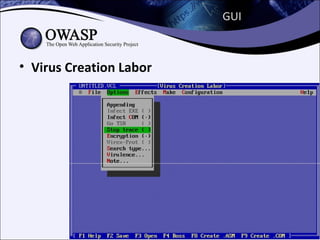
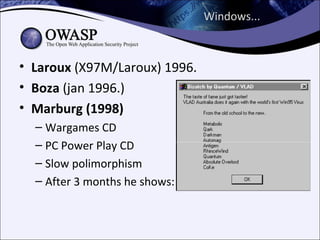
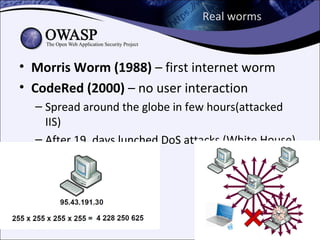
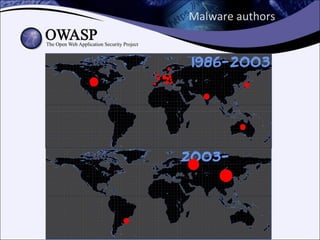
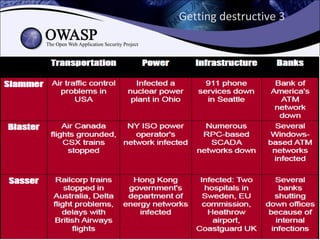
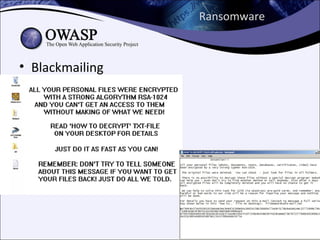
The document explores the history and evolution of malware, detailing its various forms and notable examples from the first known virus, Brain, in 1986 to sophisticated threats like Stuxnet in 2010. It includes discussions on malware types such as viruses, worms, Trojans, and rootkits, as well as analysis techniques for understanding and combating these threats. The document emphasizes the ongoing challenges in cybersecurity and the methods used to track and reverse-engineer malicious code.