This document summarizes experiences from a proof of concept (PoC) federated STUN/TURN service. Key points include:
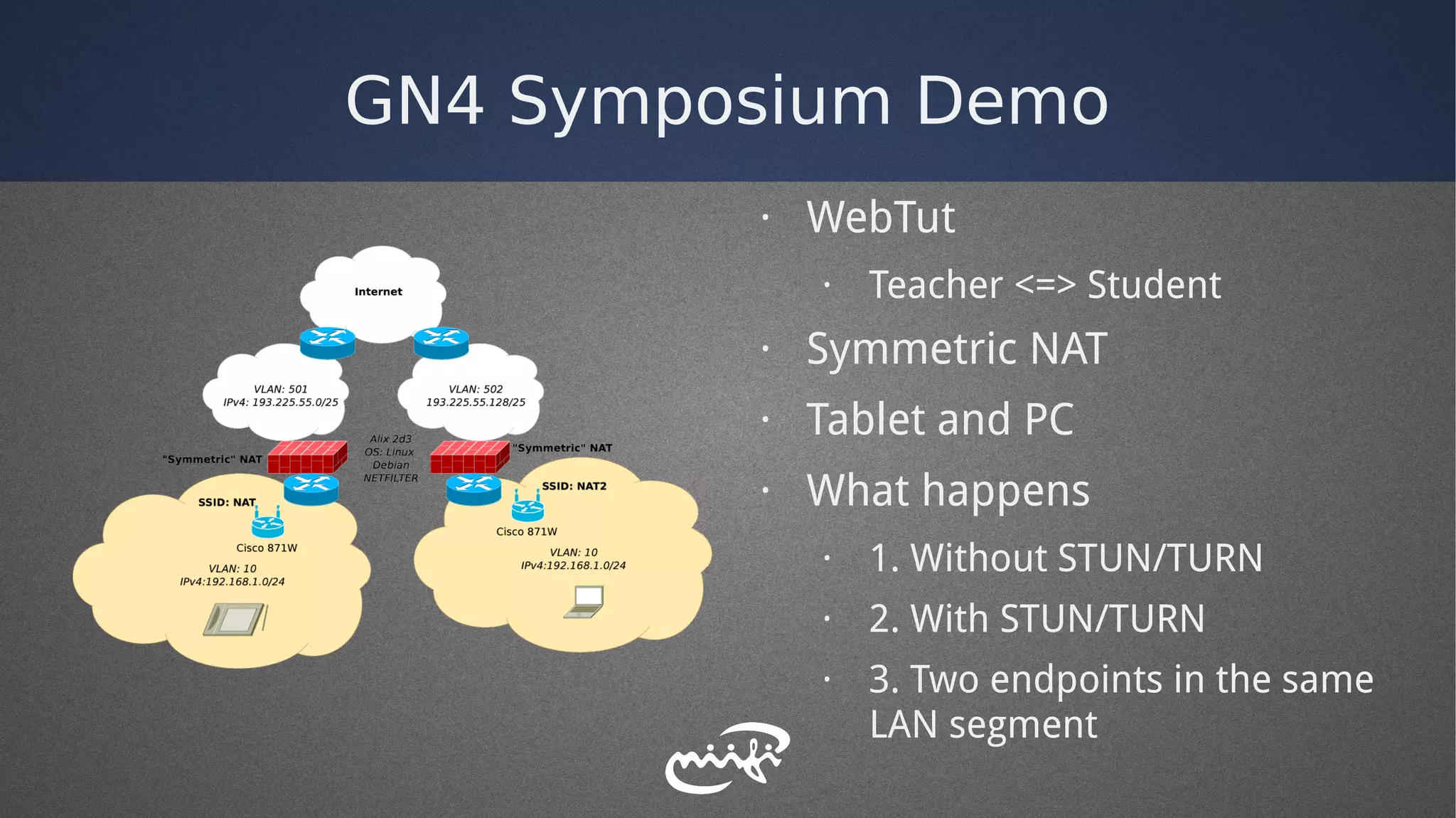
- The PoC used STUN, TURN, and ICE to enable real-time communications across firewalls and NATs.
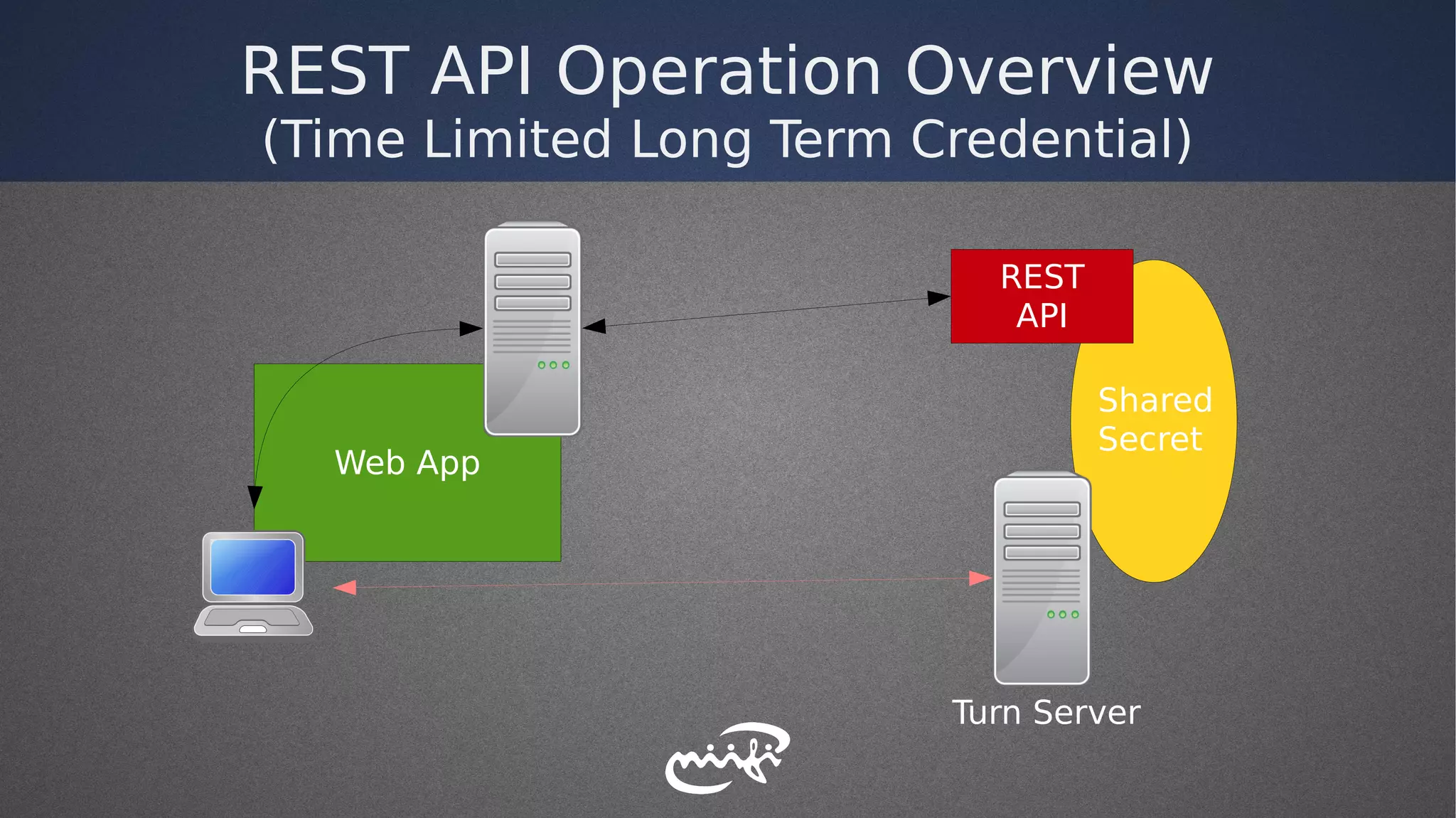
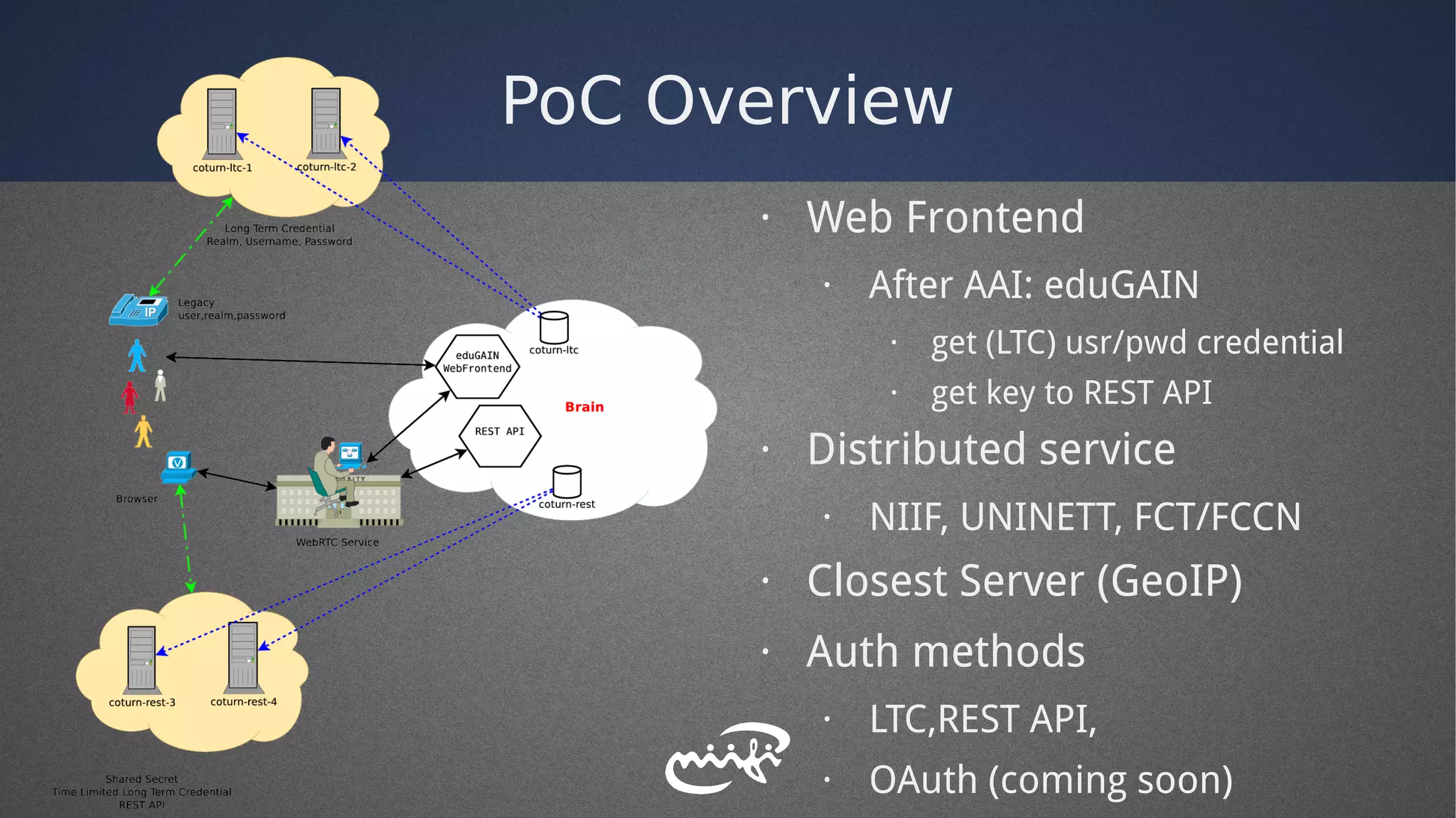
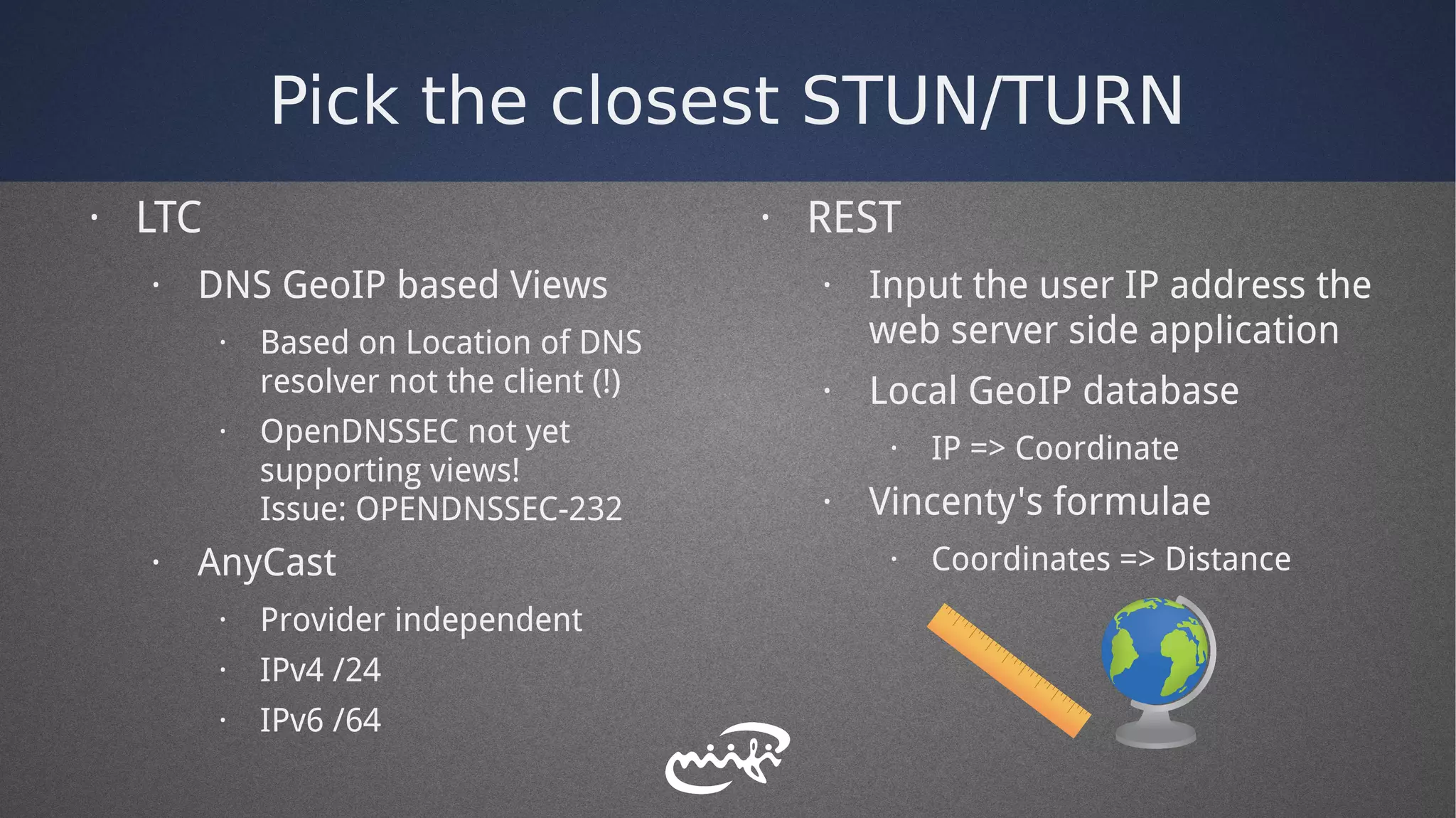
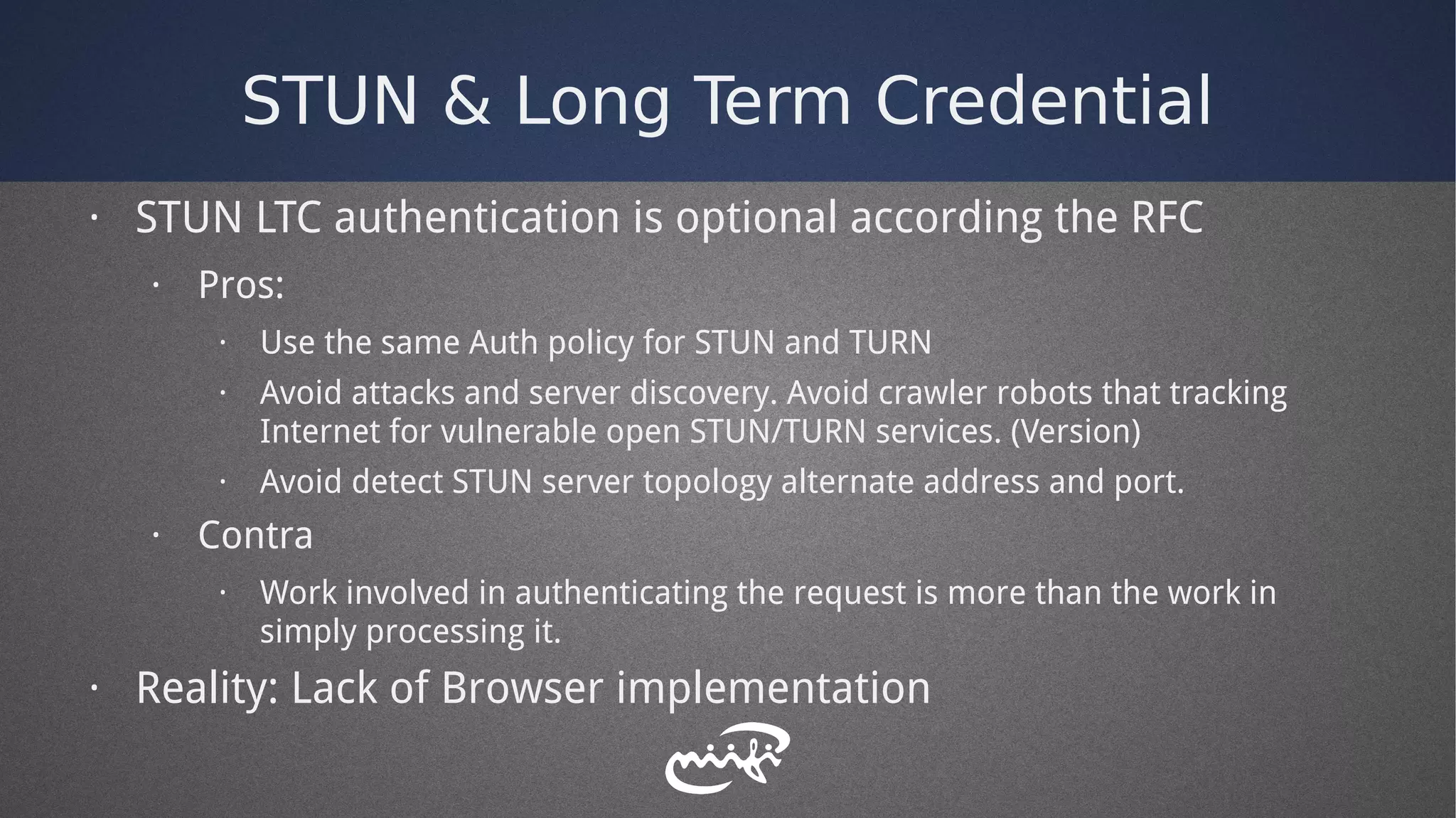
- It explored different authentication methods like long-term credentials, REST APIs, and OAuth.
- The distributed service was deployed across multiple research networks in Europe.
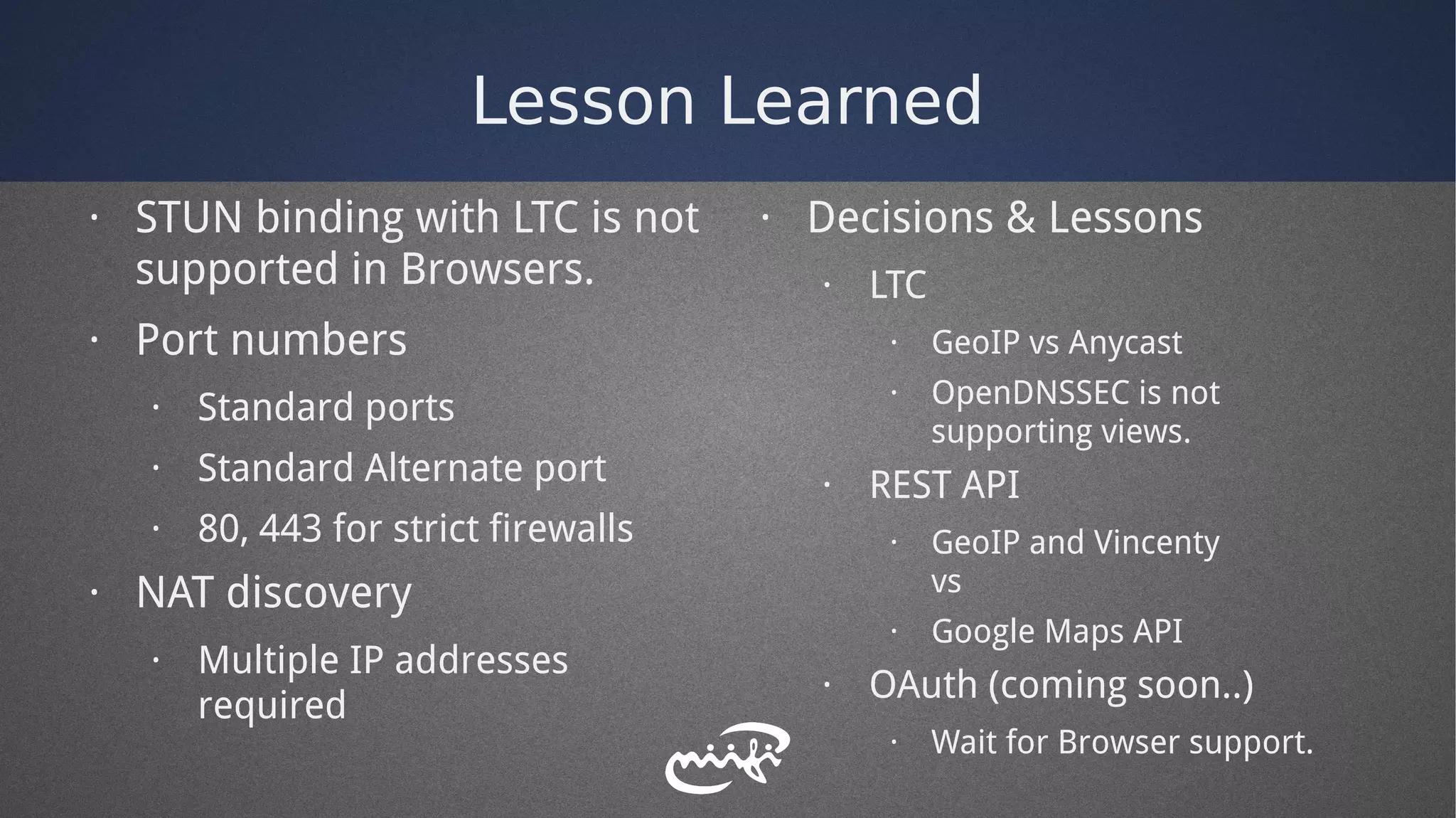
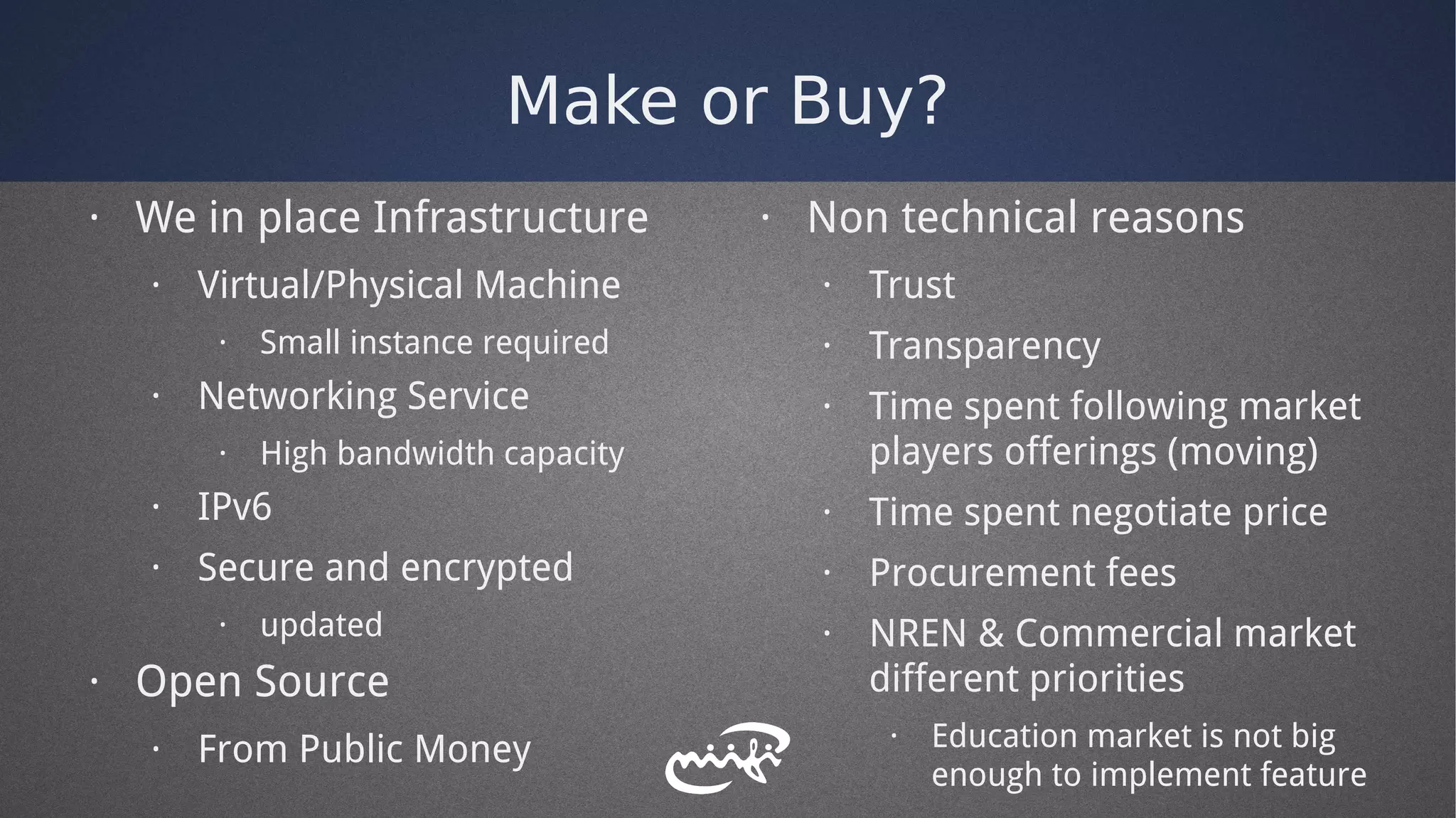
- Lessons learned from the PoC included designing for security, using open source components, and supporting multiple authentication standards.








































![STUN & LTC chrome
· Log
[1:12:0418/145114:ERROR:stunport.cc(79)] Binding error response: class=4 number=1
reason='Unauthorized'
[1:12:0418/145114:ERROR:stunport.cc(79)] Binding error response: class=4 number=1
reason='Unauthorized'
[1:12:0418/145114:ERROR:stunport.cc(79)] Binding error response: class=4 number=1
reason='Unauthorized'
[1:12:0418/145114:ERROR:stunport.cc(79)] Binding error response: class=4 number=1
reason='Unauthorized'
[1:12:0418/145114:ERROR:stunport.cc(79)] Binding error response: class=4 number=1
reason='Unauthorized'
· Turned out from source
· Not handled of STUN auth challenge in stunport.cc](https://image.slidesharecdn.com/stunturnpocpilot-160503092328/75/Stun-turn-poc_pilot-49-2048.jpg)



![Built in STUN
· Chrome
· stun.l.google.com:19302
· Firefox
· media.peerconnection.default_iceservers;[]
· media.peerconnection.ice.tcp;false
· stun.services.mozilla.com
· Default stun server removed
from ver 41
· Bug: 1167922, 1143827
· No Service Agreement about
service long term availability
· It is up to Browser vendor
· Built-in STUN SLA is not well
defined](https://image.slidesharecdn.com/stunturnpocpilot-160503092328/75/Stun-turn-poc_pilot-53-2048.jpg)



![Summary
· ICE if possible provides E2E communication (lowest latency)
· Standard based NAT Firewall Traversal and smooth IPv6 transition
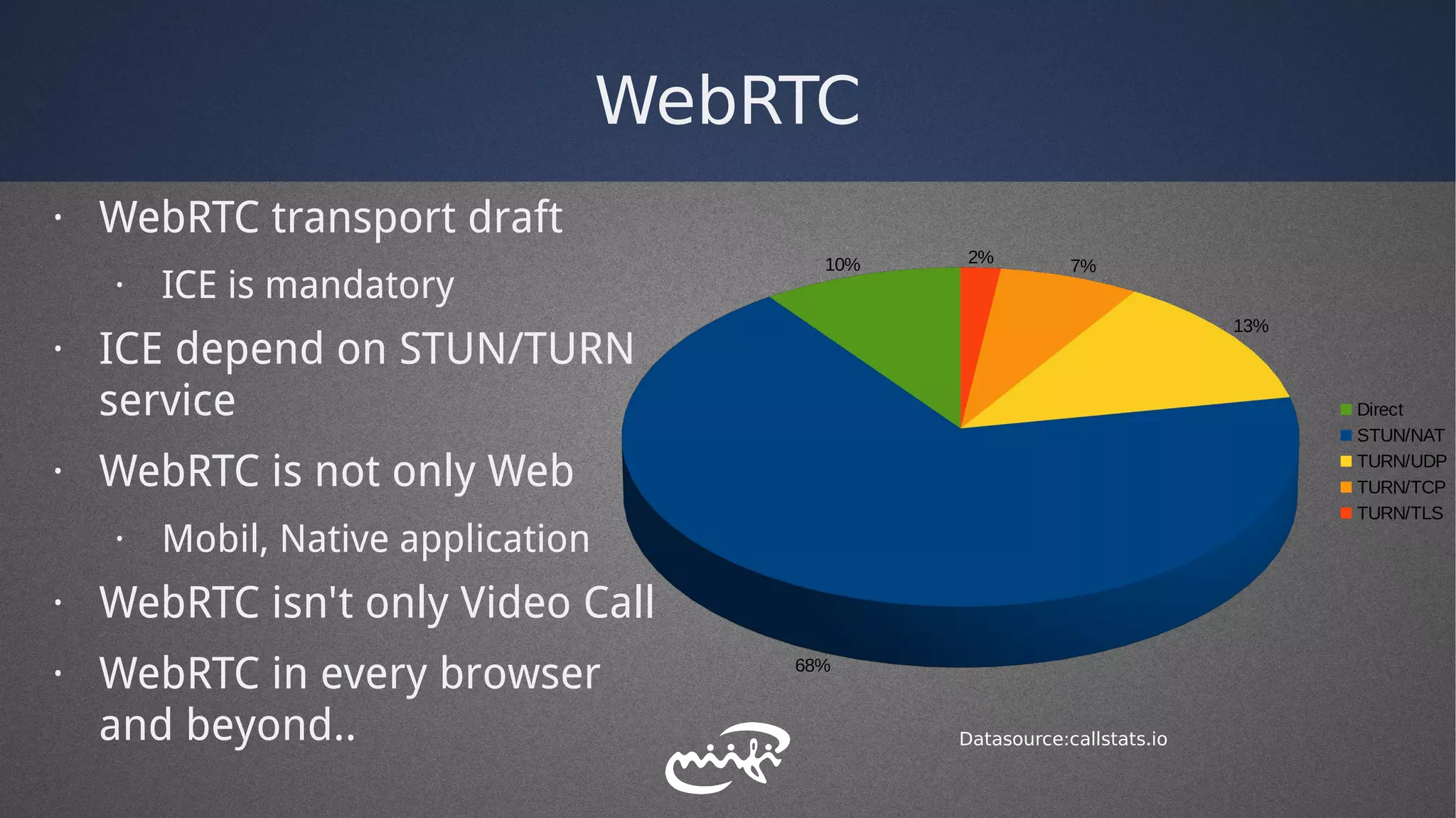
· According WebRTC transport draft ICE is MUST.
· “ ICE [RFC5245] MUST be supported.”
· ICE needs STUN/TURN server infrastructure.
· A GÉANT4 PoC service is up and running. Next step? Pilot...
· „Leading edge” collaboration technologies serving the NREN
community communications needs.](https://image.slidesharecdn.com/stunturnpocpilot-160503092328/75/Stun-turn-poc_pilot-60-2048.jpg)
