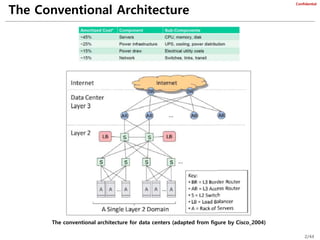
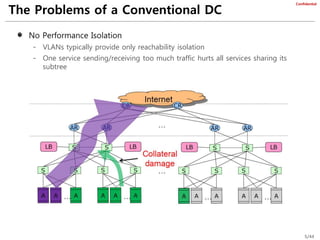
The document provides an overview of several data center network architectures: Monsoon, VL2, SEATTLE, PortLand, and TRILL. Monsoon proposes a large layer 2 domain with a Clos topology and uses MAC-in-MAC encapsulation and load balancing to improve scalability. VL2 also uses a Clos topology with flat addressing, load balancing, and an end host directory for address resolution. SEATTLE employs flat addressing, automated host discovery, and hash-based address resolution. PortLand uses a tree topology with encoded switch positions and a fabric manager for address mapping. TRILL standardizes encapsulation and IS-IS routing between routing bridges.