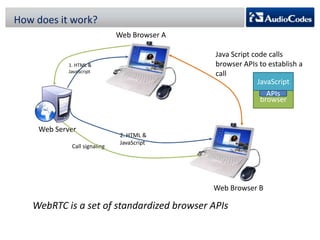
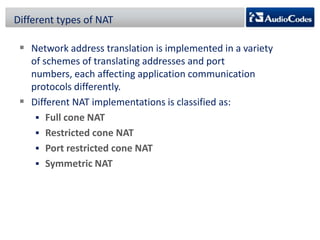
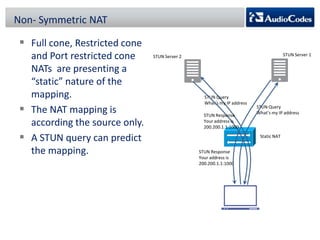
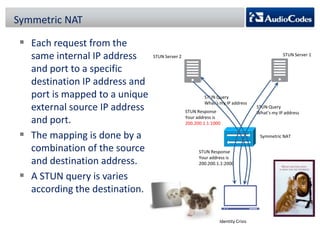
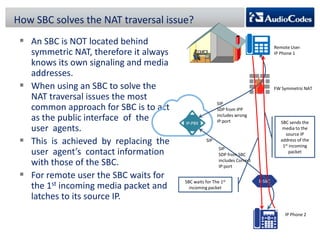
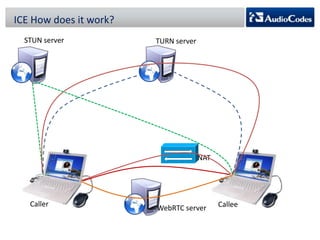
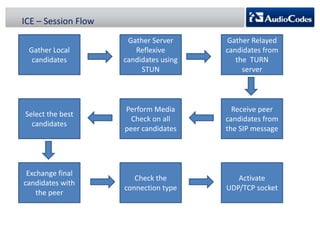
WebRTC is a project that enables real-time communication in web browsers using JavaScript APIs, allowing developers to implement voice calls, video chats, and file sharing without plugins. The document discusses the challenges of NAT traversal, particularly with symmetric NAT, and explains how tools like STUN and SBC (Session Border Controller) can assist in establishing reliable connections. Additionally, the ICE (Interactive Connectivity Establishment) framework is outlined for resolving connectivity during signaling by gathering various candidates for media communication.