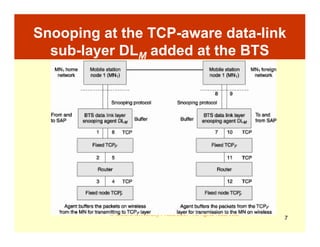
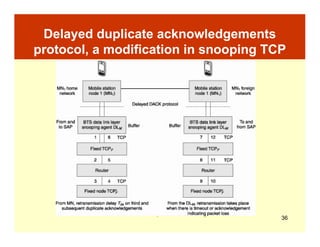
This document describes three TCP-aware link layer protocols: Snooping TCP, Wireless TCP, and Delayed DACK. Snooping TCP uses an agent at the base station to snoop and buffer TCP connections, ensuring packets are delivered to the mobile node in order and retransmitting lost packets. Wireless TCP modifies timestamps to compensate for increased round-trip time. Delayed DACK delays acknowledgments to allow time for lost packets to be recovered before triggering retransmissions.