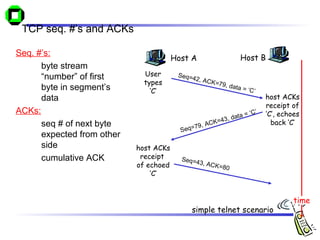
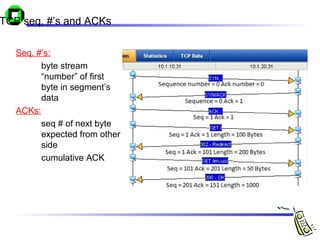
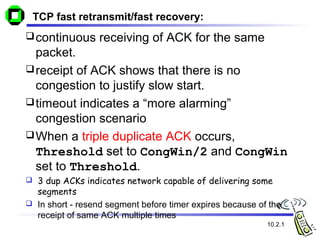
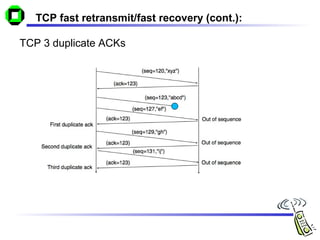
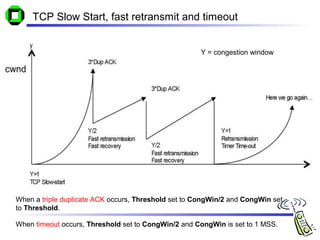
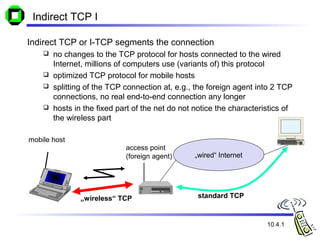
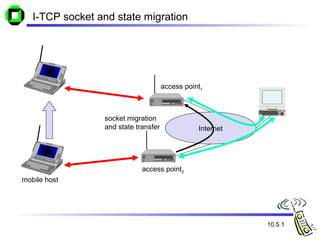
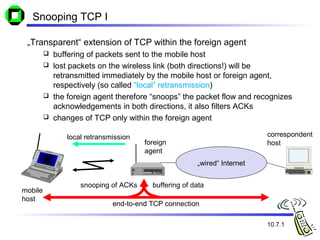
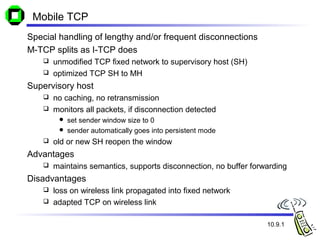
The document discusses various transport layer protocols for mobile networks, including traditional TCP, Indirect TCP, Snooping TCP, and Mobile TCP. Traditional TCP was designed for fixed networks and experiences issues in mobile networks due to factors like packet loss from handoffs. Indirect TCP splits the TCP connection at the access point to isolate the wireless link. Snooping TCP has the access point buffer packets and detect losses to enable local retransmissions. Mobile TCP uses a supervisory host to handle disconnections and restart the connection when needed. Each approach aims to improve TCP performance over mobile networks while maintaining compatibility with traditional TCP.