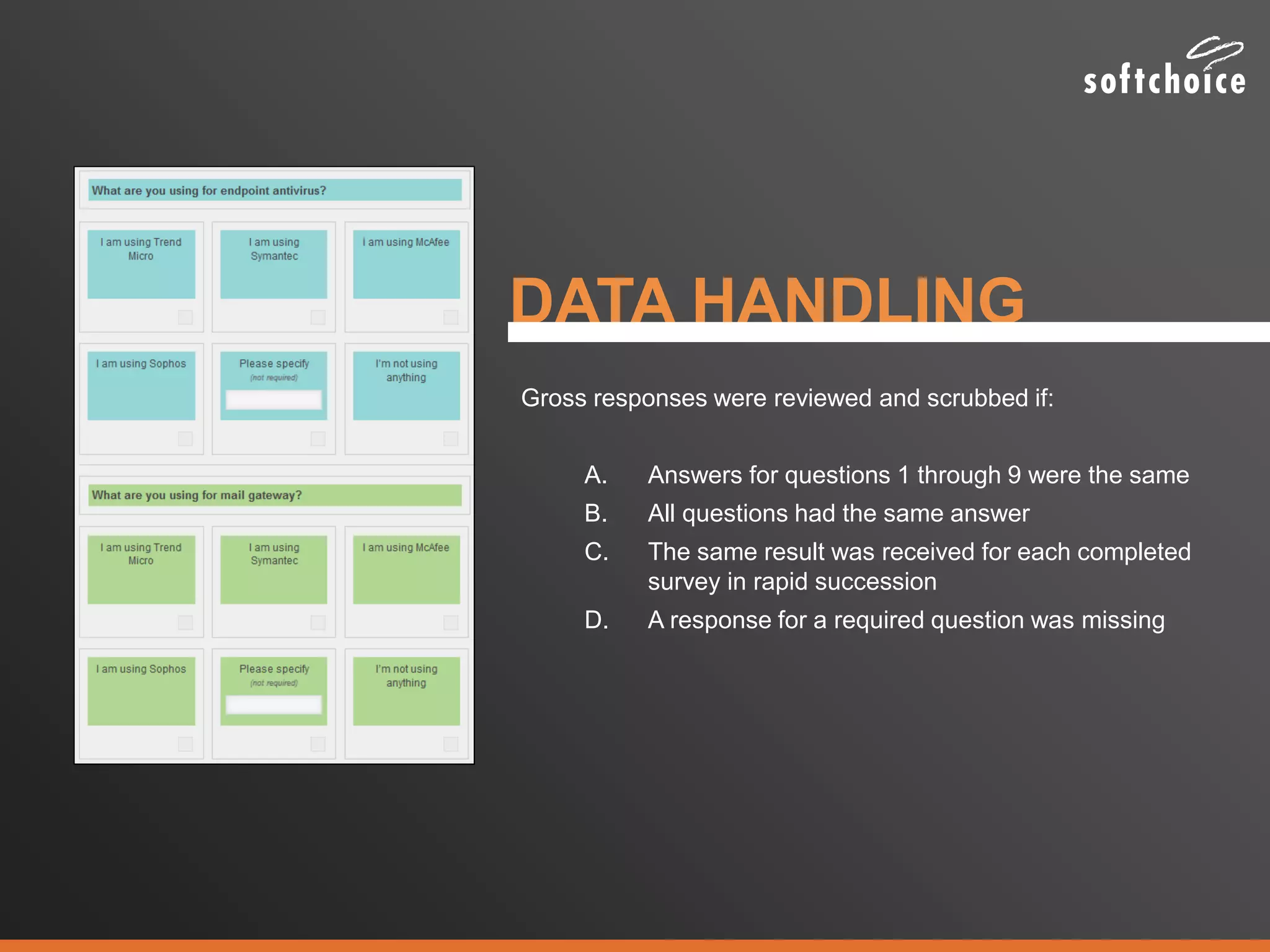
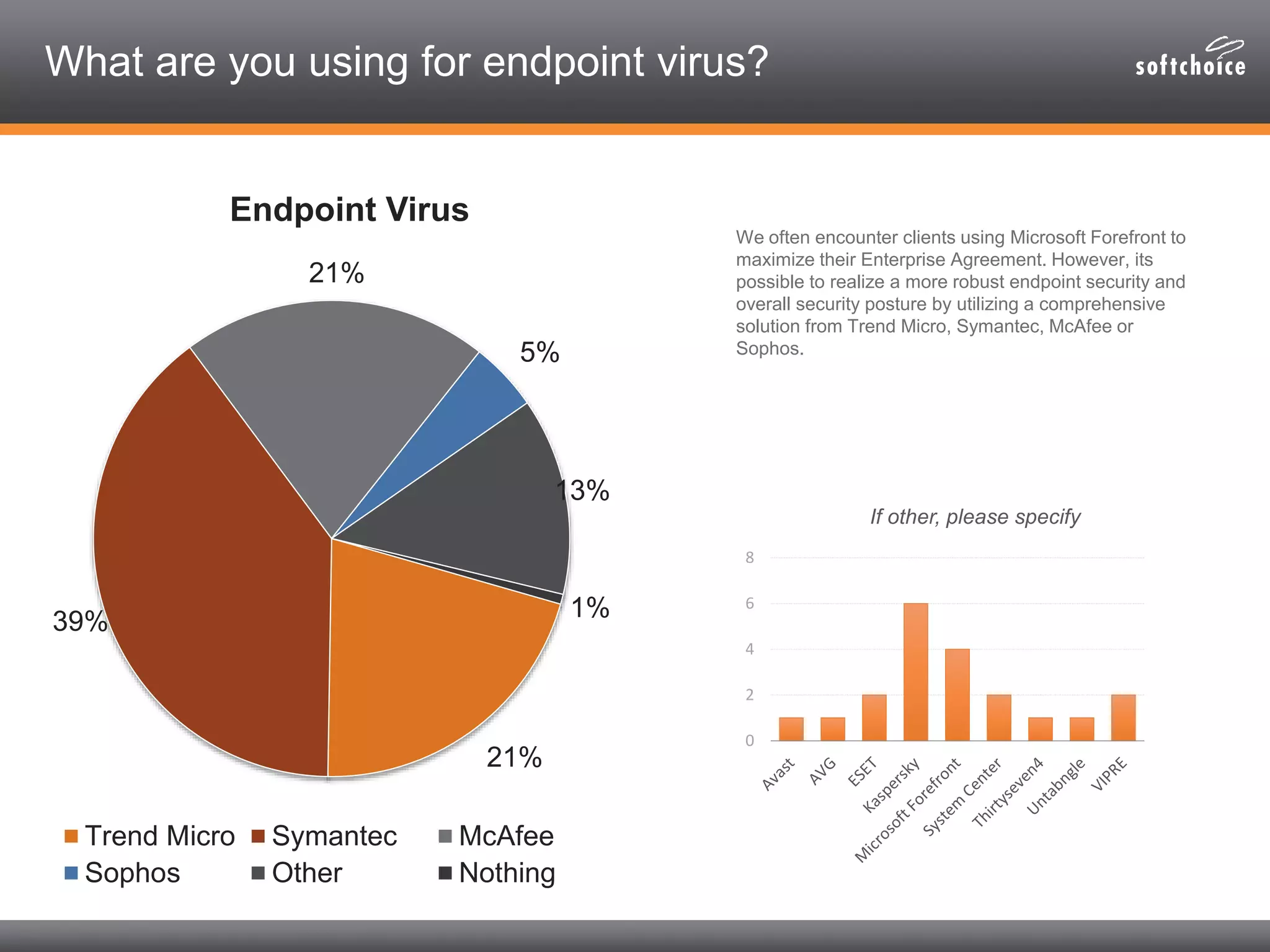
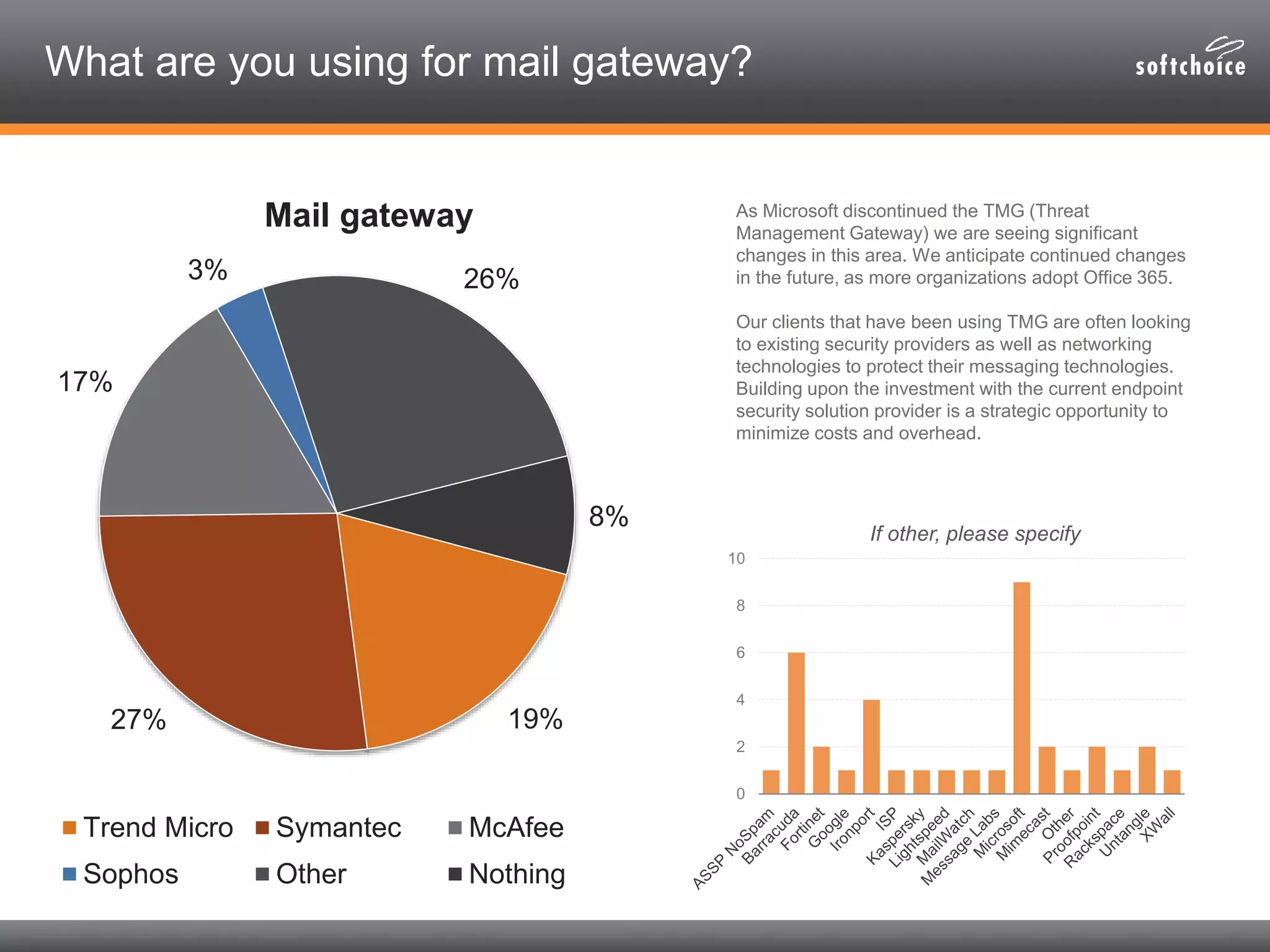
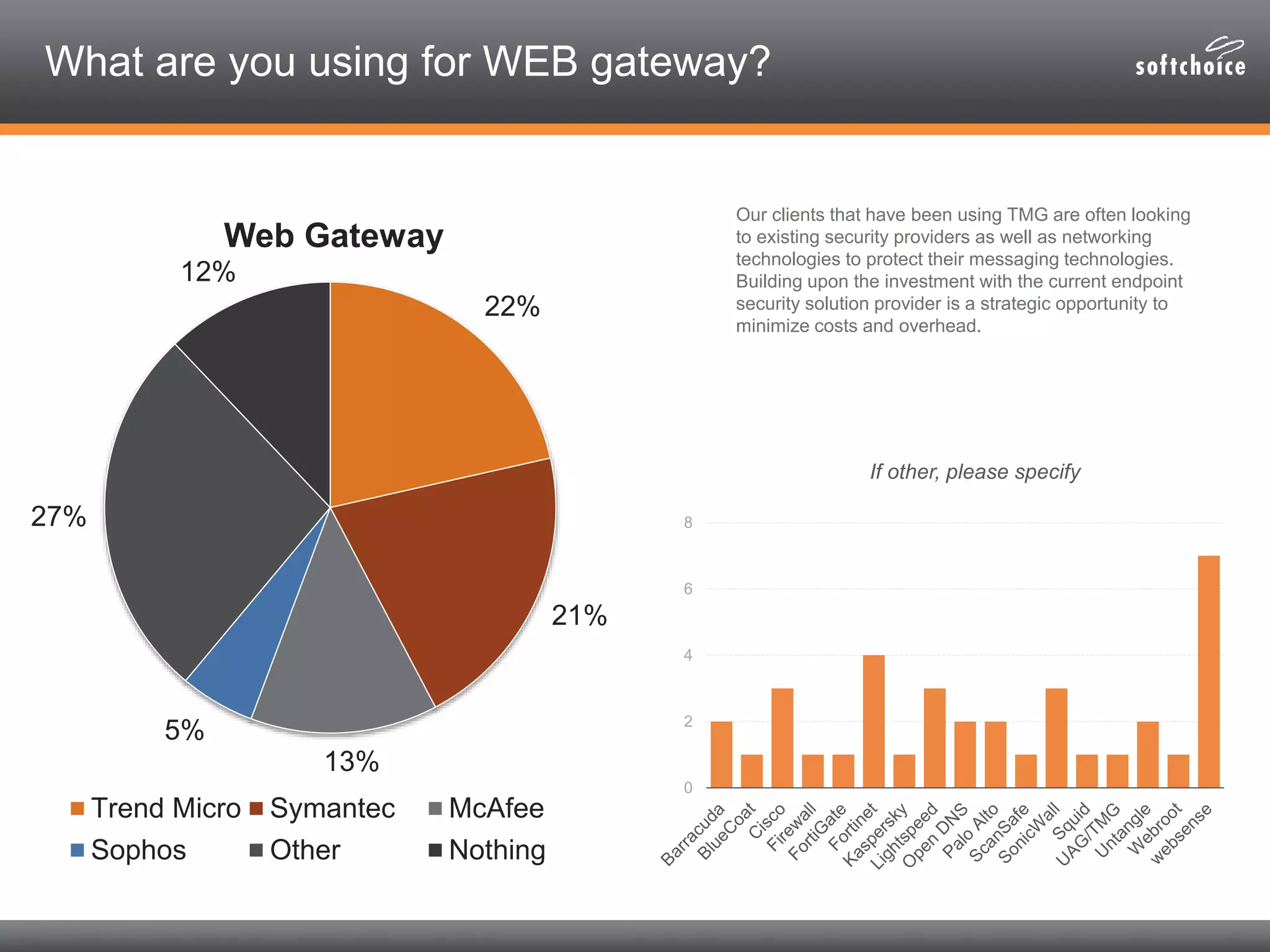
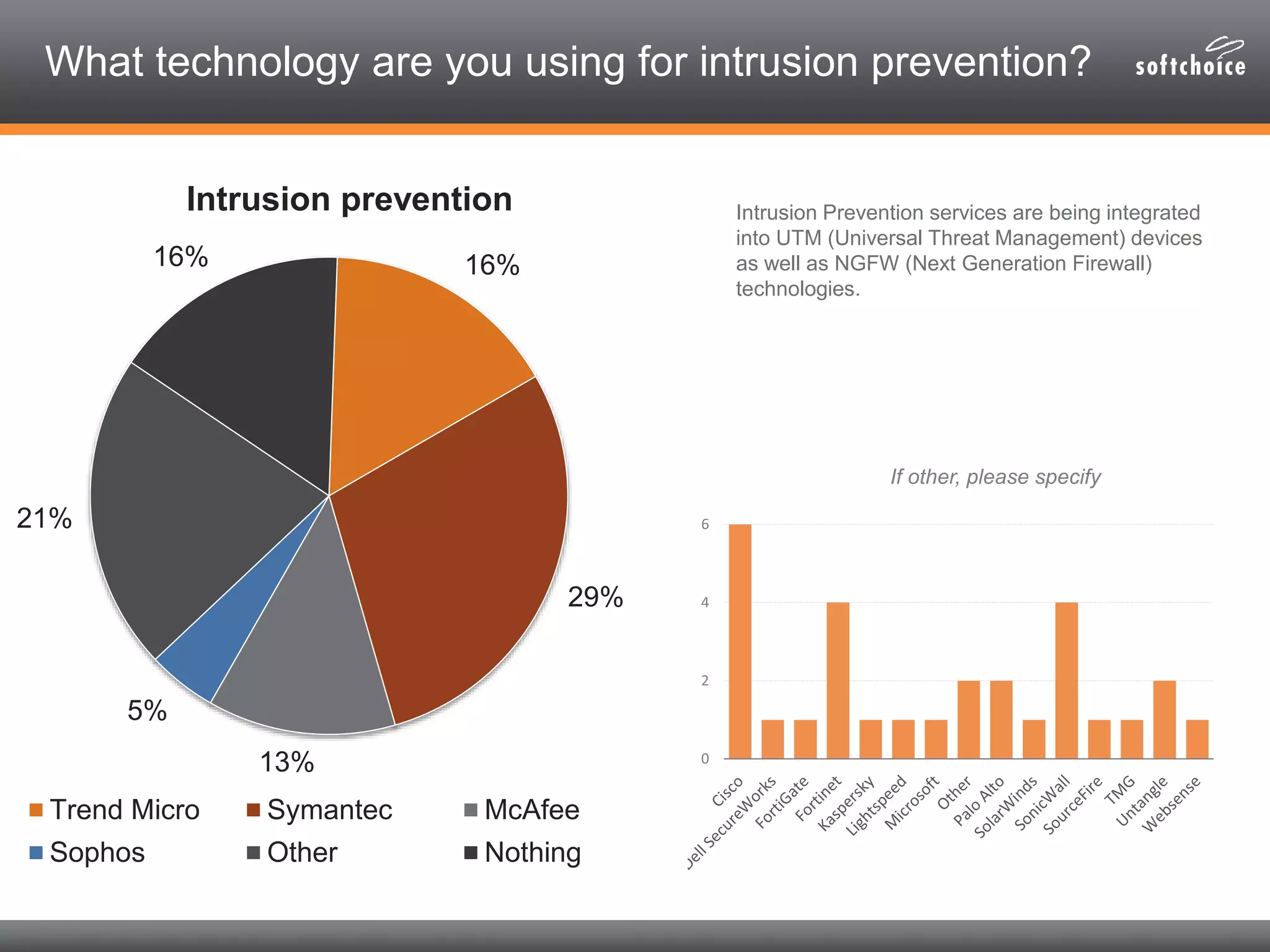
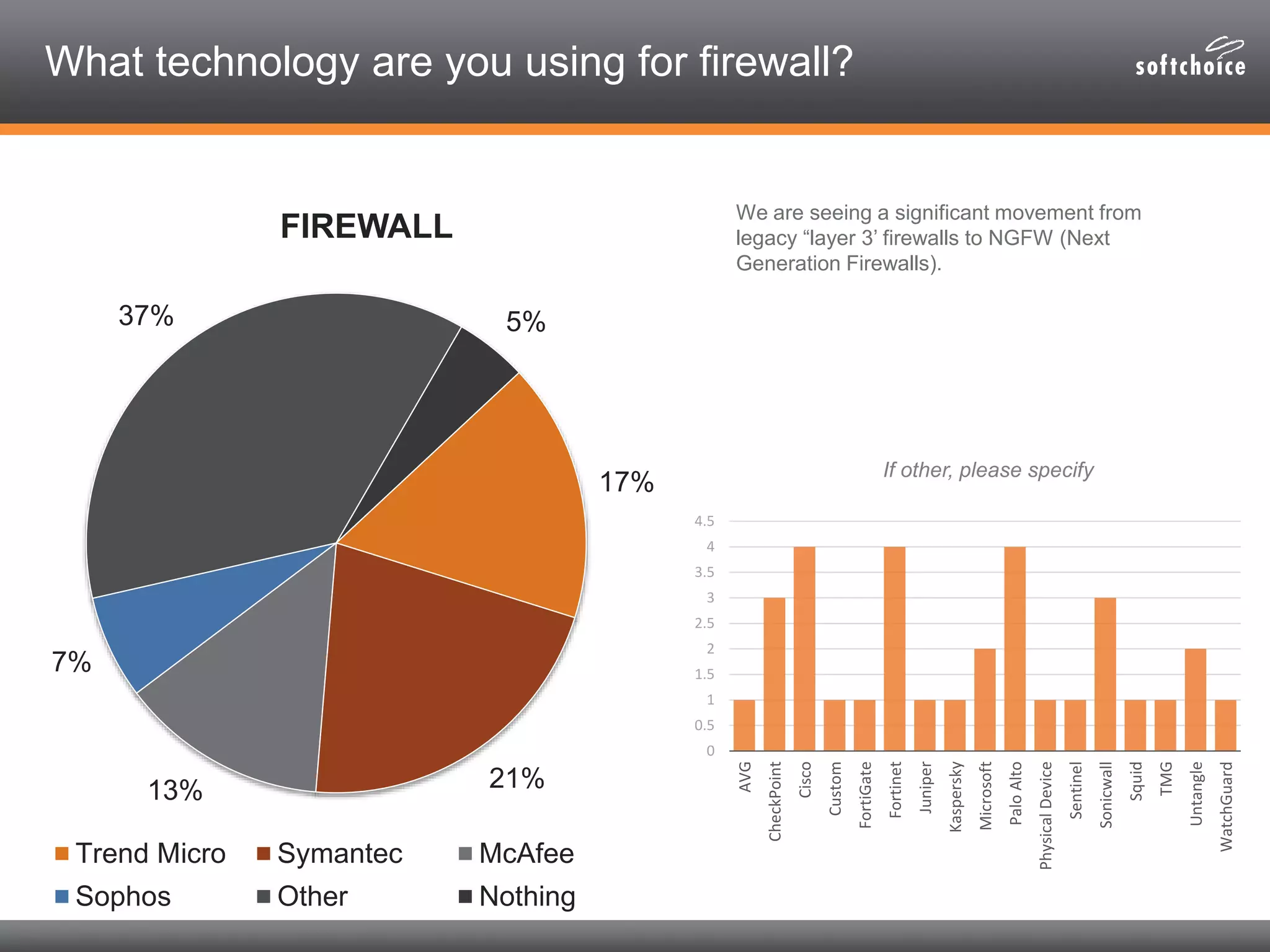
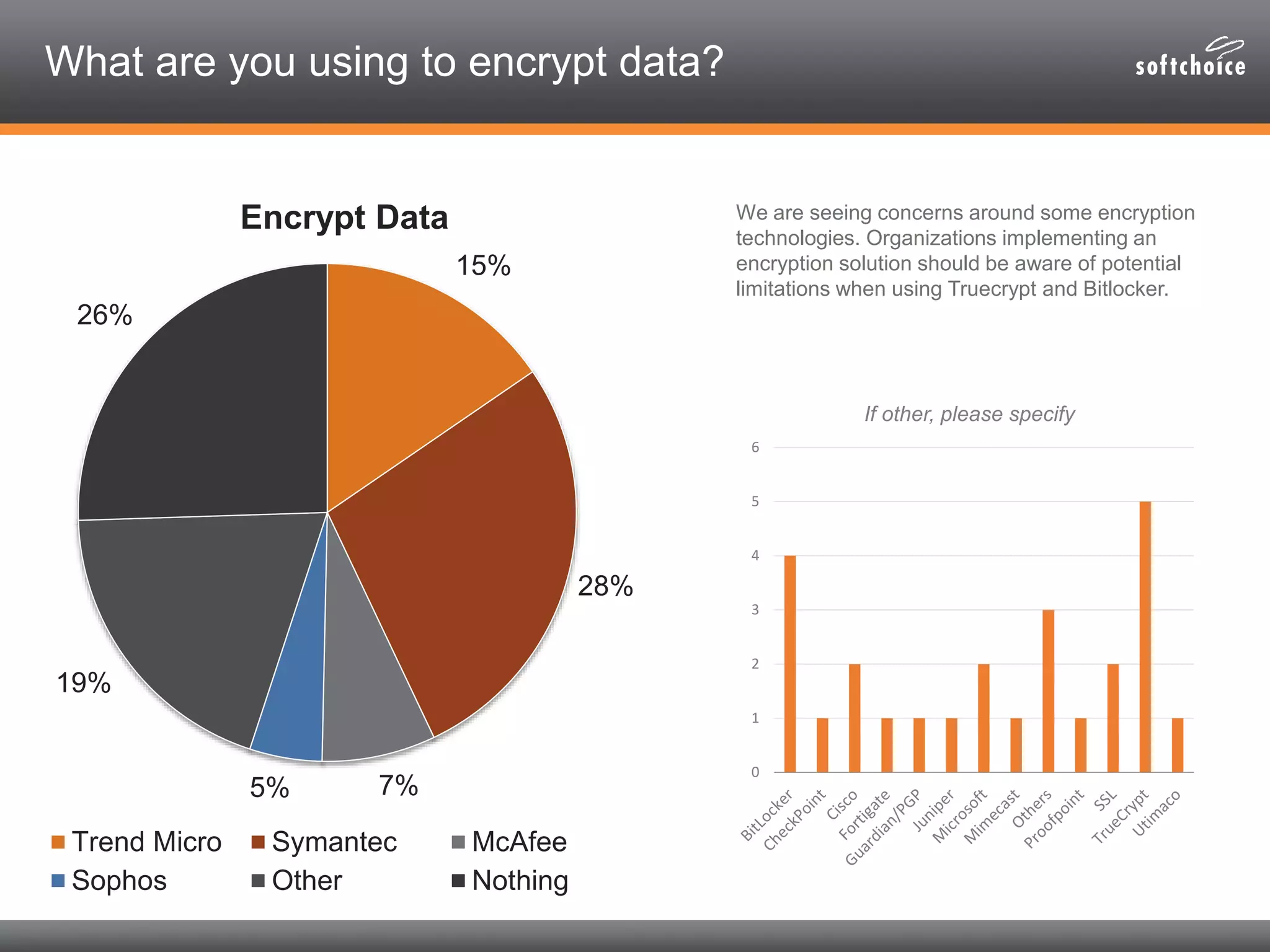
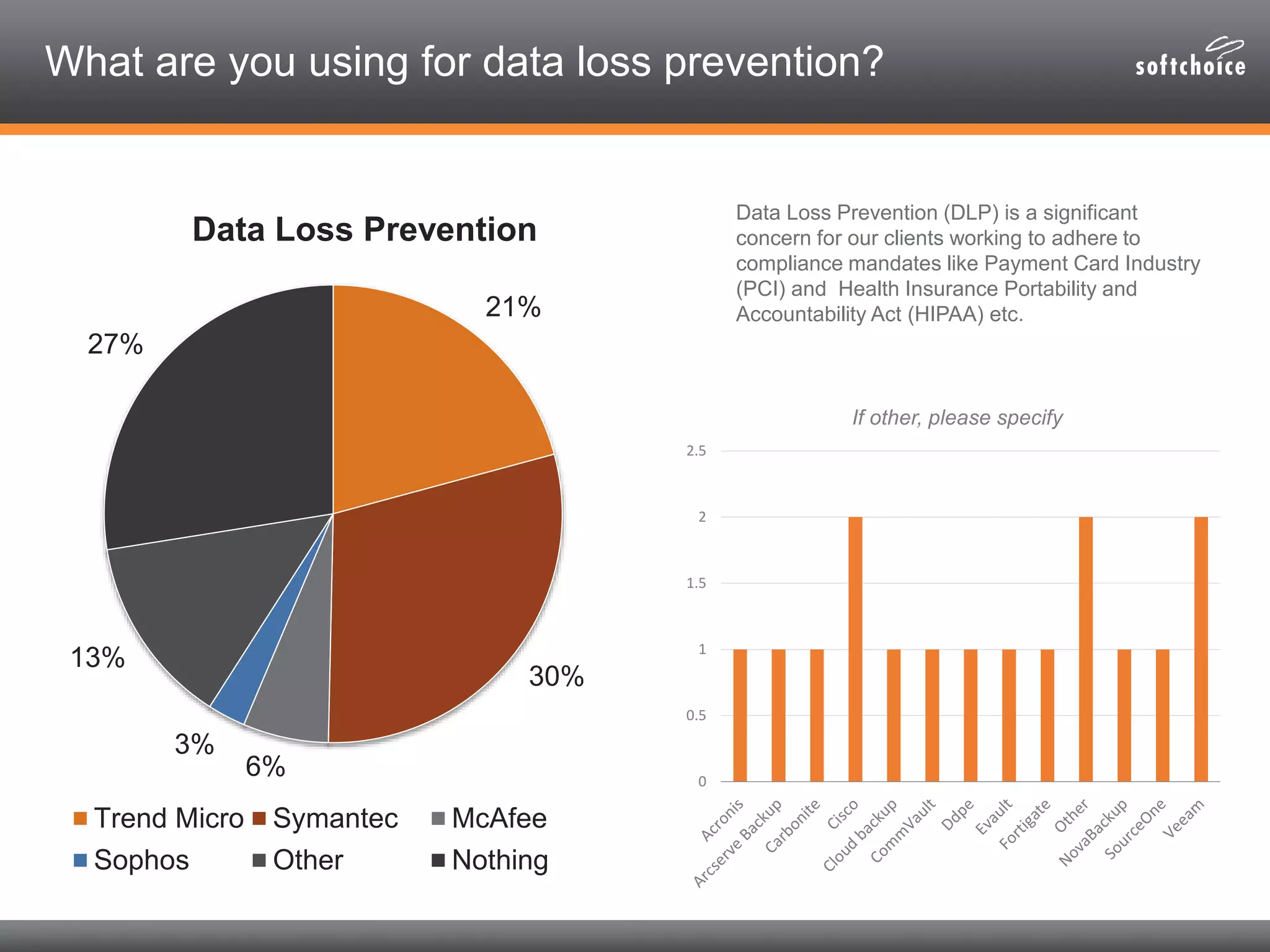
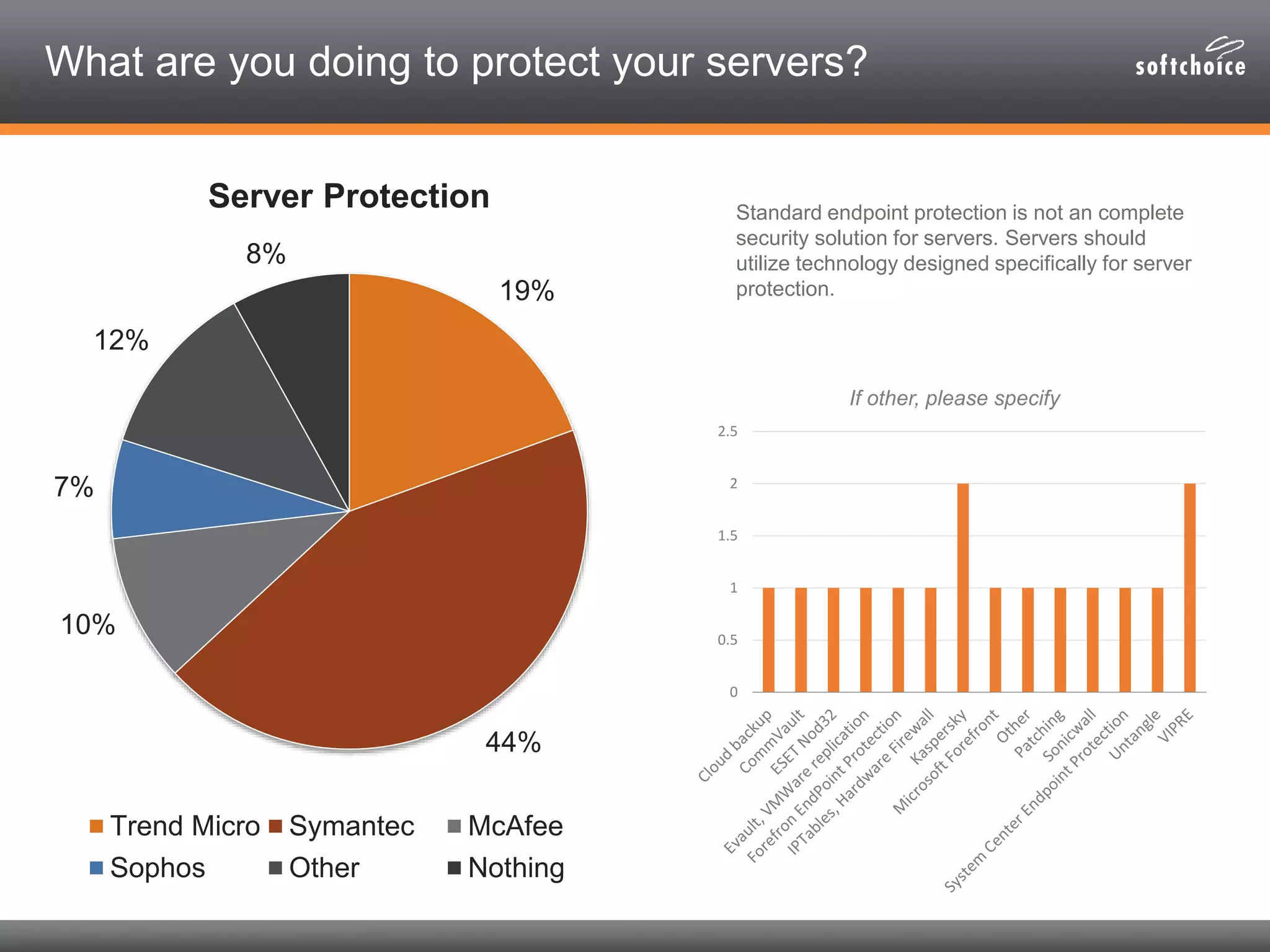
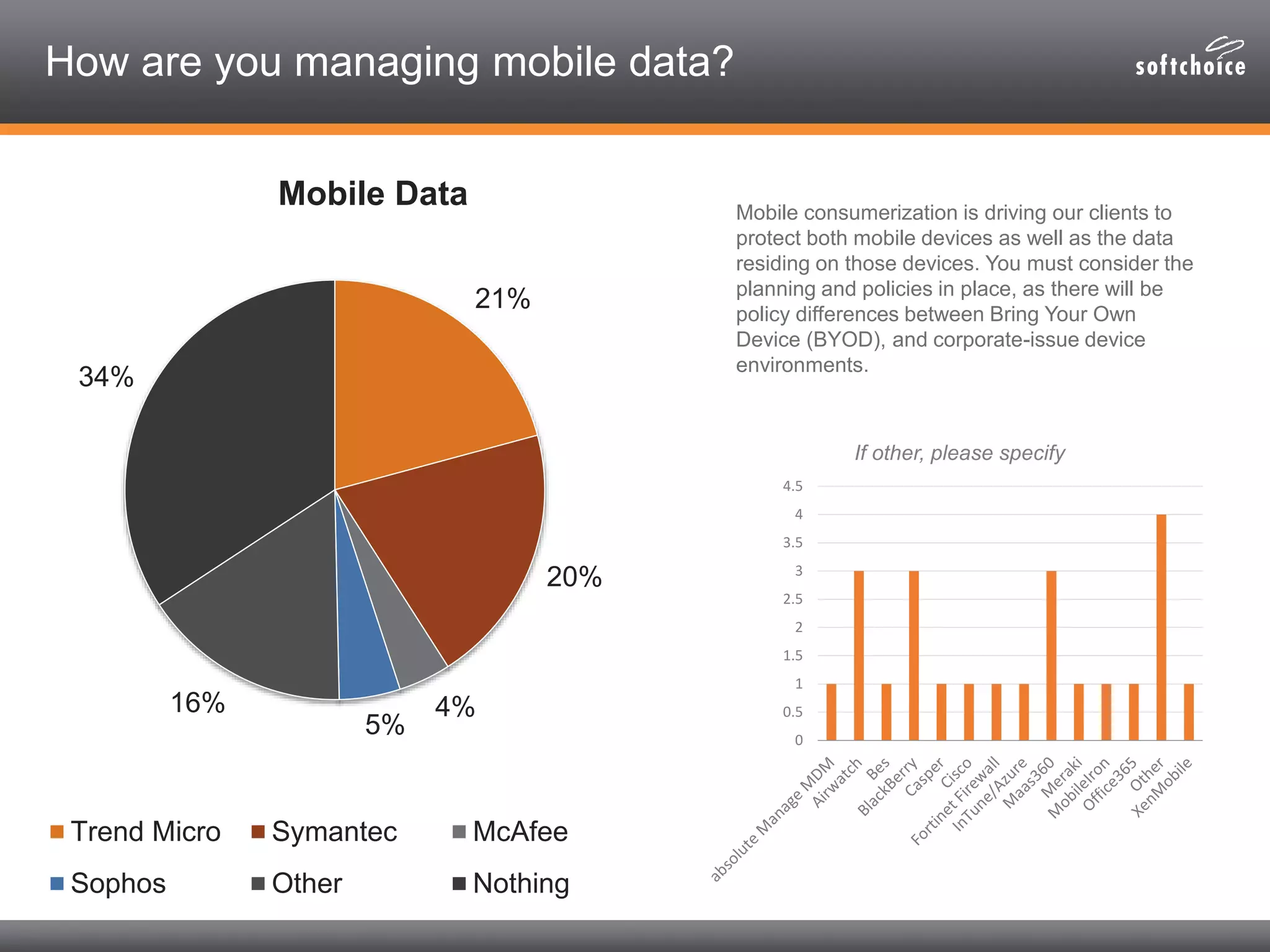
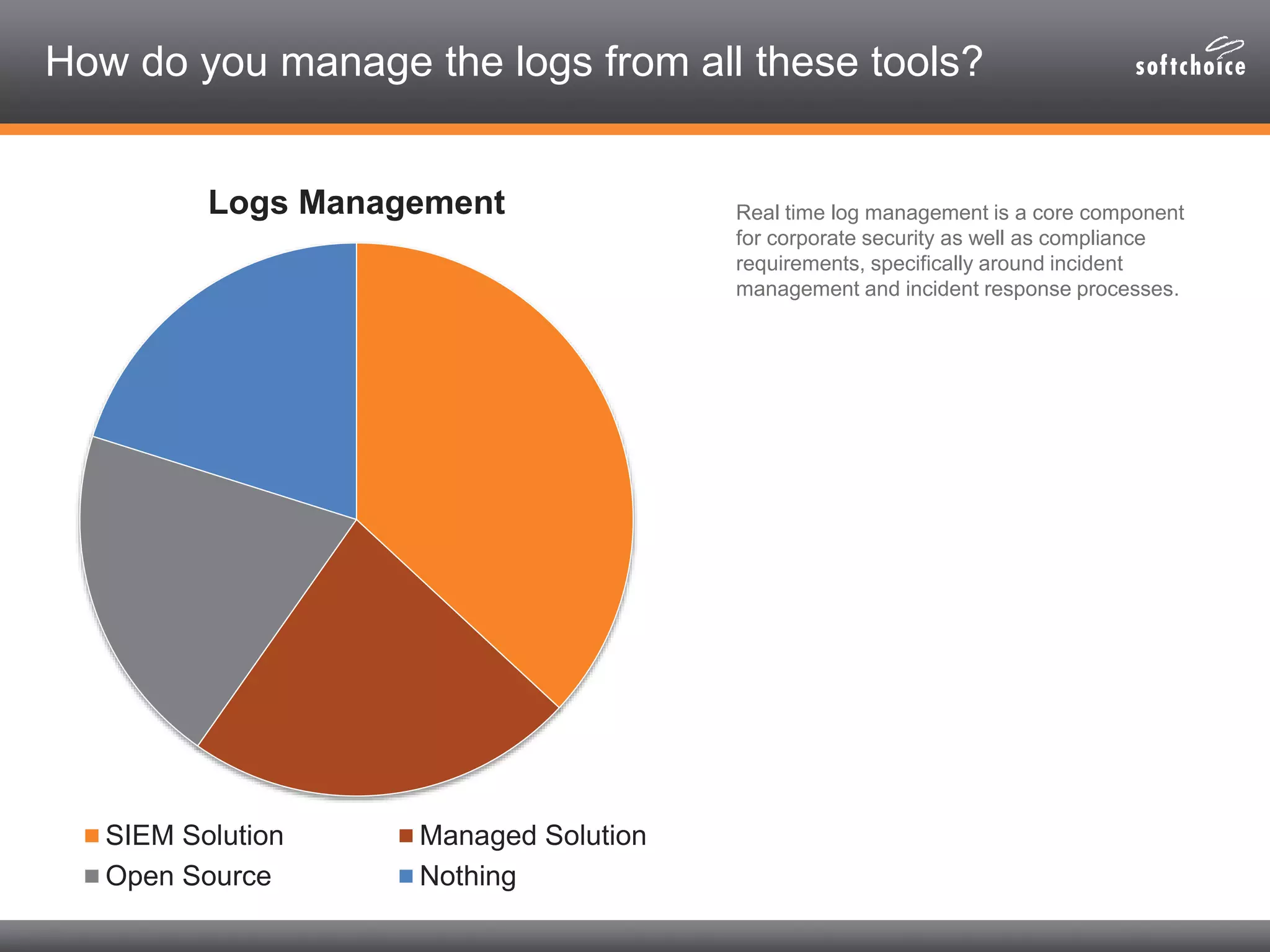
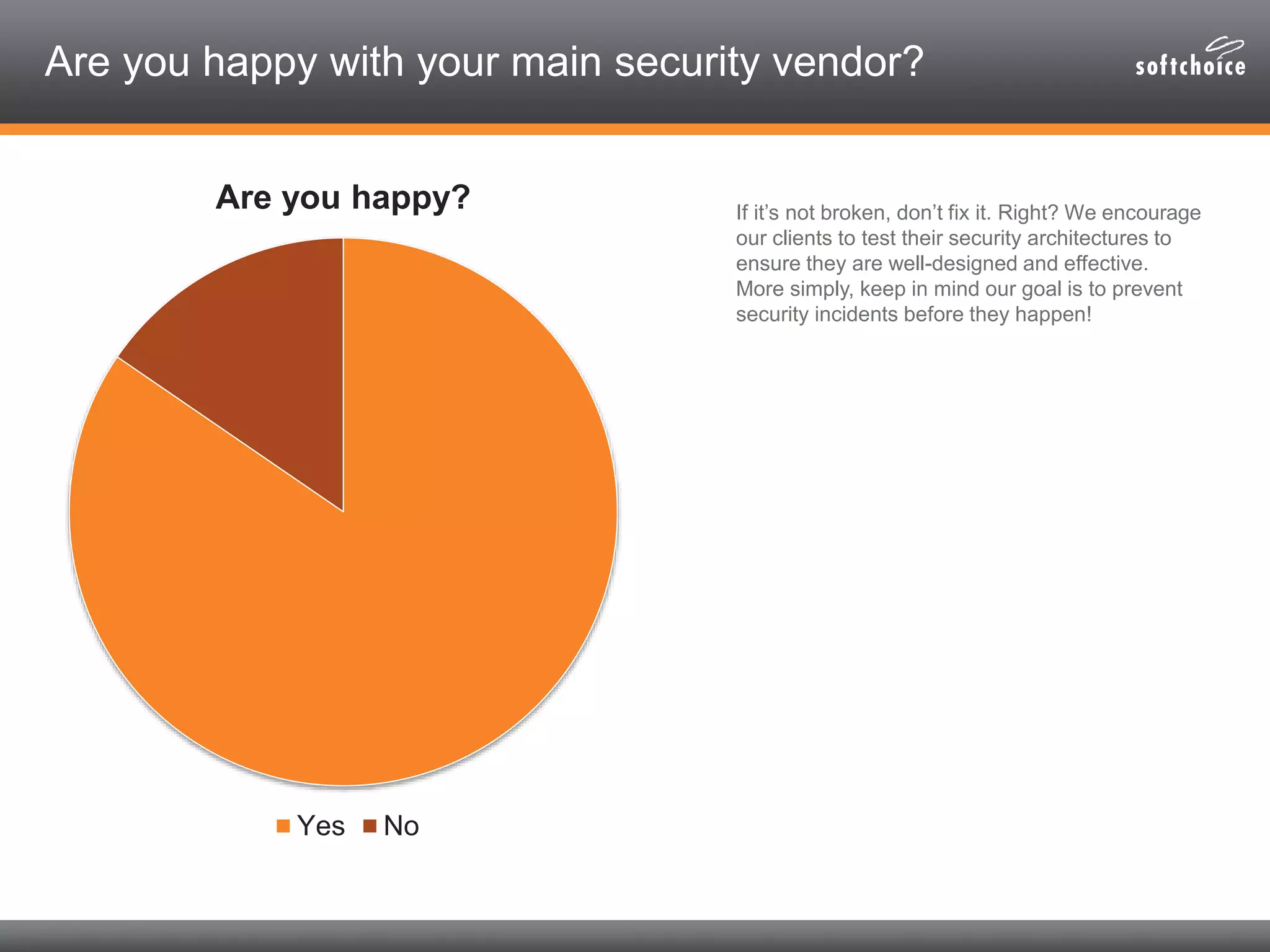
The 2014 security consolidation survey reveals that organizations are overwhelmed with logs from multiple sources, necessitating better analysis for compliance and incident detection. Key findings indicate a trend toward integrating security tools from fewer vendors for cost efficiency and improved management, with specific mentions of tools from Trend Micro, Symantec, McAfee, and Sophos for various security needs. The survey emphasizes the importance of understanding business drivers, continuous testing of security architectures, and the role of robust solutions in protecting sensitive data.