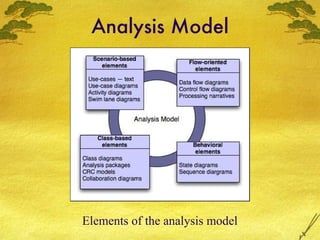
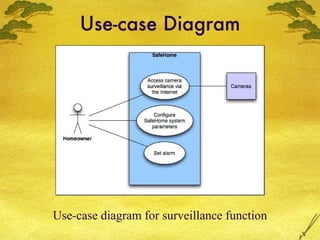
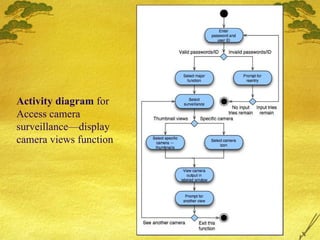
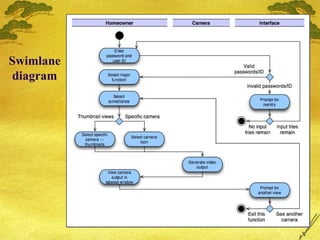
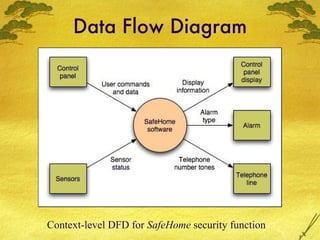
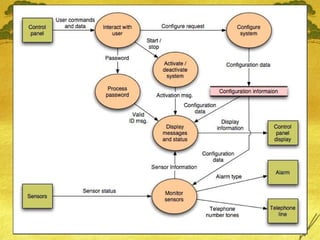
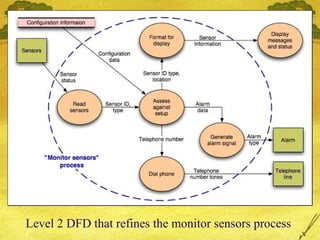
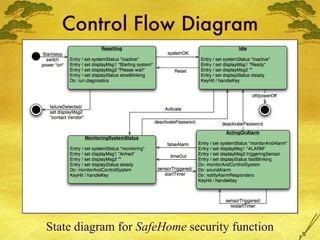
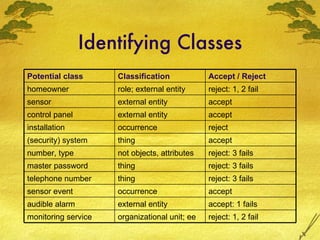
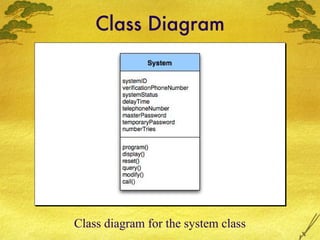
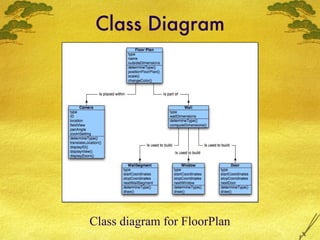
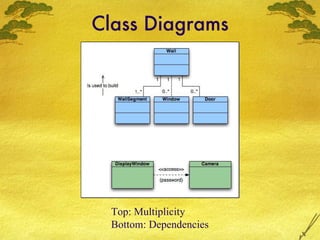
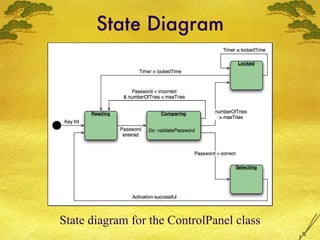
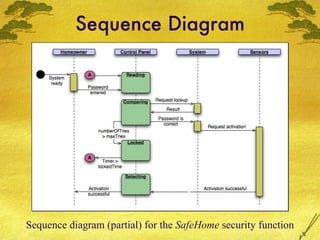
The document discusses various modeling techniques used in software engineering analysis including use case diagrams, activity diagrams, data flow diagrams, state diagrams, class diagrams, and sequence diagrams. It provides examples of how each technique can be used to model a home security system called SafeHome that allows homeowners to configure, monitor, and interact with the security system.